CrowdStrike had its Fal.con annual conference for customers and partners in Vegas back in September. Let's take a look at what products and tidbits emerged.
I called my take of last year's Fal.con "A Security Cloud Emerges" [in premium] – a theme that continued this year. After watching the event's keynotes, product sessions, interviews, and investor day – I found that Fal.con held no surprises. Said a different way – CrowdStrike continues to move into the areas it has signaled and that I expected of it. It continues to bolster its CNAPP and identity capabilities (to catch up with where Palo Alto has gone in Prisma Cloud), is finally repositioning Humio as a part of its stack, and is adding capabilities that expand its platform into new areas like ASM (attack surface mgmt) and OT/IoT – including several new products/capabilities that are leveraging its new Asset Graph capabilities announced in June.
New Announcements
Before Fal.con, they announced:
- Falcon Long Term Repository was announced in Aug-22, rebranding the Humio for Falcon announced back in Jun-22. This leverages Humio as a way to retain Falcon EDR/XDR data longer, through the use of the Falcon Data Replicator (real-time stream of data out of Falcon for backup). They are positioning this as a replacement for data warehouses or SIEMs, to instead leverage Humio as a SIEM-like security data lake.
- They hired a new CMO in Sep-22, who was the CMO at Illumio (as well as a board member), and had previously worked at Tenable, Amplitude, and Tanium. Besides the detour to Amplitude, I like her heavy history in enterprise security SaaS platforms – both at Illumio (an SSE platform, aka a competitor to Zscaler & Netskope), as well as direct competitors Tenable (vulnerability mgmt, ASM, CSPM) and Tanium (EDR, network scanning, asset mgmt) – which all have major areas that CrowdStrike is moving into.
During Fal.con, they announced several products:
- Insight EDR has been shifted to Insight XDR – unlocking XDR for all customers, as a signal to enrich EDR from other layers (better detection through context). They also announced several major new CrowdXDR Alliance partners (Cisco, ForgeRock, Fortinet) and 3rd-party integrations (non-partners Microsoft and Palo Alto), and a deeper Zscaler integration. They are focusing XDR on being enriched from areas within the security stack like email, firewall, identity, NDR, and SSE (SWG, Zero Trust, and CASB) providers.
- Humio was renamed to Falcon LogScale, which also includes a new managed offering with LogScale Complete. This debuts a renewed focus in CrowdStrike on observability use cases, to use the existing Falcon agent in place to provide infrastructure monitoring.
- They announced 2 new releases of Falcon Discover, their "IT Hygiene" network scanner for monitoring and tracking assets, apps/services, and users across the enterprise network. Discover v2.0 has new enhancements including proactive remediation & recommendation features, and to track asset relationships. They also entered IoT protection with their new Discover for IoT, built for continuous tracking of OT and IoT devices in Industrial Control System (ICS) networks, and included a new partnership with Industrial IoT tracking & security platform Claroty.
- They announced new Cloud Identity Entitlement Mgmt (CIEM) capabilities in their Cloud Security module (CNAPP), to manage and secure user accounts & permissions in cloud resources. This supports tracking users & permissions across AWS (IAM) and Azure (Azure AD), and they stressed features like one-click simulations of remediation tactics (to easily test the impact of permission changes across the downstream assets that use that identity).
- They announced they are acquiring Reposify, an External Attack Surface Mgmt (EASM) platform, moving them into a market adjacency. This is akin to Palo Alto's Cortex XPANSE (from their acquisition of Expanse in Dec-20).
XDR is clearly the new focus – I wasn't sure why it debuted as a separate product from EDR, but I think their platform and approach are clearer now, and better exposed to upsell into their entire customer base. Humio was not being leveraged enough, and so LogScale and Long Term Repository are both moves in the right direction. CIEM, for tracking identities and permissions across cloud resources, was clearly missing from their CNAPP – a notable absence given their heavy focus on identity protection. Speaking of Identity Threat Protection, I expected new capabilities to be announced, but there wasn't anything new there.
They also announced multiple new partner initiatives and venture investments.
- An expanded service provider partner program for GSIs and MSPs, with a joint GTM in their Elite tier.
- They announced their partners of the year for 2022, which included AWS, Zscaler, and Deloitte.
- Announced a new partnership with cyber insurance provider Coalition, to provide Falcon Go (the new tier for SMBs) at a discount to their 160K policyholders.
- They made new Falcon Fund investments into Vanta (compliance automation) and Salt Security (continuous API security).
The new features show they are moving closer to all the competitors in areas they have been lacking.
- They are expanding their Cloud Security into a fully featured CNAPP, including their recently added "shift left" DevOps security capabilities and now adding a CIEM. This moves them closer to where Palo Alto is going with Prisma Cloud, which is the early leader in the space, per Forrester.
- They are adding an attack surface mgmt (ASM) module, a good pivot for them into ITOps with asset tracking (Discover) and vulnerability mgmt (Spotlight). This, combined with SOAR automation (Fusion), brings them closer to where Palo Alto has gone in Cortex (with XDR, XPANSE, and XSOAR).
- They are better leveraging their new data lake capabilities in LogScale, which aligns them to where SentinelOne has recently been going with DataSet, XDR Ingest, and Skylight.
As for the limits of the Security Cloud? The CEO stressed how they are not interested in shifting further into network protection (where partners Zscaler, Netskope, and Cloudflare lie), and how they aren't competing with Okta & PingID, but are instead augmenting it (leaving out that their product is circumventing analytical capabilities in those platforms).
What does all this mean? Let's dive in deeper.
Fal.con Overview
The event had quite a few overarching themes across keynotes and investor day:
- Proactive and automation are the new buzzwords being hyped up repeatedly, coming via Fusion SOAR, AI-driven recommendations, AI-driven IOAs (announced in Aug-22), asset relationship mapping (via AssetGraph announced in Jun-22), and behavioral analytics (XDR over it all).
- SecOps and ITOps are coming together, with a renewed focus on their product line for asset mgmt from several new features being unlocked by their new Asset Graph capabilities – and now greatly enhanced with their acquisition of Reposify for attack surface mgmt.
- Security combined with Observability is a new focus, after the (long-overdue) rebranding of Humio to LogScale.
- Cloud-native security & shift left are also clearly a huge focus.
There were a lot of event sponsors across cloud, security, and managed service partners, like AWS, Google, Cloudflare, KnowBe4, Mandiant, Mimecast, Netskope, Okta, Optiv, Proofpoint, ServiceNow, and Zscaler.

They hammered home their strengths: a single lightweight smart agent that acts as a data beacon, with an inline AI that allows the agent to be an "aperture" that can increase data collection when suspicious activity is detected. From there, data is sent to their cloud-native platform for crowdsourced analytics across their entire customer base – which allows them to operate at a massive scale. Their chief data scientist said in an interview that they currently process 2 trillion events per day!
They have 3 internal proprietary databases for this:
- Threat Graph, for tracking connections between events for crowdsourced threat & breach detection
- Intel Graph, for tracking relationships between adversaries (threat actors) & attacks (IOAs)
- Asset Graph, for tracking relationships & interactions between assets, identities, apps, and configs
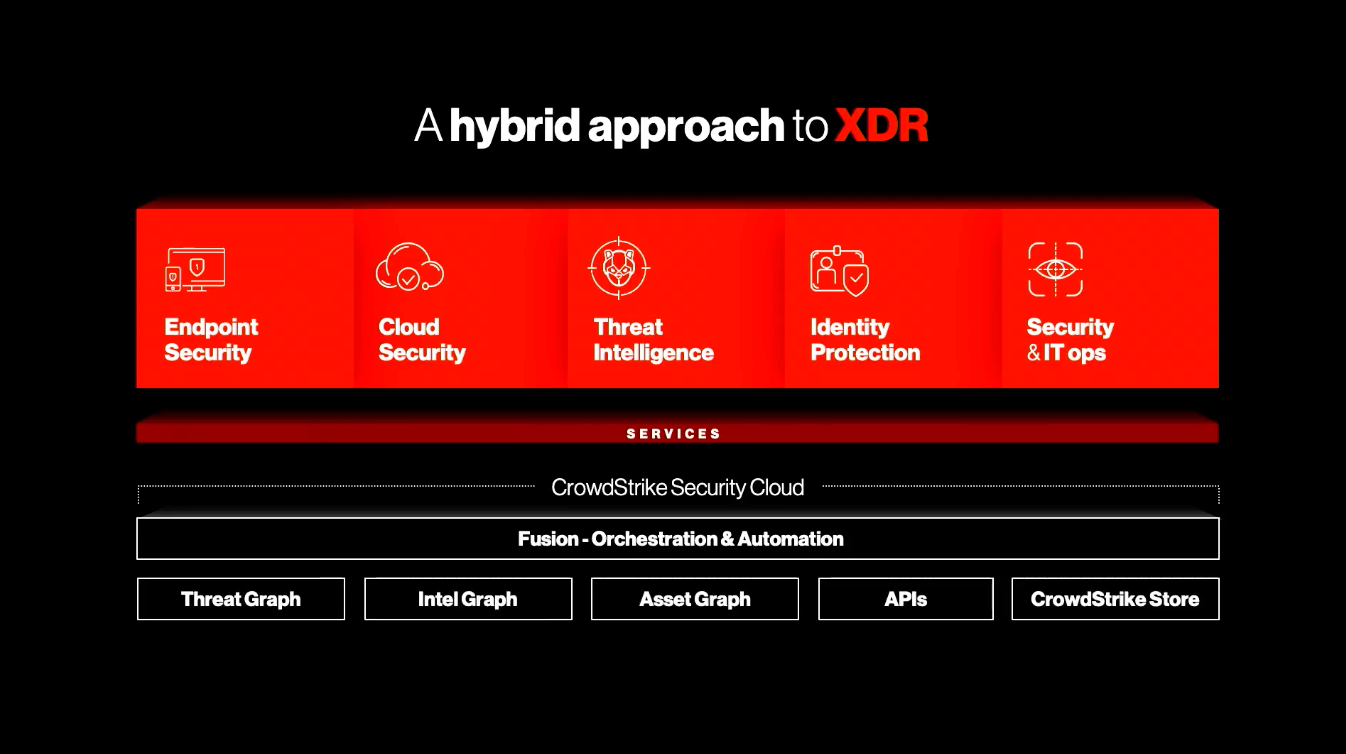
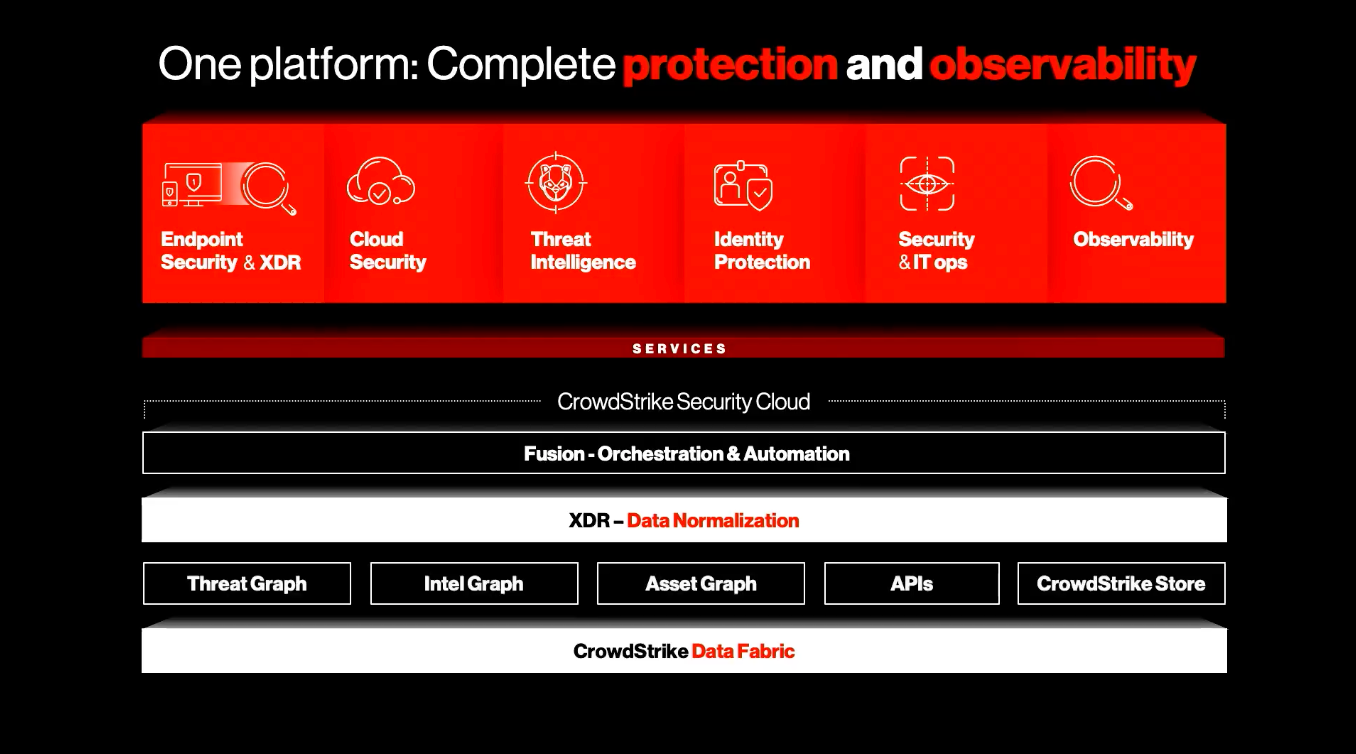
Mgmt focused on how their XDR provides data normalization from all sources, saving the data in a common schema – likely using the new OCSF schema from the industry partnership they joined in Aug-22 [discussed before in premium]. There wasn't much detail on what the "CrowdStrike Data Fabric" entails, other than the CPO saying it was the data ingestion layer underpinning the Security Cloud, with the CEO adding during investor day that the Data Fabric is leveraging LogScale for ingest, which is then processed into the graph databases.
Areas of Focus
Let's talk about a few areas I think are most important.
CNAPP Expanding & Shifting Left
I previously covered [in premium] the expansions of their Cloud Security product line. To catch up on a few past announcements that are highly relevant:
- In Apr-22, they rebranded their Cloud Security as a CNAPP platform, by tying together the two sides of their platform (CSPM and CWP), and bolstering the container capabilities like rogue container and drift detection (containers should not have configuration changes applied directly, only in their definition/creation).
- In Jun-22, they bolstered their CNAPP capabilities further by shifting left, expanding DevOp pipeline features like image repository scanning (for container vulnerabilities & misconfigs), and adding code-scanning features like Software Composition Analysis (SCA) to detect open-source libraries and scan them for known vulnerabilities.
- Beyond their previously added Cloud Workload Protection (CWP) Complete managed service added last Fal.con, back in Jun-22 they added OverWatch Cloud Threat Hunting as a managed service for human-driven threat detection over their Cloud Security line.
Cloud Security is clearly a focal point, allowing them to sell this into their Falcon customer base. Over all of this, they are stressing how they are providing both agent and agentless protection, giving them a view into the endpoint itself (host or container) as well as the cloud platform layer (via API) – but this is not that much of a differentiator, given that Prisma Cloud works this way as well. The big add at Fal.con was their new CIEM, which is not a surprise given their heavy focus on identity of late. Their "hands-on" services (Complete and OverWatch) are the one big differentiator for them currently. On that, I expect them to expand Complete into a managed service over all of their Cloud Security products (not just CWP, but CSPM and now CIEM), and for these managed services to get added to their GovCloud offerings (for Federal/State gov).
Unfortunately, I don't see much differentiation in product capabilities. They are chasing Palo Alto (Prisma Cloud) into this space, and I don't see them catching up to the market leader anytime soon. I expect them to continue to iterate on their shift-left capabilities to move further into CNAPP. (As discussed before, CNAPP is two-sided between infrastructure security and app code security.) There is still no sign of infrastructure-as-code (IaC) security scanning here, which is greatly needed and helps bridge the gap between those 2 sides of CNAPP. If they are going to focus on shift left, they need to greatly focus on code-scanning capabilities beyond their early attempts at SCA (open source vulnerabilities), as well as support other app stack environments beyond container-based ones. But let's be fair – this is a whole new market, and beyond long stale pockets of developer tools for code security, is entirely greenfield. I just want to see them take better advantage if they are moving this way. For now, Palo Alto and startups like Snyk seem to have much richer products on the shift left (code security) side. That said, mgmt mentioned they are protecting 1.5B ephemeral containers daily, so clearly these features are being heavily used!
XDR
At last year's Fal.con, they announced Falcon XDR and CrowdXDR Alliance to much fanfare [as discussed before in premium], but haven't had many announcements focused on this area since.
- In Dec-21, they expanded the CrowdXDR Alliance, including Cloudflare.
- In Jun-22, they again expanded the CrowdXDR Alliance and better integrated their Fusion SOAR into XDR workflows.
I thought they were saving up news on this front for Fal.con – and they were. They shifted their Insight EDR module to XDR (now in GA), to now open these capabilities up across all existing customers. They also expanded their CrowdXDR Alliance with major networking gear like Cisco and Fortinet, plus are adding their own 3rd-party integrations into competitors Microsoft 365 (email) and Palo Alto (firewall). To be clear, those latter ones are not partners in their Alliance – they are adding these integrations on their own, which they said would debut over the next few months. They also mentioned they had extended their already deep partnership with Zscaler. Zscaler's PR states it better enables Fusion SOAR to automate response for continuous adaptive access, plus adds additional Zscaler telemetry to XDR.

They are exposing these XDR integrations as "content packs" to upsell (which is a commonly used term in SIEMs like Splunk), and are focusing them in the areas of email, firewall, identity, network detection & response (NDR), and SSE (SWG, Zero Trust, and CASB). In the investor day Q&A, the CEO mentioned that content packs will be priced by domain (email, firewall, etc) and per node – with no additional ingestion fees (nor, I presume, storage fees). The new Long Term Repository capabilities open up longer retention capabilities here – a move that SentinelOne has made with its new DataSet.
From here, I expect more and more integrations, and mgmt mentioned how XDR will be integrating intel from their Identity Threat Protection, CSPM (Horizon in Cloud Security), and vulnerability mgmt (Spotlight) modules – plus, one assumes, their new ASM capabilities in Reposify.
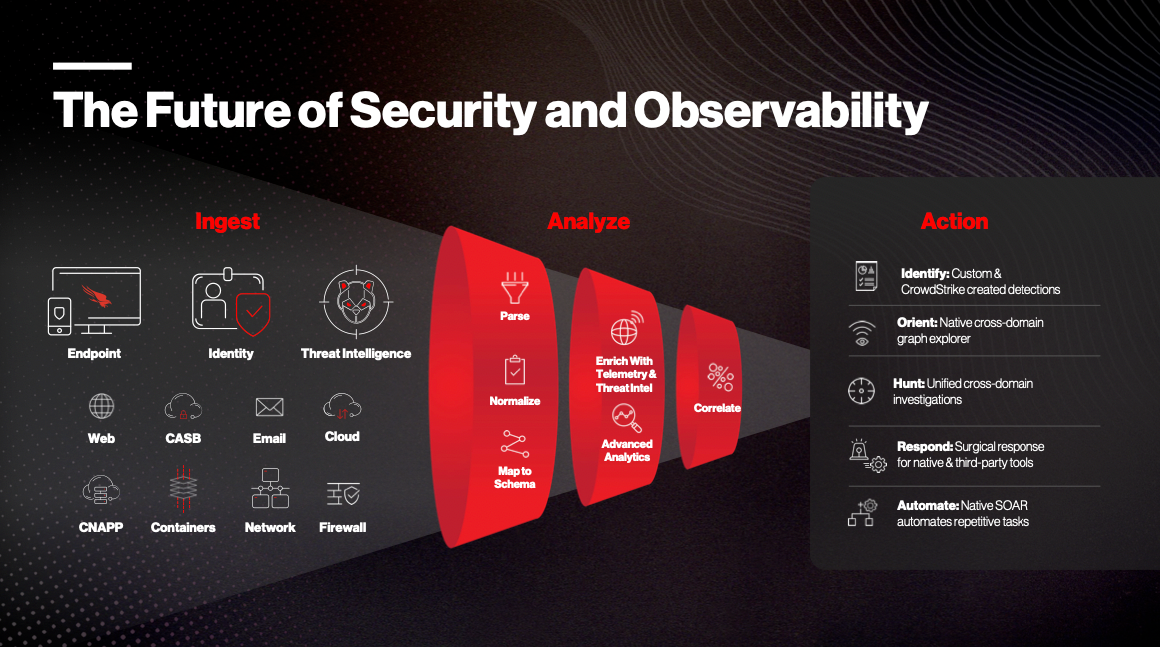
Asset Graph & IoT
They are heavily leveraging their new Asset Graph capabilities announced in June in many of the new products announced at Fal.con. I love to see their focus here, as it opens them into several new markets for ITOps. Asset Graph was used in:
- The new release of Falcon Discover 2.0 can provide a real-time continuous view of an organization's assets across its network, and the relationships between those assets across identities, configs, and apps upon them.
- Falcon Discover for IoT can provide a real-time continuous view of an organization's Industrial Control Systems (ICS) networks, over OT & IoT devices. In Q&A, the CTO stated it would release over the next month.
- Their new CIEM is for tracking and managing identities and permissions used across cloud resources – which leverages Asset Graph to tie the relationships together, and continuously track them in real-time (especially important in dynamic and ephemeral cloud environments).
All of these are backed by the new Asset Graph, which is used to track all the assets (servers, systems, laptops, devices, and now OT/IoT devices), identities, and apps – and all the relationships and patterns between them. The new Discovery capabilities are moving CrowdStrike into internal asset mgmt, and will tie closely into their vulnerability mgmt (Spotlight) capabilities from here. These changes are ultimately adding CAASM capabilities [more on that below].
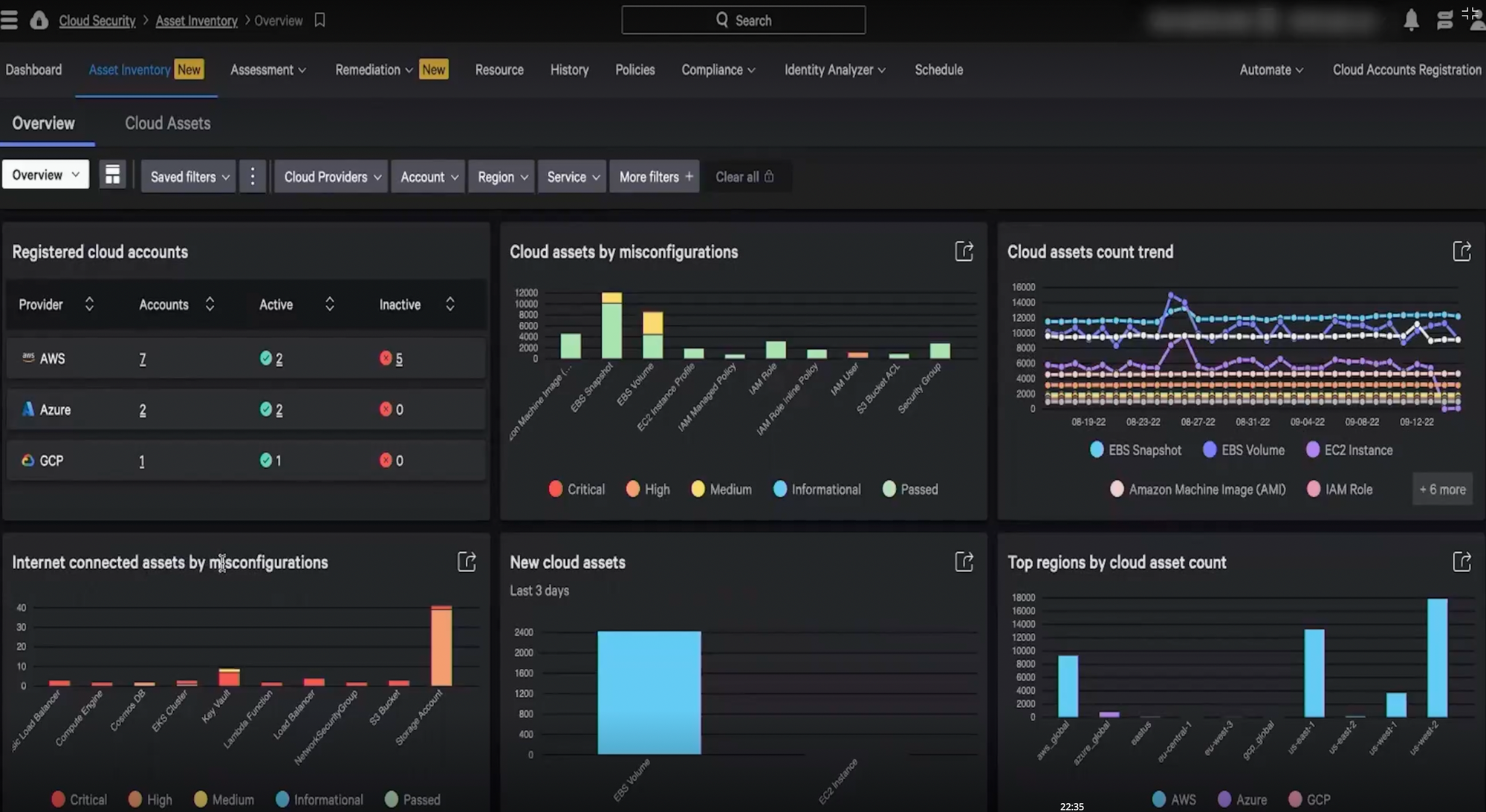
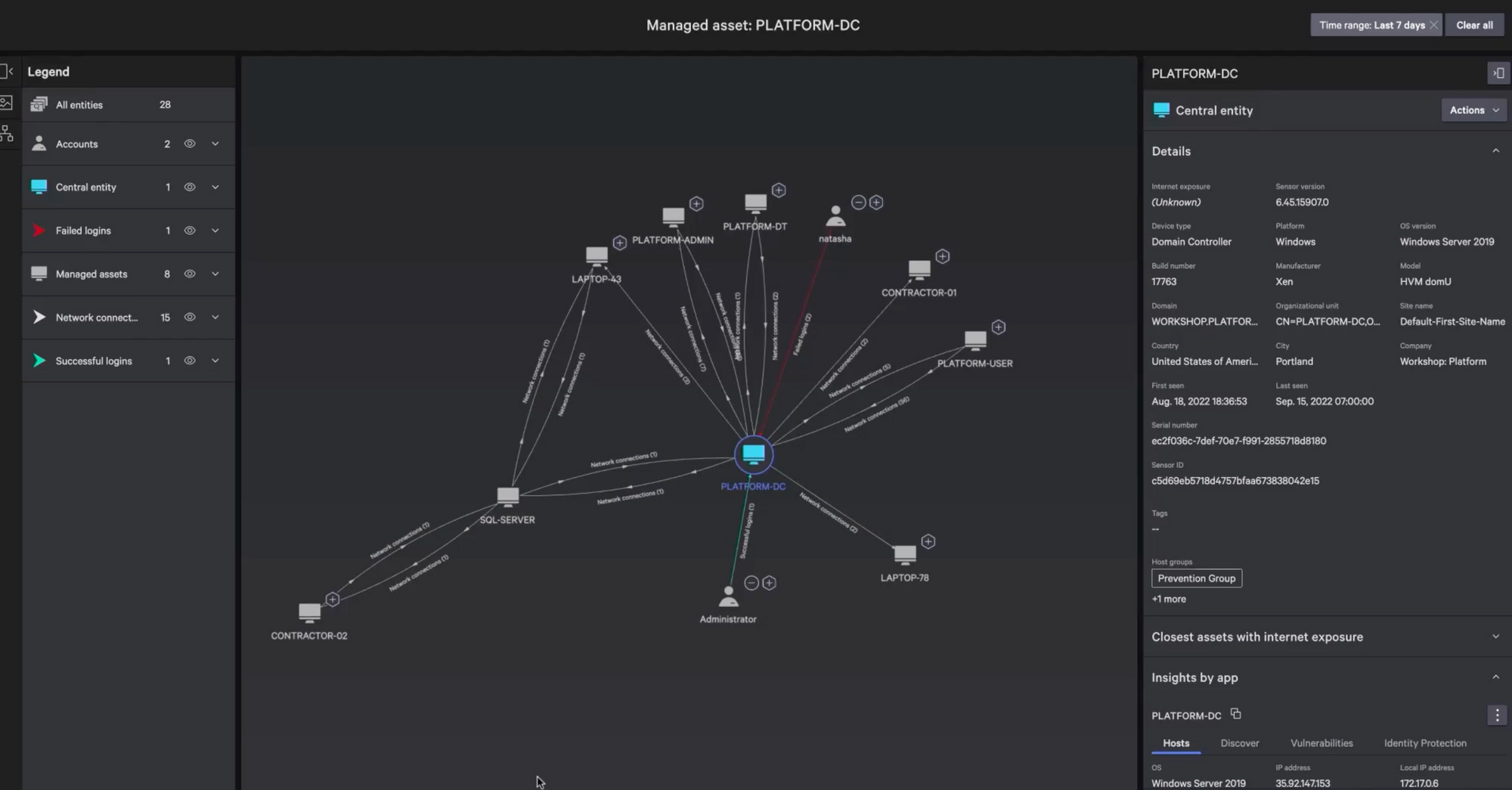
The shift into IoT is a welcome one. As I have mentioned before, it's a hard area for endpoint security to enter, given that OT/IoT devices that may not have an operating system (Windows or Linux) for an agent. Given this, I more expect networking-focused companies like Zscaler and Palo Alto to go this direction instead of endpoint-focused ones [and Cloudflare just announced during its Birthday Week in Sep-22 that they are moving this direction too]. For now, CrowdStrike is focused on visibility into industrial control system (ICS) networks, and can tie into popular ICS vendors via API to get the inventory of managed devices, plus can identify managed/unmanaged devices in network scanning. In an interview with TheCube, the VP of Global Alliances mentioned that it can tie via API into popular ICS systems now like Rockwell, Schneider, and Siemens. In a session demoing the IoT product, CrowdStrike mentioned that they are working with several ICS vendors to allow for an agent to be deployed, which include Rockwell (already done), Schneider, Siemens, ABB, Yokogawa, and Johnson Controls. Ultimately, it sounds like this will be the same Falcon agent but "industrialized" (specialized for ICS networks). So, like with CNAPP, their IoT security solution will ultimately be both agent and agentless (API-driven). On the downside, this means a lot of specialized dev work (time and resources) to adapt this industrialized agent to all these different OT/IoT systems, which may use custom ASIC chipsets. The VP of Global Alliances mentioned they will follow the customer demands on where to go with this.
Data Lakes & Observability
Humio has now been rebranded as LogScale. They have now fully integrated Humio into their platform, and per the CTO, have made several enhancements as they did so (though didn't get into details). This is specifically being branded as a log mgmt & observability platform, which can used as a security- or observability-focused data lake. In Q&A, the CEO mentioned that they now have the pieces (between XDR and log mgmt in LogScale) to completely disrupt cloud SIEMs, plus can then automate responses via SOAR (Fusion).
A few weeks earlier, CrowdStrike rebranded their Humio for Falcon as their new Long Term Repository product – akin to what SentinelOne provides in their Data Retention module. This is what allows for Falcon XDR data to be stored in the new LogScale product, which ultimately allows for LogScale to be used as a security data lake over contextual XDR data. Unlike SentinelOne & Scalyr, CrowdStrike is not replacing their entire underlying storage mechanism with Humio – their graph databases serve that purpose. LogScale is being leveraged for XDR ingest (as part of the newly branded "CrowdStrike Data Fabric") and for this new long-term retention capability.
Observability is now a much bigger focus. This is the same tact that SentinelOne has had in their DataSet product – though while SentinelOne is keeping DataSet "stand-alone" (while it also is providing their underlying data storage and analytical capabilities), CrowdStrike is keeping LogScale under the Falcon fold, adding a new Observability product line in their architecture chart (see above) and marketing. The CTO stated that they are focused on the "first 2 pillars of observability" of 5 — which perhaps showed their inexperience here. [Every one of the major observability platforms focuses on 3 pillars based on the source (metrics, logs, traces) – whereas CrowdStrike displayed a chart of 5 pillars based on intent (where, how, why...).] They are trying to compete with observability platforms like Datadog and Splunk on log mgmt (event collection) and infrastructure monitoring (metrics via agent), but likely have a ways to go before impacting those companies. For now, they will focus on leveraging the single Falcon agent to provide an observability data lake for log mgmt and infrastructure monitoring in LogScale – with the CTO hinting that they will continue to march into other capabilities over time (like, perhaps, APM traces?).
Bridging SecOps + ITOps
CrowdStrike has been heavily moving into IT-related capabilities in its Security & ITOps product line (which I'll abbreviate SecITOps), which includes Spotlight (vulnerability mgmt), Discover (network scanning and asset tracking), and Forensics (data handling for triage) modules. Also recall their new Exprt.AI system inside Spotlight announced last Fal.con, to use AI for risk scoring and prioritization over discovered vulnerabilities.
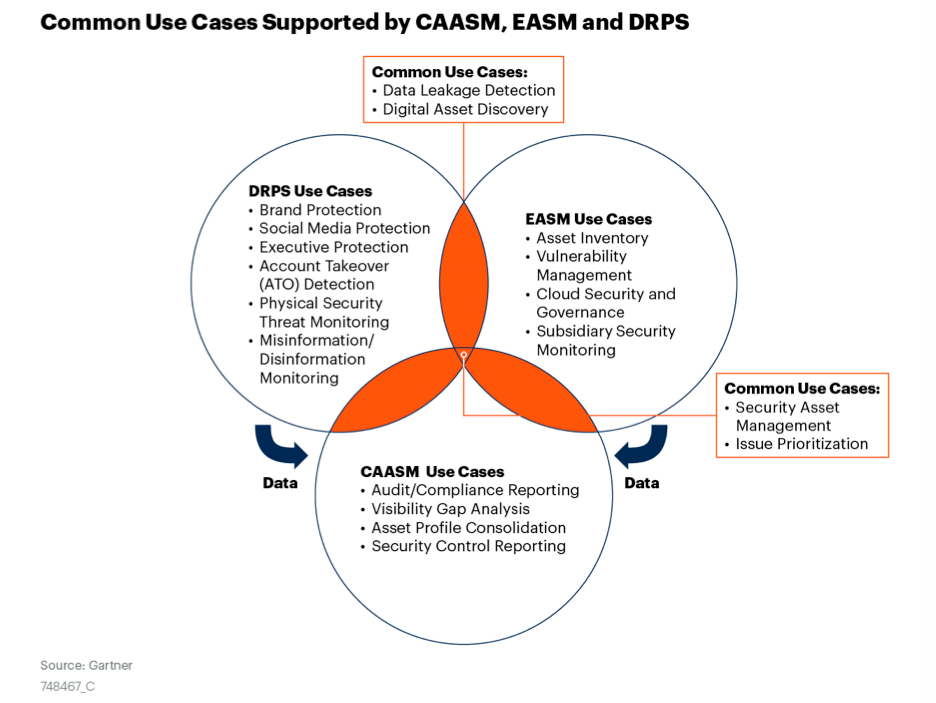
CrowdStrike is now showing several signs of moving into the hot Attack Surface Mgmt market, as expected [in premium]. If you are not familiar, Garter has a primer from Mar-22 – but, as typical, it gets bogged down in acronyms. Let's boil it down, and add some new entries to the Security Cheat Sheet [in premium].
- Vulnerability Mgmt = a scanning service to measure and monitor known vulnerabilities within the operating systems (OS) used across a pool of managed systems. This typically includes patch prioritization based on risk scoring, and can work over containers as well – which are not patched, but instead rebuilt from updated base images (newer patched version of the OS).
- External Attack Surface Mgmt (EASM, or just ASM) = a platform that continuously scans, tracks, and monitors all external-facing servers and services on an enterprise network. This is an outside-in service performed from the public Internet side to find vulnerabilities and exploitable security gaps (penetration testing).
- Cyber Asset Attack Surface Mgmt (CAASM) = a platform that helps an enterprise track and monitor over all of its known systems and services. It is typically built atop or integrates with an asset mgmt system (inventory of systems and services) and vulnerability mgmt system (tracking known vulnerabilities in system OSes), as well as EASM for the outside-in view.
- Digital Risk Protection Service (DRPS) = A service for measuring and monitoring digital risk of an enterprise's network and public exposure of external-facing assets. This is typically measured around specific operational objectives (not security ones), and can be especially useful during digital transformation projects that are moving systems and processes into the cloud. This would typically utilize other systems like EASM (attack surface mgmt) and vulnerability mgmt to measure risk via security scoring.
They just acquired Reposify for External ASM (EASM), an outside-in service that scans an enterprise's external networks for the Internet for known vulnerabilities or exploitable security gaps. They are based in Israel (the rumors were true), and, in investor day, the CEO mentioned all 20 employees were joining the Israeli R&D team (heavily kick-started before with their Preempt acquisition in Sep-20). Per their explainer page, Reposify tracks all publicly accessible systems, cloud services, domain names, SSL certificates, protocols/ports, operating systems, IoT devices, and network services across on-prem, cloud, hybrid, and 3rd-party supply chains. Mgmt states that Reposify has been mapping the Internet for the past 5 years, to now be one of the largest databases on publically accessible (Internet-facing) assets and associated attack vectors. Ultimately, this underlying feature backs their primary EASM platform, a service for zero-touch autonomous asset discovery & security scanning from the Internet to any exposed systems across an enterprise's network.
I really like the potential in this acquisition. In Q&A, the CEO said they always look at how other modules will benefit – and this one (like Preempt) is a huge winner in that regard. To start, Reposify will be a standalone module for EASM. From there, mgmt stated that its Internet mapping database would be joining their Threat Intel product line, which includes Falcon Intelligence (previously called Falcon X, their threat intel product line) and Recon (for dark web scanning). They are assuredly going to tie all these products together, as Reposify can enrich those products with its threat intel from spotted attack vectors, and vice versa. But beyond that, EASM is a security tool that integrates incredible well with those SecITOps tools mentioned above, with mgmt stating they will be leveraging its capabilities and intel heavily across Discover (asset mgmt) and Spotlight (vuln mgmt) going forward – and assuredly their XDR from there. From here, they can easily pivot the combination of these SecITOps products (Discover, Spotlight, and Reposify) into an overall CAASM as an ITOps tool that tracks assets and vulnerabilities across both internal and external assets, as well as one that can provide intel into best configurations needed in cloud resources in their CSPM (Horizon), and greatly bolster their new OT/IoT moves. They could also easily add DRPS services and better hone their products to focus further on compliance (already a focus of Horizon) and measurable risk reduction.
From Here
During investor day, the CEO mentioned "saying in our lane" and "focusing on areas we have advantage/view". He made clear they are most interested in leveraging their beachfront access (that single lightweight agent), which has already been exploited into ITOps (vuln mgmt, network scanning) and now identity. At various times, he ruled out moving toward Networking Security (SSE, Zero Trust, etc), being an identity provider (Okta), or being a Config Mgmt Database (CMDB).
Identity just getting started – though again, I was surprised it wasn't enhanced and at the forefront of the discussion. CNAPP is just getting started too, and I hope to see them get more serious about the DevOps side of the coin, by bolstering their code-scanning, CI/CD pipeline, and especially IaC features. IDC has mentioned 3 buying centers and feature sets for security tools in an org across App Dev, CISO, and Cloud SecOps – and App Dev is the side where CrowdStrike remains weakest.
LogScale is starting to be better utilized, and they mentioned expanding from log mgmt and infrastructure monitoring into other capabilities over time. IDC mentioned they don't see XDR replacing SIEM, but the CEO stressed in investor day how XDR plus LogScale positions them to do just that.
More data protection capabilities are clearly coming from their acquisition of SecureCircle [discussed before in the XDR series in premium] to secure data across the enterprise. The CTO mentioned they were integrating into their single agent, and it would be available "very very soon" (next few weeks). The CEO hinted that additional internal capabilities were being added, which I assume will feature data discovery and regulatory classification – and I wouldn't be surprised with more acquisitions in this direction. Both customers interviewed in their investor day panel signaled interest.
Customers/Partners/GTM
Mgmt mentioned having done 4700+ value assessments in sales pitches over time, which has lately evolved to now focus their pitch around agent & vendor consolidation, cost savings, and risk reduction. In his keynote, the CEO mentioned a major retail brand displaced 9 agents by consolidating on Falcon, saving an overall $5M savings across point product replacements (-$2M), operational savings from 5 less staff (-$2.5M), and a reduced cyber insurance premium (-$500K). It also resulted in a massive improvement in their risk posture, taking their SOCs incident response time from 8h to 5min!
There were a few customer tidbits from the CEO during investor day Q&A on customers and GTM that warrant a mention. One was that AWS is a Falcon Complete (MDR) customer – I'm guessing over their employee laptops, not their internal infrastructure (servers). They also mentioned how a customer moved to Spotlight from competitor Qualsys during Log4J remediation, given its accuracy at identifying the issue – it's good to see it moving into best-of-breed and displacing point products (bolstering their vendor consolidation pitch of late).
Last earnings, they reported a potential TAM of $126B in 2025. That has now been updated to now $158B in 2026, with the CEO stating offhandedly that Reposify is ~$1B of it. He also mentioned how their downmarket shift is bolstered by their new Falcon Go tier (announced on Reddit back in June), their new partnership with Coalition cyber insurance, and the intensified focus on MSP partners. But that same MSP focus is also allowing them to move further upmarket, as MSPs are being more and more utilized by large enterprises to augment their own internal SOC, due to heightened risk awareness and lack of talent. To highlight this, during a CISO panel during investor day, Texas Mutual's CISO talked about how he uses a multi-layer approach over endpoint protection – the first layer is Complete MDR (CrowdStrike staff managing EDR), a second layer via an MSSP (managed service for log review), then a final layer of their internal SOC (his staff). Certainly pricey, but seems a great way to consolidate agents, have overlapping security layers, and allow him to handle staff shortages by having his SOC team focus on the most impactful & important things.
Another oft-mentioned focus is on the lack of security talent (staff shortages). During the MSP partner panel during investor day, they all stressed how talent shortages have been very good for their service businesses. The WorldWideTech (WWT) SVP went into detail about how CrowdStrike beat out every other XDR platform in every one of their hands-on bake-offs for their sophisticated customers (which I took as meaning they have their own internal SOC), and had a great quote about "anyone who can tamp down noise and lead customers to insights will win". Long-time partner Optiv mentioned that after a slower May and June, net new business has heated up in August, making it the hottest month in history in both renewals and net new – which is continuing into September. Both Optiv and WWT confirmed that anything discretionary was going away, but not security – especially platforms that allow for cost savings & consolidation. As the Optiv CEO put it, you can defer security spending for a while, but that decision greatly increases risk.
Add'l Reading
As for Fal.con, the main keynotes weren't really that necessary to watch, providing little over what the PR of these new capabilities mentioned, beyond the tidbits interspersed above. The associated investor day wasn't that interesting either, as they muzzled their CFO (no talking financials!) to focus on product discussions – and merely reiterated all the same points from the PR and keynotes. However, I do recommend the customer (@ 1:32:04) and partner panels (@ 1:54:50) from the Chief Sales Officer to see how big customers and partners feel about CrowdStrike – which provided some details discussed above. (Too bad there was no Q&A for those groups – I guess that is the benefit of attending the event and investor day, where you can question these folks afterward.) Seagate mentioned using Falcon Complete and Identity, and being very interested in Data and ASM from here, while Texas Mutual was interested in LogScale, Identity, and Data – so good to see all these new areas immediately resonating with customers.
SiliconAngle had a Breaking Analysis before Fal.con that included some interesting ETR screenshots of spending intent, and their media arm, TheCube, was live streaming at the event. While the CEO/CTO/CPO interviews didn't provide much over their keynotes, I found their interviews with CrowdStrike's SVP Chief Data Scientist and VP of Global Alliances & Store most insightful. The data scientist gave an interesting view into the company's AI philosophies, stating he feels AI is a tool that augments and scales human decisions, which then allows them to operate at a massive scale (cloud-native) over more and more complex data relationships (XDR). The VP of Global Alliances, on the other hand, covered a lot of the why behind XDR alliances, and new products bridging SecOps with ITOps, and bridging IT with OT/IoT.
I explore hypergrowth companies within DevOps tools, observability, edge networks, data & analytics, and cybersecurity (Zero Trust, SASE, XDR, CNAPP). This was originally a post from my premium service from September. Sign up for Premium if you want weekly insights into hypergrowth tech companies and where they are going in their platforms and market pivots. I currently have in-depth research and heavy coverage over CrowdStrike, SentinelOne, Zscaler, Cloudflare, Snowflake, and Datadog.
If you sign up and want to catch up on CrowdStrike, here is the prior premium coverage that is relevant:
- A Security Cloud Emerges (Oct-21) looked at products announced at last year's Fal.con, like XDR and CrowdXDR Alliance.
- XDR series (Mar/Apr-22) was a multi-part series that explained how EPP/EDR platforms are evolving into XDR, and shifted into cloud protection, data lakes, and identity protection.
- The endpoint landscape (Jun-22) looked at Q1 earnings and new capabilities like Asset Graph, CNAPP, and Humio for Falcon.
- Federal Zero Trust series (Jul-22) was a multi-part series that updated the steps the US Federal Govt is taking with Zero Trust, and how CrowdStrike is winning all the EDR.
- XDR face-off (Sep-22) looked at Q2 earnings and new capabilities like CNAPP shift left and AI-powered IOAs.
CrowdStrike reports earnings tonight, with Zscaler on Thursday and SentinelOne next week.
- muji
