This is part of the Flavors of Security series, in particular Part 2’s investment focus on what drives the hypergrowth stories within the cybersecurity space. If you need to learn the security terms & product abbreviations, you can look up the terms that first post.
Okta (OKTA) = Identity Mgmt + Incoming Protection (Zero Trust)
Platform: Okta Identity Cloud (OIC)
Ecosystem: Okta Integration Network (OIN)
Partners: Okta Partner Connect
Flavors of Security:
- Current: IAM
- Next wave: IGA, UEBA, PAM (Zero Trust), IAP (Zero Trust)
Massive Tailwinds:
- Adoption of SaaS biz-op enterprise services
- Development of new SaaS services
- Migration to cloud
- Mobile workforce
- Zero Trust
- ML/AI-driven Security
Differentiators:
- Cloud-based -- no appliance or infrastructure needed. Infinite scale, unlimited capacity.
- Complete view of customer security.
- Platform w/ incremental add-ons, and an ecosystem of integrations and security partners.
- Strong adoption of ML/AI internally, plus are exposing it as new "Adaptive" features for customers.
- Fully embracing Zero Trust, especially with ScaleFT acquisition.
- Ease of use. Multiple products & advanced features available based on need.
Platform capabilities:
- Identity: IAM, IGA [more the A than the G]
- Security: SSO, MFA
- Access: API Gateway, PAM (Zero Trust), IAP (Zero Trust)
- Monitor: Continuous Monitoring
Products:
- Single Sign On (SSO) & Adaptive SSO
- Multi-Factor Auth (MFA) & Adaptive MFA
- Universal Directory (IAM)
- API Gateway
- Lifecycle Mgmt (IGA) for lifecycle mgmt and auto-provisioning (no Governance capabilities... yet)
- Advanced Server Access (PAM) for Zero Trust system access
- Access Gateway (IAP) for Zero Trust application access
- ThreatInsight - threat intelligence curated by Okta’s incident response team
- Risk-Based Authentication (UEBA) user behavior analytics, tied into MFA and SSO
- SecurityInsight - for end-user, suspicious behavior reporting tools; for admins, custom security recommendations & best practices
Partners:
By technology:
By partner:
Partially competing with ***.
- Sailpoint (IGA) ***
- Cisco (CASB/DLP)
- McAfee (CASB/DLP)
- Netskope (CASB)
- Bitglass (CASB)
- Kong (API Gateway) ***
- Splunk (SIEM, SOAR, UEBA)
- LogRhythm (SIEM, SOAR, UEBA)
- Zscaler (SWG, ZTNA) ***
- CyberArk (PAM) ***
Magic Quadrants:
IDaaS/IAM:
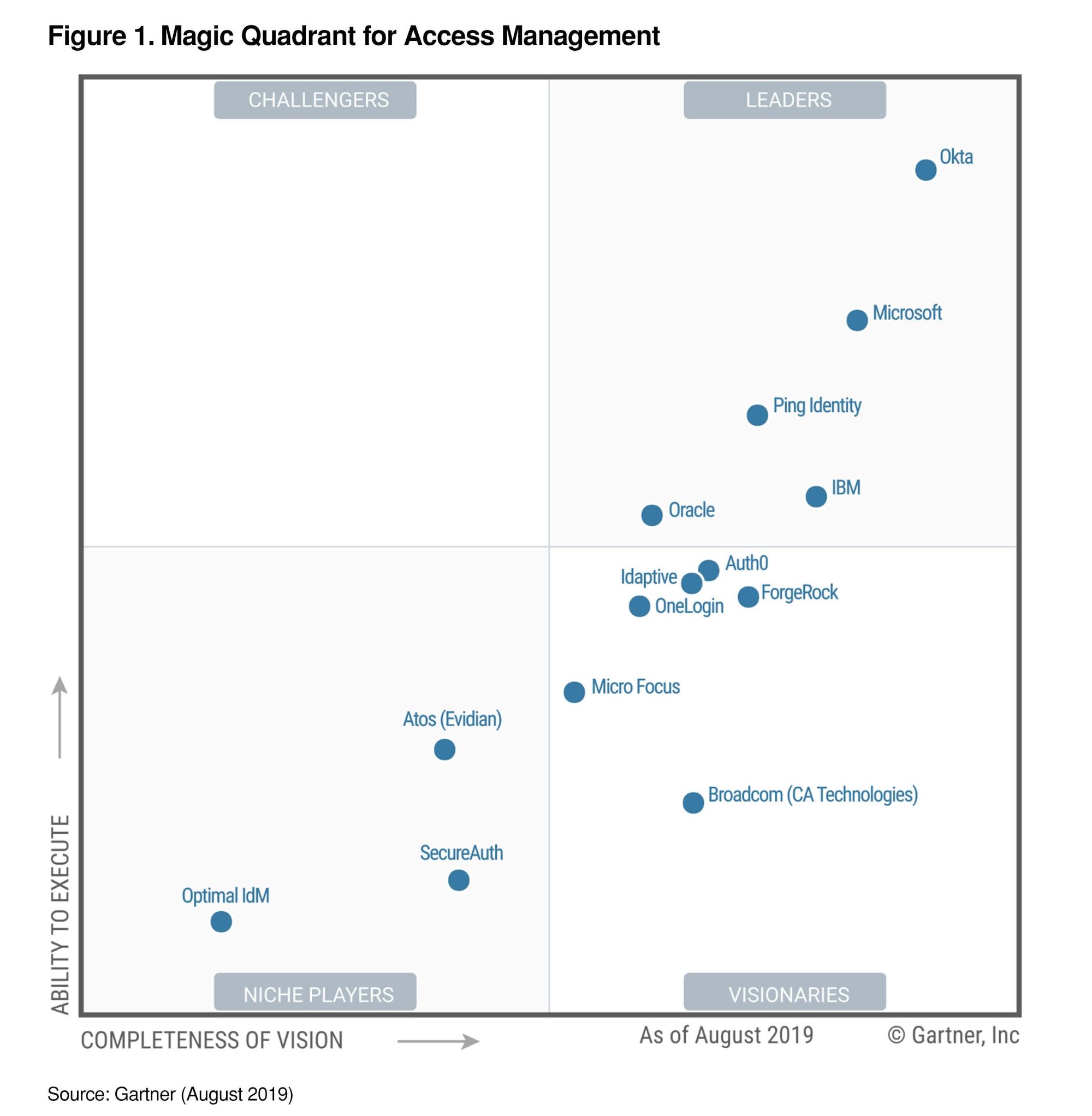
IGA: (no Okta shown)
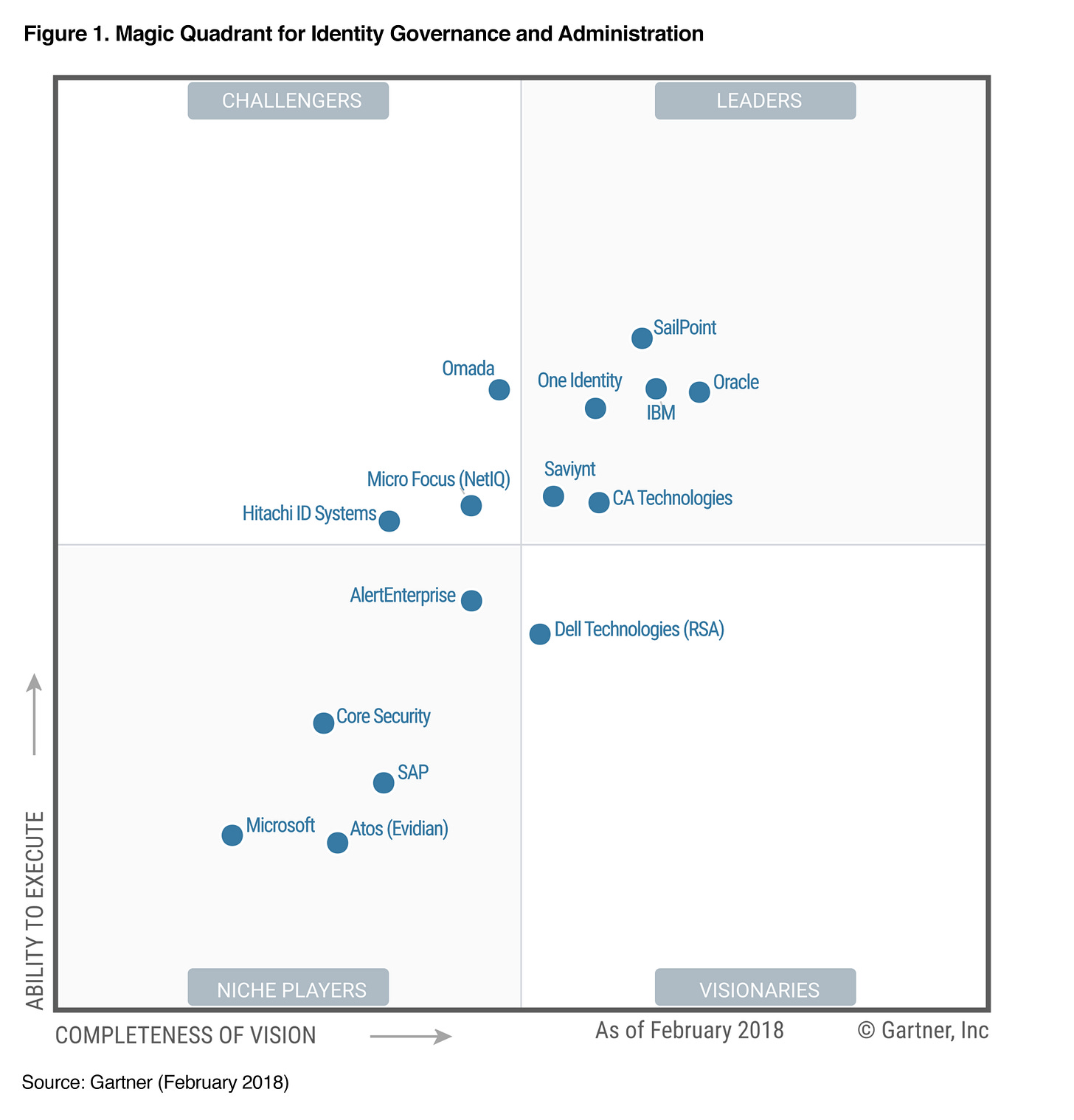
PAM: (no Okta shown)
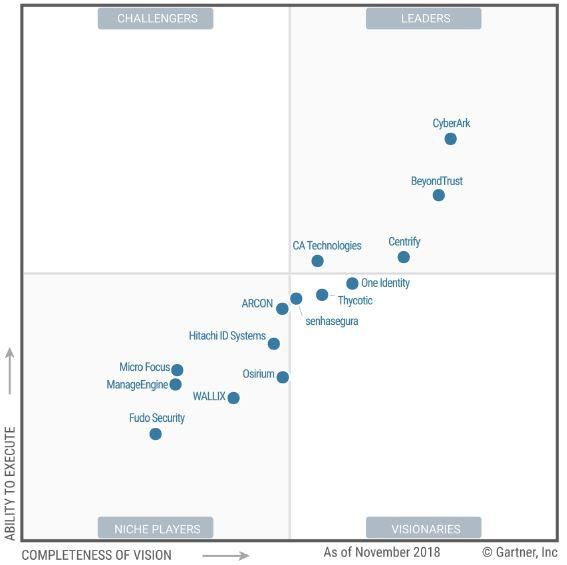
ZTNA/IAP: no MQ yet but see the Gartner Zero Trust report
Competitors:
[Okta integrates with many!]
- IAM - PingID, Centrify, Cisco/Duo, Microsoft, AWS, Google, IBM, RSA, Symantec
- IGA - Sailpoint, Oracle, IBM, OneID, CA Tech, Saviynt
- API Gateway - Kong, Microsoft, AWS, Google
- ZTNA/IAP - Zscaler ZPA, Cisco/Duo, Google, Akamai, Cloudflare, Symantec/Luminate
- PAM - CyberArk, BeyondTrust, CA Tech, Centrify
Gardner customer reviews:
Thoughts:
For detailed background on their platform and product lines, see my Okta Deep Dive, Apr 2019.
Okta rules the roost in IAM solutions that provide identity mgmt, federation, SSO, MFA, and universal directory services. Okta is sitting in a very sweet spot. It has become THE name in Identity, with a platform of ancillary products around it, plus has built an ecosystem of integration with a wide variety of SaaS services plus security partners. They have product lines that address both internal identity (workforce) as well as external identity (customers). Okta has 6000+ integrations available in its OIN - a huge advantage over any competition, to the point where new SaaS services strive to be on OIN given the potential customer base it gets exposed to there.
However, it is not just resting on its IAM laurels and vast integration network -- it is now veering into other related angles around identity in security. It finds itself in an interesting position. It tries to maintain itself as a neutral platform that integrates with a huge number of other SECaaS services, however, in adding new capabilities and products to its platform, it finds itself competing with partners (those I marked with *** above):
- It is adopting more identity life-cycle and auto-provisioning capabilities (admin part of IGA), embedding itself further into its customers workflows. So it competes somewhat with Sailpoint. It hasn't added governance features... yet.
- It has add-on product for API Gateway, which competes against their partner Kong, as well as cloud providers (eg AWS, Azure).
- It is veering heavily into Zero Trust with its new Server Access (Zero Trust PAM) and Access Control (Zero Trust IAP proxy), after its acquisition of ScaleFT. PAM features compete against CyberArk, while Access Control is competing with Zscaler ZPA, Duo (Cisco), Luminate (Symantec), Google "Beyond Corp" and Akamai.
From here, I feel Okta could easily move in some other directions that are identity- & access-related, such as Governance side of IGA (against Sailpoint), CASB/DLP (against Cisco, McAfee), and even SWG (against Zscaler's ZIA, Cisco). CASB seems most likely (regulating the SaaS intercommunications, a connection it already controls identity over).
Strengths:
- It is a top name in IAM/Identity space, a Category Crusher. As the use of SaaS services grows, so does the need for Okta. Look at Gartner's Magic Quadrant - I've never seen a company so far top right in a MQ. Okta is FAR AND AWAY the top leader; it is out-pacing any competition.
- It is a cloud-native SECaaS that is analyzing and gaining insights from a complete view over ALL their clients (no more islands). They are incredibly well positioned to manage the security of their own service plus that of their customers. They can scale as usage demands.
- Their product line and pricing on each is incredibly clear. There are no bundles - all services are available al la carte, priced per user. Their web marketing is great, and their pricing list page is a thing of beauty. After signing up, customers report that it is incredibly easy to get started with the service.
- They have an extremely sticky IDaaS (IDM) platform, and ecosystem integrating with partners into multiple different security directions from there (IGA, PAM, CASB, DLP, SWG, ZTNA, SIEM, SOAR). However, they are starting to add new products, expanding outward from their core identity product into other identity-related directions. Customers can use them a little or a lot, as desired (and depending on their existing infrastructure setup), so there is a huge ability to land-and-expand, as customers get to know the benefits of the product lines.
- Speaking of sticky - Okta is making its entire platform modular and customizable, further allowing customers to embed it deeper and deeper into their HR & IT workflows. It also recently acquired Azuqua, a flowchart-based workflow editing tool, to help customer's better integrate the modular pieces and tie it into the SaaS services utilized.
- They are fully embracing Zero Trust, acquiring ScaleFT a year ago to enable multiple new directions: Server Access (PAM) and Access Gateway (IAP, aka an IAM+Zero Trust proxy). That acquisition is why I am still fully invested in Okta -- it is a fantastic new ancillary direction of Zero Trust yet still very Identity-related. Server Access is a Zero Trust flavor of PAM, an incredibly relevant bolt-on product that existing customers are sure to expand into. Access Gateway is not being called such, but it is an IAP (Identity Aware Proxy) flavor of Zero Trust per its architectural docs, not ZTNA via micro-segmentation.
- And beyond Zero Trust, Okta has a CARTA mindset, as it is expanding existing IAM services with ML/AI. Okta created a curated ML/AI threat intelligence system over its entire customer base called ThreatInsight, and has been iterating over it ever since. Beyond that, it extended ML/AI capabilities to provide both contextual- and behavior-based adaptive rules directly to the customer as add-ons. Okta has directly monetized its ML/AI capabilities.
Let's walk through the evolution of its ML/AI capabilities:
... Sept 2015 - First version of Adaptive MFA released, using contextual information to score risk, including network & location of request and application accessed.
... May 2018 - Announced ThreatInsight, a curated intelligence platform over its entire user base, extending context-based decision making, extending Adaptive MFA product and allowing new Adaptive SSO product.
This diagram (from Adaptive MFA product page) for the types of threats ThreatInsight assists with:
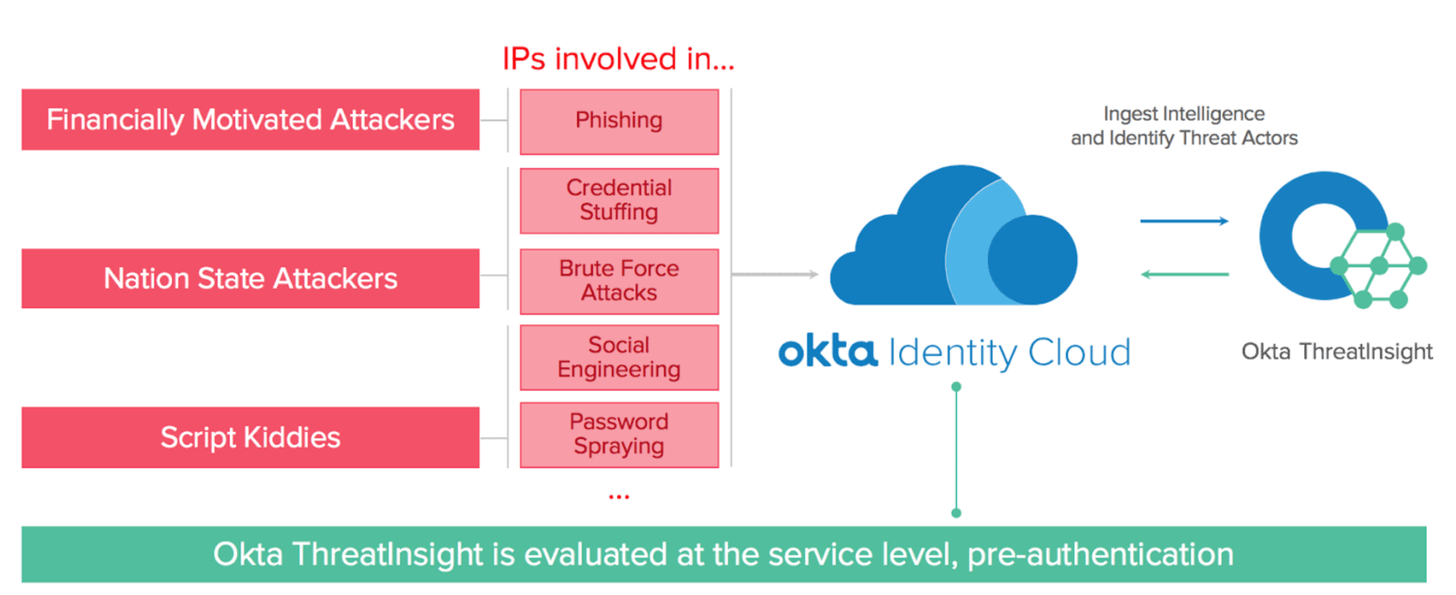
This blog post detailed how customers can utilize ThreatInsight protective features.
- global blacklisting of malicious IPs
- global network intelligence to identify bad actors and add to ThreatInsight pool
- customer's auth services can auto-block against that pool
- sees large-scale attacks like DDoS, password spraying, high rate of login failure
- can push alerts to syslog tools for customer monitoring or action handling
- malicious actors caught pre-auth, so prevents account lockout from attacks
... April 2019 - Announced Risk-Based Authentication, extending Adaptive MFA & SSO with behavior detection capabilities. This exposed better ML/AI capabilities directly over an individual customer's data. Okta customers now have insights from Okta's network-wide view (ThreatInsight) plus over their specific users' behaviors (Risk-Based Authentication) as well as context of the request.
... October 2019 - Announced new SecurityInsight features, extending ThreatInsight and Risk-based Auth features above.
- UserInsight adds new features for reporting suspicious activity to individual end users, and allowing them to flag events -- making them the front-line of an enterprise's security (as they should be). Flagged events can trigger actions in Okta IAM or orchestrated in other apps via SOAR integration.
- HealthInsight adds new features to IT admins, presenting customized best practice recommendations to individual customers, and provide one-click ways to engage recommended features.
Concerns:
- I'm not sure why, but they are not playing up Zero Trust in Okta's marketing of their new products coming from ScaleFT, compared to the marketing on ScaleFT's own site. Curious.
- Revenue growth is slowing to just under +50% YoY. I believe their new Zero Trust product lines will be big drivers of the next wave of growth, but that hasn't proven itself yet. Beyond that, I believe there are further directions they could expand from here, like Governance (IGA), CASB/DLP, as well as SWG (directly completing with Zscaler ZIA).
- They are competing with partners in their ecosystem, while still touting those partnerships. They are the ultimate "Integration" network for Identity - but aren't always playing it neutral. For example, they compete with Zscaler ZPA now, but still tout Zscaler+Okta integrations. Delicate balance between being a neutral platform around identity, and adding additional identity-related services around that which partners are already providing. There is risk to this approach, but thus far, Okta seems to be playing it deftly.
