What is an enterprise network for? To securely interconnect an enterprise's workforce to the systems and apps used across its operations, across all the locations of that enterprise. But, of course, the Internet changed how the perimeter of an enterprise network now looks. In today's modern global economy, enterprise networks are expanding in many different directions, all at once. The data center is moving more into cloud IaaS platforms. The workforce is no longer solely in centralized locations, and is now heavily working remotely. The locations might be expanding globally, and be mobile or pop-up (ephemeral). The apps are moving from data centers to cloud SaaS or PaaS services.
New solutions have emerged to help companies cope with this continual expansion of an enterprise network's boundaries. But before we get to the solution, let's take a quick walk through how we got here first.
An Especially Brief Evolution of Enterprise Networking
In the olden days of centralized enterprise networks, all software was installed on-premise, and the entire enterprise network was managed and secured by a plethora of networking appliances (routers, switches, firewalls, and the like). Beyond interconnecting their headquarters and primary data center, an organization might also want to interconnect more widely, say, across all its branch offices, factories, warehouses, and/or retail locations.
WANs
When users were primarily in centralized locations, Wide Area Networks (WANs) sprung up to interconnect all of the various locations within an enterprise. WANs were initially set up using telco services for dedicated leased lines (like a T1 or T3, or some fraction thereof), for point-to-point networking between 2 separate locations. These connections could be managed between router and firewall applicances at every location, and a WAN created by combining networks across multiple separate point-to-point connections. Companies adopted different WAN topologies, like hub-and-spoke (centralized control) or mesh (every location interconnected with every other), or some combination of the two, based on their needs and locational layout.
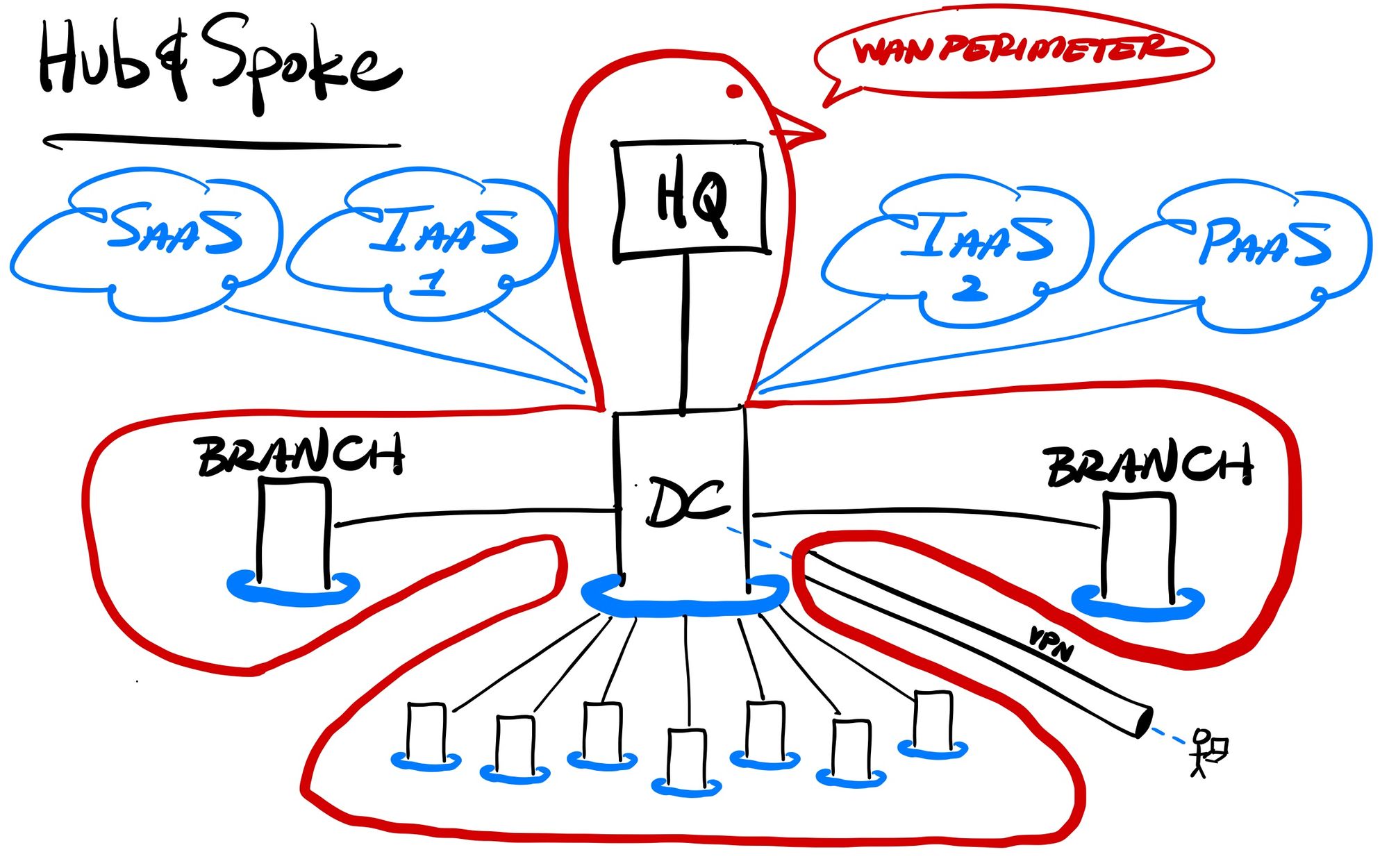
These large private networks typically had the primary data center (or the headquarters) controlling the access in and out. Since users were normally in centralized locations (headquarters, branch offices, and other locations with interconnected networks), the occasional remote worker could be handled through a VPN tunnel into the network. All access to outside SaaS services could be controlled by Secure Web Gateway (SWG) firewall appliances, while traffic to public-facing hosted services could be secured with Web Application Firewall (WAF) and DDoS protection appliances.
But those WANs of olde are now expanding outward continuously. The entire workforce can be working remotely, all or some of the time. The applications being called by enterprise users are greatly expanding to SaaS services that lie outside the protective reach of their WAN. With infrastructure moving onto IaaS platforms, the data center itself is moving outside the perimeter as well. All while locations continue to expand, as companies are going global in their reach, between supply chains, manufacturing facilities, distribution networks, partners, and store fronts.
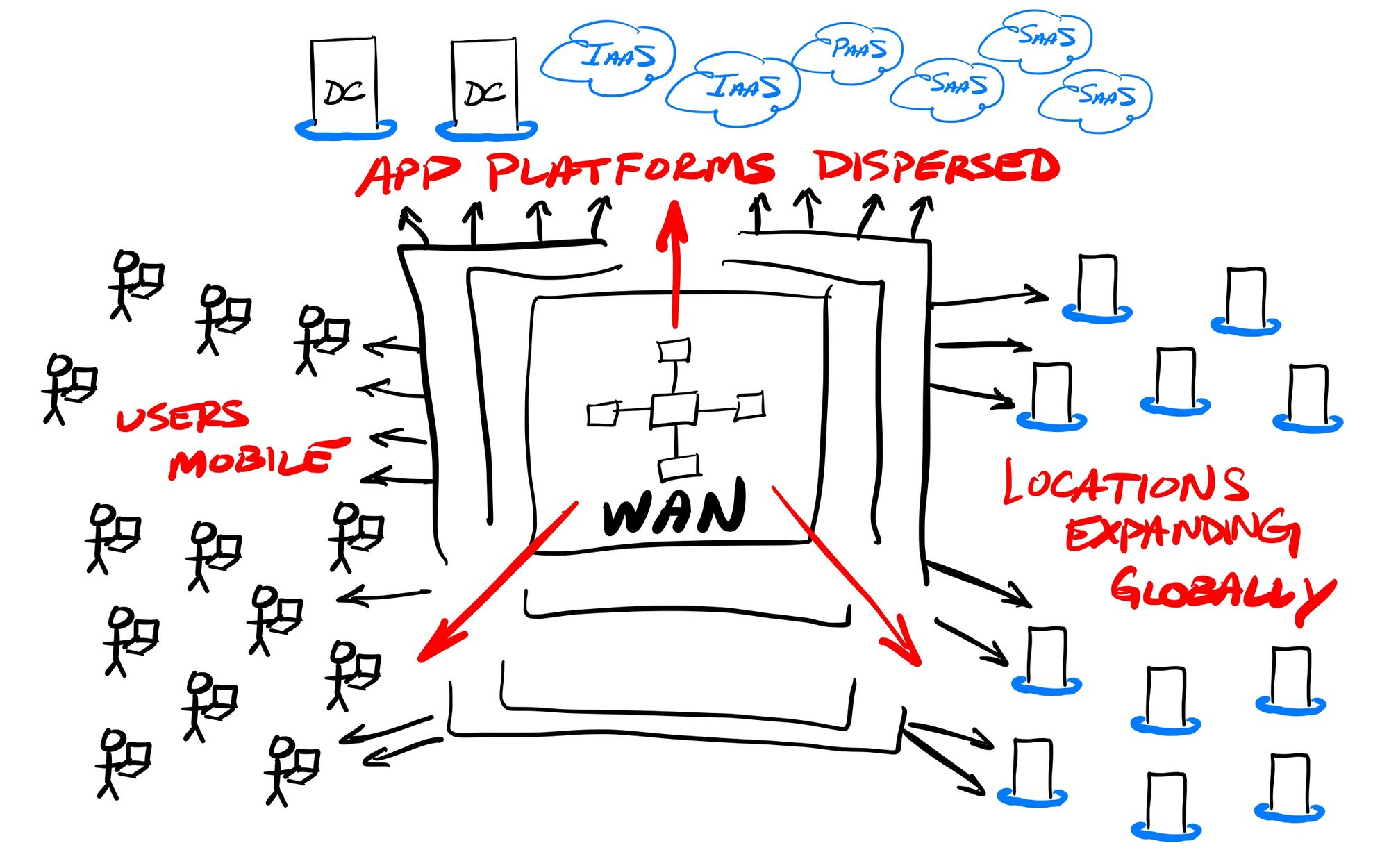
MPLS (Multi-Protocol... ahh who cares) later showed up in the 2000s as a point-to-point alternative to leased lines. It allowed telcos to continue to control the network routing between various locations, but instead of being limited to a (difficult to manage) set of individual leased lines, it could now bundle together separate point-to-point lines between multiple locations as an MPLS network internally provisioned and controlled within the telco. MPLS also greatly reduced the amount of hardware applicances needed in each location, as it didn't require additional routers or switches. This proved quite popular over managing separate point-to-point connections, and MPLS proved to be a great solution for WANs – as long as the telco covered all of the geographical areas your enterprise was in. But regardless of whether leased lines or MPLS were utilized, the telco remained in charge. It typically took a long lead time to get a leased line or MPLS provisioned, and modifications (say, changing the bandwidth) were then difficult. Ultimately, these telco-provided WAN interconnects are extremely expensive and rigid – but once in place, you typically got a very reliable private connection at a set bandwidth.
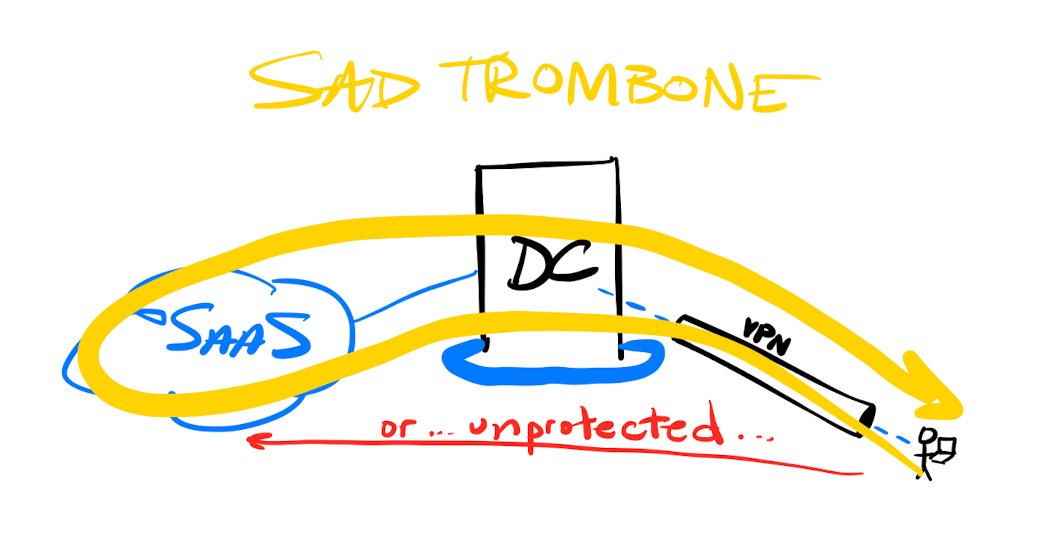
This centralization of networking security through a WAN ultimately had 2 large downsides. One was that cloud and SaaS usage kept greatly expanding, making it more and more difficult (and expensive) to integrate those resources into the WAN's protective perimeter. The other was how all user traffic to those cloud services had to be backhauled through the WAN. Remote users were forced to log into the WAN via a VPN client, and once tunneled in, had their traffic to outside cloud services be routed through the WAN's security stack TWICE (there and back). This lead to poor and unreliable performance, leading to the high latency user experience known as the "trombone effect". As the number of remote users using the VPN expanded, this layout becomes a massive bottleneck; one can imagine then what the pandemic and work-from-home did to most enterprise networks. (Cue sad trombone.)
SD-WANs
The rise of software-defined networking (SDN) has changed networking for the better. Software now drives major networking functions, instead of each location needing a stack of separate network appliances that have to interwork together. SDN has changed so many industries, including, as previously covered, the emergence of Zero Trust and Edge Networks.
The first industry ripe for disruption was those expensive telco interconnects needed for WANs. Software-defined WAN (SD-WAN) solutions emerged in mid-2010s to improve how enterprise locations could be inter-networked together, and better incorporated outside cloud services into the WAN. Instead of being forced to rely on leased lines or MPLS, SD-WAN could overlay specific point-to-point and mesh connections, in order to give the enterprise a huge amount of flexibility in how each interconnect was performed. SD-WAN could provide a centralized control and view over the interconnects, and ultimately, give enterprises a lot of agility that they didn't have with telcos. Companies could now seek out lower cost interconnects when the speed guarantees weren't as essential, or could route traffic to data centers separately from traffic to cloud services – even making dynamic real-time decisions about which lines are used, or utilize multiple lines in parallel. SD-WAN allowed a customer to use existing lines (those already installed leased lines or MPLS), or seek cheaper solutions, like broadband (DSL, cable, wireless, satellite) or cellular (3G/4G/LTE/5G). SD-WAN ultimately allows for more flexibility by having better control over the various interconnects available.
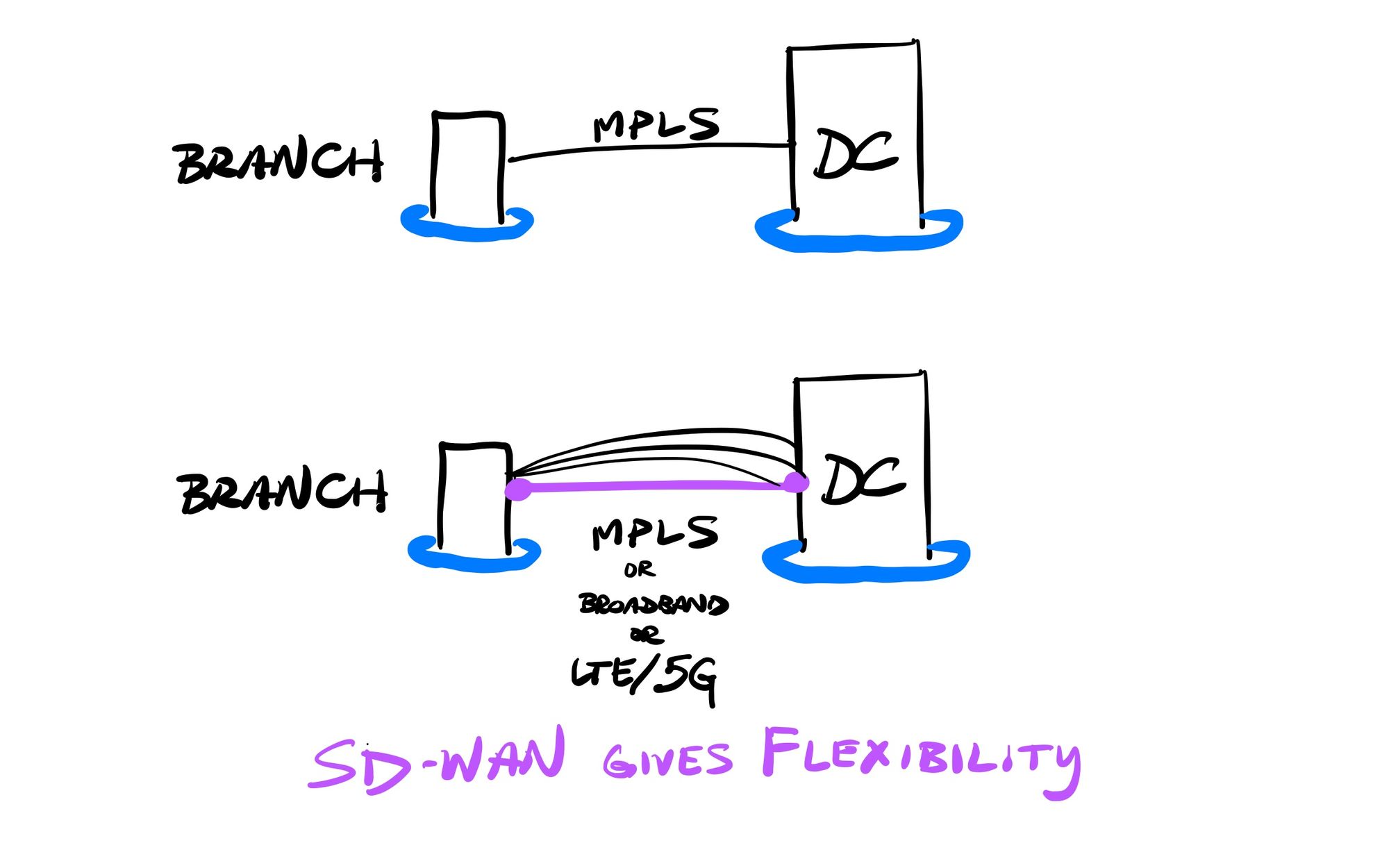
MPLS is not dead – in 2020, telcos provided an estimated $52B in services, expected to grow at a 6% CAGR for several years from here. Companies were able to continue using telco lines that were already installed (for the guaranteed speed & reliability), but with SD-WAN better controlling the flows, could then either enhance or replace those telco interconnects (for cost control and flexibility) as networks and equipment got overhauled. Gartner ultimately concluded that SD-WAN deployment could save up to 65% over traditional telco interconnects, all due to faster provisioning and more control and flexibility.
SD-WAN is an industry full of big network vendors acquiring a lot of the smaller players in order to enter the market rapidly. The Gartner Magic Quadrant for WAN Edge (aka SD-WAN) from Sep-20 shows us the industry leaders:
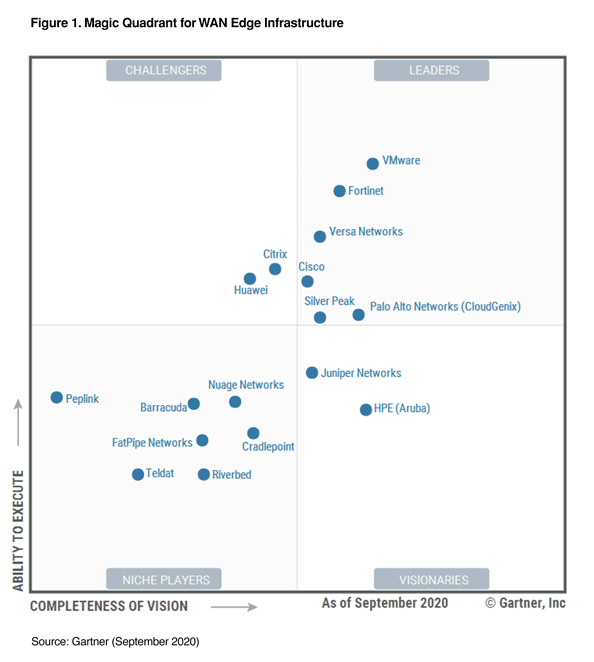
- VMware is the Gartner MQ leader, after acquiring VeloCloud in Dec-17, and bolstered it later in Jan-20 acquiring Nyansa for network analytics.
- Fortinet has its FortiGate product line, including both appliance and virtual solutions
- Cisco acquired Viptela in Aug-17
- Palo Alto acquired CloudGenix in Mar-20
- HPE/Aruba acquired Silver Peak in Sep-20, to move itself to the leader quadrant
SD-WAN is expected to continue to grow from here. In that most recent Magic Quadrant, Gartner predicts that:
"By 2024, to enhance agility and support for cloud applications, 60% of enterprises will have implemented SD-WAN, compared with about 30% in 2020."
Enterprises are moving from their on-premise data centers to cloud-based virtual infrastructure. Beyond hosting Internet-facing (public) services, an enterprise can host internal-facing (private) services in what is known as a Virtual Private Cloud (VPC). One issue with SD-WAN is that different vendors provide different types of interconnects to cloud services. Some SD-WAN solutions are still based on appliances, some force you to host their VM in your private cloud, and others might provide a SaaS service that runs on the cloud vendor's IaaS. Some do provide direct connects to cloud regions, like Cato Networks did with its edge network to interconnect WANs to cloud platforms from the nearest POP. SD-WANs can also allow enterprises to buy a direct private connection from their WAN to their private VPC as well, using pricy add-on services from cloud vendors, like AWS DirectConnect, Azure ExpressRoute, or GCP Direct Interconnect. Some vendors are transitioning SD-WAN into what is called Software-Defined Cloud Interconnect (SDCI), providing a specific service to interconnect more directly from on-prem networks to cloud-based services. Other cloud-based providers are emerging that are starting to provide WAN-as-a-Service (WANaaS), as a fully managed service. As you can tell, SD-WANs are a bit all over in features that each provides.
[Slight tangent: If you want to have a private network between VPCs – no on-prem WAN involved – you'd use a different service (like AWS PrivateLink, Azure Private Link, and GCP Private Service Connect) for VPC-to-VPC interconnections. This is what you'd use, for instance, if you wanted a private network connection between your private cloud infrastructure and Snowflake.]
A New Path
But what if there is a better way than running your network backbone yourself via expensive telco interconnects? A new solution has emerged that enhances SD-WAN further (or potentially bypasses it altogether), while flipping the underlying philosophy of WAN networking. Secure Access Service Edge (SASE) Networks provide security and networking in a single solution that no longer tries keeping a perimeter – the platform IS the perimeter. It focuses on all interconnection and access happening through a single control plane, regardless of the location of the user or service.
- Secure Access = Using Zero Trust for controlling user access to apps and servers...
- Service Edge = ... on top of a cloud- or edge-backed network that overlays across all your users, networks, and services.
SASE (pronounced "sassy") was first coined by Gartner in Aug-19. They've been all over the coming wave in Zero Trust and SASE over the past few years, covering the progress of both in every subsequent Hype Cycle for Enterprise Networking report each year, and in Mar-21 released a new "2021 Strategic Roadmap for SASE Convergence" to help enterprises begin to adopt it. And though Forrester is trying to brand it something different (Zero Trust Edge, or ZTE), their report in Jan-21, "Introducing The Zero Trust Edge Model For Security And Network Services", showed how their vision is exactly the same. So we now have two major industry minders telling everyone the same message – security concerns have to come before networking concerns, and SASE is the path forward.
Many – the SD-WAN vendors in particular – are selling SASE as the next evolution of SD-WAN. Gartner even predicts that SD-WAN is merely a stepping stone, from that Magic Quadrant for WAN Edge report above:
"By 2024, more than 60% of software-defined, wide-area network (SD-WAN) customers will have implemented a secure access service edge (SASE) architecture, compared with about 35% in 2020."
However, SASE seems like so much more than SD-WAN. The current networking architectures continue to have the on-premise networks as the focal point. This is now shifting to the expanding nature of users, cloud usage, app platforms, and locations, so that their users can have a secure, performant, and reliable connection to any service within that enterprise, regardless of either's location. This level of control is going way beyond the WAN, and into a software-defined perimeter that can encompass users, locations and app platforms that are typically difficult for WANs to control. SASE has a focus on centralizing enterprise networking down to a single control plane handled by one overarching vendor (with, of course, ties to other partners having popular platforms for identity and device mgmt). Zero Trust and SASE go hand-in-hand, with SASE Networks used to interconnect the enterprise networks, and Zero Trust for controlling user access to apps and services across that network. The various components of SASE are ( extending out from the Zero Trust ecosystem I detailed before):
- Manage and protect the fleet of devices via EPP agent, using an EDR/XDR service (like CrowdStrike or Sentinel One)
- Manage and protect the fleet of users via IDaaS service (like Okta)
- Manage and protect the fleet of apps via Zero Trust & SWG platform (like Zscaler and Cloudflare)
- Manage and protect the fleet of networks across different locations via SD-WAN (like VMware and Cisco) or via direct interconnects (like Cloudflare is allowing with CNI)
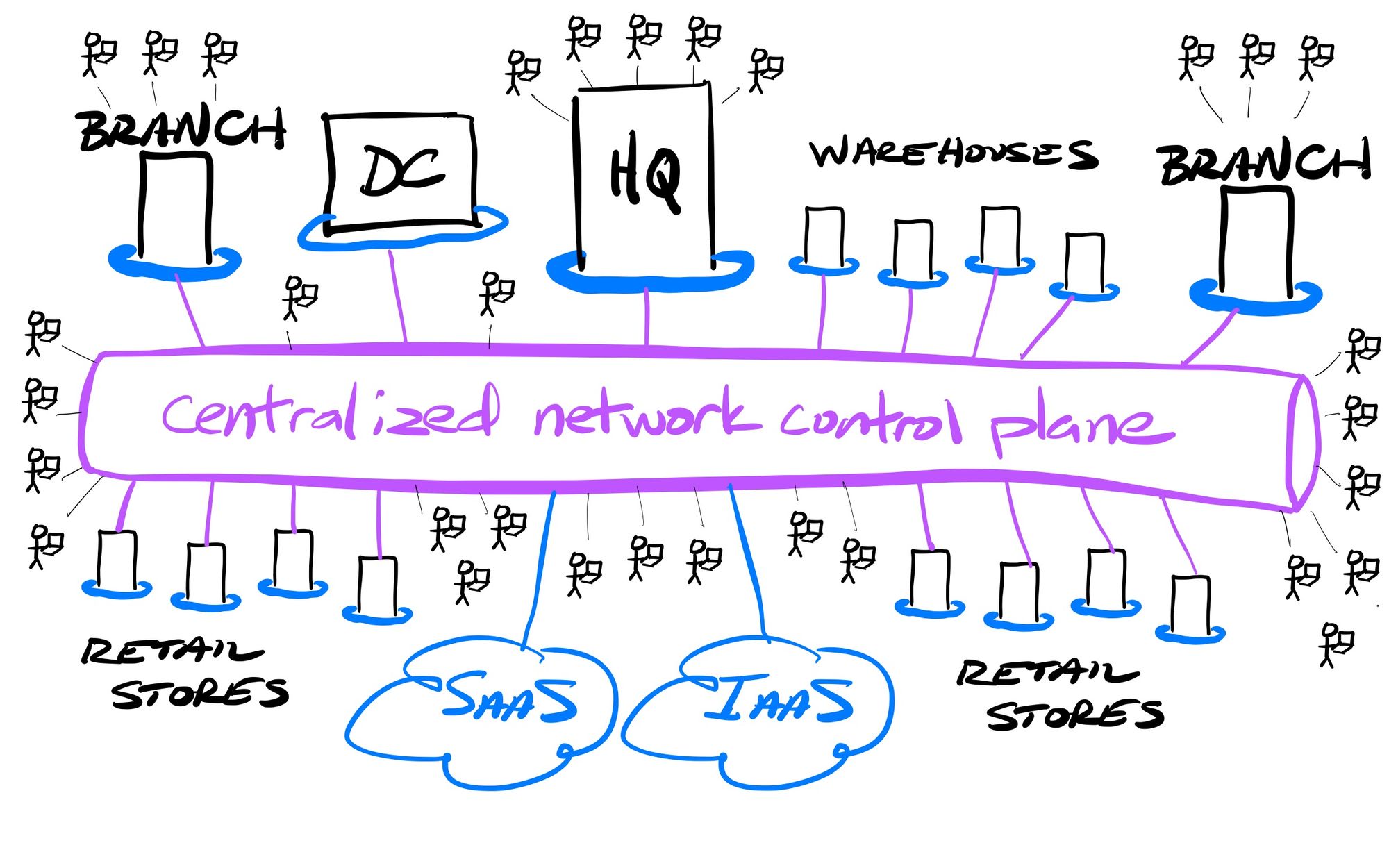
SASE Networks provide an interconnective fabric over all the above. SASE can be the connective control plane over the entire enterprise network, providing a secure, reliable, and performant Zero Trust (ephemeral) connection between all the disparate networks, users, devices, servers, and apps, regardless of the location of each. Enterprises no longer need to manage their own WAN, and its required networking and security hardware at every location.
Edge Has the Advantage
SASE is finally here, but many of today's solutions have been cobbled together. Gartner's reports on SASE continue to focus upon how globally-positioned edge networks provide the best posture for SASE services. The edge network can now become the single network control plane, and every connection to that edge (to and from networks, servers, apps, or users) becomes a low-latency spoke into it.
Remember the advantages that edge networks have? They provide a globe-spanning software-defined network that have distributed entry/exit points (POPs) into that network. This distributed nature provides low-latency to the various user, network, and cloud interconnections, but also allows the traffic to travel through fast backhaul pipes, in order to have traffic quickly span the globe without traveling through the public Internet.
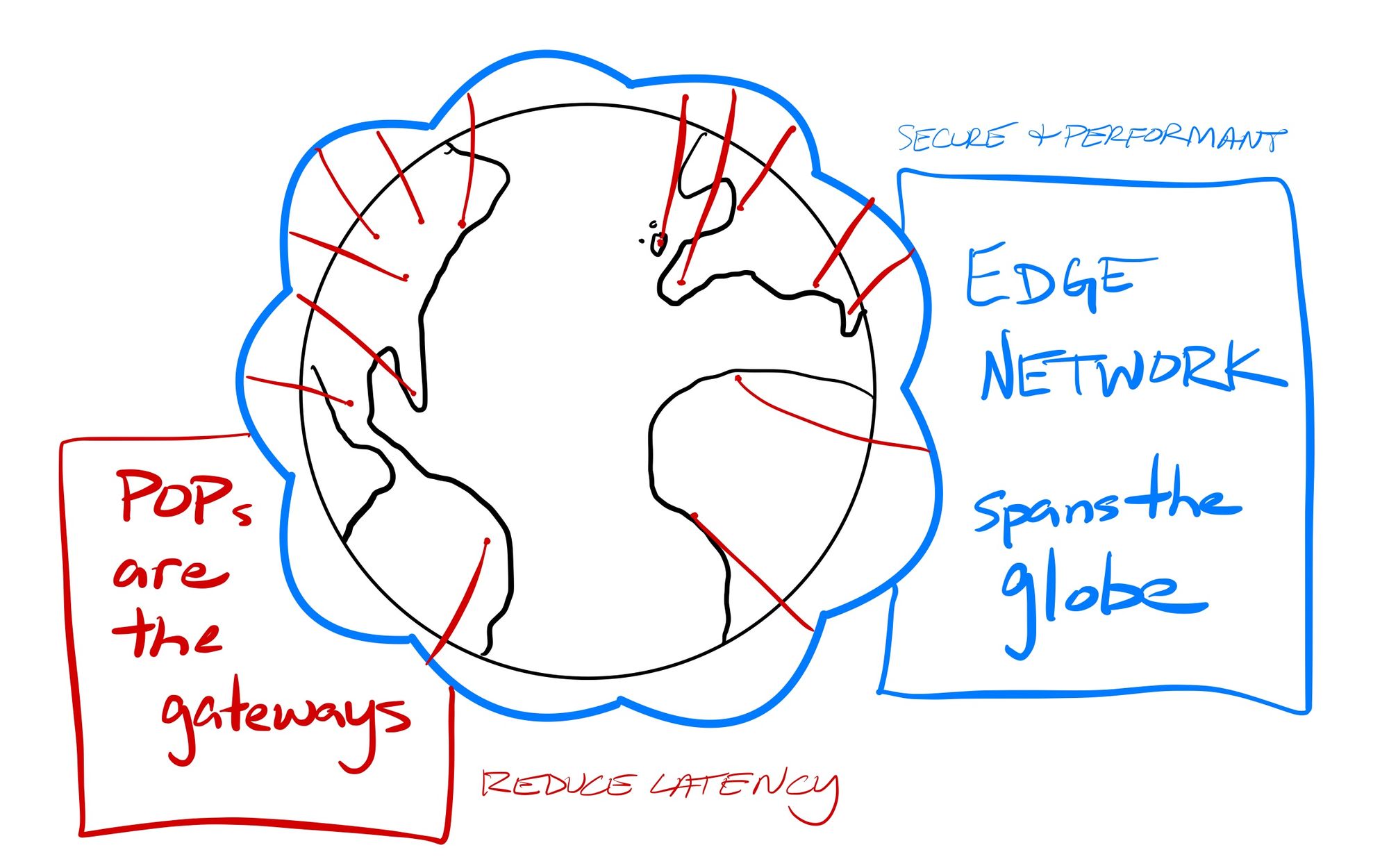
Edge networks have a decided advantage in providing SASE services. Globally distributed POPs can reduce the latency from network to platform, while massive backbones manage and secure the traffic across the globe. With SASE, I am most focused on the edge-network based solutions like Zscaler and Cloudflare, along with private companies like Cato Networks, Netskope, and Perimeter 81. There are also cloud-based SD-WAN companies pivoting into SASE, like Versa, Aryaka (who acquired Secucloud SASE, May-21), and Forcepoint (cloud security company spun out of Raytheon). And, as always, the networking companies are adapting quickly through a lot of acquisitions:
- Barracuda Networks has Cloud Gen WAN and now Cloud Gen Access for Zero Trust (acquired Fyde, Nov-20)
- VMware has pivoted into SD-WAN (acquired VeloCloud SD-WAN in Dec-17), and later bolstered its network analytics capabilities (acquired Nyansa in Jan-20)
- Palo Alto has pivoting into SASE via SD-WAN (acquired CloudGenix, Mar-20) combined with its Prisma Access platform for Zero Trust
- Fortinet now has FortiSASE (acquired Opaq SASE, Jul-20), and expanded network visibility and monitoring (acquired Panopta in Dec-20)
- Cisco announced a new SASE platform in Mar-21 (having acquired Viptela SD-WAN in Aug-17, Duo Identity in Oct-18, and Thousand Eyes DEM in 2020)
- Checkpoint has Harmony Connect (acquired Odo Security, Nov-20)
- F5 now has a full WANaaS and distributed application platform (acquired Volterra in Jan-21)
- HPE Aruba has gotten into SD-WAN (greatly helped by acquiring competitor Silver Peak in Sep-20)
Conclusion
SASE is here, but security-focused edge networks have the clear advantage over legacy network providers still trying to catch up to expanding cloud usage and remote users. Edge networks provide a private networking mesh (or "fabric" in networking parlance) encircling the globe, making the location of users, services and apps no longer matter to today's global enterprises.
SASE allows for creating a private network for a company, enveloping all of its needs across its workforce and the servers/applications/data/workflows they access. Beyond just the cost savings in reducing the need for networking appliances and MPLS, and greatly reducing the size of IT team needed to manage it all, a switch to a SASE networking architecture can have huge ramifications for companies. As I've pointed out before, there now exists the ability to not only have the network of an entire enterprise handled through SASE, but, since the interconnects are all controlled dynamically through SDN, also for creating pockets of shared networks between partners. Remember how Snowflake's Data Cloud can enable shared pools of data between companies, or between a company and its pool of partners or customers? SASE networks allow this same shareability – enterprises can not only secure their own network, but be able create specialized pockets of networking between themselves and partners or customers. SASE can now envelope all the users and workflows occurring between partnering companies. The network effect with SASE Networks is enormous (yes, pun intended).
With SASE, every enterprise can now weave a single control plane layer over all of its utilized services to interconnect and control it all through ephemeral Zero Trust connections. Workforce, partner, and customer access to internal applications & data can be tightly controlled and monitored. The devices they use, and the servers and services they access, can all be protected, plus allows for protecting the unprotectable IoT devices that you cannot install an agent on to – think of all the POS systems (cash registers), printers, cameras, and remote sensors, or, with manufacturing, all the computer vision, factory robotics, and other OT (operational technology) devices. SASE is about creating a software-defined perimeter over the entirity of your business, using Zero Trust to control all access. Think of it as every enterprise having their own private and secure global Internet, which can be securely shared with external parties as needed.
WANs were initially the sole purview of telcos, who had all the power. SD-WAN brought networking companies into the mix, democratizing WAN interconnects. SASE Networks now centralize it all in a globe-spanning edge-based security cloud. I think the greenfield in this space is likely owned by the edge-based security companies going into SASE, not the networking appliance companies that moved heavily into SD-WAN and are trying to catch up now with SASE. Today's companies don't need to start with MPLS and WAN technologies, or even SD-WAN – they can hand all the networking over to a service to be their enterprise backbone, and simply need to interconnect their networks, users, and apps into that platform. SASE marks the rise of enterprise network-as-a-service from edge networks.
When Gartner first defined SASE in its "The Future of Networking Security is in the Cloud" report from Aug-19, it had a few predictions.
By 2023, 20% of enterprises will have adopted SWG, CASB, ZTNA and branch FWaaS capabilities from the same vendor up from less than 5% in 2019.
By 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018.
Gartner then had a recent report in Mar-21 on how enterprises should approach adopting SASE, where they recommended a phased approach to achieve the goals of SASE over the long-term. It included an additional growth projection:
By 2025, at least 60% of enterprises will have explicit strategies and timelines for SASE adoption encompassing user, branch and edge access, up from 10% in 2020.
So over the next 4 years, Zero Trust and SASE is due for some extremely rapid growth. This massive shift in enterprise networking won't happen overnight, however. Gartner recommends adopting Zero Trust immediately to remove the dependency on VPN tunneling, then using every network migration and upgrade from here to inch more and more towards SASE in the long term. At the same time, in Gartner's most recent Networking Hype Cycle report, they warned that SASE is at the height of the hype cycle (not surprising, given all the acquisitions of late) – yet provided an additional prediction that showed the next 4 years will be strong for the pure plays that can provide SASE and Zero Trust in a single solution.
By 2025, 35% of companies that use multiple public cloud providers will use a single network software stack, an increase of over 10 times from 2021.
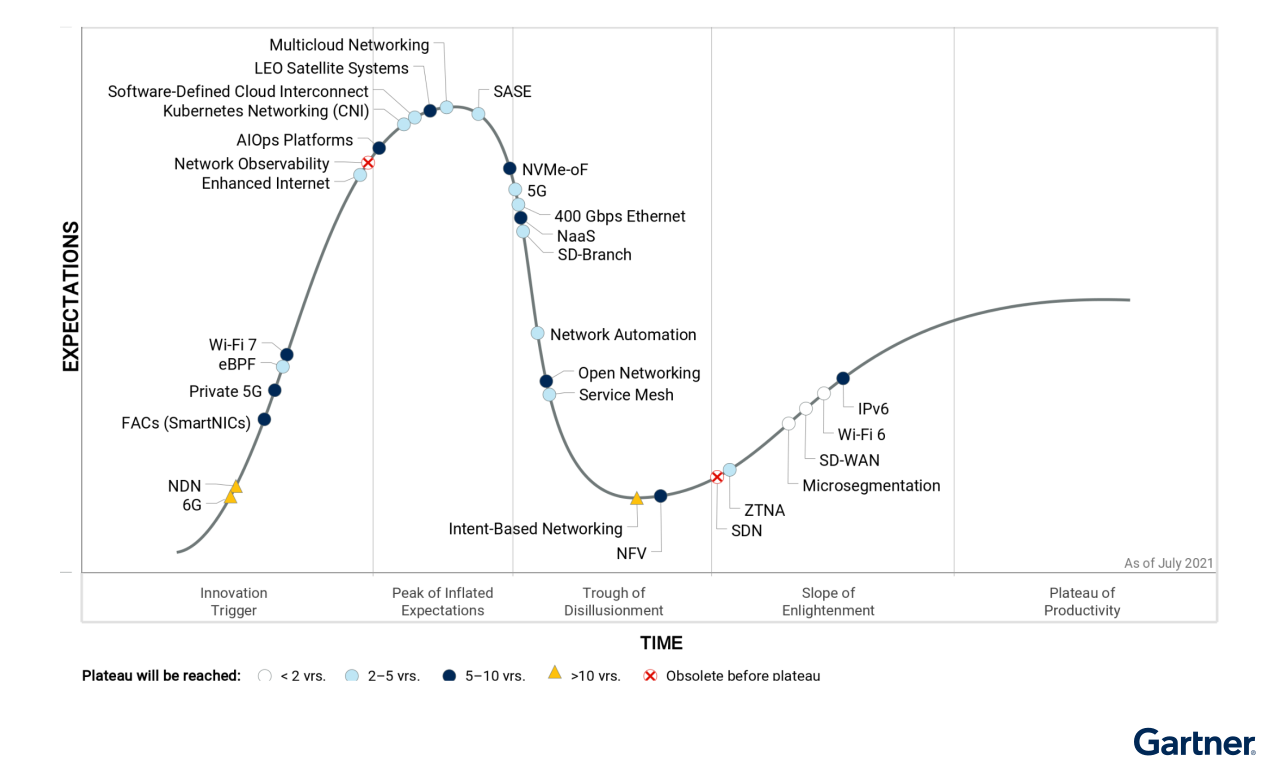
I expect more growth than this hype chart alludes too, as companies start to see the benefits of using edge-network based platforms, and how interest into Zero Trust will lead into the fuller benefits of SASE Networks. Enterprises are hopefully not going to be relying upon cobbled-together solutions from the legacy networking companies, when edge-based solutions can more easily handle the global layout of users, networks, and apps. Job listings are clearly proving the trends are there, as the percentage of Zero Trust and SASE job listings have quadrupled over the past year.
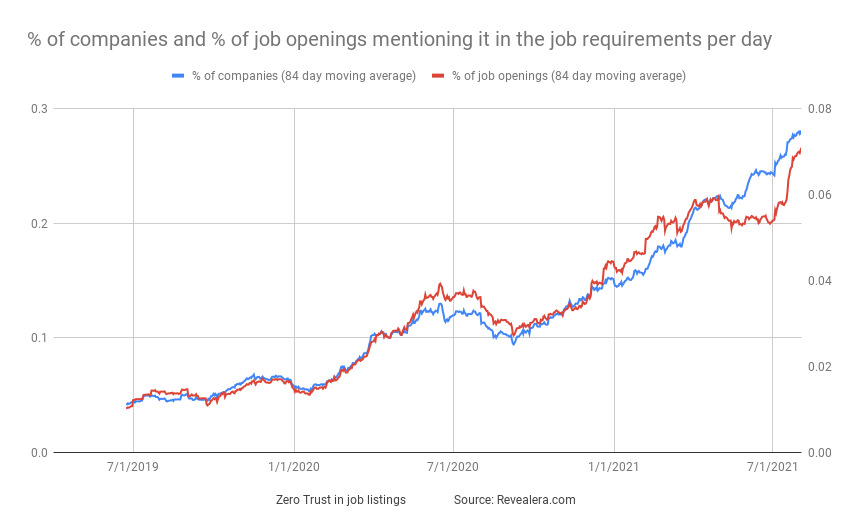
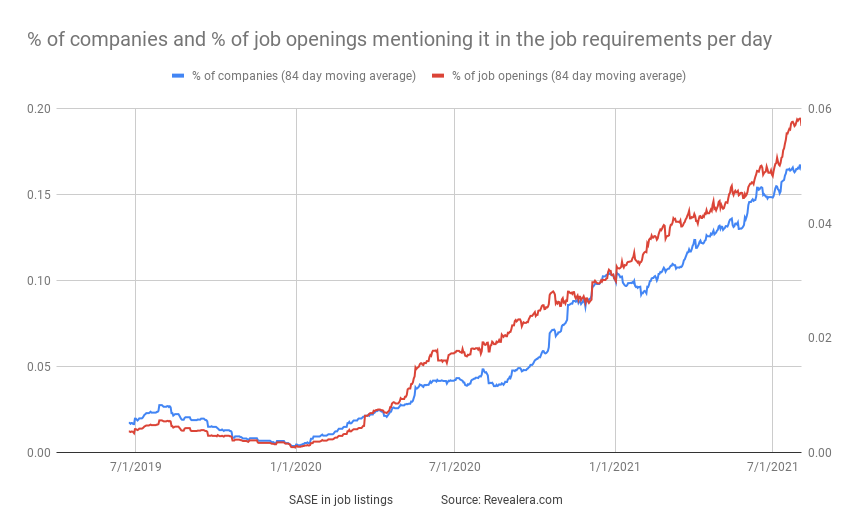
Add'l Reading
If you haven't read it yet, I recommend my piece a year ago on "What are Edge Networks?".
To read the industry reports on SASE:
- Gartner first defined SASE in its "The Future of Networking Security is in the Cloud" report from Aug-19
- Forrester agreed with them in its "Introducing The Zero Trust Edge Model for Security And Network Services" report in Jan-21
- Gartner recently laid out a roadmap for enterprises to adopt SASE in its "2021 Strategic Roadmap for SASE Convergence" report in Mar-21, reinforcing that edge networks (with globally distributed POPs) are the better option, over cobbled together solutions from legacy networking vendors
- Gartner then followed up more in its latest Hype Cycle for Enterprise Networking, 2021 report in Jul-21, stating that SASE is at the Peak of Inflated Expections, as every vendor now has a SASE product
Thanks to Revealera for the jobs stat charts.
Want to learn more about these types of tech investments? I cover SASE Networks, Edge Networks, Zero Trust, Data & Analytics, Observability, Dev Tools, and Enterprise SaaS in my premium service. Sign up!
- muji
