Twitter (TWTR) just had an extremely high profile hacking. The outward appearance was that it was for stealing bitcoin, but the deeper implications are enormous. It seemed to affect “blue checkmark” users more than others, which are verified VIP users like politicians, celebrities and CEOs. The bitcoin attack may a smokescreen. Were DMs compromised? Were other posts beyond the bitcoin traps made? The goal could ultimately be blackmail, data harvesting for analytical profile building on targets, or could be a nation-state sanctioned hackers trying to influence politics or causing geo-political strife by putting words into people’s mouths. Even if this was ultimately a complex method for stealing bitcoin, the hackers could also have sold their discovery to others that want to do those other things.
We know very little about it yet, as far as who the malicious actors are and what their intent is. But after their initial investigation, Twitter finally isolated where the hack came from:
We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.
— Twitter Support (@TwitterSupport) July 16, 2020
Looking at the response across Twitter, “social engineering” doesn’t seem to be widely understood. It means MANIPULATION of PEOPLE. I defined it as this, in my Flavors of Security series last fall:
- Social engineering = Use of deception to fool employees into divulging information or system access that they should not be (aka the human element). Beyond network security, the workforce itself is a security factor, where you need to provide education on being security conscious and aware of the threats (employee could click on malware, or could accidentally provide PII or credentials on the phone to a deceitful caller). And attacks aren't solely from the outside of your network - employees can have malicious intent. Companies have to remain diligent in their security efforts, and can never let their guard down.
Many on Twitter are assuming that this just means phishing, but phishing is but one example of a social engineering attack vector. 25 years ago, as a young programmer/hacker, I was fascinated by the story of Kevin Mitnick, a notorious hacker that was the master of social engineering. He became incredibly adept at getting corporate secretaries and employees to give up corporate secrets or grant him access to secure systems. After eventually getting caught and doing jail time, he became a consultant that specialized on helping companies combat his techniques, later writing books like “The Art of Intrusion: The Real Stories Behind the Exploits of Hackers, Intruders & Deceivers”.
Recently, many cybersecurity SaaS providers have been sounding the alarms that hacking attempts are increasing right now. Hackers attempt to take advantage of confusing situations, and the last few months of pandemic and stay-at-home have been a ripe field for exploiting that confusion. It is important to remember that ultimately, these administrative systems are managed by humans. Some companies I am aware of that are dealing with the human component are:
- Proofpoint (PFPT) focuses training to stop social engineering attacks, and protecting data in order to reduce exposure risk.
- Perched, acquired by Elastic in Aug 2019, focuses on training and consulting to help stop social engineering attacks.
Speaking of Proofpoint, Okta recently announced a cybersecurity provider partnership to attempt to cover a wide part of the protection needed to keep enterprise users safe in today’s chaotic environment.
- Okta (OKTA) is the IAM, handling identity & access rights.
- CrowdStrike (CRWD) is the EPP, handling protecting endpoint devices (laptops, mobile devices) of those users.
- Netskope (private) is the CASB, handling security policies and vision into usage of external SaaS tools.
- Proofpoint (PFPT) is the social engineering focus, handling protecting data and the workforce, and, importantly, educating that workforce. [They are not hypergrowth, so I do not follow them that closely.]
These 4 partners are going to interexchange data and better integrate with themselves, in order to try to fully protect an enterprise’s workforce.
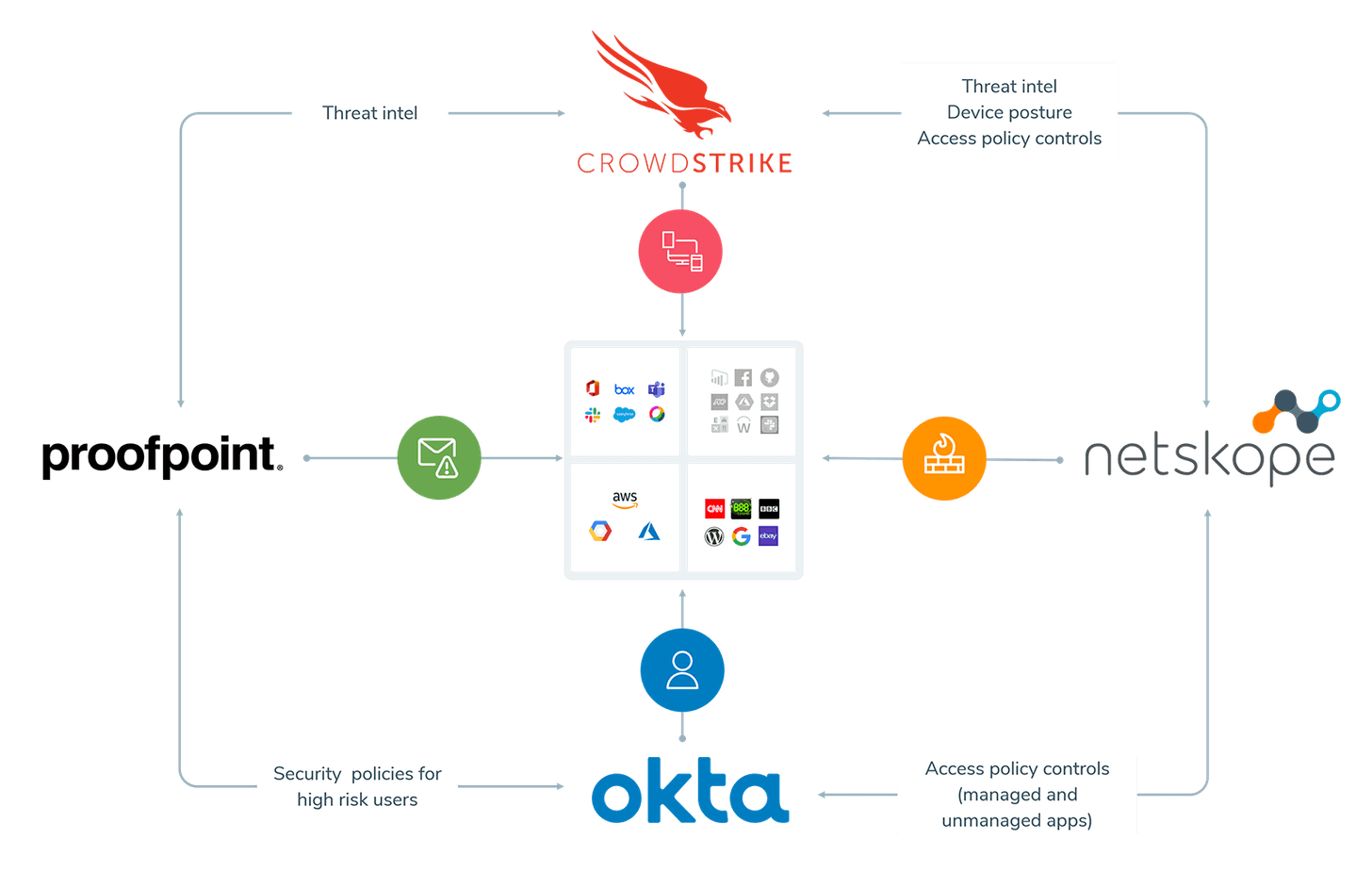
Okta is keeping neutral on CASB and continues to rely on partners for that feature (Netskope in this case). I envision that they may ultimately try to enter this market themselves, as it seems an easy pivot for their existing platform.
It appears the focus of this partnership is in covering the security over the enterprise workforce’s devices and usage. But that leads me to a criticism - one component that is missing is protection of traffic from that workforce’s devices (endpoints). So I expect this partnership to expand from here to ultimately cover traffic protection (outgoing and incoming).
For protecting the traffic between your workforce and your external SaaS tooling (outgoing traffic), this is covered by Secure Web Gateways (SWG), like Zscaler’s ZIA or Cloudflare’s Gateway products. Zscaler has already partnered with CrowdStrike to try to provide a device+traffic protection duo.
For protecting traffic between your workforce and your own company’s infrastructure (incoming traffic), that is covered by Zero Trust products. This is a market that Okta has started to enter in itself, after its acquisition of ScaleFT in July 2018. In particular, Okta’s Access Gateway product is similar to Zscaler’s ZPA and Cloudflare’s Access product in their new Cloudflare for Teams.
Twitter is making an example of why this is all important. They have been very vocal about ultimately allowing employees to work remotely for the long-term, but that means lots of scattered users need to have access to their internal systems. They are proving to be the poster child for why adopting a Zero Trust policy is important, as well as the need to educate your entire workforce on cybersecurity policies. Companies need to be able to monitor its workforces’ devices and usage, and apply analytics in order to detect anomalies (the CARTA mindset). As this partnership shows, all these angles of protection combine, and have now evolved into a new security paradigm called Secure Access Service Edge (SASE) by industry minder Gartner (pronounced “sassy”).
Bottom line is, every company now needs to protect, monitor, educate and adapt quickly in terms of protecting their users, including both their devices and their traffic. That is driving a lot of success in these hypergrowth companies right now, and will continue to for the foreseeable future.
Add’l Reading
If you want dive deeper into hypergrowth in cybersecurity providers, I recommend reading the following, in order.
- My prior Okta (OKTA) technical review from April 2019.
- My prior CrowdStrike (CRWD) deep dive from May 2019.
- If you need help understanding cybersecurity terms, and are investing in cybersecurity SaaS companies, I highly recommend you take an hour and absorb my cybersecurity tech review from October 2019 called Flavors of Security, and then how certain solutions are achieving hypergrowth in Part 2, including specific breakdowns of Okta, Zscaler, CrowdStrike and Elastic. (I consider them followups to read after the deep dives linked above.)
And to dive into the evolution of how Gartner has defined this security need:
- Gartner - Guide to Zero Trust (ZTNA)
- Gartner - Zero Trust is first step toward CARTA
- Gartner - The Future of Network Security is in the Cloud (SASE)
