This is part of the Flavors of Security series, in particular Part 2’s investment focus on what drives the hypergrowth stories within the cybersecurity space. If you need to learn the security terms & product abbreviations, you can look up the terms that first post.
Zscaler (ZS) = Outgoing Protection + Incoming Protection (Zero Trust)
Platform: ZScaler Cloud Security Platform
Ecosystem: N/A
Partners: Zscaler Partners
Flavors of Security:
- Current: SWG, CASB, DLP, NGFW, IPS (ZIA product)
- Next wave: Zero Trust (ZPA, B2B products)
Massive Tailwinds:
- Adoption of SaaS biz-op enterprise services
- Migration to cloud
- Mobile workforce
- Growth of mobile devices and BYOD policies
- Software driven networking (SD-WAN)
- Zero Trust
- ML/AI-driven Security
Differentiators:
- Cloud-native -- no appliance or infrastructure needed. Infinite scale, unlimited capacity.
- Complete view of customer security.
- Platform w/ incremental add-ons, with a network of security partners.
- Global footprint of 150+ datacenters ensures a nearby gateway/proxy into their global private network, allowing for things like SSL inspection & bandwidth control (things that competition can't do as easily).
- Strong adoption of ML/AI (acquisition of TrustPath).
- Fully embracing Zero Trust.
Platform capabilities:
- Access: SWG, Cloud Firewall (NGFW), Zero Trust
- Prevention: SSL Introspection, CASB, DLP
- Protection: IPS, Sandbox, NGAV
- Monitor: Continuous Monitoring
Products:
ZIA
- Secure Web Gateway (SWG)
- SSL Inspection - This is a key feature - their proxy network allows them to introspect ALL traffic.
- Malware Protection (NGAV) Protect systems from malware within network traffic.
- Cloud Firewall (NGFW)
- Cloud IPS threat detection
- Cloud Sandbox which now shares and blocks discovered threats across all customers
- Cloud App Control (CASB)
- Cloud DLP
- Bandwidth Control
ZPA & B2B
- Zero Trust Network Access (ZTNA) replaces need for VPNs or WAF & API Gateways
- B2B (ZTNA) Zero Trust based micro-networks between groups
Other Environments
- Zscaler FedRAMP Cloud - for US fed/state/local govt agencies
Subscription Levels ("Bundles"):
ZIA
- Professional - base level of ZIA with SWG, NGAV, and entry level Cloud Firewall and Cloud Sandbox
- Business - ... plus SSL Inspection, Bandwidth Control, SIEM logging integration
- Transformation - ... plus Advanced Cloud Firewall, Cloud IPS, Advanced Cloud Sandbox
ZPA
- Browser Access - base level of ZPA for 5 web-based apps
- Professional - ... adds adds ZScaler App (native agent), allows non-browser-based apps
- Business - ... adds up to 3000 apps, device policies, improved visibility (full monitoring & logging)
Partners:
Links to partnership marketing.
By technology:
- IAM (like Okta, PingID, Microsoft, Centrify, OneLogin, Dell/RSA)
- CASB (like Bitglass, McAfee, Microsoft)
- DLP (like Varonis)
- SIEM (like Splunk, IBM, LogRhythm)
- SOAR (like Splunk, LogRhythm)
By partner:
- Okta (IAM)
Magic Quadrants:
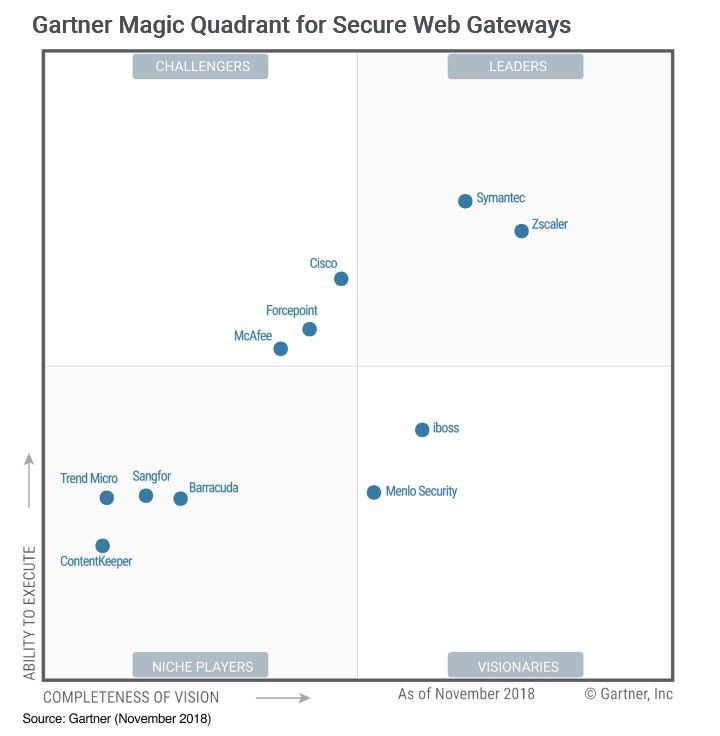
SWG:
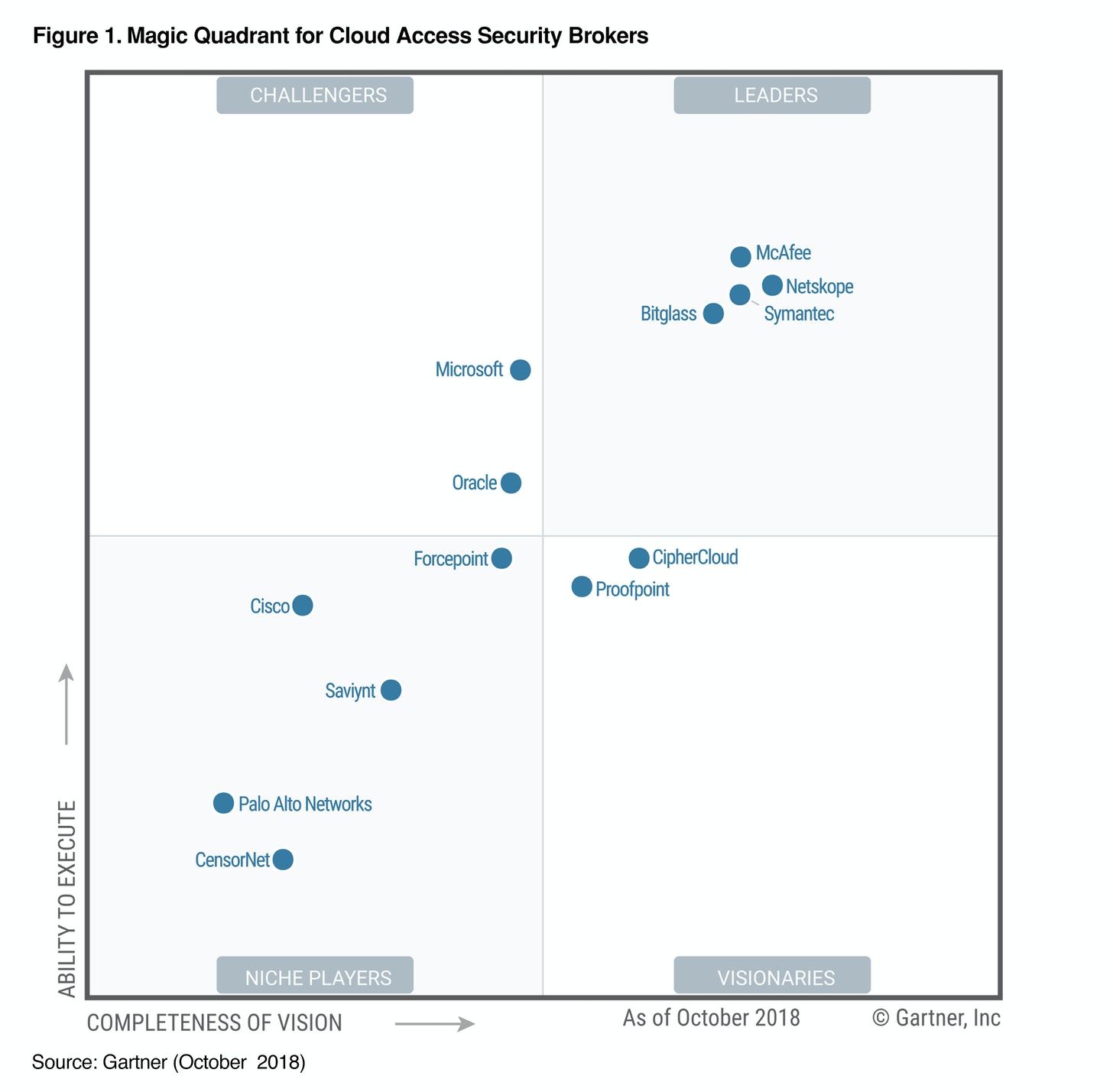
CASB: (no Zscaler shown)
ZTNA/IAP: no MQ yet but see the Gartner Zero Trust report
Competitors:
- SWG - Symantec, McAfee, Cisco, Forcepoint
- CASB - McAfee, Bitglass, Symantec, Microsoft, Oracle, Cisco, Netscape
- Mobile Threat Defense - Symantec, CheckPoint, Palo Alto, Blackberry, IBM
- ZTNA/IAP - Okta, Cisco/Duo, Google, Akamai, Cloudflare, Symantec/Luminate, Palo Alto
Gartner customer reviews:
Thoughts:
Zscaler built ZIA, a Secure Web Gateway (SWG) product for securing outgoing traffic to SaaS services, in a unique way. They built their own global private network, now across 150+ data centers, to serve as a gateway between the user and the service being requested. Endpoints must use an installed agent to access the Zscaler cloud. This private proxy network allows for SSL introspection globally across all of a customer's traffic, which is a key differentiator against the competition.
In 2016, they made a fantastic pivot by adding ZPA, a Zero Trust access system for incoming traffic. They leveraged their existing architecture to a different end path -- instead of users only accessing external SaaS services, it could also enable access to a customer's own hosted services (databases, internal software, and APIs) regardless of location (on-premise, data center, or cloud). So in a nutshell, Zscaler now secures both outbound (ZIA) and inbound (ZPA) traffic from all of a customer's endpoints.
Zscaler's CEO once stated: "We feel the world is coming towards us. I will highlight three key trends. An increasing adoption of SaaS applications, and Microsoft Office 365 in particular; SD-WAN projects that transform the legacy hub and spoke network; Application migration to public cloud using AWS, Azure and Google." [SaaS growth and migration to IaaS are the recurring theme behind the success of our cybersecurity hypergrowth stories.]
Together, ZIA & ZPA are a simpler and cheaper way to secure all your endpoint traffic than a traditional corporate network utilizing a WAN or VPNs for trusted interconnectivity. The move towards SD-WANs and Zero Trust is allowing the internet to be the company network. No more perimeters at all!
For pricing, Zscaler ZIA has 3 "bundles" subscription tiers ("bundles") - Pro, Business and Transformation. Zscaler ZPA has 3 tiers as well - Browser Access, Professional and Business. The marketing is a bit of mess, so it is difficult to understand what the tiers really provide from Zscaler's product line. You can immediately see an issue -- the naming of the tiers isn't aligned -- "Professional" is entry level on one side and mid-tier on the other. [More on this in Concerns below.]
As was mentioned for Okta, Zscaler also finds itself competing against some of its partners. Zscaler has expanded their product line to include features that some partners already provide, like CASB/DLP (part of ZIA's services) and NGFW/WAF (features that ZPA does away with). So Zscaler plays it both ways, and can integrate with tools that customers are already using if need be. Zscaler MUST tie into an external IAM service to provide authentication, so it pairs well with Okta. It also has an extensive logging system that ties into external SIEM & SOAR systems for customers to have visibility and orchestration.
A newly announced product is "B2B", which is only in beta (or "limited release") at the moment. It expands on the ZPA product, but instead of being focused on a single customer, it will allow multiple customers to pool together to create micro-networks between themselves via Zero Trust, and is closely managed by a shared IAM service. It basically sounds like a shared ZPA between businesses that are inter-operating with each other. Fantastic addition to their product line, which greatly expands the potential for the Zero Trust side of the platform, and, as a huge plus, it puts a lot more urgency into its immediate need, given that it enables secure interoperability between businesses.
I would have first guessed that Zscaler would be getting more into endpoint device protection (EPP/EDR) from here. They are already securing the endpoint's traffic with ZIA/ZPA, and specifically state they act as an NGAV for malware detection over that traffic. It seems they could easily pivot to provide a EPP/EDR capabilities within their already installed agent (which is required to use Zscaler's network). However, they just announced that they have partnered more closely with CrowdStrike and their EPP/EDR platform. That partnership does compliment each other's services very well - Zscaler is protecting the outgoing and incoming traffic from a device, and Crowdstrike is protecting the device itself. They are cross-enabling intercommunication between their platforms, to better tie together the device protection with the network protection, and I can imagine that becomes a strong pairing as they intertwine the interoperability and ML/AI more and more. So I guess I can strike off EPP as a direction they move internally.
That leaves IAM as a likely next area that Zscaler could ultimately move into; Okta is already moving towards Zscaler (Access Gateway competes with ZPA), so perhaps Zscaler will move towards Okta, and eliminate the need to integrate with an outside IAM for identity mgmt over their products. Given that all Zscaler products require an IAM to control access, this would be a very complimentary direction for them.
Strengths:
- Top name in SWG (one of only 2 leaders in the Gartner MQ), it gained momentum to become a Category Crusher once GE adopted it, validating it in a major way. Microsoft considers them a major partner to help secure a customer's connectivity to Office 365 (regardless of the crap Palo Alto is peddling).
- It is a cloud-native SECaaS that is analyzing and gaining insights from a complete view over ALL their clients (no more islands). They are incredibly well positioned to manage the security of their own service plus that of their customers. They can scale as usage demands.
- Their private network of gateways at their 150+ data centers (and growing) gives their customers an additional layer of security over public internet, plus enables a lot of desirable features like SSL Introspection (deeper level of inspection than DPI) and Bandwidth Control. They use an installed custom app to allow endpoints to connect seamlessly to the nearest gateway in order to use ZIA and/or ZPA. They can act as a giant VPN for a company's users to be able to access all the needed external and internal services over their private network. And their proxy separates their customers traffic, akin to being in a HUV lane on the internet.
- ZPA, their Zero Trust access product, is doing away with the need for VPNs or traditional WANs. It acts as a next-gen firewall & WAF & API Gateway in one, but is much more secure and flexible than appliances. It leverages their existing Zscaler Cloud Network built for ZIA, so they now secure both outgoing and incoming traffic for endpoints.
- They have an extremely sticky platform, and are integrating with partners into multiple different security directions from there (IAM, CASB, DLP, SIEM, SOAR). Customers can use them a little or a lot, as desired (depending on their existing infrastructure setup and how "all-in" they want to go), so there is a huge ability to land-and-expand, as customers get to know the benefits of the product lines. Lots of angles they can play to get initially embedded into a customer's existing setup - the move towards SD-WAN as customers deal with multiple locations or acquisitions, and the move towards mobile workforce as customers deal with getting rid of VPNs to access their internal software & outside SaaS services. [However, see the Concerns - perhaps land-and-expand isn't the focus any more.]
- Global 2000 customers were up +33% last Q, so the bigger companies are taking notice after GE got the ball rolling, validating the concept. Zscaler has stated that the deals are getting larger up-front as more companies start with Zscaler "all-in" instead of piecemeal.
- They are fully embracing ML/AI for threat detection capabilities. They acquired TrustPath a year ago in order to expand their ML/AI capabilities for threat detection. And it has a CARTA mindset, as it is using ML/AI to provide contextual- and behavior-based adaptive rules. Their CTO had a good writeup on the importance of ML/AI in cybersecurity:
- I feel that Zscaler's products are about as sticky a service as it gets. Once a company goes towards the Zscaler Cloud Platform, it is going to be VERY difficult for them to pry them away. Enterprises are never going to return to self-managed networking once they have gone to a cloud-based service like Zscaler. The only place a customer could migrate to is a competing platform, but Zscaler is the only company I've seen where "your enterprise network is the internet". ZIA (outgoing protection) and ZPA (incoming protection) are a VERY powerful two-sided punch.
Concerns:
- ZPA is a fantastic add-on service to ZIA, so it now is covering both directions of traffic from endpoints (outgoing and incoming traffic) over their same private network. However, I am not sure that ZPA is driving non-ZIA customers to sign up for just that service, as it seems to me to be more positioned as an add-on to the existing ZIA customers. This seems like a correctable sales & marketing issue. Also, B2B seems to improve upon the scope of ZPA, and fulfills a very common need that should increase the urgency for companies to sign up, as it enables secure inter-collaboration of services between a given group of businesses.
- Zscaler does have a wide variety of partners it works with (IAM, SIEM, etc), but, disappointingly, their partner initiatives seem weak compared to Okta's and CrowdStrike's. They just publish a list of partners and have docs to show how to integrate with them. A better solution would be an ecosystem for customers to engage with partners and to integrate directly with their services. CrowdStrike even publishes a set of APIs for integration. I think Zscaler could improve here.
- Zscaler appears difficult to implement, at least for companies going "all-in". They have a heavy reliance on System Integration partners, like Deloitte, Accenture, Cognizant, and Infosys, and on system network partners like AT&T, Sprint, Verizon, BT, and Tata . My initial understanding of Zscaler was that it could be bolted onto existing WAN network setups for initial projects (like Office365 protection) and worm their way into more from there (land-and-expand), but they have been saying that upfront deals are larger now. Larger deals require a longer timeframe due to the complexity to plan and set up (hence the integration partners). As just mentioned on their latest earnings call, they are starting to have some difficulties in closing these larger deals in a timely fashion. This is disappointing. However, they just hired a new CRO role to specifically tackle these issues. Hopefully they start to focus on some self-install capabilities for certain marketing angles (to allow customer to be more nimble, and putting Zscaler back into "land-and-expand"), while still working on the "all-in" larger deals of the bigger enterprises.
- Surprised to see Google missing from Partner list and from ZPA integrations. ZPA is only available on AWS and Azure. Perhaps it is due to Google "BeyondCorp" being a direct competitor to ZPA. However, GCP is a distant third place behind AWS and Azure cloud platforms, so likely not that much of a negative. But it makes me curious.
- Their marketing is completely unclear on what services are provided per subscription level (which they call a "bundle"). They need a lesson from Crowdstrike and Okta, who make it incredibly clear exactly what features are included in each tier (or a la carte in Okta's case), and what the per-node prices of each are. Zscaler's descriptions are fuzzy, and do not correlate one-to-one with services in the product line, nor do they provide links to pages in the product line explaining the details of each. They aren't clear on what the differences are between Standard and Advanced levels of Cloud Firewall - I had to dig into a white paper to find out. There is no pricing shown, you have to request a quote and engage a sales rep. They have a fantastic product line, but the marketing on their pricing tiers is a mess. The new CRO has a lot to fix here.
As an example, on their difficult-to-find pricing page click "Compare ZIA Bundles". An item in the feature list is "Advanced Threat Protection", that kicks in at Business tier. What is that? That is NOT something in the product line. The only reference on their website to "Advanced Threat Protection" is under Solutions. There it talks about SSL Introspection and Cloud Sandbox. But those are items already in the feature list.
