HashiCorp went public in December 2021 under the ticker "HCP". The stock is well named, as HCP is the acronym of their managed cloud platform. [All references to HCP that follow are to the cloud platform, not the company's ticker.] See the amended S-1, or, if you want a shorter breakdown, see this one from Alex Clayton of Meritech Capital. [This post was written in Premium in December. They have subsequently released their Q422 earnings in Mar-22.]
There are many strategies and tools that help companies control the infrastructure & app stacks they use in modern DevOps architectures (across strategies like microservices, and cloud-native infrastructure like containers and serverless functions – all covered in an earlier premium piece). This is the space where HashiCorp lives, having a focus on improving the pain points across multiple layers of modern application stacks. Like with Confluent, Elastic, and MongoDB, at its core (and deeply intertwined with its purpose), HashiCorp is an enterprise open-source company. Its primary products are available under the open-source freemium model, while also providing enterprise-licensed versions with additional features & support, and now managed SaaS offerings. And like with those companies, the SaaS offering is likely to be the most interesting bit to hypergrowth investors, being the part of the company that can best scale the financial success.
But this company is very different than those others. Where the others focused on solving one aspect of data infrastructure (whether messaging or databases), HashiCorp is focused on every layer of today's modern app stacks. And while those companies had one core product and then built an ecosystem around it, HashiCorp has multiple products that all can be used individually or combined.
Let's look at their history, their products, and what the financials are telling us.
A Brief History
Founders Mitchel Hashimoto & Armon Dagar both attended UofWA in Seattle, and there, in 2008, had early access to what eventually became the modern cloud – just as it was unveiling (during the early years of AWS, and what soon became released as Azure). Eventually, both moved into tech jobs in the Bay Area, but once there, ended up seeing all the same issues they spotted years earlier. Developers found it difficult to provision and manage cloud infrastructure. So they opted to solve these frictions themselves.
Their initial open-source product was called Vagrant in 2010, which aimed to help automate the provisioning and deploying of VM-based app stacks into developer & cloud environments. Except at the same time, Docker & containers were gaining in popularity, and they soon found it eating into Vagrant's success.
By 2012, HashiCorp was born, with Mitchell as CEO, and Armon as CTO. They quickly adapted from that early start with Vagrant, to take advantage of the rise of cloud infrastructure & containerized apps, and help automate & solve pain points for developers throughout the various layers of the DevOps workflow. Numerous products emerged over the next few years, including Packer in 2013, Terraform and Consul in 2014, and Vault and Nomad in 2015. The only new open-source products since then have been the more recent announcements of Boundary and Waypoint in Oct-20.
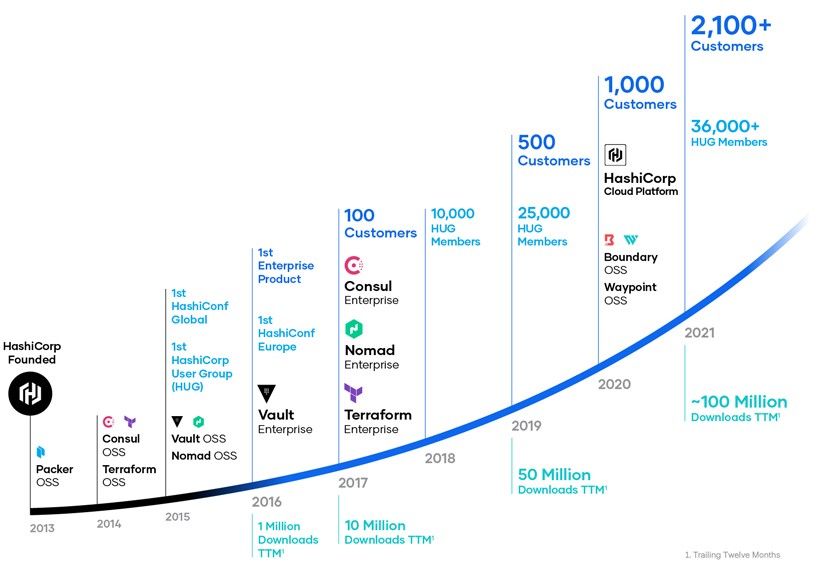
The company eventually enticed mentor Dave McJannet (ex VP of Marketing at GitHub, Hortonworks, VMware/Pivotal, Microsoft) to join as CEO in 2016, with the founders then becoming co-CTOs. In Jul-21, Mitchel Hashimoto left management completely (as well as the Board), returning to being a coder. An unusual move – but in looking at his open-source contributions on GitHub, the man is clearly a coder at heart. So we are now left with the key players being Dave McJannet as CEO, Armon Dagar as CTO/co-founder, and "individual contributor"/co-founder (aka lead engineer, and namesake of the company) Mitchel Hashimoto.
They have always been a remote-first company. They now have 1650 empl, distributed in 850 cities in 20 countries. Their main San Francisco office houses <10% of the company, while the 2 co-founders are both in Los Angeles.
A wider focus
So as stated at the top, it is important to understand that this company is managing multiple products with different focuses. Yet it all revolves around today's continuous and automated style of development, built upon cloud-native infrastructure like containers and serverless, to host distributed app stacks like microservices that are more frequently deployed. To put it simply, HashiCorp serves the entire modern DevOps workflow.
Unlike other open-source companies I've covered, HashiCorp has multiple product lines that focus on all the layers of the infrastructure stack, including the underlying infrastructure, the app stack that runs upon it, the networking between apps, and security over it all. These layers focus upon:
- Infrastructure automation and mgmt
- The modern DevOps workflow that automates across the building, testing, and deployment of apps (what is known as "progressive application delivery")
- Microservice networking & security
- Zero Trust security for DevOps and applications
And it all splinters from there. They have a plugin-oriented design across their stack, to integrate with a wide variety of cloud infrastructure and service providers across the DevOps workflow. This has exploded the popularity of their tools, as 3rd parties create integrations into their services for provisioning & controlling infrastructural needs, like databases, cloud providers, containers, software-defined networking (SDN) services, and more.
Their company profile on GitHub shows they manage 855 (!) different repositories, between their core products, official plugins, and a variety of ancillary tools. (And growing quickly -- it is now 4 higher than when I wrote my first draft.) Of those, the pinned ones are the main focus.
Products
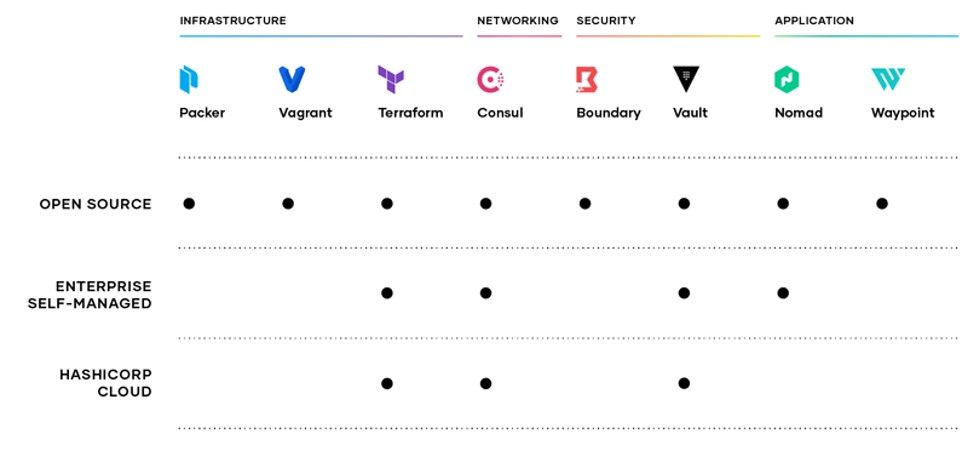
They have several core open-source products.
- For the infrastructure layer: Terraform, Packer, Vagrant
- For managing security & access: Vault, Boundary
- For networking between distributed microservices: Consul
- For DevOp workflows around app deployments: Nomad, Waypoint
Let's quickly walk through what each does, in the order above.
Terraform
Terraform allows for infrastructure provisioning & management via Infrastructure-as-Code (IaC). DevOps users write declarative configuration files using the native HashiCorp Configuration Language (HCL) or JSON. These configurations map out the desired end state for the infrastructure they need across any on-prem, IaaS, PaaS, or SaaS service. From there, the user can map out the exact actions the code will take as a test (via the "plan" command), and then perform the actions to provision or modify the underlying infrastructure (via the "apply" command). IaC makes changes to infrastructure programmable and repeatable (consistent), while codification makes it trackable, testable, and deployable. All of this enables the automation of infrastructure, via modern DevOps workflow tools.
They claim nearly endless use cases for IaC, including provisioning self-service infrastructure, multi-tier app stacks, disposable environments (such as for sales demos or QA tests), software-defined networking, or multi-cloud deploys. Users can run Terraform via cli, UI, API, or trigger it via version control systems (VCS) or CI/CD tools. Even the cloud providers see the value in this DevOps-friendly tool, so Terraform is fully supported by AWS, Azure, and GCP.
The Terraform Registry currently has 7500+ integration modules from 1600+ verified (commercial) & community (open-source) providers across the DevOps landscape of services, including Digital Ocean, Datadog, Heroku, Palo Alto, FiveTran, Fastly, PagerDuty, Elastic Cloud, Okta, Cloudflare, Splunk, VMware, MongoDB Atlas, ServiceNow, JFrog, and many, many more. Any well-used service in DevOps or infrastructure tooling has a plugin. As a sign of how quickly this ecosystem is growing, I noted that in May-21, the registry had 5700+ integration modules from 1000 providers, growing +30% and +60% over the last 6 months.
HashiCorp sees a journey that organizations take in the adoption and usage of Terraform. It starts with one individual user using it to provision infrastructure, then moves across DevOps teams who need to collaborate over and share infrastructure. From there, it moves more fully into an organization, becoming the primary tool utilized by Ops to control how developers are able to provision infrastructure. As enterprises embrace Terraform more fully, HashiCorp provides an enterprise policy-as-code feature called Sentinel, which allows Ops to programmatically control and automate the security and governance over any internal use of infrastructure-as-code. Sentinel ultimately empowers developers to be able to self-provision their own infrastructure, in a secure and governed way, moving away from needing to make a service ticket with Ops and wait for an approval process to okay the request. The entire request & provisioning process can now be entirely automated via Sentinel, which can also use plugins to tie into other external services to make policy decisions.
Competition includes other IaC-based open-source packages, like CloudFoundry, Ansible, Chef, Puppet, and SaltStack – most of which have their own enterprise-managed services. The cloud vendors also have their own native IaC tools, like AWS CloudFormation and Azure Resource Manager. Multiple pure-play SaaS services have emerged for cloud infrastructure mgmt as well, such as Pulumi, CloudBolt, and Morpheus Data, as well as offerings from traditional players in infrastructure & networking like VMware vRealize and Cisco CloudCenter.
In Sep-18, HashiCorp announced that they were creating a managed service to help track Terraform runs collaboratively across a team. That effort initially debuted in May-19, but by Sep-19, morphed into Terraform Cloud, a fully-featured managed service that provides additional team collaboration, centralized tracking, and governance features over the Enterprise edition. In Jun-20, this initial SaaS service became part of the new HashiCorp Cloud Platform (HCP), their new platform to house all of their managed SaaS services.
Packer
Packer is a CLI tool for building app stack templates (known as automated machine images, or AMIs) that can be used across any on-prem or cloud VM or container environment. It runs on any platform (even a developer's laptop), and, via plugins, can generate images for use on AWS, Azure, GCP, VMware, VirtualBox, Docker, Kubernetes, HashiCorp Nomad, or Digital Ocean. It can also tie into many CI/CD or IaC provisioning tools, including HashiCorp Terraform and Ansible. In Oct-21, a new service in HCP was announced in beta called HCP Packer, which is a managed Packer tracking service (not Packer itself, which can run anywhere).
Vagrant
Vagrant is a tool for building virtual machine (VM) environments in a single, programmable workflow. It can provision VMs on VMware, VirtualBox, AWS EC2, or OpenStack, and can tie into IaC tools for provisioning the VM. The goal was to have a single workflow so that developers, ops, and designers can all recreate a VM-based app stack in a repeatable and consistent way, and then allows that team to use their own IDE, browser, debuggers, or image editors from their laptop. (As mentioned before, this tool has waned in popularity as the use of containers has risen, which has programmability built in, to easily generate a consistent copy of an app stack.)
Vault
Vault is for credentials and secrets management – but goes way beyond the traditional tools in this space, veering into what Privileged Access Mgmt (PAM) services provide. It is focused on identity-based security, which, as we know, is the lynchpin for a Zero Trust security posture. Vault is built for tracking identities and access rights across human users, apps, systems, VMs, containers, orchestrators, microservices, functions, DevOps tools, and SaaS services. It currently has 70+ integrations, and in Oct-21, added integrations with a variety of observability platforms, such as Datadog and Splunk. Once an identity has been established as trusted via authentication (authN), there are many authorization (authZ) features available.
- It can look up the static credentials and secrets (such as encryption keys) an authenticated identity has authorization to access – like any credentials & secrets mgmt system provides.
- It can merge trusted identities across multiple identity providers (IdP) like Okta, AWS IAM, Azure Active Directory, and LDAP. Once authenticated, it can then serve as an SSO broker to allow access to any services that that identity is authorized to access – like any PAM system provides. This prevents having to expose the credentials & keys with the identity directly.
- Extending that further, it can not only deliver static credentials, but has the ability to generate dynamic credentials to systems that the identity is authorized to access – like many PAM systems provide. These are one-off credentials that are created on the fly (known as "just-in-time"), and expire after a pre-determined length of time or the connection ends. This further strengthens the security, by putting a time limit on any connection to privileged systems.
- It can provide advanced data protection (including disk, volume, and VM encryption) by controlling the reading and writing of data via managed encryption keys, which are only accessible to authorized identities. This is extremely useful to organizations that don't fully trust the cloud providers with their data at rest or in transit! Going farther than most PAM services, this is an encryption-as-a-service feature that enables real-time encryption as data is read or written. Going further, Vault can enable advanced security features like automated key rolling (pushing new keys out across the entire architecture) and key rotation (changing a given key on a set schedule).
Like with Terraform, HashiCorp sees a journey that organizations take in the adoption and usage of Vault. It starts with the centralization of credentials and secrets for manual lookup (human-to-machine). Ops teams begin to orchestrate these secrets into infrastructure via IaC (such as writing to config files), while developers then automate access to credentials programmatically across all apps, APIs, services, and functions that need access to other systems (machine-to-machine). Advanced teams then improve the security further by using the dynamic credentials and encryption-as-a-service features.
Competition includes other secrets mgmt and PAM services like Thycotic, CyberArk, Centrify, and BeyondTrust (and is a market Okta is expanding further into), as well as cloud-provider specific ones like AWS Key Mgmt Service (KMS), AWS CloudHSM, Azure Key Vault, and GCP Cloud Secrets Mgr.
Understanding Zero Trust is the key to understanding Vault. It allows for not trusting the underlying networks and infrastructure. Vault wants to serve as the centralized interconnect that every human or service must utilize to connect with the other services it depends upon. But going further, the security with Vault is greatly strengthened by the addition of Boundary. In Jan-21, they announced HCP Vault, a managed service in HCP. It went GA in Apr-21.
Boundary
Boundary is a more recent addition to their open-source products, being announced in Oct-20. Boundary provides identity-based access management over dynamic cloud infrastructure. What does that mean? It enables Zero Trust access capabilities, serving as a broker between existing identity providers (IdP) and the infrastructure or service it is requesting. It is accessible via a CLI, web UI, or desktop app from an endpoint, and requires an installed agent.
This agent securely connects to the gateway at the network's boundary (get it?), which integrates into existing identity providers (IdP) to initially authenticate the human- or machine-based identity. From there, the gateway serves as a policy engine that allows enterprises to control what identities can access what systems, and then serve as a proxy for the Zero Trust connection between the identity and the requested service. In combination with Vault, it can either retrieve the given credentials for the service requested (and not expose them to the identity originating the request), or utilize dynamic credentials that expire after a set time or when the session terminates. Users are never exposed to the underlying network, nor the credentials used.
In essence, Boundary is a Zero Trust brokering service for creating ephemeral connections to dynamic infrastructure & services, that (in my opinion) greatly enhance Vault's capabilities. If you think it sounds a lot like Zero Trust solutions like Zscaler ZPA or Cloudflare Access, you are correct, as well as SaaS services like Teleport and Twingate.
Consul
Consul allows for managing & securing the networking between services, across any cloud or environment. It is a multi-cloud service mesh that discovers & tracks dynamic services, and then secures & automates the traffic between them. (This type of service-to-service inter-communication across data centers is known as east-west traffic, in networking parlance.)
Like in Vault, every service has an identity, which is used to help secure intercommunication between services in a Zero Trust way. It can be run on and interconnect between any infrastructure environment that can host services, such as VMs, containers, Kubernetes, HashiCorp Nomad, and serverless. Like Terraform and Vault, it is built upon integrations with clouds, networking, and security services, with plugins to AWS, Azure, GCP, VMware, HashiCorp Vault, F5, Nginx, and more.
Again, Hashicorp has a vision into the journey that organizations take with Consul. At first, organizations use it to track dynamic services, and allow those services to intercommunicate via direct requests to each other. From there, companies begin to programmatically control their microservices app stack, via automations triggered when new services are seen or existing services destroyed. This allows for the services to shift to a dynamic "pub-sub" model for service-to-service intercommunication, instead of direct requests, which eliminates the need for load balancers. Advanced users can use the "sidecar proxy" to directly place a Consul agent next to their services (so no code needs to be modified), in order to then be able to securely encrypt the traffic between two registered services, eliminating the need for firewalls. This is extremely useful to organizations that don't fully trust the cloud providers with their data in transit between services, environments, and clouds!
Competition includes open-source service meshes like Istio, Open Service Mesh (OSM), and Linkerd. There are also several cloud-specific managed solutions (like AWS App Mesh and GCP Anthos Service Mesh), and enterprise SaaS solutions (like Kong) for interconnecting services. Google's evolution of the Kubernetes platform, Anthos, has directly embedded Istio to provide native service mesh capabilities, and Azure Arc did the same with OSM (as discussed recently).
While Consul is a DevOps microservice networking tool at its core, the advanced features around encrypted traffic reinforce a Zero Trust posture. It again allows for not trusting the underlying networks and infrastructure. In combination with Vault's key rotation capabilities, you can have extremely high levels of security by encrypting your machine-to-machine traffic as it traverses across and between environments and clouds. This vaguely reminds me of Zscaler's Workload Segmentation product – not in how it is implemented (very different products – Zscaler applies behavioral analytics via AI/ML over service traffic), but in the end result of how the traffic between cloud services is being secured.
HashiCorp has provided the ability to directly provision a managed Consul cluster directly in Azure since Sep-20, which is billed through Azure. Soon after, they began offering HCP Consul as a managed cloud service in HCP in Oct-20. They recently announced a new feature in Consul in Oct-21 called the API Gateway, which allows external API clients to securely interconnect with the service mesh (what is known as north-south traffic, from/to an outside network). As of Nov-21, Consul is now available on AWS Elastic Container Service (ECS).
Nomad
Not only do they stress the portability of apps, but also the portability of the app stack it runs on. Nomad is a microservice and container orchestration platform. It competes with the popular Kubernetes (K8s) platform, but goes beyond containers, supporting legacy app stacks based on VMs, Windows, and Java – allowing for modernizing legacy apps without a rewrite. It is lighter-weight and simpler than Kubernetes, but natively integrates with Terraform, Consul, and Vault to provide a comparable feature set. It is also highly scalable, and can even serve as an app stack control plane across environments and clouds. It is widely compatible with other DevOps tools and services, including Gitlab, JFrog, Datadog, and Splunk.
They admit that Nomad and Kubernetes are each better at some use cases than the other. Kubernetes clearly has all the momentum in container orchestration, and is recommended when dedicating your app stack to a single cloud provider. Nomad seems best for a mix of containers and non-containers, migrating legacy apps to the cloud, or having app stacks that span hybrid and multi-cloud environments. Users of Nomad include Cloudflare, Roblox, Pandora, Github, and Autodesk.
Waypoint
Like Boundary, Waypoint is another recent addition, also announced in Oct-20. It provides a common workflow, based on a single configuration file, to build, deploy, and release container-based apps on any host platform – including Kubernetes, HashiCorp Nomad, AWS ECS, GCP Cloud Run, and Azure Containers. It supports an extensive number of languages and frameworks, including Angular, React, Ruby, Python, Go, Node.js, and .NET, as well as CI/CD tools like GitHub, Gitlab, CircleCI, and Jenkins.
Waypoint strives to greatly unify & simplify the workflow of how DevOps teams deploy containers across these platforms. Like with the other products, Waypoint has an extensive set of plugin integrations with deployment tools and services, such as version control systems, CI/CD tools, and artifact repositories (like JFrog). DevOps teams can also automate deployment triggers, based on a git-ops (triggered by Gitlab or GitHub), chat-ops (triggered by Slack messages), or manual approaches.
Putting it all together
Of those 8 core products, they sell enterprise licenses & support for Terraform, Vault, Consul, and Nomad. One unique feature of their Enterprise level is their Sentinel policy-as-code engine, which allows for codifying governance policies around infrastructure and security, and checking actions against those policies in real-time. I mentioned it above in Terraform, but it is built across Vault, Consul, and Nomad as well. It allows for dynamic logic and integrations with 3rd party governance tools, so allows for programmable policy enforcement.
As for managed SaaS services over those products, HCP now contains Terraform Cloud, HCP Consul, and HCP Vault, all built over their Enterprise versions that include Sentinel, as well as the newly introduced HCP Packer (a tracking service, not Packer itself). HCP customers include Barclays, Citadel, Pandora, Adobe, and Progressive.
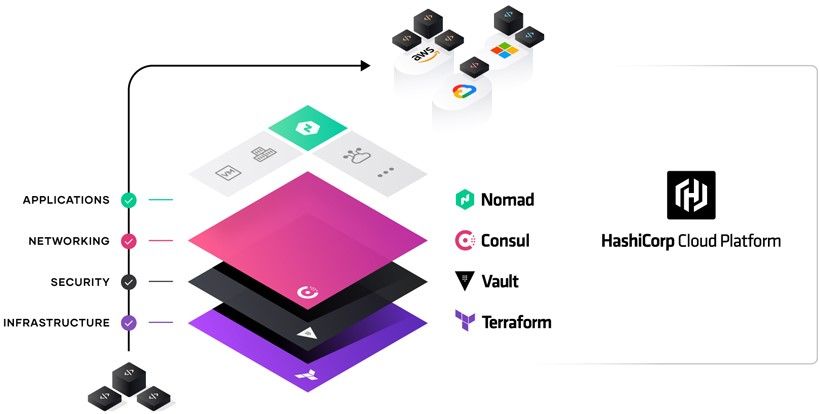
HashiCorp has an impressive array of products that touch on several DevOps pain points. Their products can be adopted individually, but also (like Voltron), can combine together into a greater whole. As for the journey that customers take through their products, it tends to all start at Terraform and Vault – either an Ops lead will start provisioning via Terraform, and then secure it via Vault, or a Security lead will start securing via Vault, and provisioning secrets via Terraform. From there, organizations have services that need to talk to each other securely via Consul. Nomad might eventually be utilized as a common deployment & runtime platform regardless of environment, especially helpful for migrating legacy apps or doing multi-cloud.
Across their products, they stress how DevOps teams want a consistent workflow & standardized approach over their processes and tools, regardless of the environment or cloud. They have a clear focus on being platform-agnostic, and a partner to all. They have a growing ecosystem of partners with cloud providers, ISVs, and SIs.
GTM motions include open-source, self-service, direct sales, and partners. Their open-source products are clearly resonating, and have been downloaded 100M times over the TTM, and have 216K stars on GitHub. Open-source (as always) serves as a funnel into the enterprise levels, but they most focus their direct sales on the Global 2000, by convincing CIOs to standardize upon their DevOps point of view and toolsets. They claim a flywheel between these GTM motions and their growing ecosystem, as customers adopt, land, expand (their usage), and extend (into new products). ["Land, expand and extend" is land and expand that goes to 11.]
Their growth strategy is to continue to land new customers, expand (and extend!), grow internationally, foster their ecosystem, and continue to unlock additional value with HCP (grow the cloud). They ride the trends of cloud adoption, and especially multi-cloud (which Consul and Nomad both help cross). The fact that these products can be used across environments and clouds should not be ignored. They mentioned a stat that cloud spend should see a CAGR of 15% through 2026, per 650 Group.
They report a TAM of $41.7B in 2021, growing to $72.5B in 2026 with the rising trends in cloud adoption. That TAM is composed of:
- Terraform TAM rising from $2.1B -> $12.0B
- Vault TAM rising from $16.3B ->$20.8B
- Consul TAM rising from $22.6B -> $30.9B
- Nomad TAM rising from $0.7B -> $8.8B
Vault and Consul clearly solve specific pain points, and seem to have the most opportunity. I find it unsurprising that Terraform's TAM is expected to rise so heavily over time, considering how adaptable and pluggable it is (so can change with the trends). Nomad's trend is more surprising, perhaps a testament to how much expectations are for multi-cloud strategies to kick in, and having those last legacy workloads finally migrate in place (without refactoring or major changes).
While their moves into tooling over the modern DevOps workflow are interesting (across Nomad, Packer, Vagrant, and Waypoint), their strategy with Zero Trust interests me the most. This presentation from Jan-21 goes over this strategy in-depth, but it is clear in the product reviews above that Consul combines well with Vault (securing the network between services, across environments and clouds), and that Vault combines well with Boundary (securing human- and machine-access to app stacks) – and then Terraform can be used to tie them all together across provisioned systems and networks. This is the product area to watch, in my opinion.
The look at the numbers
[These were as of the IPO.]
FY21:
Revenue 211.9M +75%
Custs >100K 500 (vs 338)
... 83% of rev
LTM:
Revenue 259M +55%
Gross Margins 82%
Op Margin -22%
Last 6mo:
Revenue 142.0M +50% (vs 94.8M)
Revenue trends (last FY -> next 6mo):
- License 95% -> 44%
- Support 71% -> 46%
- Cloud 75% -> +373%
- Pro Svcs 65% -> 8%
Custs 2101
Custs >100K 558 (vs 419)
... 87% of rev
NRR 124%
This company is clearly in the midst of a shift. License & Support are slowing to mid-40%s. Their Cloud is now emerging off an extremely small base, growing +373%. The biggest criticism I have is how late to SaaS cloud managed services they are. These really only started contributing this year, so now comprise <5% of total revenue. But it looks like their focus on large enterprises is working – they now have over 300 of Global 2000 as customers, and enterprise custs (custs > 100K) contributed 87% of revenue, from 80% 6 mo ago. Revenue growth is dropping, while costs are heavily increasing, and customers aren't expanding as quickly as before. I remain on the sidelines to watch how they get their HCP Cloud services off the ground, and to see if operational leverage can start appearing.
Add'l Reading
Hashicorp is an incredibly open company, and I enjoy listening to the founders speak – especially CTO Armon Dagar, who has a knack for boiling down highly technical details via whiteboarding. I recommend these videos if you are curious to dive in more on their philosophy & stance, and have a lot of time on your hands.
Videos on their philosophy & history:
- What is the Tao of HashiCorp?, Jan-19 (mentioned in the last piece)
- How does HashiCorp think about solving problems?, Jan-19
- Origin story, Jan-19
Videos on their stance across DevOps & security:
- App Delivery, May-18
- Mutable vs immutable infrastructure, Nov-18
- Challenges & oppos in multi-cloud, Jun-19
- Why adopt multi-cloud?, Aug-19
- Zero Trust approach, Mar-21
This post was originally written in December 2021. Sign up for Premium if you want in-depth coverage of DevOps Tooling, Observability, Zero Trust & SASE Networks, Edge Networks, Data & Analytics, and Enterprise SaaS, including companies like Zscaler, Cloudflare, CrowdStrike, and Datadog.
- muji
PS If you are immersed in DevOps workflows and want to know more about these products for your own use, see these dives into how they work and the customer journeys over them (summarized above).
- Where to start in the HashiCorp stack?, Aug-19
- Crawl, walk, run with Terraform, Jul-18 or the similar Why Terraform enterprise?, Nov-18
- Crawl, walk, run with Vault, Nov-18
- Crawl,walk, run with Consul, Jun-19
- Intro to Nomad, Jul-18
- Intro to Boundary, Oct-20
- Intro to Waypoint, Oct-20
