Today's enterprise networks are fractured, moving farther and farther away from a centralized location. Zero Trust is the next-gen security paradigm that is capable of helping to secure today's scattered networks, but it's becoming so heavily used a term that the definition is getting blurred.
Let's look at what Zero Trust is solving, how the ecosystem has evolved, and look at the moves major players like CrowdStrike, Okta, Cloudflare and Zscaler are making within it.
Network Sprawl
Traditionally, the primary usage of an enterprise network is interconnecting infrastructure which runs services hosted internally, handling traffic from enterprise users who use some type of device to access the network. Remote workers had to use connection tools, like a VPN, in order to get onto the trusted company network to access internal services.
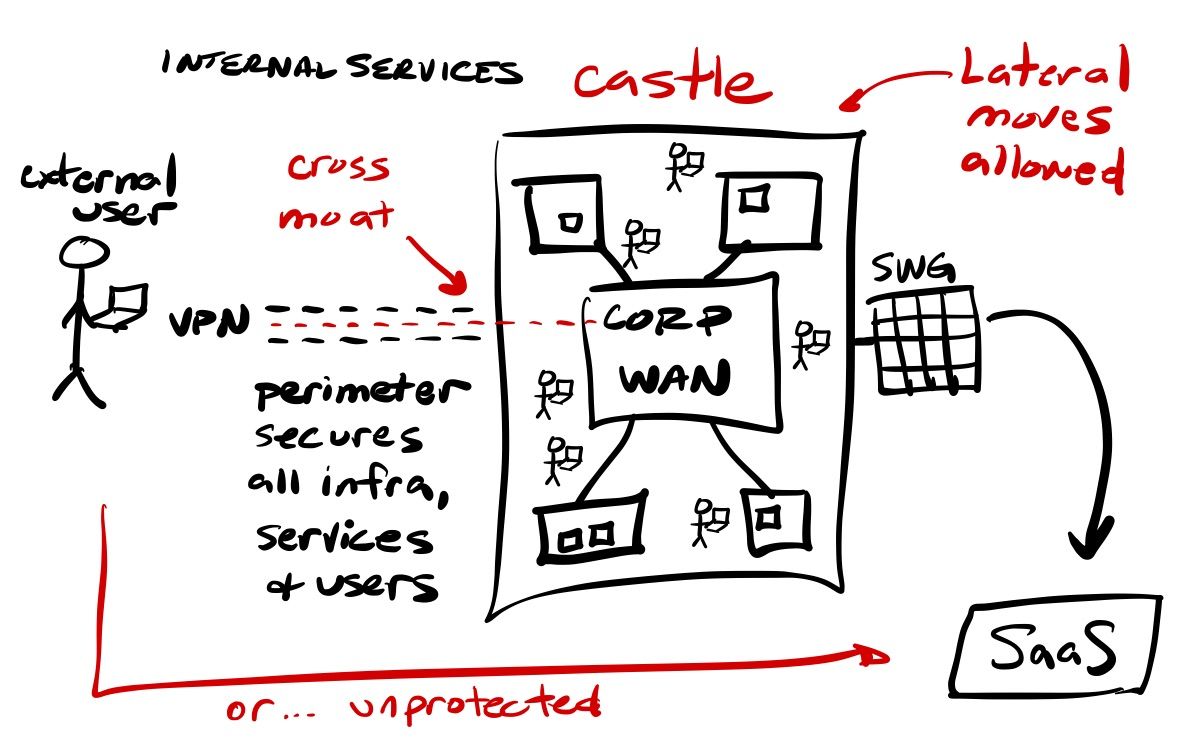
The old method of castle & moat security, where you maintained a trusted network across all of your enterprise infrastructure, apps, devices and users – with a secure perimeter around it all – is becoming a thing of the past, as all of those areas continue to sprawl outside of the perimeter (and IT's grasp).
- Infrastructure, like servers and databases, can be hosted in any number of locations - either on-premise, in remote data centers, on cloud infrastructure, or as a SaaS managed instances. Hybrid environments are spreading infrastructure between on-premise and cloud, as companies attempt to transition systems onto the cloud at their preferred pace. Different departments of a dispersed company may have spread their infrastructure across cloud regions, or even cloud vendors. New acquisitions might be bringing with them an entirely different set of cloud vendors. Multi-cloud strategies are spreading infrastructure between cloud vendors, and companies may find it better to mix and match between them for specific purposes.
- Before the cloud, a company installed all software apps they utilized onto servers within their trusted network. This is now a thing of the past, as companies today likely use a wide variety of cloud-native SaaS services that handle the critical day-to-day operations of their business, such as tools for HR, finance, payroll, sales tracking, customer engagement, marketing campaigns, and team intercommunications. SaaS management app Blissfully estimated in their 2020 SaaS Trends report that, on average, mid-sized companies use 137 SaaS applications, while large enterprises use 288! Complicating matters for IT, it is impossible to draw a protective moat around infrastructure you do not own and manage, and which require traversing the public internet to access.
- The enterprise workforce used to all be in the same physical location, or on a WAN that interconnected different business locations securely, using devices that were managed by the enterprise. Even when apps shifted to the cloud, if the workers accessing those tools were all on same network, you could have some semblance of control over security of those SaaS applications since it could go through a centralized Secure Web Gateway (SWG), located at the network perimeter, to provide real-time protection (such as threat & malware detection) over outgoing web requests. But today's workforce can now be across multiple locations, potentially spanning the globe. The devices they use may or may not be controlled by the enterprise. The global pandemic in 2020 only accelerated this, as instead of centralized enterprise locations, you now have an even more widely scattered workforce.
The users (workforce, partners, consultants), the devices used (mobile, laptops and workstations), and the servers & services being accessed (SaaS apps, internal apps, cloud infrastructure, on-premise servers), now span the globe. Further amplify all that networking complexity by adding in devices to your enterprise network like IoT devices (smart buildings, smart vehicles, POS systems, and cameras), or OT devices (operational machinery, smart factory control systems, and robotics). Whew!
One of the biggest risks of the castle & moat security philosophy was the fact that, once you were allowed access to the trusted network, it allowed a user lateral movement (a phrase you will see often in the news after major breaches) in order to access anything on the network within the enterprise. Once a bad actor has access to the trusted network, they can move laterally across that network into other systems, and exploit ways to get deeper and deeper into your network and critical systems using methods like privilege escalation (granting more access rights to the user than should be available) to finagle their way deeper and deeper.
What is Zero Trust?
Zero Trust was a concept that first appeared in 2010 (coined by industry minder Forrester), but didn't come into prominence until Google published their take on it in 2014 with an initiative called BeyondCorp (as in, beyond the corporate network). The basic premise stated that neither external networks (the internet and SaaS services) nor the internal network (enterprise network & WAN) should ever be trusted!
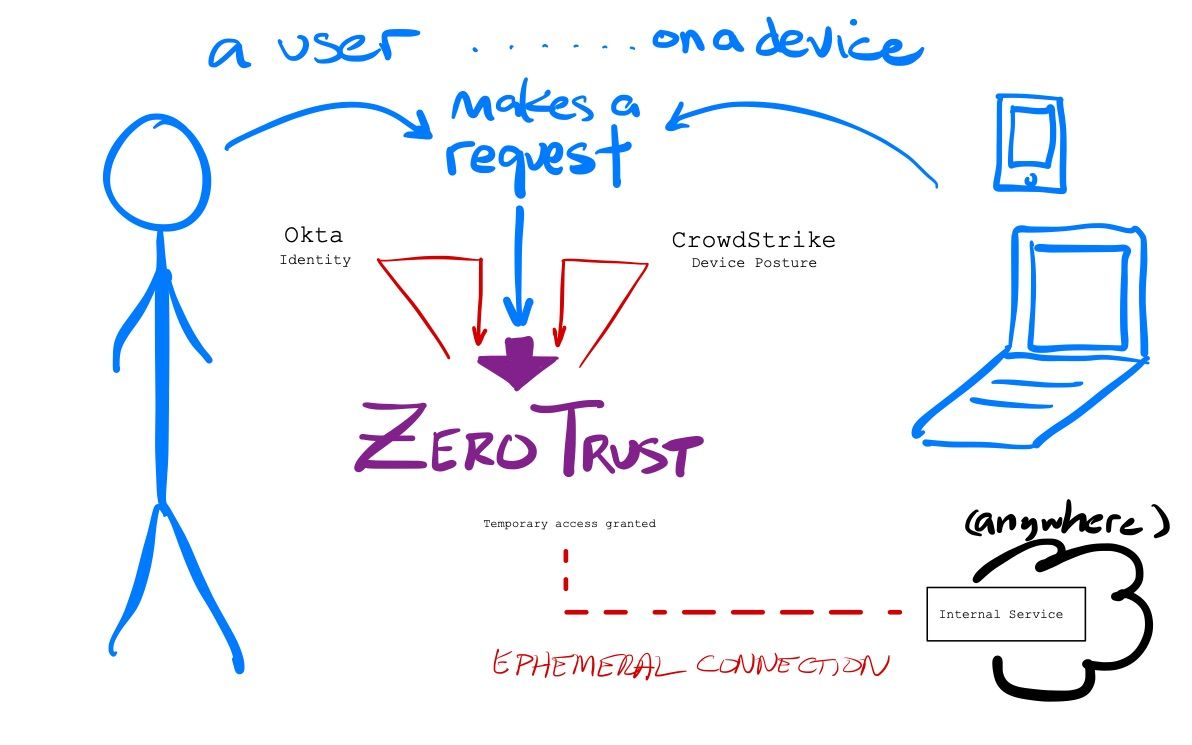
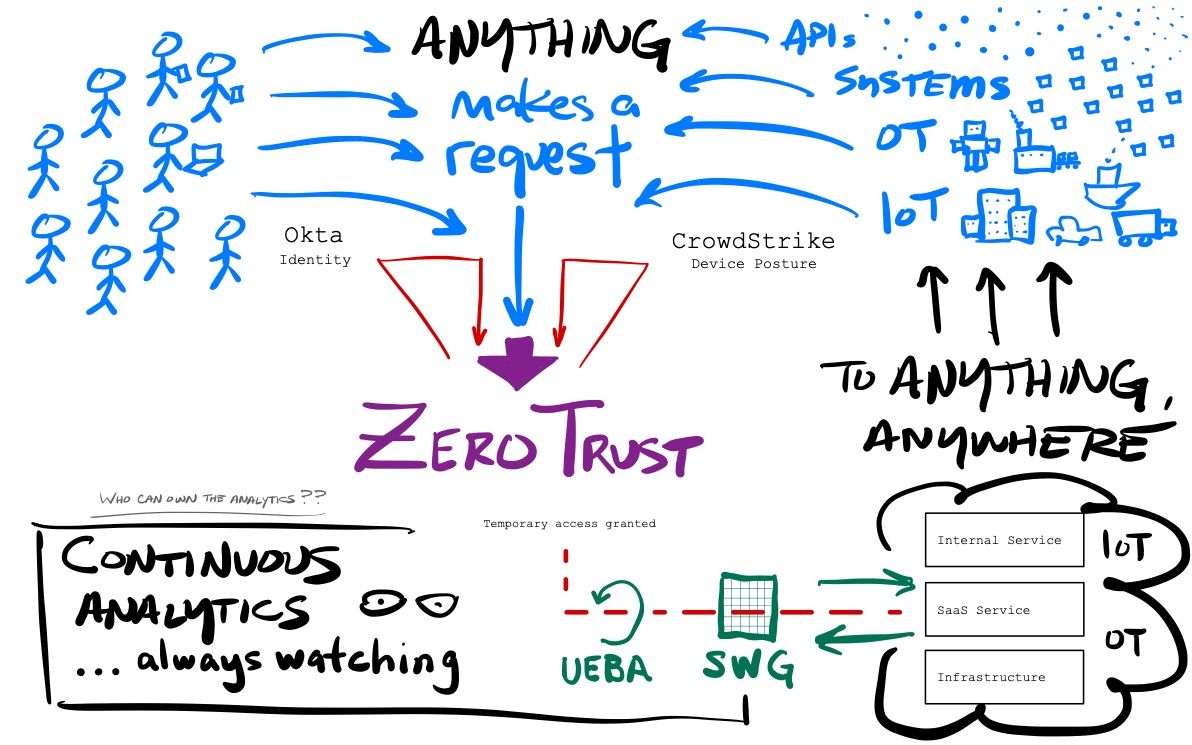
Zero Trust allowed for a software-defined perimeter instead of a network driven one, where you never trust a user requesting access to a particular service. You lose the entire concept of the trusted network – the entire basis of the castle & moat strategy. Users must establish who they are (authentication), and then the system determines the rights of that user to access the given service (authorization). Once BOTH identity and access rights have been established, the Zero Trust service acts as a proxy to the service, creating an ephemeral network connection to the requested service. The user doesn't need to know where app is hosted – the networking is all handled invisibility to them. Once the user is done, the temporary connection from that user to that service can be severed.
Zero Trust flips the entire process of requesting & securing user access to be application-focused, not network-focused. Every service is individually secured, instead of being in pool of services within a trusted network. Zero Trust inherently prevents lateral movement, as users cannot access anything else in that connection except the service they originally requested. It also prevents privilege escalation, as the user only has the access rights determined by the identity system when the connection is established.
This is a fundamentally different mindset than traditional network security architecture. Unfortunately, it is also a lot more complex to set up and manage by IT, due to the intricacies of how to manage services, users, and access rights so granularly, how to manage the ephemeral network connection, and then how to monitor and audit over all of that. Luckily, the rise of cloud-native cybersecurity services were able to provide turnkey solutions that could do it all for you.
Identity-based Access
Zero Trust solved how to better secure internal resources, and could completely eliminate the need for VPNs and network perimeters around your services. But what about the other type of traffic that a scattered workforce is making – to external SaaS services, that Secure Web Gateways (SWGs) are used to secure?
Infrastructure and services were already moving to the cloud. And as users and devices are no longer being situated within the enterprise's trusted network, a new paradigm of user access came about. Cloud-native SaaS services began to appear that could secure BOTH types of traffic from your workforce – securing incoming requests to internal services (Zero Trust), as well as protecting outgoing requests to external SaaS services (Secure Web Gateway). This combination really solidified the concept of perimeter-less networking to a lot of enterprises. Zscaler was a pioneer in this area, proving that the concept of a cloud-native SWG & Zero Trust platform would be an attractive option to large enterprises needing to secure user traffic.
The key to this combination was tying the access system into an identity provider that could better handle the identity and access tracking (authentication and authorization) part of the equation. Luckily, enterprises already had an ideal solution in place for managing identity - the Identity and Access Mgmt (IAM) services from cloud-native providers like Okta, Duo, and PingID were already in use, managing their workforce security and providing features like SSO and Multi-Factor Authentication (MFA). Customers could now get a synergistic solution between their User Access provider and their existing Identity provider, to have them work together to better protect users. The Identity provider could validate the user and manage what access rights they had for each service, then hand over the user to the User Access provider to manage and secure requests from that user to external SaaS services (via SWG) and to internal services (via Zero Trust).
Major Zero Trust providers include Zscaler, Palo Alto, Cisco, Akamai, Cloudflare, Netskope, and Illumino (the last 2 privately held). These platforms must hook into a wide variety of authentication stores in order to have wide applicability to whichever IAM tool that its customers prefer most. Okta seemed to become the preferred partner from the start, and has been the clear leader on Gartner's Magic Quadrant for IAM for years (until dropping a few notches in the past one against Microsoft and PingID). I expect Okta to remain a vital partner for Zero Trust networks. On the flip side, Okta acquired ScaleFT for its Zero Trust capabilities, which eventually spawned 2 products: Access Gateway (IAP) and Advanced Server Access (Zero Trust for infrastructure). Okta Access Gateway, in particular, happened to directly compete with all of its Zero Trust partners - but has not seemed to be a major player in that market at all, nor seems to be focused on much by Okta. [Anecdotally, in watching Oktane'21 recently, there was no mention of Access Gateway in any of the lists they showed on which product lines each customer being interviewed utilized, while its sibling product, Advanced Server Access, was heavily mentioned. Likely because of their newly announced PAM product. More on that below.]
Context-based Access
While Zero Trust began with a major dependency on identity, it quickly expanded from there to include other aspects that could provide more context about the request beyond only the identity of the user, such as the device they use, the location they are in, or the network they used.
A remote workforce tends to use enterprise-owned devices (mobile and laptops) for performing their work. So just how enterprises are relying on IAM services to manage the security of their pool of users, they are relying upon EPP/EDR platforms like CrowdStrike and Tanium to manage security over their pool of devices. These SaaS security platforms provide Endpoint Protection Platforms (EPP) to protect all enterprise-owned devices, and Endpoint Detection and Response (EDR) systems to manage the security over their entire fleet of devices. These systems allow the enterprise to directly assure that a utilized device is a known & managed device in the enterprise's network of endpoints (via EDR), and that this device is currently showing as safe & malware free (via EPP).
This total view over a device's status in the pool of an enterprise's device network is what is known as Device Posture. Like Identity, it has become a vital component of the Zero Trust ecosystem. Zero Trust platforms could now rely on both IAM and EPP/EDR partners to provide better vision into the user and the device utilized, and partnerships started quickly forming.
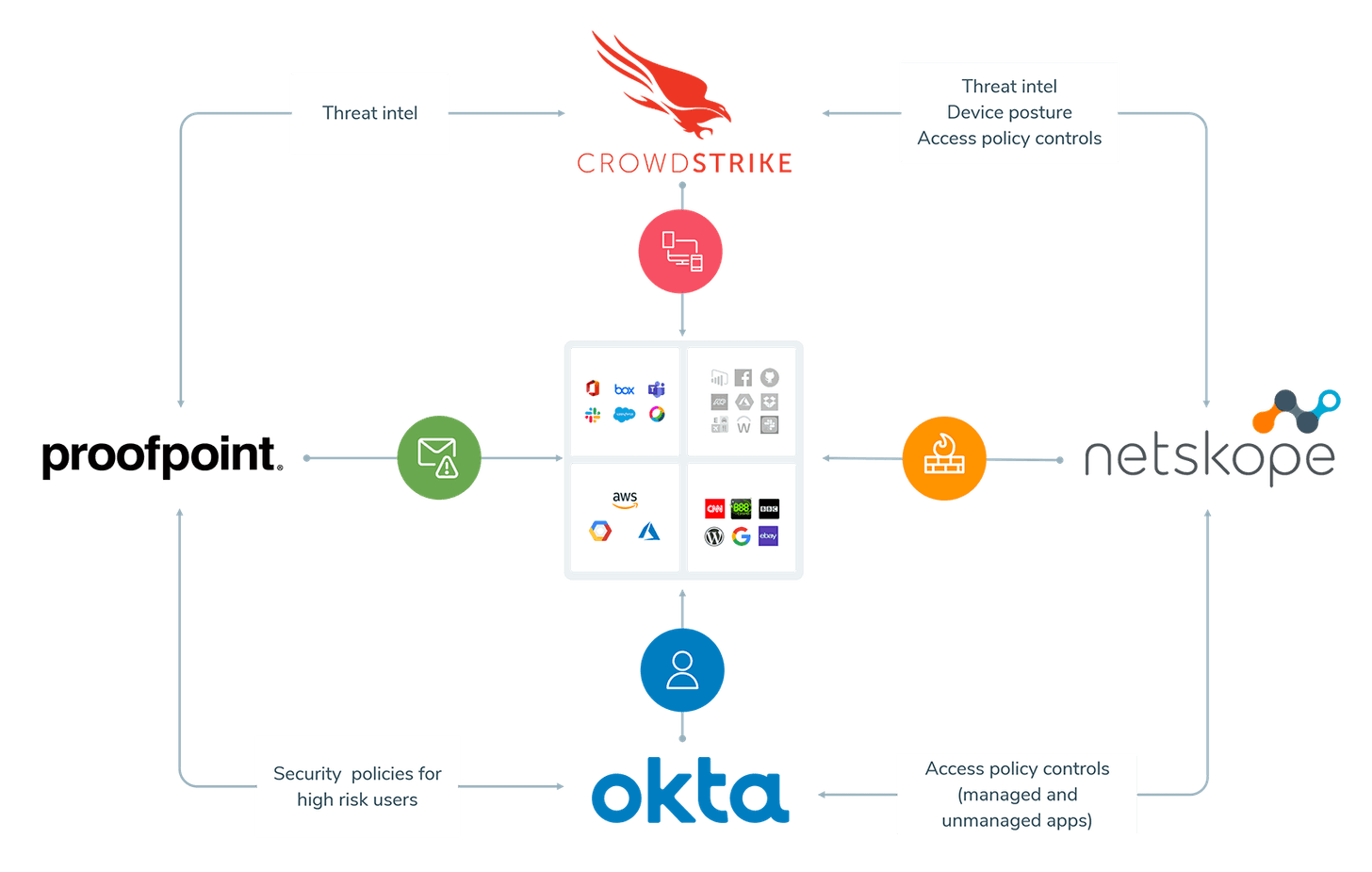
CrowdStrike navigated partnerships with Zero Trust platforms extremely well, much to its benefit (having had incredible hypergrowth over the past year). In 2019, they first partnered with Netskope, then with Zscaler, to more closely integrate their systems together. As new Zero Trust based security platforms emerge, they too must partner with CrowdStrike, as Cloudflare for Teams did in March 2021. CrowdStrike is extremely well positioned as a vital partner in Zero Trust. CrowdStrike & Netskope later partnered together with Okta & Proofpoint in June 2020 as a complete solution.
Continuous Analytics
But security needs don't stop with simply securing user access at the start of the request – it had to remain secure throughout the lifespan of the request. By leveraging the signals they can receive from the identity & device posture partners, as well as from the traffic going through the ephemeral network connection, Zero Trust platforms can assess risk and trust continuously through the lifespan of the connection, and can dynamically adjust itself based on changes in context or if it detects abnormal behaviors.
Continuous Analytics is about utilizing ML/AI over all the known identities and devices to establish a base line of expected behavior (what a user or device normally does), then continuously profile the session to flag any risky or anomalous activity it sees. The process is known as User & Entity Behavior Analytics (UEBA), and the goal is to flag deviations from the norm in an internal risk score. Rules are built around those risk scores to trigger actions, such as requiring additional forms of identification during authentication (requiring MFA), stopping an action, or severing the connection. This means that Zero Trust can take an adaptive posture that is proactive, instead of reactive. Access is conditional based on the risk scoring, and it can dynamically adapt if it determines the risk level is too high, and perform actions like blocking a download or terminating access completely if warranted.
Does a user normally always log in from a variety of networks in Chicago during the daylight hours, but is now appearing on one from Beijing at midnight? Does a user normally download megabytes of files, but is now downloading hundreds of gigs? Does a user normally use one device (a laptop), but is now coming from an unexpected one (a web server)? Continuous Analytics are extremely helpful at detecting compromised systems and user accounts, as well as insider threats, brute-force attacks, changes in permissions, and attempts to access unauthorized areas.
Continuous Analytics was originally called "Continuous Adaptive Risk and Trust Assessment" (CARTA) by industry minder Gartner in 2017. Luckily, that acronym didn't take hold. The entire ecosystem of Zero Trust access, plus identity and device posture partners, plus continuous analytics, is now typically called the Zero Trust eXtended (ZTX) Ecosystem – if you want to use the mouthful that industry minder Forrester coined in 2018.
I think it best to simply call all of the above Zero Trust.
Exciting Directions
Beyond analytics, there are other exciting new directions that Zscaler, Okta and Cloudflare are taking Zero Trust from here.
Analytical Moves
The ecosystem seems pretty well defined at this point, but I believe Continuous Analytics is the area where we see some jockeying amongst the various players in the Zero Trust ecosystem. Okta and CrowdStrike have both made some interesting moves here.
CrowdStrike has been making some serious enhancements to expand reach of its core threat detection system more and more into Zero Trust. In September 2020, it acquired Preempt, a behavioral analytics service over identity. This gave them the core technologies to add conditional access features, in order to allow for more real-time access control and threat prevention. Preempt applies ML/AI over data from identity stores (like Microsoft Azure AD, Okta, or PingID) and other auth sources, in order to detect identity-based attacks and unauthorized access attempts in real-time. This allows for the system to react to perceived threats, and to then block, notify, force re-authentication, or further challenge the user with MFA. Essentially, it helps harden the security of the identity store. This eventually turned into their Falcon Identity Threat Detection (ITD) product.
CrowdStrike then created a partner integration feature called Falcon Zero Trust Assessment (ZTA), which allows them to provide continuous real-time security posture assessment across all protected devices. It can dynamically adjust the conditional access based on risk assessment as it continuously reads the device posture and performs compliance checks. It can also pull in identity data from Okta, whom they partnered with in order to factor in identity signals in the risk analysis. This feature takes the conditional access & behavioral analytics features of Preempt, but uses it over devices. This power of this integration was highlighted with the partnerships announced across all the major Zero Trust platforms, including Zscaler, Cloudflare, Akamai, Google, Okta, and Netskope, in order to integrate CrowdStrike's risk engine into their Zero Trust threat detection systems.
In other (related) moves, CrowdStrike showed how it wants to improve the strength of its threat detection. In October 2020, CrowdStrike enhanced its threat detection capabilities by integrating feeds from 3rd party threat intel partners into ThreatGraph, which allows for providing more contextual signals in device protection. So it was not that surprising when, in Feburary 2021, they acquired Humio as an enhancement their threat detection capabilities. Humio is an observability platform that, per CrowdStrike, has a log ingestion architecture that can perform at the speed & scale required by ThreatGraph (their massive graph database at their core for their threat detection architecture). This allows CrowdStrike shifts its EDR into what is known as eXtended Detection and Response (XDR) – which greatly enhances the amount of contextual data they can pull into ThreatGraph. (Think of XDR as EDR+context.) I also think XDR features enabled by Humio will greatly enhance their cloud workload protection features (EPP for cloud containers), as it can now pull in network and application metrics. [The Humio acquisition will be more deeply explored in a later post. It opens up other possibilities as well, such as allowing more Observability features from the Falcon EPP agent.] As an investor, I really like both acquisitions by CrowdStrike - but Preempt's technology, in particular, really solidifies them as a vital partner in the Zero Trust ecosystem.
But while CrowdStrike has been strengthening their continuous analytics features (including around identity, slightly moving into Okta's turf), Okta has not been sitting still, and it has been expanding its features around devices & its own continuous analytics features. In October 2020, Okta announced a new integration feature called Okta Devices. This allows for devices to directly communicate with Okta's Threat Insight (their core threat intel engine) in order to ingest device posture signals from EPP/EDR vendors. It also enables other interesting features since Okta can now tie more closely to the device, like passwordless logins in Okta FastPass (tying authentication to specifically that identity on that device).
Besides the many new product lines announced in Oktane'21 in April 2021, Okta also announced new analytics capabilities around a new integration feature called the Okta Risk Ecosystem. This allows Okta to serve as the centralized risk engine for collecting risk signals from across the security stack (such as devices, apps, and networking services like Web Application Firewalls). The device, IP, and location signals they collect are all coming from their Okta Devices integration feature just mentioned. It is currently available only in Early Access preview (aka early beta).
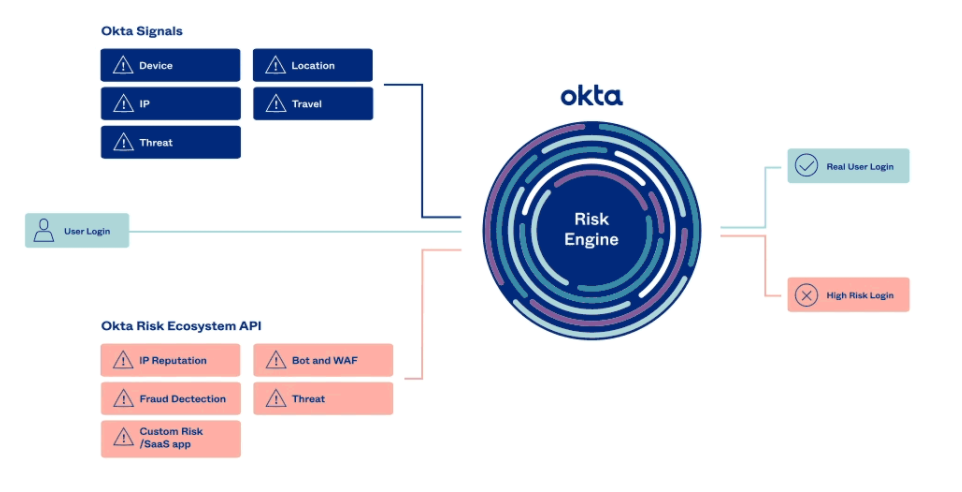
While CrowdStrike's latest moves seem to be solidifying it as a vital part of the Zero Trust ecosystem, I cannot say the same for Okta. They did not specifically mention if their Risk Ecosystem was capable of real-time behavioral analytics. If not, then Okta is not fully shifting into the continuous analytics side of Zero Trust, happening AFTER the initial authentication. I'd like to see Okta move this new Risk Ecosystem towards Zero Trust and continuous analytics.
Zero Trust Over SaaS
Zero Trust has thus far been focused on protecting internal applications, meaning on-premise or cloud-based applications that an enterprise wants to only make available privately to its workforce or partners. (For instance, an internal HR application.)
After Cloudflare introduced its Cloudflare for Teams product, it later more deeply integrated the SWG together with the Zero Trust to allow enterprises to force all SWG usage to go through Zero Trust for determining authentication and access. This allows applying authorization rules and governance over SaaS providers, and almost acting like an SSO that can control governance. This seems a unique approach from other Zero Trust platforms, and would allow for very granular access controls over calls being made to the underlying SaaS service, such as restricting what Zero Trust users could call '/admin' URLs on a SaaS web app. It will be interesting to see where this leads.
Edge-based Browser Isolation
Cloud-based Browser Isolation is not a new concept. It is feature that enhances an SWG, since, as middle-man proxy for web requests, it can become a specialized security buffer. As a user retrieves a web page, the SWG can capture and render the page in a sandbox (throwaway environment), then deliver an interactive copy to the end user, so they are not directly exposed to any malware or threats contained within it. Fantastic idea, yet existing solutions have not been performant, which then greatly slows down the end user's entire experience.
New edge-native Zero Trust platforms have an advantage here, as edge networks allow for the process to be done so much nearer to the end user. Cloudflare announced its browser isolation product in March 2021 (which it acquired from S2 Systems in January 2020). Zscaler announced its browser isolation product in April 2021 (which it acquired from Appsulate in May 2019).
Workload Segmentation
Beyond human-to-machine requests, Zero Trust can also be used for machine-to-machine requests, like API-to-API intercommunication, or having APIs interact with IoT or OT devices. Zscaler just moved heavily into this direction, with the announcement in December 2020 of their new Zscaler Cloud Protection (ZCP) product line, which extends identity-based Zero Trust from users to workloads.
In particular, the Workload Segmentation part of ZCP allows them to use Zero Trust to create ephemeral network connections between workloads. So as a service needs to intercommunicate with another service, it can go through the same Zero Trust process that a user talking to an application would. As an investor, this is an extremely exciting extension of their platform, as it now gives them more than one direction to scale usage (users vs workloads).
Zscaler also isolated their underlying Zero Trust architecture into what they dubbed the Zero Trust Exchange (ZTE), which can now secure any-to-any connection between users, apps, workloads, and IoT & OT systems.
Zero Trust Privilege Access Mgmt (PAM)
Beyond managing and securing application access, Zero Trust can also be used over infrastructure access, such as logging into servers or databases.
Okta is moving heavily into this direction, first with its Advanced Server Access product, which it recently extended further with its new Okta PAM product. Cloudflare is also chipping away at infrastructure access, by now allowing Zero Trust access to SSH via a browser interface. I expect them to continue bringing in more and more features around Zero Trust infrastructure access.
Secure Access Services Edge (SASE)
SASE ("sassy") Networks, also known as Zero Trust Edge, combine Zero Trust access with networking-as-a-service, in order to interconnect dispersed users, services, infrastructure, and networks together. Zscaler and Cloudflare, as globally dispersed edge networks, are extremely well situated for this. [Much more coming on this in a later post!]
Competitive Space
Two flavors of products emerged from identity-based access - Zero Trust Network Access (ZTNA), which typically requires some type of agent be installed on the user's device to communicate with the cloud service, and requires integrating the service with an IAM, and, less frequently, Identity Access Proxy (IAP), a cloud proxy that only ties directly into its own identity system.
The major Zero Trust SaaS providers:
- Zscaler ZIA (SWG) + ZPA (ZTNA)
- Netskope SWG + Private Access (ZTNA)
- Palo Alto Prisma Access (SWG + ZTNA)
- Akamai Enterprise Threat Protector (SWG) + Secure App Access (ZTNA)
- Cisco Umbrella (SWG) + Duo Beyond (ZTNA)
- Illumino Core (SWG + ZTNA)
- Proofpoint Meta (ZTNA)
- Google BeyondCorp Enterprise (IAP)
- Okta Access (IAP)
- Cloudflare Teams - Gateway (SWG) + Access (ZTNA)
Identity partners include Okta, PingID, CyberArk, Duo (Cisco), and Microsoft Azure AD. Device posture partners include CrowdStrike, SentinelOne, Tanium, Carbon Black (VMWare), Palo Alto, Cisco, and FireEye.
For now, there is a lot of success happening within the Zero Trust ecosystem, as the pandemic has fueled a new wave of interest in helping them corral user access since their workforce is now more scattered than ever. Companies clearly need a centralized method to unify how its workforce and partners can access the necessary applications to perform their work. There is clearly a lot of competition in the Zero Trust space, but I believe that the vital role that identity and device posture play in establishing the validity of a request are critical. Hypergrowth companies like Okta and CrowdStrike would seem to be in the ideal position of being critical partners to the Zero Trust and SASE Network paradigms. I feel this gives both companies a long-tail of opportunity.
As for the competitive Zero Trust space, I feel that edge networks have an advantage over the legacy networking security players that are still adapting their products from hardware appliances to cloud-native, especially as Zero Trust initiatives start migrating into SASE Networks. In particular, the clear hypergrowth in Zscaler and Cloudflare have most of my attention. Netskope is also edge-native (after a retooling of their architecture in 2019), and remain a private company to watch.
Where does it all go from here? Start putting all these new directions in place, with improvements in continuous analytics, machine-to-machine communications, and infrastructure access all via Zero Trust, and a bigger picture starts to emerge. Zero Trust can become a secure network to allow anything to connect to anything, anywhere. [To be explored in more detail later, with SASE Networks!]
Add'l Reading
I first covered the basics of identity management and security in my Okta technical review in May 2019. I then did a deep dive into cybersecurity in my Flavors of Security series from October 2019. It is all still highly relevant, with breaches still appearing in the news every week! Read them if you want to learn more about cybersecurity threats & solutions, or to dive more deeply into the underlying technologies that power Zero Trust, such as how ephemeral network connections happen under the hood (cloud proxies or micro-segmentation).
I later explored the Okta, CrowdStrike, Netskope and Proofpoint partnership in The Age of Hacking post when it was announced in July 2020.
I cover the Zero Trust industry heavily for my premium subscribers. I just explored the recent Executive Order on improving the cybersecurity of the US Federal Government agencies & contractors what industries will benefit, and how CrowdStrike, Okta, Zscaler, and Cloudflare are positioned. Later this summer, I will be diving deeper into SASE Networks. Sign up!
-muji
