It has been a busy 2020 for Cloudflare. This company is my 2nd highest position (right behind CrowdStrike) as it sits at the nexus of two of the next-gen enterprise technology waves that I follow closely - Edge Networks and Zero Trust. Over the second half of 2020, it has had 4 different announcement weeks: Serverless Week, Birthday Week, Zero Trust Week, and Privacy & Compliance Week. They are continually moving forward at an incredibly rapid pace, and while these announcement weeks are great for seeing the product innovations, it also gives us outsiders a view into how these moves fit into the larger picture.
And whoooo-boy... were there a lot of announcements. So many that it may look like they are moving in too many directions, or seem scattered or are stretching themselves thin. But no - every advance Cloudflare makes is improving either their core platform (web protection and performance), or one of the key directions I am watching them move more fully into. Instead of going one-by-one through the new products and features, let's instead look at what Cloudflare had before, the key platform areas that I am watching as an investor, and how those areas advanced.
I'm going to be referencing their prior products heavily. Pop quiz: What is Magic Transit, Argo, WARP? You need to know... so let's recap their product lines & features stood (at the start of summer) before we explore the new enhancements.

Existing Platform
This is mostly a recap from my first deep dive back in February 2020, with a couple of additions and clarifications.
Core platform
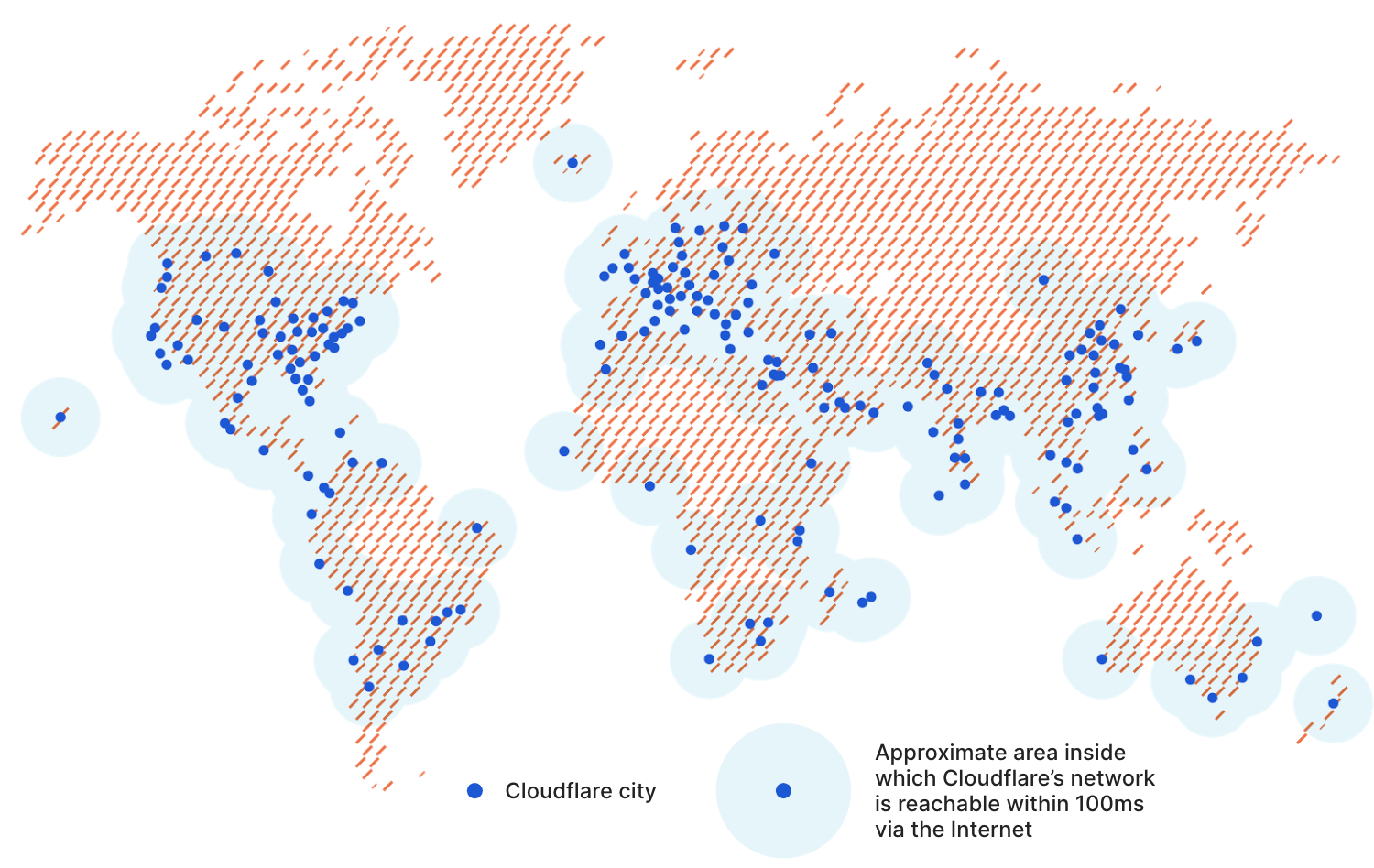
Cloudflare is an edge network, currently with 51Tb+ of global network capacity that is interconnecting with nearly 9000 outside networks (ISPs, cloud providers, internet exchanges, and customers). Their edge network is generally accessed via 200 Points of Presence (POPs), strategically situated across 100 countries – putting the vast majority of the world within 100ms of their edge. They handle 18M+ web requests per second on average, hitting 25M+ protected web sites and services -- which means they typically handle ~1.5 trillion web requests a day. The insights gained from handling all that traffic then powers a threat intel system that protects the edge network and its customers, which blocks an average of 72B cyberthreats a day.
Behind the core architecture of their platform is:
- Software Defined Networking = Cloudflare architected their global network and backbones to be software-based, which allows for their entire edge network to be programmable. [Covered before in my Edge Networks write up.]
- Local Edge Routing ("Anycast") = Allows for incoming requests to the edge network to be routed to different locations; any edge server, instead of one origin server. This is what allows CDNs and edge networks to be a proxy, and provide an umbrella of services by sitting over all requests to origin servers.
- Global Private Backbone ("Argo") = Their private network backbones between major interconnects, which all combine into their global edge network. This allows them to efficiently monitor global network conditions, and to achieve higher speeds by routing traffic globally across those private backbones instead of over the public Internet (using Argo Smart Routing - see below).
- Global Anycast Network = Their mesh of global networks and backbones, with 200+ edge servers across the globe serving as gateways into that network. [You can see the list of POP cities in the link.]
Their edge network sits between a company's applications (web sites, web apps, or mobile apps) or services (APIs, microservices, or serverless), and the users making requests to them. Being a proxy between a service and the users accessing it has a lot of advantages, and the primary focus of Cloudflare over its first 10 years has been around 3 pillars: improving the Security, Performance and Reliability of their customers' web applications and services.
Security
Cloudflare is known mostly for its security features. Security over your web applications and services remains critical! Some tidbits from a recent technical blog post looking at attack trends: DDoS attacks are surging in 2020, and for the past 3 quarters, the number of attacks have doubled each of those quarters.
- Web Application Firewall (WAF) = A proactive next-gen firewall over your web application. Uses threat intelligence (ML & signature recognition) and customizable rules to block suspicious traffic.
- DDoS Protection = Ensure performance of your web app or service, by making sure only legitimate traffic is hitting it. Prevents denial of service and concurrent bot attacks.
- Bot Management = Stop automated bots in real-time, tracking both good or bad actors. Prevents common attack vectors, like application DDoS and content scraping.
- Rate Limiting = Once traffic gets in through the WAF, provides rate limiting capabilities over your application, to curb application DDoS attacks, brute-force login attempts, and other abusive behaviors from "legitimate" requests.
- SSL = Provides SSL/HTTPS capabilities over your web application or service.
- Spectrum = Extends these core security features to work with non-web protocols (email, FTP, SSH, MQTT, or any specialized TCP/UDP traffic, like game protocols).
- Cloudflare for Campaigns = Free service protecting local, state and federal US political campaigns from attack (via DDoS and WAF).
Performance
Besides being a security layer, being the proxy between web services and end users also allows Cloudflare to help improve the performance of the application being called, so that it is as fast as possible. This is primarily through caching and optimization of content.
- Content Delivery Network (CDN) = Caching static content for faster delivery and greatly reduced trips to origin server.
- Web Optimization = Compressing content & images for faster delivery. Automatically encode images to a variety of formats, allowing for right-sizing of images by tailoring it to the device it is viewed on (phone vs tablet vs web).
- Stream (Video Optimization & Delivery) = Compresses video for faster delivery and caches it to CDN. Automatically encodes to a variety of formats, allowing for right-sizing of video, to tailor to device it is viewed on (phone vs tablet vs web). Allows for limiting access based on geo-location, user or time-based rules.
Reliability
And hand-in-hand with performance of your application comes the reliability of the entire network between a service and its users, to assure it is always available. Cloudflare provides an array of services to bolster the resilience of your site, and make sure the network there is always at the ready.
- Argo Smart Routing = Route optimization system to determine fastest route for web requests to origin. Detects real-time congestion via ML, and routes around it; think of it as the "Waze for the Internet". Finds the fastest & most reliable routes over both the edge network backbone (Argo) and the overall Internet.
- Load Balancing = Allows for routing incoming Anycast requests to different origin servers, or have failover should a server go down. Allows for geo-steering, to assure certain regions of users hit a particular server.
- Managed DNS = Fast, secure and resilient Domain Name Service (DNS, the lookup that routes URLs to the network IP that serves it). Built to be highly redundant, with built-in DDoS & spoof protection.
Consumers
Besides their core enterprise platform, they have several consumer-facing applications.... and like their enterprise platform, it has very generous options at the free tier. In particular, it is important to understand their WARP-line of products, which is a VPN that protects the endpoint's traffic to the nearest edge server.
- 1.1.1.1 = Free & fast open DNS resolution service for consumers (the lookup to determine what IP to route a web request to). Similar to what Google provides as their Public DNS server at 8.8.8.8. [This blog post covered the history of DNS and its issues, if you want to understand DNS better.]
- 1.1.1.1 for Families = Family-friendly public DNS resolution servers for use on home routers, for malware and adult content blocking.
- 1.1.1.1 + WARP = Free consumer VPN app for mobile (iOS and Android), and, as of this year, Mac and Windows desktop. Beyond using the 1.1.1.1 DNS service, it is a VPN that protects the network traffic between your device and the nearest edge server.
- WARP+ = Paid consumer VPN service in the 1.1.1.1 app, that extends WARP by adding in Argo Smart Routing over Cloudflare's private backbones, to achieve higher speeds on web requests (30% faster on average), and gain overall better performance & reliability. This leverages their enterprise-focused edge network towards consumer use.
Their consumer products don't provide revenue (they are free or low-cost), but provide clues as to where their enterprise products can go, plus assuredly provides a lot of intel in their routing & threat detection analytics happening over network traffic.
Connectivity
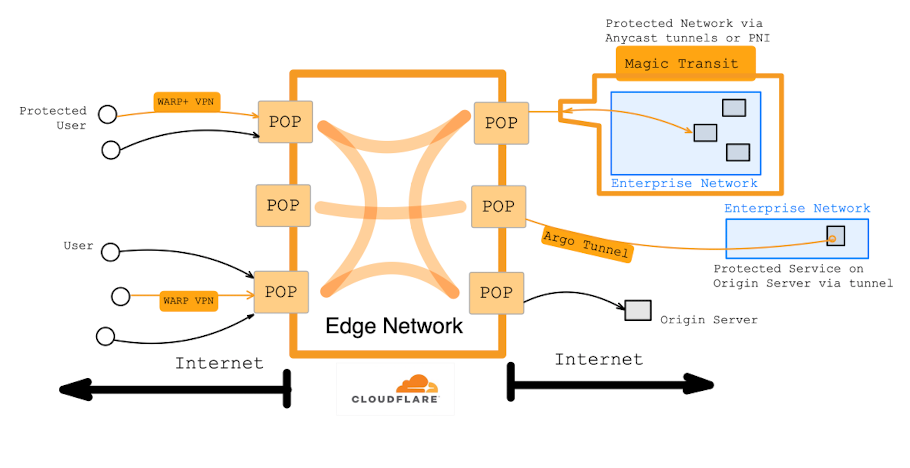
All of these are the enterprise flip-side of those consumer services - they protect the traffic between a company's enterprise network or specific origin servers to the nearest edge server.
- Argo Tunnel = Secure tunneling for the edge to connect to individual web apps and services. It is a lightweight agent that runs on an origin server, creating a tunnel to the nearest edge server, so traffic can route in through Cloudflare's application security -- to then take advantage of WAF, DDoS protection, rate limiting, load balancing, etc. The request and response speeds are improved via Argo Smart Routing over their private backbones. [The agent is called "cloudflared", with the "d" for daemon (a service running the background). But it must be fun to say your service is "cloud-flared".]
- Private Network Interface (PNI) = Network interconnect to an enterprise's network, via an interconnect partner (Data Center) or Internet exchange (IX). This is essentially a direct link to the edge network, so the traffic is not going over the public Internet.
- Magic Transit = Extends the edge network into your office or data center, to bring Cloudflare's platform directly onto the enterprise network – whether at an HQ, branches, or data centers. This is where Cloudflare's platform started to pivot from application protection to network protection. Uses a private connection between the nearest edge server and the enterprise network, in order to become an umbrella over your enterprise network, giving your network all the security and reliability features Cloudflare covers like DDoS, WAF, Teams, and even Workers. Can be enabled over a dedicated tunnel or a PNI.
An enterprise and set of consumers might connect to the edge network like this (with orange being protected by Cloudflare, black being over public Internet):
Edge Developer Platform
- Workers = Edge compute platform, allowing developers to deploy serverless functions to run on edge servers. Allows logic decisions at the edge nearest the endpoint making the request, resulting in a much lower latency than services in core cloud or on-prem (possibly only one hop from the user's ISP).
- Workers KV = Distributed edge key-value store to use with Workers, for simple data storage & caching.
A lot of the excitement about Edge Networks is wrapped into the potential of using Edge Compute as a development platform, and the possibilities that will open up within this new paradigm. But advances here are not only expanding what customers are capable of building, but also what Cloudflare can build upon itself.
Edge networks like $FSLY $NET will enable next-gen solutions for IoT, fleet/asset/infra/network tracking, smart buildings/appliances, 5G, AR/VR, smart networks, device/app/vehicle AI and voice recognition, regional compliance and distributed analytics ... /1
— muji @ hhhypergrowth (@hhhypergrowth) October 8, 2020
Enterprise Security
Cloudflare recently pivoted their platform to include an entirely different security focus; what started as application protection (WAF, DDoS) shifted to include enterprise traffic protection (SWG, Zero Trust) as well. Cloudflare for Teams was announced in January 2020, with two products to protect both sides of enterprise traffic -- protecting enterprise users' outgoing requests to SaaS tools (SWG), as well as their incoming requests to internal services (Zero Trust), regardless of whether those enterprise users are on-premise or remote. [As I have mentioned often, this product line is akin to Zscaler platform's ZIA & ZPA products. If you aren't up on Zscaler, or on terms like Zero Trust or SWG, read my extensive Flavors of Security series from a year ago.]
- Gateway = Secure web gateway (SWG) that protects enterprise users' traffic to remote SaaS tools.
- Access = Secure connection tool to allow enterprise users access into internal services via Zero Trust.
This new product line (and assuredly every new product line from Cloudflare going forward) was developed entirely on Workers edge compute. The fact they pivoted into protecting enterprise networks gives you a glimpse at the potential of edge compute over a programmable global edge network.
Key Directions to Watch
As I have mentioned numerous times, thinking of Cloudflare as just a service protecting your web app, or, worse, as just a CDN, is not a complete picture. They are an edge network that is capable of all those products, and much, much more. From the letter from the founders on Cloudflare's 10th birthday:
"Today we secure the Internet end-to-end — from companies’ infrastructure to individuals seeking a faster, more secure, more private connection. Our programmable, global network is at the core of everything we have been able to achieve so far."
Demand is strong for their core features (application protection, performance, and reliability), but all the other CDN players also provide these same features. These core features are vital, of course, and got them to where they are today, and so they must continue to innovate and enhance the features here. However, the excitement with Cloudflare (and my investment thesis) lies in their future paths as an edge development platform, and in how they interconnect with enterprises in order to become a next-gen enterprise network.
- Edge compute over their programmable edge network (expanding developer platform): Workers, their serverless edge compute platform, will be beneficial both for them (the continued expansion of their platform's product lines), as well as what their cutting edge customers are building over these capabilities. It competes against Fastly, as well as several other smaller players like Netlify. Cloudflare has a huge head start against Fastly (who still isn't in GA production), but I don't want them getting comfortable - I want to see new development features, architectural improvements, and continued adoption by developers and customers.
- Extending edge outward to become the enterprise backbone (expanding connectivity): They have been expanding their edge to the endpoints and origin servers at either end of a request, in order to lessen the exposure of traffic to the public Internet. Between the WARP consumer VPN, the enterprise connectivity options, and now the Cloudflare for Teams products, Cloudflare is protecting not only inside the edge network, but also outside its borders -- from the edge to either the endpoints (consumers or enterprise users) or the origin servers (services they are talking to). Cloudflare is also now interconnecting more directly with enterprise networks (PNI) and protecting them (Magic Transit), so I want to see them moving more towards having their edge network become the backbone of an enterprise's network. Advancements here make them a more sticky platform by better securing all of Cloudflare features – but especially enterprise security!
- Securing enterprise users and traffic (expanding enterprise security): This is the most recent pivot in their platform; not only securing public traffic to web applications and services, but also securing all traffic from the users (either on-premise or remote) within that enterprise. They are now positioning their edge network to enhance or even replace an enterprise's network, in order to secure all outgoing traffic by enterprise users, and all incoming traffic to the internal applications and services within the enterprise's network (in data centers or cloud). A primary competitor here is Zscaler, however I see Cloudflare as being well positioned – it is easier to implement (especially piece-meal, Zscaler seems more an "all or nothing" choice for the C-suite to make), and I like how Cloudflare already covers application protection for a huge number of existing customers (free and paid) that they can tap into (sales funnel) for more advanced security needs. I want to see a heavy focus here in making this a turn-key platform for enterprise security, and how they integrate this with their existing platform and interconnectivity options.
New Features
Cloudflare's many "announcement weeks" lead to some major shifts & enhancements in those 3 areas just mentioned. Beyond those areas, Cloudflare continues on its general motto of "helping build a better Internet" with a few new products that deserve highlighting as well. [Links are to the blog posts announcing it.]
Expanding Developer Platform
Workers is the edge compute service that enables logic at the edge, which can then control custom behaviors across that programmable global edge network. We learned a lot about where this development platform is going during Serverless Week, and then the biggest point of interest came later during Birthday Week.
To kick off Serverless Week, Cloudflare CEO Matthew Prince gave us his vision for what matters to enterprises using edge compute, with the lessons learned over the 2.5 years since Workers was released into production. After those valuable years of being in use by customers, he found that speed is not the primary differentiator, contrary to what Fastly is so heavily focused on. [Reminder - Fastly is still struggling to take their edge compute development platform into full production (GA aka "generally available"). They initially announced it 2 years ago as "Terrarium", went to beta a year ago as Compute@Edge, then finally released it into production this past Halloween – but only in private "limited availability" that filled up instantly.]
"Only a limited set of applications are sensitive to network latency of a few hundred milliseconds. That's not to say under the model of a modern major serverless platform network latency doesn't matter, it's just that the applications that require that extra performance are niche."
Certainly speed is a consideration -- but Cloudflare has discovered from its customers that the order of importance seems more to be Compliance, Ease of Use, Consistency, Cost, then Speed. They are continuing to build developer tools around Workers that are focused on those key points. They are making continual enhancements to the dev tools for debugging & deploying apps, and are expanding the languages supported. Workers is out solving real problems over the last 2.5 years it has been in production, and is driving a growing use of the Cloudflare platform.
- 20% of customers have adopted Workers.
- 25k new developers deployed an app last Q.
- 10% of all requests across edge network are Workers.
Workers Enhancements
Customers were finding the compute and memory caps over their serverless apps to be limiting, so Cloudflare announced Workers Unbound. This introduces a higher pricing tier for Workers, with more of a usage-based pricing model. This allows for uncapped compute/memory limits, so that the function can be more resource intensive (higher compute and memory usage) or longer running (up to 15 minutes). The prior capped version of Workers has been rebranded as "Workers Bundled". I expect Workers to now start contributing more to the top line with the usage-based higher pricing now available.
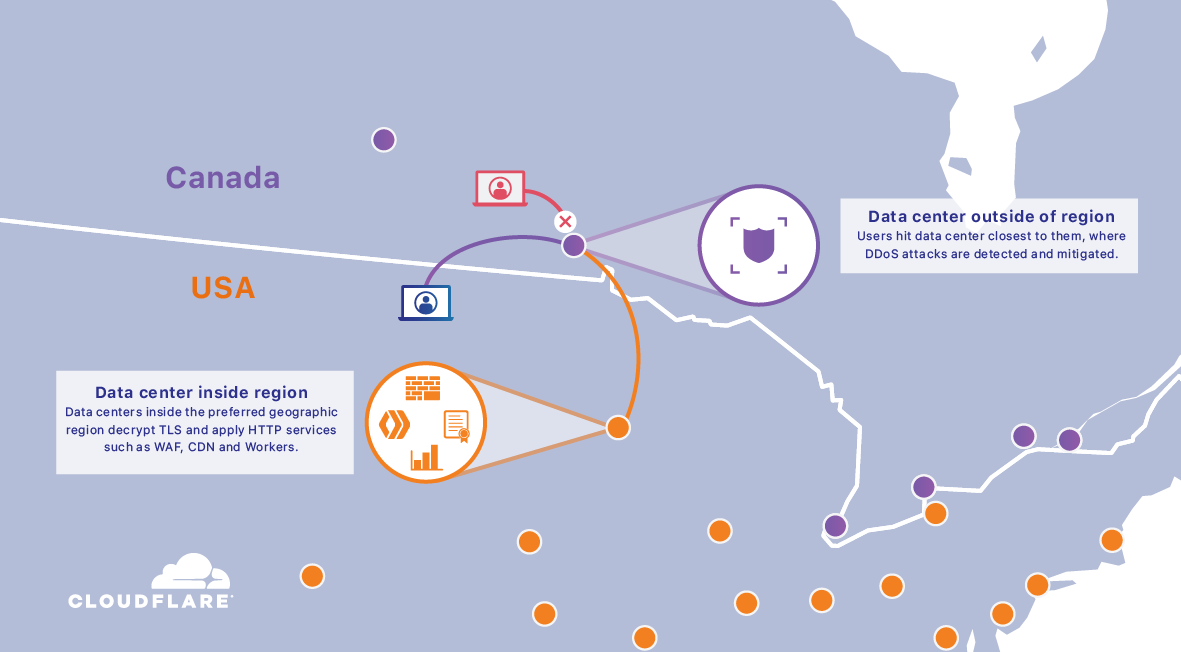
The top consideration from the CEO above was on compliance. A globally distributed platform needs to assure compliance with local/regional regulations, and the Cloudflare platform is compliant with all of the major ones (like GDPR, PCI DSS, FedRAMP, SOC 1/2/3, HIPPA). This matters greatly to global companies (banks, fintech, insurance, health care, logistics) that span multiple regions, each with their own laws and regulations to adhere to. And now, many regions and countries are starting to enforce data sovereignty, where data must reside inside the region. EU, India, Brazil are all moving this direction, plus China, Indonesia, Russia, and Vietnam are now adding more restrictive data laws. Edge networks span ALL of these countries!
So it was little surprise when Regional Services was then announced, which allows users to geo-fence Workers requests to certain regions (stay in the EU for GDPR) or countries (forcing requests to be routed to US POP even if a Canadian POP is the closest edge server hit), as well as being able to prevent access to users outside of those regions if needed. This allows apps to better handle regional or local restrictions, such as encryption restrictions or financial regulations. The way it works is that external traffic would still access the edge network via the closest POP (giving fast low latency connection to the edge network, and DDoS protection), but then, internally, the edge network redirects the traffic (via Argo backbone) to a edge server inside the specified region, for all operations after edge entry (like decryption, WAF, CDN, Workers). There are 2 pre-configured regions to start - US and EU.
Even after Serverless Week was over, the changes kept on coming, with the biggest feature appearing during Birthday Week. I had guessed an edge database was on the horizon, but I was apparently thinking small. Durable Objects in Workers brings us a fundamental change in how to think about serverless. It enhances Workers with stateful objects. This is way more impactful than the “edge db” I was guessing was on the horizon.
Instead of having a shared, multi-tenant database that lives on the edge (like Workers KV), Durable Objects are a different type of Worker instance that can be created to share data between any number of other Worker instances (the application functions). These shared objects act as in-memory storage and logic controller, created to act as a miniature database that is dedicated to a specific purpose, group or user -- holding just the data that group of users or Workers need. This allows for multiple simultaneous requests to all be sharing and acting upon and changing that same data. Think of it as a shared spreadsheet or document that the other Worker instances can call and use, with those Workers then controlling what user requests can access each particular document. “Durable” (or "stateful") means the object remembers (persists) its data between requests, which the Worker instance stores in-memory. And if that Worker instance must sleep (due to lack of activity), it persists the data to Workers KV. Once it is needed again, the Durable Object will reinstantiate and repopulate its data from KV, picking up right where it left off.
"Durable Objects provide a truly serverless approach to storage and state: consistent, low-latency, distributed, yet effortless to maintain and scale. They also provide an easy way to coordinate between clients, whether it be users in a particular chat room, editors of a particular document, or IoT devices in a particular smart home. Durable Objects are the missing piece in the Workers stack that makes it possible for whole applications to run entirely on the edge, with no centralized "origin" server at all."
This is flipping “serverless” on its head a bit, as serverless functions & microservices are all about enabling and scaling “stateless” requests (each request is self-contained, so nothing is remembered from request to request), while data is typically then persisted elsewhere, outside of the serverless environment (a cloud-hosted database, for instance). This is now keeping the data side-by-side with the application on the edge -- you aren’t storing it in a separate database or API layer elsewhere. Now add in the scale and portability and geo-locationality you get from edge compute within edge networks. This feature greatly increases the sheer scale of what is possible with serverless.
It might be difficult to truly understand the potential here if you aren't a modern developer, so let's step back a bit. Workers are serverless functions, pieces of your API broken out into individual functions that are running in the edge. Your serverless functions can now spin up countless data objects when and where they need them, as usage demands – all still in the edge. So you have 2 different types of Workers - application instances vs data instances, with either being able to scale as needed. Worker instances can be either keeping their data objects private to just themselves, inter-exchanging data with other Worker instances, or ultimately relaying that data off into some centralized storage (out in core cloud) where needed. Each Worker instance can be shut down when idle, and can recreate itself again later on demand. Worker data objects could be moved from POP to POP, or region to region. This is cutting edge stuff from a development platform. [And, being in the business, I tip my hat to the software architecture team that designed & implemented this.]
The easiest way to see its potential is in tracking pockets of intercommunication or shared data between small pockets of users. Some potential use cases:
- Video sharing/broadcasting, where each shared feed or event or webinar is its own Durable Object instance. Zoom (or an edge-based competitor!) could spin up endless serverless instances to each serve up, maintain the metadata, and manage access to that meeting's video feed, geolocated across the edge to be as near to the users accessing it.
- Communal gaming or gambling where each match is its own shared Durable Object instance. Matches could be spun up and down as played, running on nearest edge to the globally situated users, or could be region-bound in the area they are legally restricted to operate in (EU or US). Skillz, a company that recently went public via a SPAC, (or an edge-based competitor!) could spin up game match instances, and have it manage user access and game coordination data. DraftKings (or an edge-based competitor!) could be creating objects to track the shared data for each separate betting pool, or separate instances could be created to manage each individual online poker match in their casino.
- Collaborative editing (documents) or chat rooms as separate Worker instances that are being edited or exchanged in real-time, in its own edge compute instances apart from others. Every user could be accessing an application that would be talking to a core set of Worker functions (the API), that in turn would be creating an endless number of Durable Objects to manage each shared document or chat room it manages – all happening directly on the nearest edge server to the users, or over the Argo backbone if users are scattered globally.
Those are just a glimpse at the potential. Any Workers developer could spin up millions of shared stateful objects across the globe, each representing a separate database or document or game match or video conference or webinar or chat room. This greatly changes how software developers can approach developing on edge compute. I am excited to see this play out from here, especially paired with the power of the underlying programmable edge network. Edge compute is now developing its own feature set, with a very different purpose than what core cloud gives you with serverless and networking, which is sure to enable some incredible next-gen capabilities. I predicted they'd release a "distributed edge database" -- but Durable Objects seems much more potent and exciting then I imagined. For now, it is in private beta, and pricing is not yet clear.
Speaking of edge data, Fastly hinted at a Data@Edge product line in their latest Altitude conference, coming some time in the future. The description seemed more like a distributed edge database than what Durable Objects ended up being (separate Workers instances for sharing data). We'll see what path Fastly goes, if and when it finally arrives. [Reminder: Compute@Edge still not publicly available after nearly 2 years of working on it, and Security@Edge was bolted on via an acquisition.]
Two months later, in Privacy & Compliance Week, Cloudflare extended Durable Objects even further, announcing Jurisdictional Restrictions. With the recent Regional Services feature, Worker instances can be geo-bound to certain regions. It now also applies to Durable Objects, to bind the storage and processing of data to a certain region (initially EU to start, clearly for GDPR restrictions). This will help developers comply with regional data regulations, and help them adapt their applications into new regions [once Cloudflare adds more].
Another enhancement to Workers was allowing Cron Triggers for Scheduled Workers. This allows a developer to run a given Worker app on a scheduled basis, such as for running periodic jobs at fixed intervals (update API lookups, bulk export data, refresh caches, do maintenance, etc). It is tracked in a core Cloudflare API, which then distributes the schedule to an edge service that triggers and runs the Worker. A new workload distribution system was created to evaluate the current state of the edge, and then distributes schedules between POPs.
"Cron Triggers gave us the opportunity to finally recognize a new Worker 'type' in our API. While Workers currently only run on web requests, we have lots of ideas for the future of edge computing that aren’t strictly tied to HTTP requests and responses. Expect to see even more new handlers in the future ..."
Global Reach
With Workers, Workers KV, Unbound (usage-based) Workers, Durable Objects and Cron Jobs -- combined with the power of the global programmable edge network it all runs across, and now the geo-fencing of instances for regulatory reasons -- there are a lot of ways to utilize this platform. This is the future of software development needing global reach and low latency.
Later during Privacy & Compliance week, they wrapped up a lot of their new compliance-oriented features into the Data Localization Suite. This allows enterprises more control over what regions their encryption keys, applications, logs and data operate in, tying together related features from their core platform (SSL certificate mgmt, edge logging) and Workers (Regional Services, Jurisdictional Restrictions). This reinforces how they are trying to make their edge development platform more appealing to global enterprises, and allow them to more easily adhere to regional restrictions like GDPR in the EU.
Features built over Workers
All those direct new enhancements to the Workers platform are geared for developers to build APIs and services upon their serverless platform – what is known in the app dev world as the back-end side of the application. However, Cloudflare is also improving the experience of running web sites and applications from the edge as well, by building new product lines on top of the Workers platform that are geared for front-end developers & website operators. These are tools that use Workers to serve up static and dynamic web content directly from the edge.
Cloudflare first announced it is making publishing and blogging platforms way faster with its new Automatic Platform Optimization (APO) tool. This creates a direct integration of publishing platforms into Cloudflare's edge network. The first supported platform is WordPress, which happens to power nearly 39% of websites today. [Unfortunately, not this blog!] Built over Workers and Workers KV, APO intelligently caches dynamic content at the edge, greatly improving web site speed, and nearly eliminating origin lookups; dynamic content is entirely served from the edge -- a single hop from most ISPs, instead of having to pull it from an origin server. This competes with any number of web hosting companies that have WordPress hosting features.
They then announced a similar product called Cloudflare Pages, that is instead focused on website developers. It allows front-end developers & website operators to build and host JAMstack-based front-end websites entirely from the edge. JAMstack is an increasingly popular development architecture that is lighter-weight & more nimble than traditional web applications, and is one that is perfectly aligned with the architecture of edge networks. Front-end HTML web pages and Javascript code are hosted on a CDN, while back-end services that it calls are handled by outside services (like external APIs or serverless functions). While Pages currently only covers static web sites & applications for now, they are going to be converging it more closely with the Workers platform, in order to serve up dynamic app content as well (where the front-end is calling a back-end API for dynamic data). Ultimately, Pages will be the developer platform for front-end apps and web sites, and Workers will be the developer platform for back-end APIs and services.
With both the back- and the front-end running on Workers, entire application stacks will now be easy to run completely within the edge (no origin servers or core cloud needed). For now, it is in beta, and the release may have been rushed after an intrepid web developer discovered it on their platform and docs earlier this month. Pages will compete with other popular edge-based front-end developer platforms like Netlify and Vercel, and it seems sure that Fastly will be following suit with something similar (they have mentioned JAMstack APIs as a use case of Compute@Edge).
Cloudflare didn't stop there. A few days later, they announced the acquisition of Linc, a startup focused on deploying web applications to edge-based serverless platforms. Linc has improved upon the traditional build and deployment process (the CI/CD pipeline) for both static and dynamic front-end web apps, so this helps Cloudflare Workers stand out with unique features over the edge-dev competition. [An edge developer of a SaaS service had a good take if you want the technical details of what makes Linc's offering stand out from Netlify or Vercel, and how this greatly strengthens Cloudflare Pages.]
It is good to see Cloudflare leveraging their Workers platform to make these more "out of the box" tools like APO and Pages, which both greatly expand usage of Workers, without requiring every web developer or operator benefiting from Workers be a serverless programmer.
Expanding Connectivity
Cloudflare has taken to calling its edge network the "orange cloud", while outside the network is the "gray cloud" (aka the public Internet). It wants to extend that orange cloud out past its current edges as much as possible [an orange fog?], to reduce or remove the gray entirely between the edge network and its enterprise customers. Cloudflare continues to focus on interconnectivity with enterprise networks, which not only creates stickiness with its customers and extends its platform's reach, but it also better connects enterprises to the next wave of product lines around enterprise security (Zero Trust) and edge compute (Workers & Pages serving up content).
To further blur the edge, Cloudflare now allows you to Bring Your Own IP (BYOIP). Your IP can now be available across the Anycast edge network, and is protected as if it was within it. It can be used with any application security products like WAF & CDN, as well as with Spectrum (non-HTTP protocols) and Magic Transit (within your protected enterprise network), where it can help to simplify firewall management, allowing a company to get rid of legacy network appliances.
The biggest news on connectivity is their announcement about Cloudflare Network Interconnects (CNI). They are streamlining the ability to directly interconnect HQ, branch and data center networks directly to the edge network. This type of direct link is inherently more secure, as you are bypassing the public Internet for that leg of the traffic (company network to the nearest edge server). Direct CNI connections boost security, performance, and reliability, plus allows enterprise networks to better interconnect with Cloudflare's platform for features like Teams, Magic Transit, and Workers. Global companies can connect branch & remote locations to the nearest POP or partner network, so the edge network can now become their corporate network. CNI enhances Magic Transit and BYOIP by completely removing public Internet from the equation, greatly reducing threat exposure; all incoming traffic to your services and IPs are first exposed to Cloudflare, then filtered and sent on to the customer's network. CNI greatly enhances the enterprise security in Cloudflare for Teams, by providing a direct connection to the edge network, so all outgoing (SWG) and incoming (Zero Trust) user traffic initially hits the edge instead of initially routing across the public Internet.
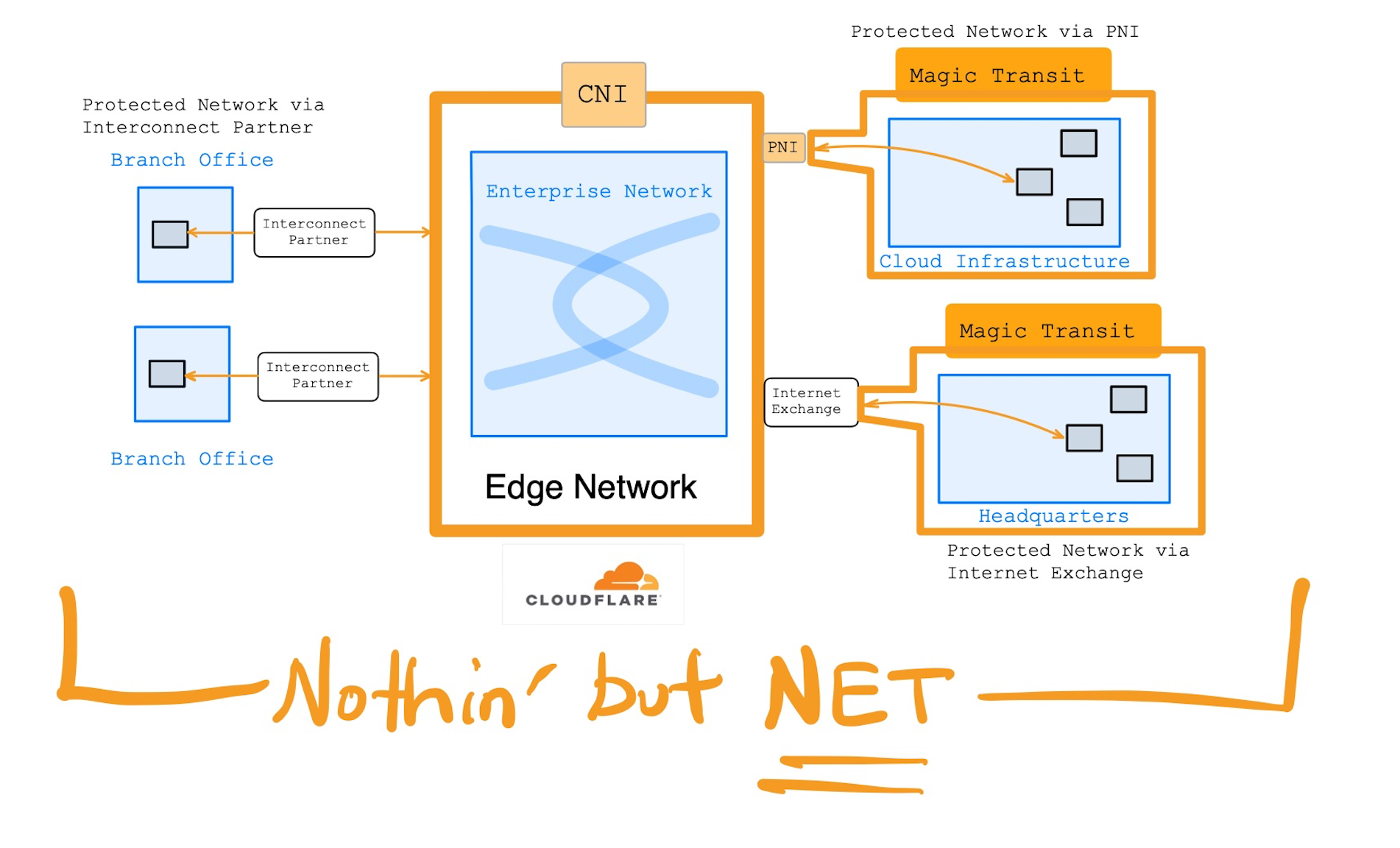
But if not using direct network connections, Cloudflare also made several Argo Tunnel enhancements. One agent can now create multiple tunnels from a single origin server (one tunnel per app). The security of the tunnels are now greatly enhanced by BYOIP, which prevents end-running around DNS (directly referencing the origin IP instead of the URL); all requests hitting that service must now come in from Cloudflare. They also improved it to make it more resilient to restarts and connection failures, and extended the tunnel to protect Remote Desktop traffic (especially helpful when paired with Access Zero Trust).
Cloudflare $NET:
— muji @ hhhypergrowth (@hhhypergrowth) October 12, 2020
ALL YOUR NETWORKS ARE BELONG TO US pic.twitter.com/FnS3IJ7co2
Cloudflare clearly wants ALL the network hooked in, as it continues to make it easier and easier to interconnect an enterprise's separate locations into its edge platform. These moves greatly improve the security of entry points into and out of each location, by reducing the public Internet exposure as much as possible. They are angling to become a vital backbone for enterprise networks. Cloudflare wants to be an enterprise's "network within a network". Which leads us then into securing the traffic upon that enterprise network....
Expanding Enterprise Security
Both of the above areas of interest (Workers and Connectivity) enable and strengthen Enterprise Security (Cloudflare for Teams). The most exciting week of announcements was Zero Trust Week, which brought us a huge number of enhancements in enterprise security, as well as a much clearer vision into what Cloudflare is trying to move towards.
Cloudflare One
The biggest news is that Cloudflare for Teams is now a major part of new product line dubbed Cloudflare One. Last February, I ended my first Cloudflare deep dive by stating that there were 2 halves of Cloudflare now, the core platform vs Teams. Those halves are now combined into one whole; it is now a single platform for enterprise networking and security management. They are merging enterprise traffic protection from Teams (the combination of Gateway and Access) with all the application and networking security features already present in the Cloudflare platform (Magic Transit, WAF, DDoS protection, load balancing, rate limiting, etc), to now be one complete solution for all your enterprise networks' security needs. Their new focus is to be a Secure Access Security Edge (SASE) platform, to help customers corral all enterprise traffic, whether from public users (application protection from their core platform) or from private users (enterprise users in Teams). [SASE, pronounced "sassy", is basically Zero Trust over a programmable software-defined network, focused on protecting outgoing and incoming traffic.]
"Rather than trying to build more private networks, the "corporate network of the future" leverages the Internet but with heightened security, performance, and reliability."
This means using their edge network as the corporate network backbone, turning their platform into a secure, optimized global "secure enterprise network-as-a-service" solution. It can replace a patchwork of appliances and WAN infrastructure, so that, like Zscaler, it makes the edge network the new enterprise software-defined WAN. They are taking their existing application protection features in their core platform, adding in the enterprise traffic protection features from Teams, and then unifying this all over the enterprise network interconnectivity from CNI and Magic Transit.
"Whether you call this SASE or simply the new reality, today’s enterprise needs flexibility at every layer of the network and application stack. ... And the new corporate network needs to be global. No matter where applications are hosted, or employees reside, connectivity needs to be secure and fast. With Cloudflare’s massive global presence, traffic is secured, routed, and filtered over an optimized backbone that uses real time Internet intelligence to protect against the latest threats and route traffic around bad Internet weather and outages.
However, you’re only as strong as your weakest link. It doesn’t matter how secure your network is if you allow the wrong people access, or your end user’s devices are compromised. That is why we’re incredibly excited to announce that Cloudflare One takes the power of Cloudflare’s network and combines it with best-of-breed identity management and device integrity to create a complete solution that encompasses the entire corporate network of today and tomorrow."
A huge factor in Zero Trust & SASE is the need for establishing Identity (is the person who they say they are, and what rights do they have across the enterprise's services) and Device Posture (integrity of the device making the request, and its known state by the enterprise). Cloudflare One has a number of partnerships to integrate these features.
- Partners for Identity (IDaaS): Okta, PingID, OneLogin, Microsoft Active Directory, Google Workspace. Can be one or more simultaneously, in order to have different blocks of users.
"... the identity provider issues passports and Cloudflare One is the border agent that checks that they're valid. At any particular moment, different passports from different providers may be allowed or forbidden to enter just by updating the instructions the border agent follows."
- Partners for Device Posture (EPP/EDR): CrowdStrike, VMWare CarbonBlack, SentinelOne, Tanium. [To start with, they noted more coming.]
"Extending the border control analogy, it's like having a temperature screening and COVID-19 test when you enter a country. Even if you have a valid passport, if you're not healthy then you will be turned away. By partnering with the leading identity and device integrity providers, Cloudflare One provides a robust identity and access management solution that fully delivers on the promise of Zero Trust."
They have combined all the pieces of their platform into an all-in-one security solution for enterprise traffic, and, like the other top names in SASE & Zero Trust, are leveraging partners for the pieces of the puzzle already done well by others (identity and device tracking). [As I have surmised before... over the last year, they have pivoted their platform to bolt on Zscaler's TAM and more. Exactly the kind of platform pivot I love to see!]
There are two types of products in the Cloudflare One platform:
- On-ramps that connect users, devices, or locations to the edge (using WARP, Magic Transit, CNI, Argo Smart Routing, etc). [This highlights why I focus on Connectivity enhancements as an area to watch. Connectivity options are covered more deeply in this blog post.]
- Filters that shield networks & application services from attacks, inspect traffic and apply Zero Trust rules (using Access, Gateway, Magic Firewall, WAF, API Shield, DDoS protection, etc).
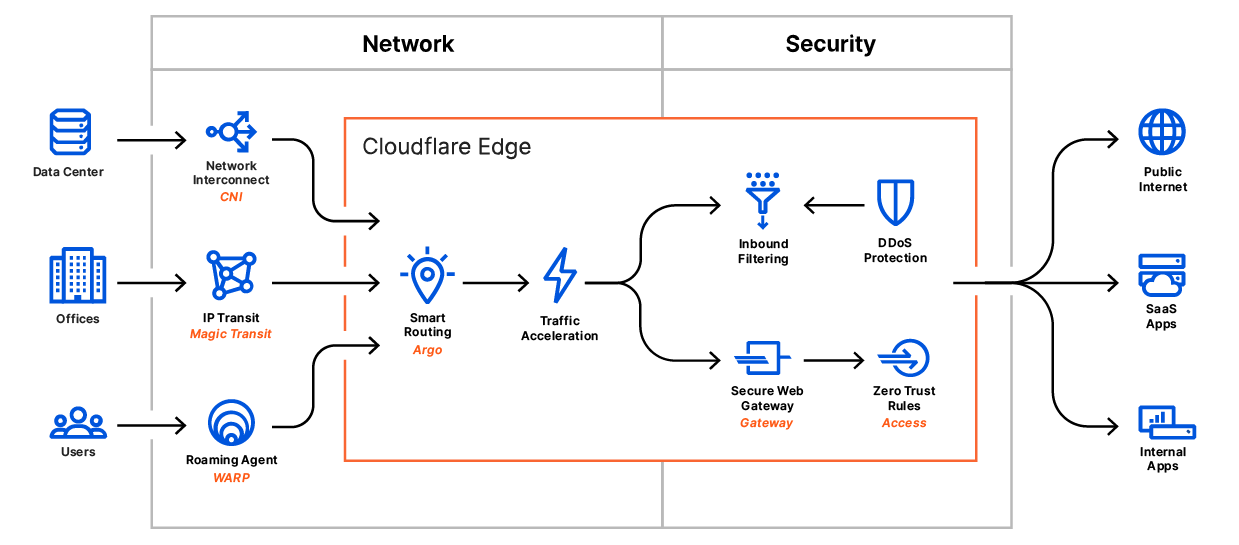
Their customer strategy with Cloudflare One is:
- Comprehensive enough for enterprises, but easy enough to be used by any team.
- Unified solution for all network traffic that is simpler and gives better vision & security. Plug in one or more providers for identity and device security.
- Fixed-rate pricing, that will be cheaper than other cloud-native solutions built on public cloud. Plus (as they love to do), they added a very generous free tier for up to 50 users or for initial try-outs.
- Global reach - 95% of the globe is within 100ms of the 200 POPs controlling the border of their edge network.
Cloudflare One is the culmination of how their vision has taken all the right steps over the years towards this lofty goal, and how the architecture of their platform (a global programmable edge network, combined with Workers edge compute) is allowing them to innovate so rapidly and to implement these additional features so quickly. And this is just their use of their own development platform -- imagine what customers will do! Besides Cloudflare One, a huge number of product announcements and enhancements also came out... which again showcase the amazing pace this team is keeping.
Security Enhancements
The existing Magic Transit product allows firewall rules to control what can exit and enter your enterprise network, but it is currently a very manual process (which require getting support involved). So they added Magic Firewall, a new next-gen firewall (NGFW) over it, to better protect all enterprise networks (offices, data centers, cloud). This allows IT admins to set firewall policies for all traffic entering or leaving the enterprise network. Magic Firewall runs entirely in the edge network, so it replaces legacy firewall appliances, with the scale of the cloud. No more capacity limits (# of users, # of connections), no more chokepoints (network bottlenecks). The first version, coming over next few months in limited beta, will allow simple static rules over your entire network, and only ties into Magic Transit and Gateway.
This is just the start of what they plan on adding into Magic Firewall. It will be integrated fully into Cloudflare One, applying the same rules over all access methods. It will eventually add more advanced policies based on traffic type, and be deeply integrated with other product lines for their firewall needs. Both Magic Transit and Magic Firewall are getting APIs exposed, so these products are becoming programmable building blocks that enterprises can use to better interconnect the pieces of their enterprise network. (The benefits of that software-driven programmable edge network cropping up again!)
A new product in the application security side, API Shield, is a new client-cert (SSL) and schema validation system for better securing back-end API traffic (whether it is Workers-based, serverless, cloud, or on-premise). This new feature assures only legitimate clients can connect based on behavior & identity (must have a valid client SSL cert, and the request payload must adhere to a specified schema), instead of solely relying on WAF rules & threat intel. Good to see Cloudflare continuing to iterate on protecting enterprise API and application traffic (as the competition is focused on this too) -- and they signaled there is more to come. [Fastly recently added a lot of application protection features with their Signal Sciences acquisition, including API protection. This acquisition not only brought Fastly up to par with Cloudflare on application security (WAF, DDoS, bot protection, rate limiting), but went beyond them with features like Run-time Application Self-Protection (RASP).]
Gateway Enhancements
Gateway, the Secure Web Gateway (SWG) product for an enterprise's users, protects their outgoing traffic as they go through the edge network to SaaS providers on the public Internet. As discussed earlier, Cloudflare's consumer WARP product line can protect traffic from device to edge, so they are extending Gateway with WARP+, for more network security & performance from desktop & mobile devices. WARP+ now adds a VPN (tunnel from the endpoint to the edge network), and uses Argo Smart Routing to pick the fastest route to the destination. This showcases how Cloudflare keeps moving so quickly with their enhancements – they are taking their consumer VPN (which has been in production now for 1.5 years) and are now using it as the new foundation for securing connections for enterprise users as well. This extends the protection of the edge to the enterprise user's device, removing any exposure to the public Internet between that user and the edge network.
Gateway is also upgrading security by integrating with the newly announced Magic Firewall, where enterprise IT admins can set policies to block requests based on rules (by destination, file type, or request type). Going forward, Cloudflare will continue to expand these security and admin rule features within Gateway and Magic Firewall, to allow things like finer grained control of user roles (via split tunnels, to allow a certain set of users to go to sites that others cannot), and improved support for BYOD (turning Gateway+WARP off and on to switch between personal or business use).
Then Gateway got a major security upgrade from there, by adding in Browser Isolation features that were acquired from S3 Networks back in January. [Zscaler did the same last year, acquiring Appsulate in mid-2019, to put into ZIA.] For web requests made within Gateway, the edge becomes the browser, which requests the page from the edge then sends a fully rendered "safe copy" of the page to the user's browser. This greatly minimizes the user's exposure to malware, as threats do not reach the user - they remain in the sandbox environment.
It isn't brand new technology, but what is new here is using the edge for this feature. Traditionally, browser isolation products run in a VM in the core cloud, and have been extremely slow in how they stream the final page to the end device (pushing pixels to render the page), made even worse when having to interact with the page (such as entering text). Cloudflare's solution runs the browser sessions in sandboxed environments within the edge network, milliseconds away from vast majority of the globe. The browser constructs the web page entirely in the edge sandbox, and only the final render is sent to user -- sped up by sending draw commands (a vector stream) instead of individual pixels. Think of it as a photo snapshot, but interactive, delivered at low-latency, and responsive. It is fully HTML5 compliant (works in any modern browser) and scales to any display size. It is not scrubbing the HTML or acting as a firewall (with rules about what it passes) – it is simply acting as a protective layer over that web page, that the user can see and interact with it in a highly responsive way, without getting sent any of the threats that could be lurking within. The edge network seems a much better location for this kind of functionality than core cloud; being vector-based means it is compact, being edge-based means it is FAST. This was a fantastic acquisition by Cloudflare. As mentioned, Zscaler ZIA already has browser isolation features too, but Cloudflare claims that theirs is better & faster, by being vector-based instead of pixel-based – meaning it has to transmit only a fraction of data to fully render the page.
Browsers are one of the least controlled softwares in an enterprise, exacerbated by mobile devices & BYOD (both personal & office use) – it is much too easy to unintentionally download malware onto your enterprise device, so it is always high in the list of attack vectors. This feature powers the next generation in Secure Web Gateways; SWG stops known threats, Browser Isolation stops unknown threats. This feature might seem like a threat to CrowdStrike at first blush, but this is traffic protection over just the web requests, not full device protection. The browser is but one way malware can enter the device, so it is not protecting the device as fully as an EPP agent does (which also protects against threats from mobile apps, emails, text messages, shared network drives, attached usb drives, etc). While it does protect against a major attack vector (browsing the web), this only benefits EPP, as it is one less threat vector into the device. Consider it one more "layer of the onion" in protection.
Access Enhancements
On the other side of Teams, Access also got a major facelift, with one of the more intriguing product enhancements announced during Zero Trust Week. Thus far, Access (like other Zero Trust products, such as Zscaler ZPA and Okta Access Gateway) has been solely focused on providing Zero Trust access into exposed services that are internal to the enterprise's network. So typically, Zero Trust is for allowing enterprises granular control over who can access the APIs and services that they have exposed internally in their own networks (cloud or on-premise). Access has now been extended to provide Zero Trust over ALL services an enterprise user might use. Not just internal ones, but also every external SaaS service utilized can also be protected by Zero Trust.
This is different than what Gateway already provides – this is about controlling access to these resources to specific users via Zero Trust, whereas SWG is about being a firewall over the network traffic, once access is granted. The key with this new change is that Access can now be managing ALL user rights, as a single point of access for both SaaS & internal services. Admins can also tie in other authentication rules, like restricting country the user is accessing it from (say, only be able to log in from the US).
This is a major enhancement that feels like Cloudflare just took a big step into Okta's lane, as well as differentiated their Zero Trust capabilities over Zscaler ZPA. They are angling to be a Single Sign-On (SSO) for Zero Trust, over every internal or external (SaaS) service your enterprise uses. This is NOT eliminating Okta – Cloudflare One will always work with them (and a wide variety of other identity providers) to establish a user's identity in the authentication process. But after relying on Okta for that, Cloudflare One can then take over the authorization process, allowing access to any of the enterprise's services from there. This would circumvent Okta's SSO (not to mention Okta's own Zero Trust feature, Access Gateway).
Cloudflare is also partnering with EPP providers like CrowdStrike for device posture (what and where is the device being used), like Okta and Zscaler do for their own Zero Trust capabilities. To see how this major enhancement changes the Zero Trust landscape, let's review this diagram from the recent partnership announced earlier this year between Okta (IDaaS), CrowdStrike (EPP), and Netskope (SWG) -- ignoring Proofpoint (the human side, aka educating your users) for now. [CrowdStrike and Zscaler have a similar partnership too, so Zscaler ZIA could be in place of Netskope.]
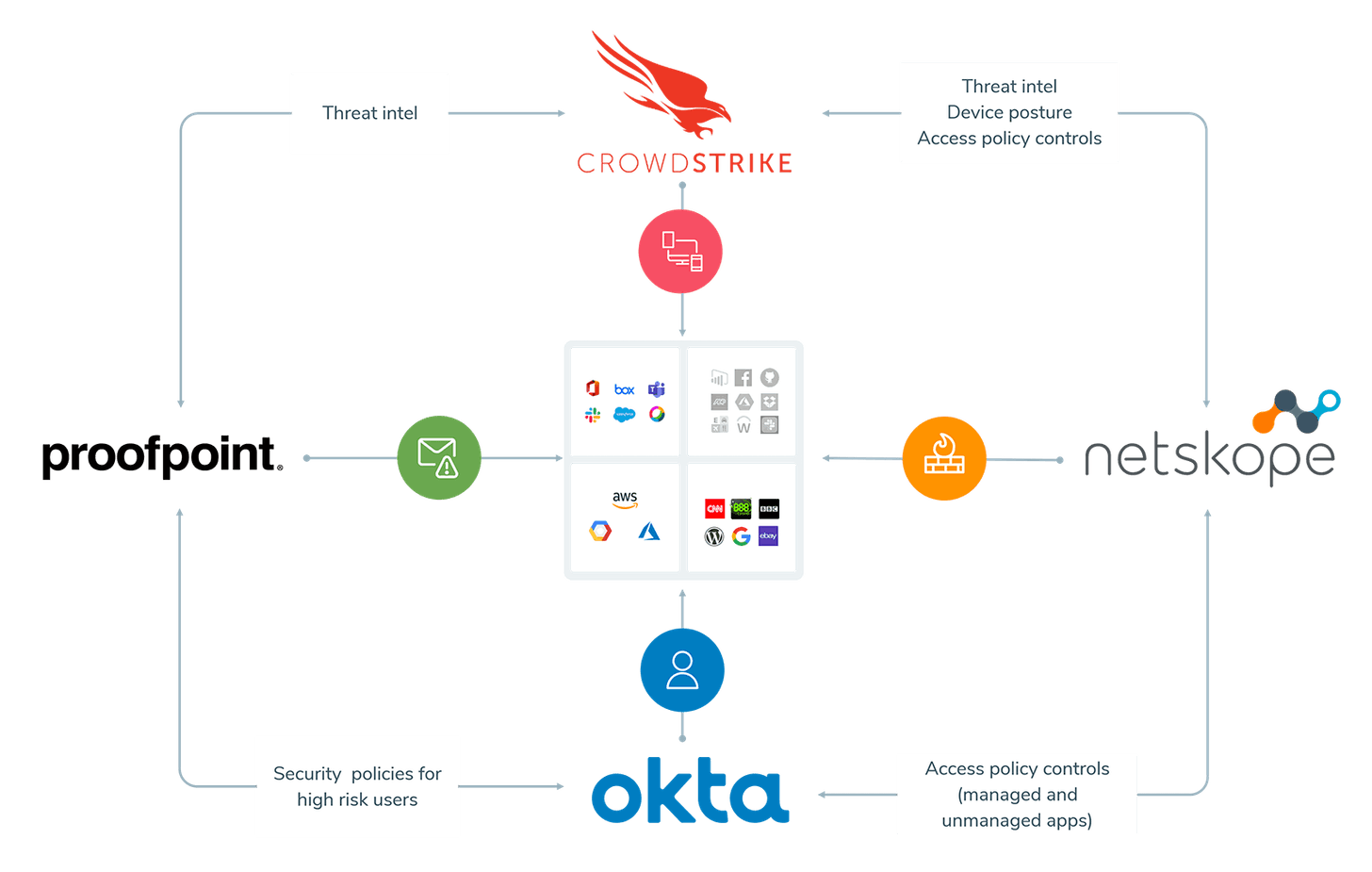
Cloudflare One injects itself into the Zero Trust workflow over not only the SWG portion on the right side (which could be Netskope or Zscaler ZIA or Cloudflare Gateway), but also includes a Zero Trust wall that covers over ALL the services in the middle that an enterprise might then access.
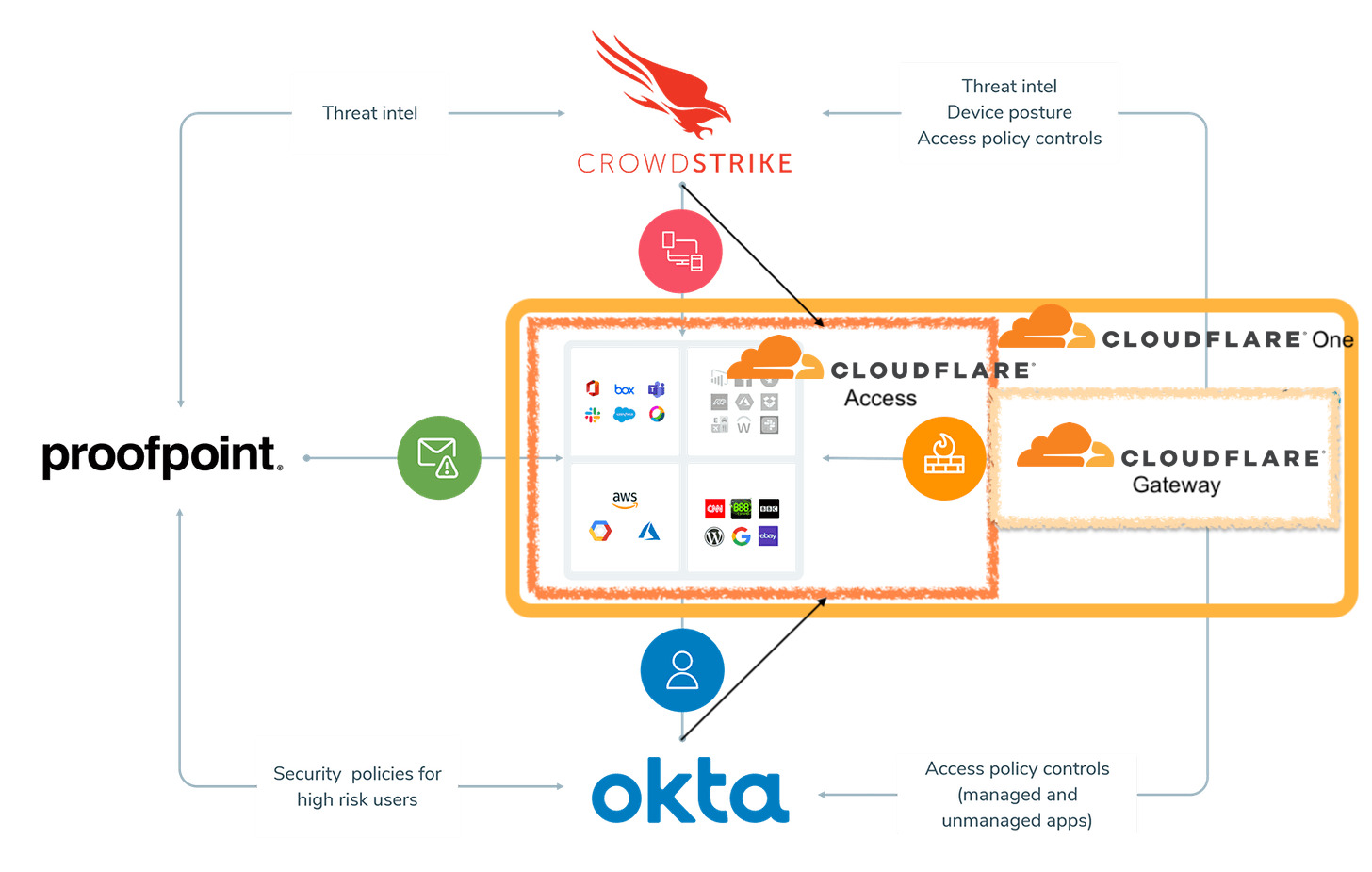
Access is now situated to be the Zero Trust SSO over all SaaS and internal access, with integrations for Identity (IDaaS) and Device (EPP) tracking. Cloudflare One is now doing what Okta has been moving towards – providing a SASE (Zero Trust) backplane over all an enterprise's SaaS & internal tooling access. [CrowdStrike is making moves towards Okta too in its new Zero Trust initiatives and its Preempt acquisition, so... this industry is getting interestin’! These frenemies are all circling around a core set of SASE & Zero Trust features – which I will write on more in the near future.]
Gateway + Access - Together is Better
[The day after I originally published this piece, Cloudflare announced that Access is more tightly integrating with Gateway, so I added this update.]
At the end of the year, Cloudflare announced that they are more closely integrating Access with Gateway. This feature allows enterpries to enforce that its Zero Trust users in Access must also be accessing the service through Gateway SWG. The 2 sides of Teams - Access for authentication & authorization (Zero Trust), & Gateway for the web traffic protection (SWG) - are now tying together more closely -- with the effect of greatly improving (hardening) enterprise security.
Zero Trust users can now be forced to be on the 'protected enterprise network' when accessing either internal services and external SaaS tools, and be using a device controlled and monitored by the enterprise. This prevents enterprise users from end-running around enterprise security by using the "Zero Trust SSO" in Cloudflare Access from other non-protected devices. If Gateway is forced, the access MUST be from an endpoint that the enterprise has installed Gateway on (meaning a device that the enterprise controls & has visibility over). And overall in Cloudflare One, if the enterprise uses an EPP partner (like CrowdStrike or Tanium), they can add device posture rules to Zero Trust -- so not only must the enterprise user be on an enterprise controlled device (using Gateway), but that device must also be registered in EPP and currently showing as healthy. Beyond the device ramifications, this more-secure combination also assures all access to internal services and external SaaS is properly logged and monitored by Gateway, which also forces use of any Magic Firewall rules. Enterprises can now have their eyes over all external SaaS usage, and can be enforcing rules over it!
This immediately exposes a fanastic new feature. Gateway can allow or disallow access to any part of these exposed services (via URL routes), and tie it to certain Access roles. So as Zero Trust users are accessing SaaS tools, enterprises can restrict specific sections within those tools to certain roles in Zero Trust. Example: All users can access Workday, but an enterprise can add rules so that only HR users can access the Reports & Admin routes within it. This requires setting up granular rules per SaaS tool, but, ends up being very potent.
And imagine if you could set up granular access controls within an application. Only these employees can access this particular record in Salesforce, even if Salesforce itself doesn’t provide that level of granularity. #staytuned
— Matthew Prince 🌥 (@eastdakota) October 13, 2020
These are all great steps towards a stronger enterprise network, and is made possible by having Zero Trust protect not just internal services, but also all external SaaS services as well. Combining Access more directly with Gateway strengthens the capabilities of both. By now allowing granular security & monitoring over an enterprise's use of all external SaaS tools, Cloudflare One is making heavy moves towards being a Cloud Access Security Broker (CASB).
Enterprise-Friendly
To further make these tools be enterprise friendly, Gateway and Access are both getting better logging interconnectivity with Cloudflare Logpush (to push access logs into any SIEM system), and better visibility tools over enterprise traffic in Gateway & Access.
During Privacy & Compliance week, they also announced Workplace Records for Teams, which combs Access & Gateway logs to provide the location that users are working from. It remains privacy-focused (isn't exact address, only State/Country), but was created to help the enterprise (finance, HR and legal teams in particular) assure that payroll taxes and records are compliant. Admins can also tie this record back into Access rules, in order to require the user be in a certain region in order to access a particular service via Zero Trust.
Improving Threat Intel
Cloudflare heavily signaled their future intent for Cloudflare One with an initiative called Cloudflare One Intel. It is not a product (at least not yet), but an overarching ambition to streamline & simplify network and security operations for all enterprise traffic moving through their edge network. Cloudflare One Intel is to bring together all the insights from a given enterprise's network activity (their private enterprise network within Cloudflare One) and further enrich it with the global threat intel from the overall edge network (crowdsourced intel covering all customer and consumer use), and ultimately build in better monitoring, alerting, and automated remediation efforts on top of it all. It's a signal that Cloudflare wants to grow into being an "all in one" enterprise security platform.
In the final announcement of Zero Trust week (the first of many products likely to focus on Intel), they introduced a new Intrusion Detection System (IDS), to detect & stop intrusion attempts over an enterprise's network within the edge network. IDS monitors over all enterprise traffic, from Gateway & Access (user traffic), Magic Transit (offices and data center traffic), and the new Magic Firewall. It proactively scans over & inspects all of an enterprise's traffic to look for anomalous events. It performs behavior analysis to learn each user’s “normal” network behavior, by looking at global location & routine behaviors, plus looks at traffic contents to try to identify targeted attacks. Cloudflare can also give each enterprise a bird’s eye view of their specific usage patterns over its edge network. I see some immediate benefits over on-premise or cloud-based IDS solutions with this new solution. First, it is offloading the traditionally heavy process of traffic inspection to the edge, which makes much more scalable. Second, threats have no impact on the enterprise's network, as containment happens at the edge instead of deeper inside the enterprise's network.
Overall, Cloudflare One Intel sounds a bit like CrowdStrike's Threat Graph, and I am guessing that, like that platform, Cloudflare will eventually allow external intel sources to be pulled in to further enrich the threat intel capabilities. And like with CrowdStrike, this intel system will only improve the security of the entire edge network. Because it is enriching IDS with both private traffic behaviors plus the platform's overall intel, it can potentially detect intrusions affecting multiple customers or different parts of the edge network, and block them all at once. All this further strengthens the security of Cloudflare's own platform.
From here, several next steps were announced to improve threat intel & detection across Cloudflare One. The initial version of Magic Firewall announced only does static rules for now, so they will be extending it with IDS to do behavioral analysis. IDS will also tie back into Gateway, Access, and Magic Firewall to enable automated remediation (adding new rules) when threats are detected.
Conclusion
There were so many innovations from Cloudflare over 2020 that it was hard to keep up. I finally had to just wait it out and let all the known announcement weeks play out before I summed them all up into the 3 areas I am watching from my Edge Networks and Zero Trust themes. The only thing I have to complain about is their rapid pace getting ahead of itself – many of the products are in limited beta at announcement. But given Cloudflare's track record (move fast, solve problems ... and NOT break things!), I don't have any worries that these go GA soon, and continue to improve from there. And as the company grows it's product lines, it is interesting to see the core personality traits of Cloudflare shine though in these new product lines - they remain security and privacy focused throughout, have a knack for simplifying these problems down to easy-to-use interfaces, and have incredibly generous free tiers. Not to mention their deep love of the color orange.
With their edge compute development platform, there were major enhancements for serverless back-end development, and more turnkey solutions built over it for publishers (APO) and front-end developers (Pages + Linc). In particular, Durable Objects really changes what is possible in serverless, by keeping the data directly next to the application on the edge. Between Workers and Pages, now web applications & APIs & data can be fully edge-native. They also included the ability to restrict their stack to certain regions for regulatory compliance.
With Cloudflare One, we now have a complete overall vision of how enterprise security will sit over the entire Cloudflare platform. Cloudflare can protect the entire enterprise network, including its publicly-accessible and private web apps & services, the traffic from an enterprise's users, and the traffic between an enterprise's interconnected locations. It has now become a more holistic platform that secures an enterprise's entire network. Gateway got a major upgrade by adding in the WARP+ (VPN and Argo Smart Routing), and both Gateway and Magic Transit benefit from the new Magic Firewall. Access can now control Zero Trust access to all SaaS services, including external SaaS services, and was combined with Gateway to give enterprises control and vision over all their external SaaS usage. New Intrusion Detection features will secure all of this from the platform threat intel and behavioral analysis over that enterprise's normal usage patterns.
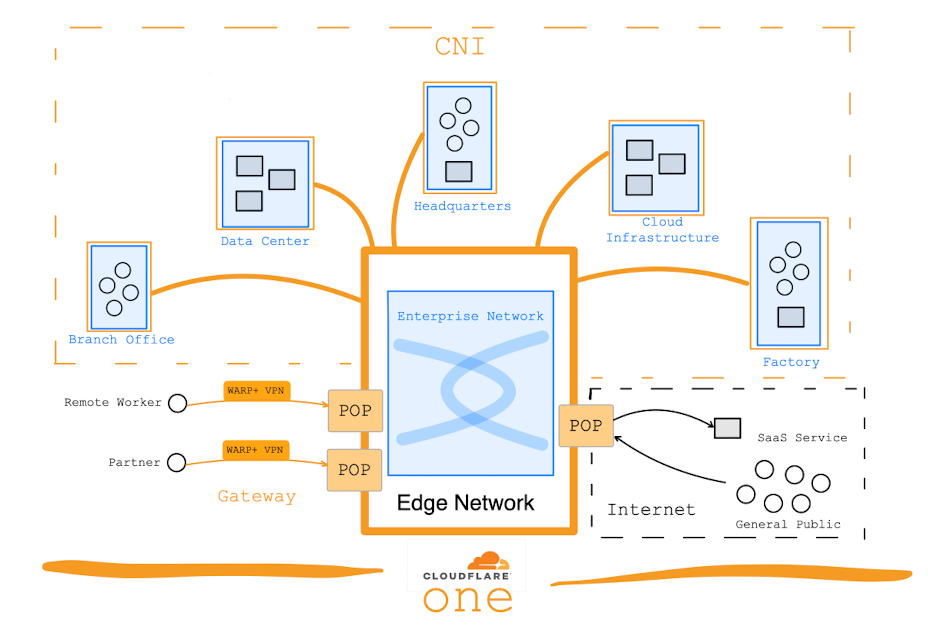
Then add in better connectivity, to add each enterprise into the "orange cloud". (Cloudflare might become the Borg of the Internet.) CNI allows Cloudflare to become the backbone of the enterprise network, interconnecting all of an enterprise's locations into one large secure network – without needing any fancy WAN networking equipment. When Cloudflare is the network backbone, the enterprise doesn't need to manage the "moat" around it all – Cloudflare has the expertise and will do it for them. Magic Transit then brings Cloudflare's security onto the on-premise networks, and adding Cloudflare One over all that adds in all the application and user security. The more dispersed the company (across various offices, locations, data centers, and cloud environments) and its users (in office locations, or fully remote) - the more Cloudflare One + CNI will help. Add it all up, and Cloudflare is now providing a "secure enterprise network-as-a-service", giving each customer a One on WAN.
Where It Goes Next
From here, I expect more and more enterprise-friendly features get added to One and Workers, plus still see a few gaps that could be filled.
Expanding Cloudflare One
- In combining Gateway with Access, Cloudflare is adding in Cloud Access Security Broker (CASB) features, which is about controlling & monitoring the use of external SaaS services. One piece of Zscaler's feature set that is still missing in Cloudflare's, however, is Data Loss Protection (DLP), for controlling what data can be pulled from SaaS services. I expect a DLP service to be added, so a more formal CASB product can emerge from all these moves. [This point on CASB/DLP was updated after Cloudflare announced (a day after I published) that Gateway and Access intertwining more closely.]
- Cloudflare will continue to add more application & API protection features, and to heavily push this part of their core platform in Cloudflare One. Together with the Workers platform, Cloudflare is becoming a one-stop shop for software development companies to utilize – regardless if the applications & services are hosted on the edge or elsewhere.
- Fastly is making strong moves in this direction via its Signal Sciences acquisition, and may have even slightly surpassed Cloudflare's capabilities. Runtime Application Self-Protection (RASP) is a feature that embeds within your application via an SDK, in order to bring the platform's threat intel directly into the application itself – which is one feature in Secure@Edge that Cloudflare is missing.
- I expect Cloudflare to get into cloud workload protection. CrowdStrike and Zscaler are both moving in this direction, to protect the traffic to serverless and containers running in public cloud environments. Cloudflare has not yet focused on working more directly with core cloud services. Of course, much of their existing application and API protection features can cross apply to cloud-based services, but they could add more direct features to protect AWS, Azure and GCP app workloads more directly. If One is truly protecting the entirety of an enterprise's network, this part is still incomplete.
Expanding Connectivity
- Cloudflare can not only be the backbone of a given enterprise – it can serve as the backbone BETWEEN enterprises. They could easily enable creating private networks in Cloudflare One + CNI between disparate teams across multiple enterprises, in order to create secure networking between partnerships, joint ventures, or any collaboration between teams requiring shared services or network access. Zscaler has a focus on this with their B2B product built over ZPA (Zero Trust), and if you recall in my recent Snowflake deep dive, this type of collaborative need between partnering enterprises is a huge focus there as well with their Data Exchange product. I fully expect this to be on Cloudflare's roadmap as this opens a whole new market. (And if it isn't yet on the roadmap, it is now.)
Expanding Edge Development
- I expect Cloudflare to continue to improve developer processes around creating, building and deploying applications to the edge. Pages and the acquisition of Linc was just the start - there are many other application architectures beyond JAMstack that could benefit from the edge. There are also several startups focused around improving developer workflow that could be added to further enhance how the development pipeline works over edge-based applications.
- Any improvements in observability & alerting over edge serverless will surely be welcome by developers. Ultimately they need to allow developers to tie in custom metrics from their functions – something like Application Performance Metrics (APM) but for serverless, and tie it into observability partners like Datadog. Fastly has mentioned they are making a separate product line called Observe@Edge to focus on these things.
- Taking observability even farther, they could potentially add in the behavioral analytics and threat intel from Cloudflare One into something that better secures Workers instances.
- Fastly is likely to ultimately be the biggest competitor in edge compute workloads. I'm not convinced of their platform (considering it still isn't fully in production after 2 years!), but even if turns out that Fastly built a better mousetrap with Lucet (which is WASI-based, running WebAssembly at the system level instead of in a browser engine), nothing is preventing Cloudflare from continuing to improve their serverless architecture from here. They could move towards WASI-based architectures to power their WebAssembly-based serverless engine, instead of using Google's V8 browser engine. If Lucet or Wasmtime are that much better of a runtime, both are open source and could be utilized by Cloudflare as it streamlines its serverless architecture. (BTW, Fastly recently acquired the entire Wasmtime team out of Mozilla. Lucet is likely the best path for WASI going forward.)
- Could Cloudflare start adding GPU capabilities at the edge? Nvidia is making a focused GPU product line for this. This type of equipment would enable a different class of Worker instances that could be more ML & AI focused. For now, it is probably best if ML & AI workloads remain in core cloud, given their heavy compute needs.
Bring enterprise features to consumers
- WARP went to Gateway. Could Gateway (SWG) be coming to WARP? This would add threat protection over consumer web traffic to the WARP+ product.
- Browser Isolation is the big one that WARP+ customers could heavily benefit from. The edge could be acting as the browser, and the consumers would only be seeing and interacting with a copy of the page locally on their device. I'd pay for that.
All in all - there are several ways for Cloudflare to move forward from here. And over it all, Cloudflare continues to make it all secure and, most importantly, simple to use (hiding away the complexity of all this). While the development environment with edge compute captures most of the attention, Cloudflare One + CNI is the primary reason I remain heavily invested. I foresee them getting a lot of interest over the competition given their ease of implementation and interconnectivity, and how well their platform overlaps all the critical areas of enterprise security. As Ramírez told MacLeod, "there can be only One"!
Add to all this – what else does Cloudflare build over its own edge network from here? And what do its customers build on the edge? There is a lot of success to come with this company.
Addendum: Making a Better Internet
Besides the areas I am heavily focused on above, Cloudflare continues to "build a better internet", so wanted to also mention these fantastic additions, unrelated to my investment thesis.
Cloudflare Analytics is a new privacy-focused web analytics tool, that tracks metrics from your web traffic in near real-time. It obviously competes against Google Web Analytics and many other paid solutions, to see what users are accessing on your web site and from where. However, it has a heavy privacy focus – it does not track or fingerprint users, and remains private to you (it is not aggregated and used by Cloudflare). It will also include tracking the new Core Web Vitals metrics, Google's newly announced scores that greatly impact a site's ranking in search results. It was originally for Cloudflare users, but was later released to the general public during Privacy week.
Cloudflare Radar is a new public dashboard that allows you to introspect the state of the web. It provides a view into what the Cloudflare network sees, to provide Internet insights (traffic patterns, popular domains, attack activity), Domain insights (status, content and popularity of individual sites), and IP insights (view status of an individual IP). See it here.
Add'l Reading
Peter @ SSI blog covered Fastly's latest quarter, and their overall roadmap for edge compute from their Altitude conference. He goes into how Cloudflare's serverless compute architecture compares to Fastly's, plus recaps Cloudflare's advancements during the first 3 announcement weeks.
TechCrunch wrote on Cloudflare entering the JAMstack market, that I thought covered the developer perspective well. And if you want to see through some developers' eyes, don't miss those spoilers on the Pages release, or another's tweet storm raving about using Linc on Workers.
If you got lost in cybersecurity terms above (like Firewall, SSL, SSO, SWG, Zero Trust, SASE, DLP, and CASB), you should read my Flavors of Security series, then come back revisit this post. (Or at least use it as a lookup.)
- muji
