It's a new technologically-driven landscape for today's enterprises. EVERY COMPANY MUST be a tech-driven company.
- EVERY COMPANY MUST rely on applications to run the day-to-day operations of their business.
- EVERY COMPANY MUST maintain security and monitoring over those systems.
- And EVERY COMPANY MUST ultimately take advantage of analytics over those systems, to better drive their strategy and stay ahead of the competition.
Coincidentally, I just watched the CEO Keynote that was just posted from Oktane19, Okta's annual conference, where CEO Todd McKinnon stated to attendees: "You need to be a technology company, or your replacement will be." Watch the first minute here:
This new landscape is driving the hypergrowth stories we are seeking here, as companies sprout up to be the "picks and shovels" plays that are supplying this gold rush of technological innovation. They are creating new tools that are enabling companies to solve their own problems themselves that cross-applicable to every business, across every industry. And luckily for us, it still seems like the early innings! I'm going to start looking in-depth into a few of our favorite "tooling" companies as to what vital products & services they are providing to enterprises and what is making them so indispensable -- all while trying to explain the technical basics behind them. Today, I'll start with Okta (now my 3rd largest position at 11%) on the security side.
Security Basics
Before we dive into details, let's start with some security-related basics for the non-technically inclined amongst you. If you are a novice to these concepts, don’t just skip over this. You need to understand these terms, as I believe it helps you more clearly see the potential in Okta as an investment.
- Authentication (authN) = proving to a system that you (the user) are who you say you are. Can be as basic as username & password, a PIN code, or as advanced as biometric scans on your phone with TouchID (fingerprint) and FaceID (facial recognition). End result is being a trusted user.
- Authorization (authZ) = once you are authenticated, now what can you do? What level of access do you have? This is normally tracked via some combination of RBAC (role-based access control) or ACLs (access control lists that track the rights each individual user has for every action in the system). Roles are fairly self-explanatory. For example: In a sales tracking app, are you a salesperson tracking their assigned leads, or a manager needing dashboards to oversee metrics? In an HR app, are you the employee entering time sheets and viewing their own paystubs, or a manager that is managing the users and approving payroll?
- Authentication factor = categories of info that is user is presenting during authentication. Either something you know (a password or PIN), something you have (a token or device), or something you are (biometric data). Most common form is username and password.
- One-Time Password or PIN (OTP) = security mechanism where a single use temporary validation password or PIN is generated for authentication, provided to the user via a trusted method. Stronger than static passwords, as it is not subject to common attack vectors like man-in-the-middle or replay attacks. [I'm not getting into attack vectors here. Look 'em up if you want more details.]
- Security token = security mechanism where a temporary code must be used that is associated with a given user's identity for a set time frame. Common in authentication systems where trusted hardware devices (like RSA SecurID) or software apps can generate a token to use for login attempts, each valid for a short time window (say, 30 seconds) before it then refreshes with a new one.
- Multi-Factor Authentication (MFA) or Two-Factor Authentication (2FA) = having a system require more than a single authentication factor (user credentials) to log into it. First called 2FA until security folks realized they should leave it a bit more open-ended. If you use online banking, you likely have been using some type of MFA to complete your login. Forms of MFA may include receiving an OTP via SMS or email, using an OTP from a software app, using a software- or hardware-based token generator, or providing biometric information like a fingerprint, retinal scan or facial recognition. [As an aside, I highly recommend using the Authy app from Twilio to track 2FA software tokens for all your accounts.]
- Lightweight Directory Access Protocol (LDAP) = an open protocol and data store (a "directory") for tracking user authentication (credentials) and authorization (access rights) on a organization's trusted private network. A common one is Active Directory (AD), Microsoft's LDAP service for Windows networks.
- Identity and Access Management (IAM) = a application to track and manage users' authentication and authorization details across an organization's systems.
- Provisioning = process in IAM that relates to automating authorization changes (access rights) when users are created, modified, disabled or deleted. An example is when a new employee on-boards, HR would need to coordinate with IT to get accounts and rights set up in multiple systems (such as systems for payroll, benefits, travel expensing, email account, server or software access, etc). This step has becoming increasingly complex with the proliferation of SaaS tooling!
- Delegate = handing your access rights over to another trusted system or user.
- Federation = common standards and protocols to enable identity sharing across trusted disparate systems. This is the key to enabling inter-dependencies between SaaS apps!
- Security Assertion Mark-up Lang (SAML) = open standard to pass authentication and authorization data between federated parties (the user, an identity manager, and the service the user is accessing). Typically used in enterprise systems.
- Open Authorization (OAuth) = an open standard for token-based authentication to authorize across systems (enabling "delegated authorization"). For example, this enables how you can allow LinkedIn to access your GMail contacts, or let Yelp post on Twitter on your behalf. OAuth 2.0 is the current standard. After authentication, OAuth will generate a token that subsequent requests can use for a limited time (say, an hour), instead of requiring re-authentication each request. Internally the system will track what tokens are associated with what identity, and will expire or invalidate those tokens as needed.
- OpenID Connect (OIDC) = an identity layer over OAuth 2.0, allowing OAuth authorization across cooperating systems over a common identity (enabling "federated authorization"). For example, this allows how you can use a Google or Facebook account to log into Yelp or LinkedIn, where it then creates a new local account within that app, linking back to that Google or Facebook identity for needed details like name or email. Typically used in web and mobile apps.
- Single Sign On (SSO) = the ability to use same credentials to authenticate into multiple disparate systems. SSO is enabled by SAML or OIDC. (NOTE: SAML or OIDC are competing standards for identity intercommunication, with different process flows and message formats. OIDC is newer, and IMHO, more streamlined for using with web & mobile apps and APIs.)
- Federated Identity Mgmt (FIM) = an IAM system linking your users' identities across multiple disparate systems. SSO is one of the important features federation enables.
- Identity-as-a-Service (IDaaS) = FIM SaaS provider.
- Zero Trust Security = newly emerging business strategy for keeping systems secure, by no longer trusting a network perimeter (such as a firewall blocking the public internet from accessing a company's private network) to isolate trusted users from untrusted. Zero Trust = Always Verify -- all users must be verified on every system at all times.
Okay... that's as deep as we need to go into the terms. Back to Okta...

Okta Overview
Okta is all about identity management. Identity is about knowing who a user is, what systems they can access, and what they can do in that system once in. Okta is helping companies mitigate the huge overhead needed to manage and track their users across all their systems -- whether those users are their workforce (employees, contractors and partners) or their customers.
Okta is Identity-as-a-Service (IDaaS), which provides identity management capabilities for businesses (Okta's customer). Companies sign up and pay Okta, on a monthly basis per user, to manage their workforce users (controlling what systems and data they can access) and/or their customers (controlling access to the company's software), allowing companies to embrace a Zero Trust security paradigm.
Companies today are spread out more and more (remote employees, global locations), and are utilizing a wide variety of 3rd party applications as deeply integrated pieces of their day-to-day operations. For example, they need to use SaaS applications for sales & marketing (Salesforce, Marketo), HR and payroll (Workday, Paycom), communications (Slack, Gmail), and document mgmt (Google Suite, Office365), and on and on. Beyond business operations, companies who develop their own software on on-premise, IaaS (cloud compute) and PaaS (cloud platforms) systems need to manage developer and sysadmin access, developer tooling (Atlassian, Github) and infrastructure monitoring (Splunk, New Relic).
Rather than manage individual user credentials and rights across all these applications separately, companies use a FIM provider to do it for them, so users can log into the provider, and via SSO, be able to access all the internal and external systems needed. Think of it as getting a wristband at an amusement park, which you use to ride every ride within (auth once, access many), instead of having to buy separate tickets per ride (auth each time).
But SSO is JUST THE TIP OF THE ICEBERG of what Okta provides. As the number of needed SaaS business tools has exploded, so does the complexity of managing it all. A massive amount of time and resources are saved by having a IDaaS provider manage the vast number of systems you need to utilize, multiplied by the number of users needing access. Combine all that with assuring security is buttoned down tight, and needs to be audited and continuously monitored for risk and intrusion. Why would a company burden itself with having to create and maintain its own internal system to manage and track identities, and then having to secure and monitor it? Besides the time and resources needed, the security risk is immense. An IDaaS solution like Okta is greatly preferred right from the start, as it can scale (as the company's user-base grows x all the systems they need access to), can adapt quickly (as new security threats arise), and works with everything (integrates w/ new SaaS/PaaS/IaaS tools as they emerge).
Once a business starts using a IDaaS provider to manage their users across all their internal and 3rd party systems, I don't see them EVER GOING BACK to a self-managed solution. This means Land and Expand is the name of the game for Okta -- get companies to start using its IDaaS platform and their use will spread from there, as their users scale up, as their identity needs change, and as they integrate into more and more systems. The only way a customer is going to stop using Okta is if they migrate to a competing service providing the same features. And as workflows get automated and customized from there -- I'm not sure that competition is going to have a seamless way to pilfer Okta's customers.
All that means staying power (customer retention) and continual use (recurring revenue), as Okta shows with its ever growing customer base (a very steady +40% YoY) that is spending more ($NER 120%, with customers >$100K +50% YoY).
Product Lines
So - what does Okta actually sell?
Okta Identity Cloud is the primary platform or ecosystem that Okta has built, and all its SaaS products are within. This platform is built around identity - interconnecting all the employees, contractors, and partners a business might have, as well as their customers. It helps an enterprise manage its users, their access rights, and allow them to connect to needed SaaS apps, mobile apps, on-premise apps, devices, APIs and infrastructure systems.
At its core, Okta depends on integration. Okta Integration Network (OIN) is their platform's collection of pre-built integrations with that vast pool of 3rd party SaaS systems. Entire list is at ...keep scrolling ...keep scrolling ... there are >6000 of them per their last earnings call.

Okta Identity Cloud is HIPAA compliant for health care requirements, and is FedRamp approved for government agencies at Moderate level. (Here is the full list of their security/audit certifications.)
Tangentially, Okta also has some supporting mobile apps users can utilize to interact with their SaaS services. [Both are rated very poorly, so not sure this is a focus. And marketing doesn't highlight them at all.]
- Okta Mobile on iOS/Android, provides SSO to any OIN mobile apps on the device for any Okta identity.
- Okta Verify on iOS/Android/Windows, provides MFA mechanism for use with Okta. Tracks software tokens as well as utilizes push notifications called "Okta Verify with Push".
So let's dig into their suite of FIM products on the Okta Identity Cloud.
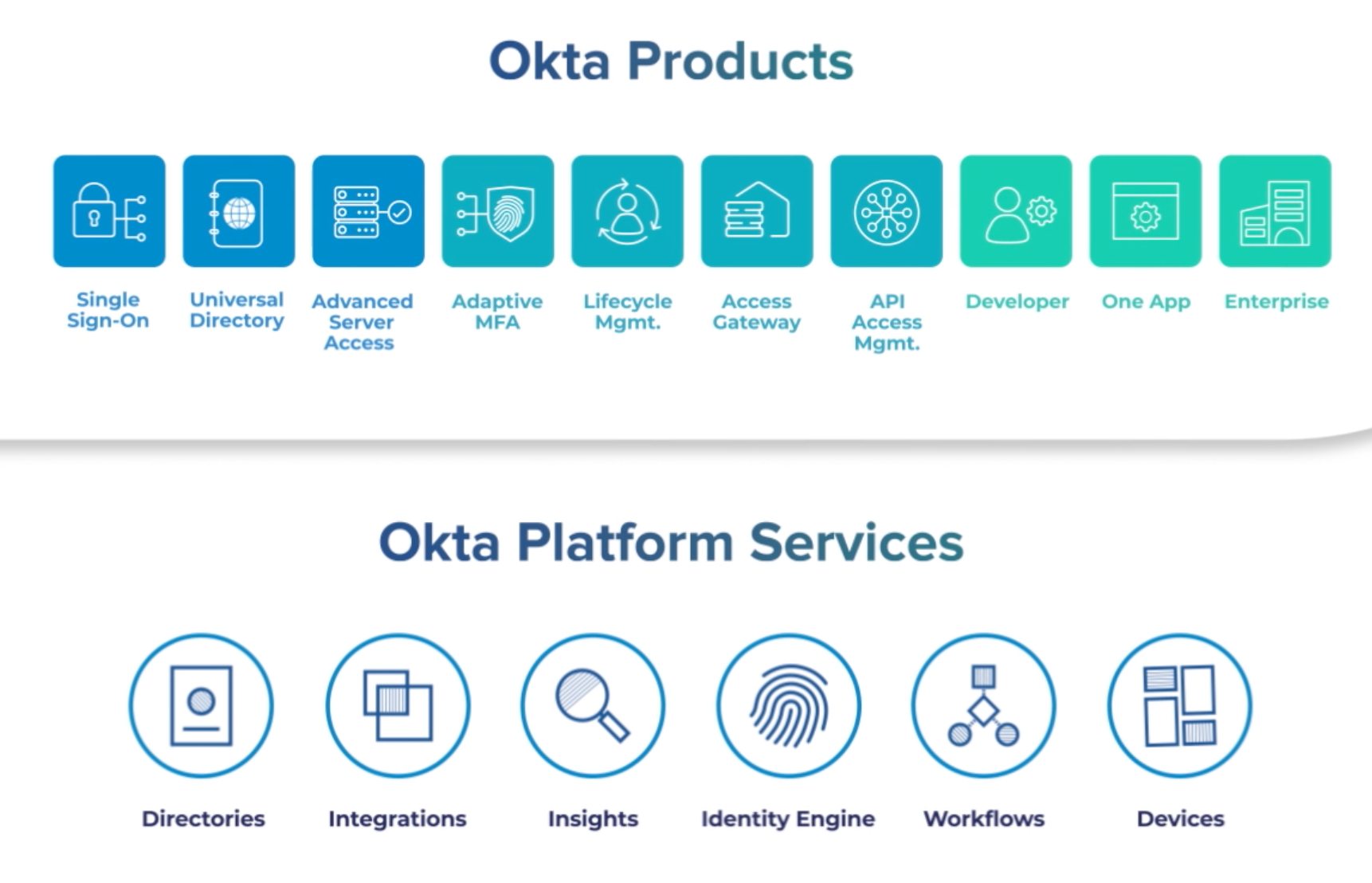
Segments
Workforce Identity
This segment is comprised of products for tracking workforce access to a company's internal or 3rd party (SaaS providers & APIs) systems. Okta helps companies adapt their business operations to an ever-growing SaaS toolset, as well to the complexities of managing their infrastructure. This is especially difficult when migrating to a hybrid or multi-cloud setup (using some combination of on-prem, AWS, Azure, and Google Cloud to build your infrastructure). They have been "riding the wave" with cloud migration for years now, as nearly every major business moves its infrastructure into an all-cloud or hybrid setup.
Magnifying all that complexity is the extreme risk in self-managing your security. Companies have thus far relied on devices (firewalls and routers) to build a walled-in zone of trust. Today's all-cloud or hybrid setups needed a new paradigm, and as Okta has been at the front lines of the move into the cloud, it is now a part of the Zero Trust movement of "Trust nothing! Verify everyone, at all times!". Companies using an IDaaS are simply never going back to the old ways - they are eliminating, at a minimum, multiple employees that would be required to manage it all in-house, but more likely are eliminating entire departments. As I mentioned before, there is no turning back from IDaaS once they pull the ripcord. They are likely SAVING money in the long-term using Okta, compared to their old solutions.
Various products can be utilized, depending on how "deep" a customer wants to go. [Customers highlighted in Okta marketing show exactly which of these products that customer uses, if you want to dig further.] All workforce products are priced per-user, per-month. Some higher tiers are available (called "adaptive") that take advantage of context of security requests for risk mitigation, for companies that are extremely risk-averse or security-conscious.
Single Sign On (SSO)
Allows user to log into all OIN platform apps (see above) from a common identity. "Adaptive" mode allows creating policies around user login context (geo-location, device, network and risk contexts) to help limit risk. For example, it'd be impossible to be logging in from Hong Kong when you just logged in an hour ago from NYC. [This is obviously the product that people think of when they think Okta.]
- $2/user/mo standard
- $5/user/mo adaptive
Universal Directory
Cloud-based IAM, providing a single location to manage all users, groups and devices. Can authenticate against existing LDAP or AD service. Meta-directory can combine identity metadata from multiple sources. Integrates with all OIN apps over LDAP or API.
- $2/user/mo
MFA (Multi-Factor Auth)
Improve security beyond just security questions and passwords. Add MFA features to SSO logins, like (in order of improved security): SMS/voice/email OTP, software OTP, Okta's Verify mobile app, security tokens, and biometric checks. "Adaptive" mode allows creating policies around user login context (geolocation, device, network) to limit risk. For example, if this is a new device or location for the user, require additional MFA verification steps beyond the norm. [Side note, Okta uses Twilio for things like MFA OTP notices.]
- $3/user/mo standard
- $6/user/mo adaptive
API Access Mgmt
Centralize authorization and access control to company's own enterprise APIs via OAuth/OIDC. Configurable policy engine and audit trail.
- $2/user/mo
Lifecycle Mgmt
Automate any business process involving users. Manage identity access and automate triggered processes after workforce events via customizable policy engine. For example, auto-provision OIN app access after employee onboarding or dismissal. Integrates with Universal Directory or LDAP. Audit reporting and rogue account tracking. APIs to customize integration into existing IT workflows. "Advanced" mode ties into your company's HR application (like Workday) to drive the Lifecycle policies and event handling.
- $4/user/mo standard
- $6/user/mo advanced
[Oddly, I found a crack in the Okta website marketing. I have seen references to another product that is NOT currently in the list of Workforce Identity products, called "Mobility Management (OMM)", plus there is a non-working link in their Solutions list in the footer ("Enable a Mobile Workforce"). Found this old PDF that show latest release was this month, and I can see OMM was a heavy focus of Oktane18 sessions just a year ago. I believe device management capabilities got folded into Universal Directory & Lifecycle Mgmt products.]
Okta marketing highlights several ways the Workforce-oriented product line can help an enterprise:
- Protects against data breaches: Clearly, improved security is the forefront of what they provide. Centralizes identity. Enables strong auth. Reduces attack vectors. Improves visibility.
- Collaborate with partners: Faster integration by tying to their IAM/LDAP. Allow access to internal & external systems. Tightens security. Centralize and automate mgmt.
- Increase M&A agility: Faster integration of new acquires. Consolidate their existing IAM/LDAP, provides immediate access to needed systems. Easier onboarding of acquired employees.
- Reduce IT friction: IT can move way faster. Foster innovation, as can leverage new advancements in the Identity Cloud and OIN apps. Reduces manual work by automating account mgmt through lifecycle event triggers. Simplify by centralizing all identities. Decrease cost while increasing visibility into audit and risk.
Customer Identity
Outside of those workforce-focused products is the Customer Identity segment (originally known as API Products). These products are for tracking customer access by companies developing their own SaaS solutions, who want to manage their customer accounts while integrating better security and federation capabilities to be able to work with other systems. Once it gets embedded, the company can then easily tie their SaaS products into the Okta ecosphere (be in the OIN network). This "Customer Identity" segment was announced at Oktane18 in May 2018. These are relatively the same products from the workforce side, just packaged and priced differently, as they are exposed through APIs and SDKs that developers can integrate.
These tools gives SaaS companies a huge leg up in security and identity mgmt without having to code it all, plus having to maintain and monitor security and track risk, plus federated capabilities to make their application be able to inter-work with other SaaS apps. I think their Customer Identity side is pretty compelling for SaaS companies. The pricing seems quite good considering the employee and infrastructure resources they may be able to trim. Okta provides full SDKs across a wide variety of modern development languages, to get developers kick-started, and it supports all major security and data protocols to integrate it with a company's existing systems.
It is probably even more attractive to a company if they are already an Okta customer on the workforce side, as both sides of their business are centralized on the same platform. Adobe is one such Okta customer utilizing both sides.
Adobe did a major pivot to cloud, both in product (such as Creative Cloud, which took their softwares for creatives from licensed to SaaS) and in tooling (they shifted from on-prem hosted apps to the cloud). They left their legacy SSO solution behind and migrated their 20.5k employees to use Okta SSO to access 300+ cloud apps in only 3 months! Adobe then decided they needed federation capabilities and needed to add Creative Cloud to the OIN, so used Okta's developer tools to build identity services directly into their products. Today, all Adobe lines (Creative Cloud, Document Cloud, Experience Cloud) utilize Okta to manage customer identities, and all are integrated into OIN. As for lock-in, think Adobe is going to back Okta out of every product of theirs? They have a set annual fee for unlimited number of customer identities across unlimited products. That is about as sticky a service as it gets. Looking at the pricing, it appears the annual fee for a major Okta development integration like that covers about 1 programmer's annual salary. [News flash: most enterprises need way more than 1 programmer handling major security integrations in their products, while keeping security as tight as possible, while monitoring it all and reacting to breaches.]
Price for initial "developer" tier is based on monthly active users (MAUs), up to 50K MAUs -- until 2 higher enterprise pricing levels kick in. First 1000 MAUs are free, then each 2500 MAUs are $50/mo, up to 50K MAUs max at $1000/mo.
- "One App" ($17k+/annual) is mid tier, for unlimited MAUs on up to 5 OIDC clients.
- "Enterprise" ($42k+/annual) is the highest tier, for unlimited MAUs on unlimited OIDC clients.
Base tier (MAUs-based) includes Authentication, Authorization, User Mgmt, and basic MFA. Higher tiers allow add-ons for extra price: Directory Integration, API Access Mgmt, SSO Integrations, Inbound Federation, Adaptive MFA, Lifecycle Mgmt.
Authentication
Embed secure login and SSO into custom applications via SAML or OIDC. Reduces user friction. Enable logging in from OIDC enabled providers (Google, Facebook, LinkedIn, Twitter, etc). Custom emails and sign-in & registration forms.
Additionally, a new "Sign in with Okta" feature was also announced at Oktane18, which allows Okta to be the OIDC provider. Developers can add this feature to their web applications to allow users to log in using their Okta identity.
Authorization
API access management. Integrates with API gateways. Centralized administration with role-based access control.
Basic MFA
Embed MFA in Authentication. Allows only Okta Verify app and "bring your own SMS" OTP (so you have to configure a custom SMS provider, like Twilio).
User Mgmt
Universal Directory to manage users and groups. Frictionless user registration. Progressive profiling (adds user details as needed).
Add-ons include:
- MFA ($8k/annual, Adaptive $16k/annual) = Embed MFA beyond the basic tier. Set login and auth policies based on login context (location, device, network, risk context). Password-less authentication allowed, using email-based "magic-link".
- API Access Mgmt ($8k/annual) = Centralize authorization and access control. Configurable policy engine and audit trail.
- SSO ($2K/annual) = Allow customers SSO access to OIN apps
- Lifecycle Mgmt ($10k/annual) = Automate lifecycle of any business process involving customers. Integrate with CRM.
- B2B Inbound Federation ($8k/annual) = Integrate with other identity providers via SAML or OIDC using custom branding.
- B2B Directory Integration ($21k/annual) = Connect to your customer's LDAP or AD server. Synchronize into Universal Directory.
Some solutions that Okta highlights that these products solve:
- Secure and seamless customer experience.
- Centralized global identity for customer across your company.
- Seamless interaction across omni-channel (login & registration).
- Frictionless interactions (no more requiring long forms).
- Centralized management of customers and access rights.
- Increase speed to market.
New Pivots
Oktane19, their annual customer & developer conference, just occurred in this past week. Several new products were announced. And in my eyes, they are really increasing the stickiness of their platform with these products. (Names are links to the PR announcement or marketing page.)
Okta Hooks
Customers can use code to customize Okta policies and behaviors. Increases extensibility of platform, as it enables new custom integrations and downstream workflows. This is a new core functionality in Okta Identity Cloud. Hooks really increase customer lock-in, as it allows businesses to tie Okta into internal processes more tightly.
This also greatly enhances their Customer Identity offerings (developer APIs and SDKs), as this allows a huge degree of customization over what was allowed before.
Inline hooks can pause Okta workflow to add info or decision or make an API request. Enterprises can hook into their internal systems as needed, and pass info into Okta.
Sample uses:
- performing user validation during registration
- calling external dbs for OAuth/SAML checks
- enriching profile/metadata from HR or CRM systems
Event hooks are notifications to a customer's downstream services when an event of interest occurs.
Sample uses:
- having a user delete event trigger a call into customer's CRM or IT systems
- enroll new users into CRM marketing campaigns during registration
- push profile changes to internal marketing systems
- automate IT service mgmt
Okta Identity Engine (OIE)
Perhaps taking a cue from Twilio Flex, but Okta is now breaking down their API workflow into a series of building blocks that can be customized & better integrated into a customer's workflow. This allows a customer to customize Okta to exactly their own needs. As with Okta Hooks, tighter integration means increased lock-in, plus a lot more customization is now allowed.
Sample uses:
- Password-less users: customers can build systems with secure registration and authentication w/o password, using contextual info (geo-location, application used, email, push codes).
- Progressive profiling: prompt users for more profile info when needed. Leave long registration and order forms behind, the system collects that data when it needs it.
- Per-app branding in registration or authentication workflows.
Risk-based Authentication
Keep high level of security while removing user friction during authenticating. On each login, system observes contextual variables (device, location, IP, typing biometrics, etc) and builds profiles of each user as a sort of "Digital DNA" of their login pattern.
Risk-based Auth model calculates the risk of each login event and scores it. Model will continually improve via ML, tuned to each user's behavior at login. Admins can pair risk levels of various auth methods with different responses, and can trigger more auth steps or custom actions. If user fails, all sessions can be cleared and password reset can triggered.
(Currently in beta. Part of Adaptive MFA.)
Advanced Server Access
Extends identity services to infrastructure. Centralizes system access controls across on-premise, hybrid and cloud infrastructure (Linux and Windows servers). So now Okta is extending it's platform to help manage sysadmin access to a company's servers. This really helps any organization that maintains its own infrastructure, but is even more vital for companies that are moving into hybrid setups that are inherently more complex. This seems like a VERY easy up-sell for existing customers on the Workforce products. It is already appearing on Workforce Identity product page (but not the Pricing page yet).
This will prevent credential theft, and helps centralize server access with a seamless access experience via SSO. "Continuous Authentication" will allow customers to move on from using static keys, as credentials can now be ephemeral. It employs single-use credentials for each sysadmin login. Identity workflow manages who can access what, and from which device. Each certificate expires after a single use.
Allows granular access decisions in each login request (considers device, session context, user info). Okta can be used for server management, and can leverage its other products (Universal Directory, Lifecycle Mgmt, SSO, Adaptive MFA).
Access Gateway
Extends Okta from managing cloud applications to on-premise applications. Centralizes access for hybrid enterprises, creating further lock-in. Allows SSO & Adaptive MFA access to on-premise apps. Makes transitioning legacy softwares easier. Must deploy a proxy on-premise or in cloud provider of choice. [NOT GA YET, later this year.]
Okta Ventures
Not a product, but Okta is starting an in-house VC fund like Google Ventures. $50M investment fund focused on solutions in identity, security, and cutting edge related technologies (AI, ML, blockchain). Further strengthens OIN as new SaaS tools emerge. First investment is Trusted Key, secure digital identity w/ blockchain.
Acquired Products
And while we are at it, let's look at Okta's recent acquisitions and see how those are going to fold into product line.
ScaleFT (Jul 2018)
Techcrunch article on ScaleFT acquisition.
The Advanced Server Access product just released is all from last summer's ScaleFT acquisition. The ephemeral client certifications that enable "Continuous Authentication" methods are directly from their Server Access product. Most likely ScaleFT underpins their new Access Gateway product as well. A great move by Okta, keeping itself on the forefront of security technology, and especially with the burgeoning Zero Trust initiatives being widely adopted. Really really fantastic acquire that resulted in 2 new Zero Trust products focused on hybrid environments.
Their Zero Trust Access Mgmt platform has 2 sides:
- Zero Trust Server Access = Ephemeral client certificate architecture for admin access to infrastructure. Essential in cloud and hybrid deployments, and distributed architectures. [Definitely is core of their brand new Advanced Server Access product.]
- Zero Trust Web Access = Centralized gateway for all web application access. Policy-driven access control. Transparent to end user. [Likely underpins their new Access Gateway product. Okta hasn't released enough details yet since it isn't GA.]
Azuqua (Mar 2019)
Techcrunch article on Azuqua acquisition.
Allowed for quickly creating complex workflows between SaaS tools, in a no-code visual designer. 200+ existing SaaS integrations [they were starting to build a mini-OIN]. Graphical workflow designer (which they called a "FLO") that allows making a flow-chart like connection between elements, where events flow left-to-right. Place and configure 'Trigger Events', Actions' and 'Logic Functions' in order to automate workflow between multiple integrated apps. Can embed no-code handlers for logic, math, data manipulation, integrate API calls, etc. Full list of handlers here. Everything is just a little logic or data building block.
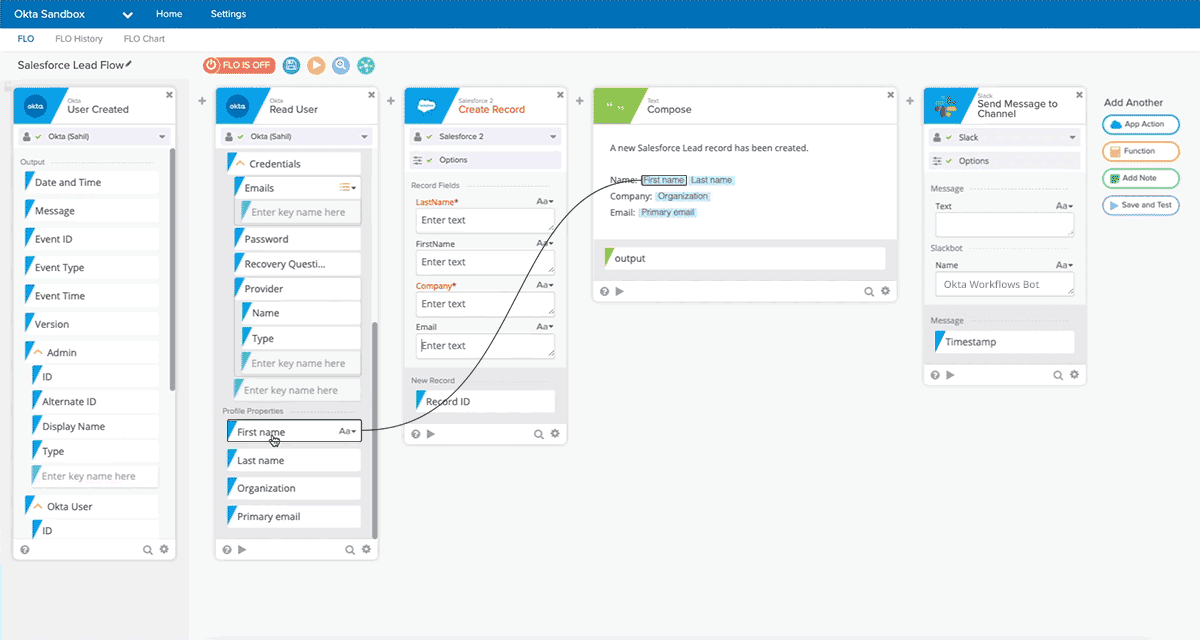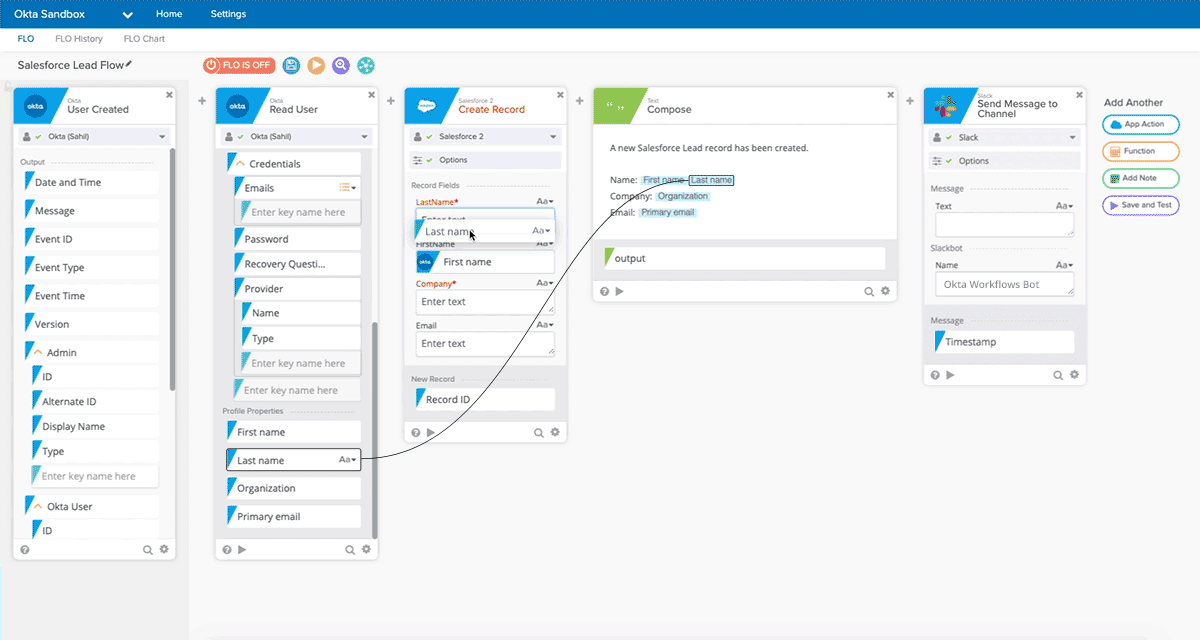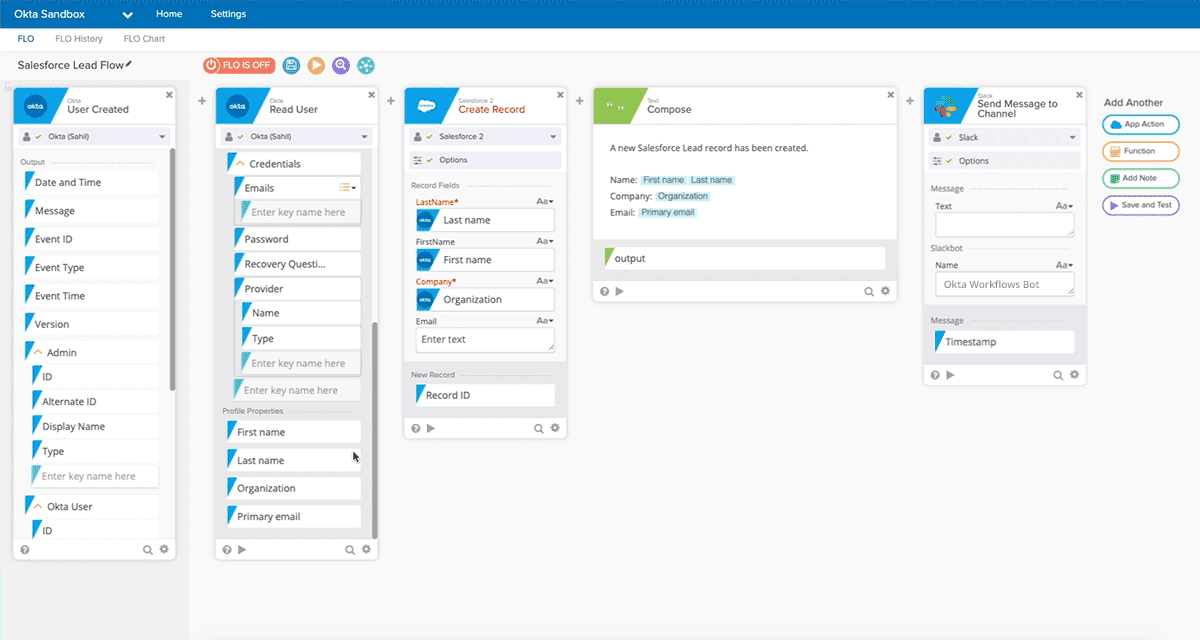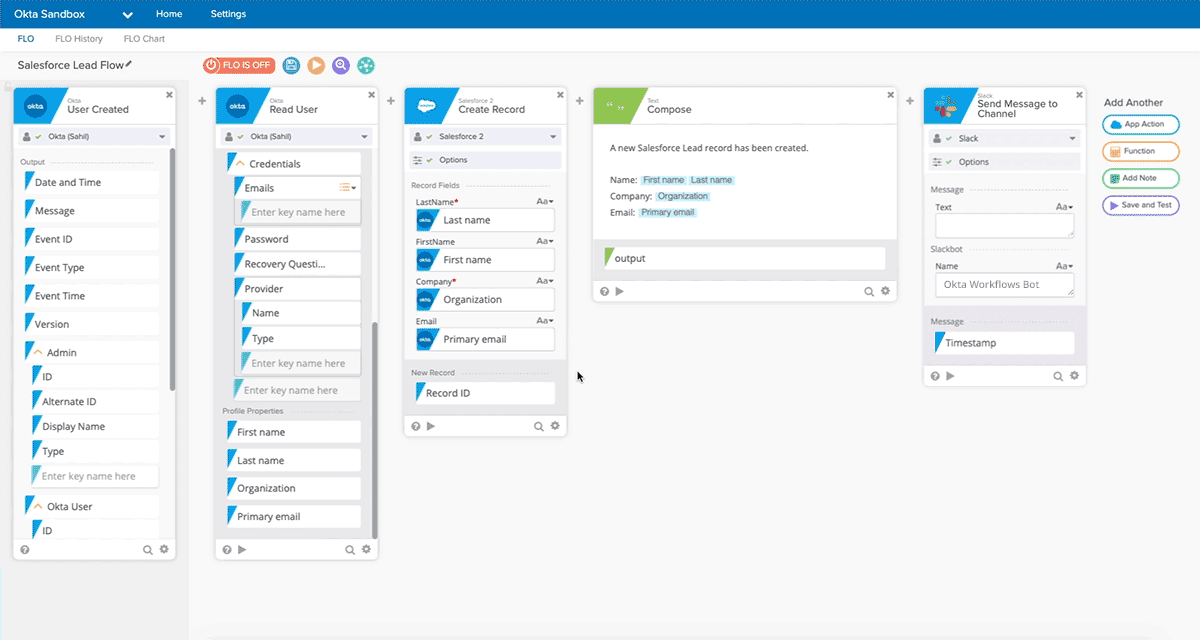
As an example, you could have new employee event in Workday trigger provisioning actions in other SaaS tools (create new user, grant certain rights based on their role). Or a new sale in Square or Shopify could add a user to Marketo campaign.
Once again, a brilliant technology and talent acquisition. This expands Okta's workflow capabilities, and supercharges it by hooking it up to the 6000+ integrations in the OIN. [I could get into their pricing, but I think it's moot as seems likely to be discontinued as a separate product, and will get integrated as a new UI over Lifecycle Mgmt and tie into the new Okta Hooks.]
Some marketing facts on their site:
- 1000+ avg unique SaaS apps in use in the average enterprise company.
- Each app has 6+ interdependencies w/ other apps.
No wonder Okta having great success!
Final Takeaways
In terms of SaaS tooling, I like to break them into several categories:
- business-operations enterprise apps (planning, CRM, HR, inter-communication, document mgmt, finance, B2B platforms, conferencing) ...Workday, ADP, Paycom, Salesforce, Marketo, HubSpot, Cvent, Concur, Slack, Office365, G Suite, Dropbox, Adobe, Zendesk, ServiceNow, DocuSign, Coupa, Zuora, Shopify, Square, Anaplan, Zoom, on and on and on... [Yes, this category could be further broken down into biz departments, but I like to throw them all into one bucket of "Biz Ops"]
- developer and data tools (databases, PaaS platforms, APIs, coder tools, ETL) ...Elastic, MongoDB, Twilio, Github, Atlassian, Pivotal...
- IT/Security related (IaaS cloud compute, networking, user managing, auditing, monitoring) ...Zscaler, Splunk, New Relic, Apptio, PagerDuty...
- analytics, ML and data flow, which can overlay any/all of those other categories ...Alteryx, Cloudera, Tableau, Talend...
Before now, I would have placed Okta in the IT/Security category (in a way that oversaw biz-ops use of SaaS apps), but after this exercise, I now realize that Okta seems unique in that it spans ALL these categories. It is a business operations app (manages employees AND customers, manage and automate workflows between biz-ops tools), a development tool (integrate better security & SSO into your company's applications, hook your app into OIN), IT & security app (manages users, security monitoring, allows access to SaaS apps) that incorporates analytics & ML (the new Risk-based Authentication scoring system uses ML to score risk of user actions).
I said in a recent earnings writeup that I have been prepared to demote Okta to '2nd Tier' due to declining growth. After this review of their product line and where new products are heading, I am taking that back -- as well as my thoughts on the stickiness of its products compared to Zscaler. Okta is clearly intent on embedding itself deeper and deeper into the workflows of its customers. I will be keeping Okta in the "top tier" of my holdings until another company can prove itself more invaluable to businesses. And even then, Okta is likely to remain a 2nd Tier holding for a long while thereafter, as this company's revenue streams are going to have a very long tail. Okta itself is benefiting from this transformation in business technology tooling -- as all our other SaaS companies grow and succeed, so to does Okta.
Some long-tail reasons...
- Of anything, I love that Okta seems future proofed; its customers will always need identity management, and once on the platform there is NO incentive to go back, nor seek cheaper alternatives. Costs seem very reasonable, compared to the savings they will get in employee/infrastructure workload. And the platform can only improve from here. Disruption seems... unlikely.
- Okta solves problems across the entire organization. (HR, sales, development, IT/networking, infrastructure) Infrastructure gets simplified. HR & IT gets their processes simplified and automated. Developers get a kickstart into securing their apps w/ federation capabilities. Sales gets exposure from federation and being in OIN.
- It further strengthens OIN as new SaaS tools emerge. Okta is benefiting from this wave of Saas/IaaS/PaaS tooling that companies MUST utilize in their day-to-day business operations, security, monitoring and analytics. As all our other SaaS tooling companies succeed, SO DOES OKTA. (Just as we investors in those tooling companies are.)
- So many of our SaaS tooling companies are inter-dependent on each other, so they all succeed together. Okta provides identity mgmt and SSO over Twilio, Elastic (Kibana), Zscaler, Smartsheet accounts, etc. Okta uses Twilio for MFA. Twilio uses Okta internally. Okta partners with ZScaler. Okta partners with Sailpoint.
- Okta provides a development platform for companies to re-architect the user identity processes in their own applications. Like Twilio, they provide building blocks for helping companies develop their own applications. So companies are embedding Okta directly into their applications for handling identity, security and federation (inter-working with other apps). This is extreme lock-in.
- Okta is sticky. Both Zscaler and Okta are both eliminating the alternative methods -- there is no going back to the old way of doing things once a company commits to these paths. They are only going to be losing a customer via competition or disruption.
- Okta is getting stickier. The level of customization and automation of workflows that can occur locks Okta in further to its customers. And it is still growing, w/ the recent acquisition of Azuqua, and the introduction of Okta Hooks and the building blocks of Okta Identity Engine.
- Okta is STILL riding the cloud wave as companies adopt SaaS cloud tools more and more. However, Okta is now also riding the hybrid and multi-cloud trends as it adds multiple new products focused to help companies manage this complex arrangement. In particular, the new focus on Zero Trust is really going to resonate. The Advanced Server Access product (acquired from ScaleFT) looks like a complete no-brainer for any existing Okta customers with infrastructure to bolt on to their subscription.
- Like Zscaler, being a security-related SaaS means they gain a huge benefit from analyzing the usage logs of every interaction from every user on their platform and can feed that into ML algorithms for risk management and breach detection. Hardware device companies and stand-alone products CANNOT DO THIS, as every company using it is its own island of data. Okta benefits from the COMPLETE VIEW over its own platform in order to further improve security of its products.
- Okta is finally exposing analytics and ML with their new Risk-based Authentication system in Adaptive MFA, where they can analyze and score the context of user authentication requests to measure risk, which in turn allow customers to adapt responses based on risk level (such as adaptively requiring additional MFA checks, or temporarily disabling the account). I think this exposure of ML features for customer use will only expand from there. Taking that out a bit wider, I wonder if they could transition into performing analytics as a service around other aspects of identity beyond auth security. It would be possible to inject analytics or ML into some of the workflows between OIN apps. It will be interesting to see where it goes from here.
Whew! That was a lot of words! I hope you found it of value. I most certainly did.
-muji
