Well, well, well. Another SaaS-based company just IPO'd after we saw Figma back in July. This time it was Netskope, the first next-gen security provider to IPO since Rubrik a year and a half ago.
Netskope should be a familiar name if you have been following next-gen security takes in my blog, as I heavily covered the rise of SSE (Zero Trust et al) and SASE in 2020-2022. Let's break down what they do and see how enticing this newly public company is. This will also be of interest to other next-gen security competitors like Zscaler, Palo Alto, Fortinet, and Cloudflare in SSE/SASE, as well as Rubrik and CrowdStrike in data protection, and Okta, Sailpoint, and CyberArk in identity.
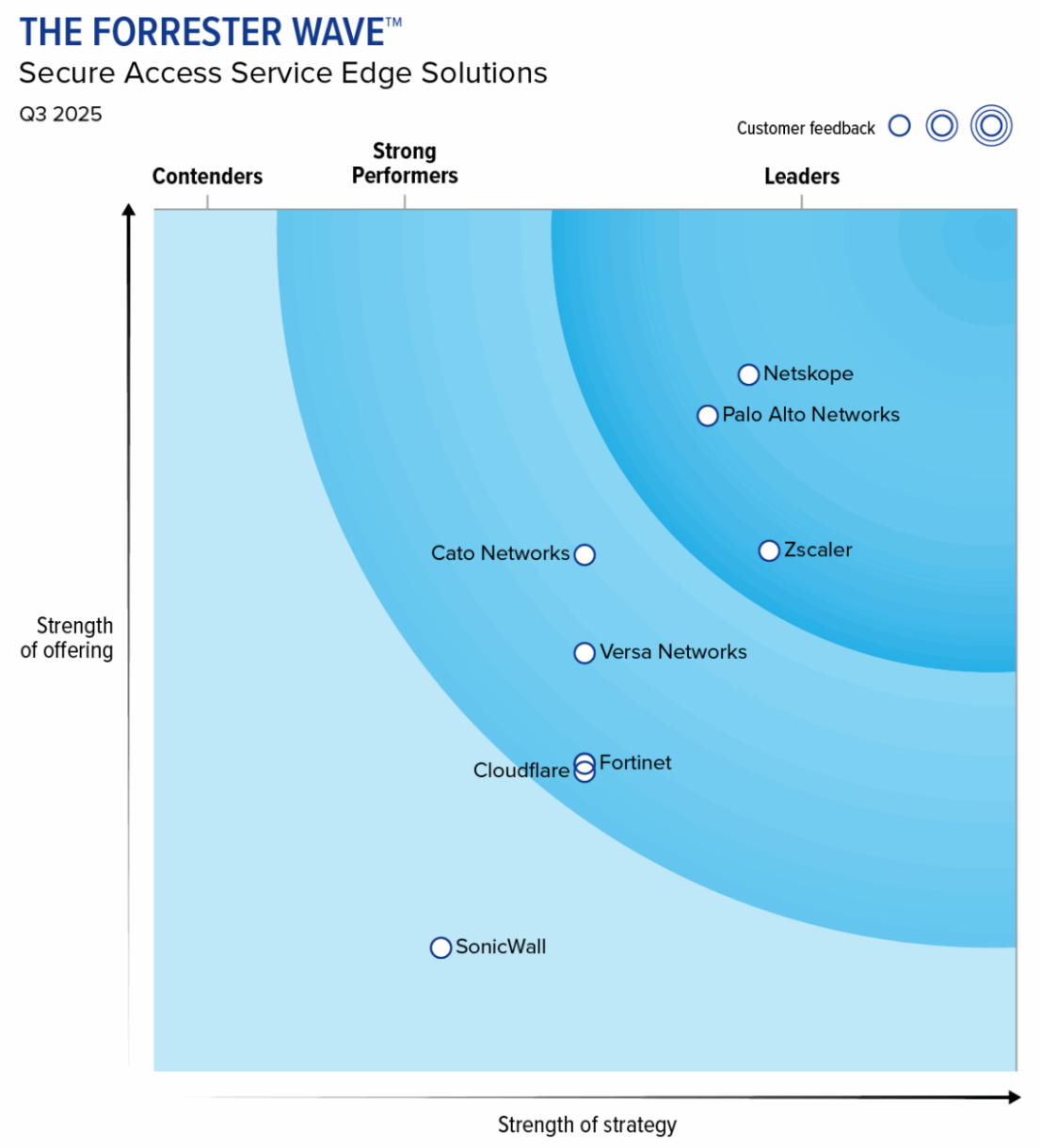
- Netskope has evolved from CASB to SSE to SASE over the past few years, and continues to be a top leader per industry reports.
- This is a mini-Zscaler that is earlier in its trajectory, and they have some of the highest growth in security right now (after CyberArk and Rubrik). But like most other security names I follow, their hypergrowth is gradually slowing.
- They are growing fastest in EMEA and APJ, but GTM improvements are also re-accelerating their core Americas (North and South) market as they push deeper into Federal and mid-market.
- Will Netskope become the next Zscaler? I see some cracks in that trajectory. Like when I looked at SentinelOne vs CrowdStrike, they aren't growing as fast as Zscaler was at the same ARR level.
- While they are a top leader in their core market (SSE/SASE/DLP), they seem behind Zscaler in subsequent adjacent moves into Workload Zero Trust and CNAPP (which again reminds me of SentinelOne).
- Profitability metrics are improving, but are still deeply negative. The big improvements to FCF margin are being significantly aided by a billing change implemented earlier this year. But they do seem likely to go non-GAAP positive soon as a coming catalyst.
- They invented their own profitability metric (Incremental Gross Margin) that IMHO is worth ignoring.
- Growth vectors include continued international expansion, further expansion into Federal and mid-market segments domestically, and upselling into their AI and data security features.
Netskope wil report its first earnings since IPO later this week.
I entered Rubrik a year ago, and covered their successful shifts to cloud & subscription licensing, their subtle shift into AI data delivery (Annapurna), and the overall Resiliency landscape. Since then, I've covered Q4, Q1, and Q2 earnings results, as well as how their platform has evolved over the past year (including new areas like Identity & DevOps Resilience). Last week, I looked at their recent Q3 results, which include yet another platform shift – this time leveraging their resilience foundation to now allow them to oversee, manage, and remediate enterprise AI agents.
Lately, I have been heavily focused on the AI industry, including NVIDIA's latest moves across networking & sovereign push, and the great AI buildout by OpenAI, xAI, and the neoclouds over the next few years. I then looked deeper at the neocloud thesis, and have expanded coverage to CoreWeave, Nebius, and IREN. Thus far, this has included a deep dive into CoreWeave and its big whale deals, a take on its Q3 earnings and buildout delay, and a look at its current and future buildouts, its funding mechanisms, and where it is going next.
I have also looked at earnings results and product moves from Figma, NVIDIA, CoreWeave, Samsara, Axon, Cloudflare, and Rubrik.
Join Premium for insights like this every week across AI & ML, Data & Analytics, Next-Gen Security, DevOps, SaaS platforms, and the hyperscalers.
Sections:
- Netskope
- A brief history of SSE/SASE
- Platform skope
- Newer areas
- Pushing into AI security
- What they are not
- Partners
- A global edge network
- Financials
- A Zscaler comparison
- GTM
- Final thoughts
To catch up on their core SSE and SASE features, see What is Zero Trust? and What are SASE Networks?, and past Zscaler coverage.
Shorter version: SSE helps protect over user traffic between disparate enterprise users and apps (including both SaaS and private apps). SASE bolsters this further by protecting the network traffic between disparate locations and environments.
I also recommend reading What are Edge Networks? for more on edge network architecture.
Netskope
Netskope was founded in 2012 as a cloud-based Cloud Access Security Broker (CASB), a middle-man service between enterprise users and the enterprise SaaS tools that they use on a day-to-day basis. This allowed enterprises to gain visibility into SaaS app usage patterns, as well as isolate unsanctioned tools (Shadow IT) and underutilized licenses. They quickly rose into a market-leading solution, and by 2016-2020 had consistently ranked as one of the top leaders in Gartner's Magic Quadrant for CASB.
CASB had been considered a point product during the rise of cloud infrastructure & SaaS apps, until the later emergence of Zero Trust and SASE tools in 2017-2019, which was further honed into the SSE subset in 2022. Today, CASB is considered a core feature in SSE platforms.
While Netskope started in CASB, they have been busy morphing into broader SSE and SASE since 2018. Direct competitors include Zscaler, Palo Alto (Prisma Access line), Fortinet, Cloudflare, Cisco, Check Point/Perimeter 81, and private startups Cato Networks, Versa Networks, and Menlo Security.
A brief history of SSE/SASE
Though 2018-2020, Zero Trust and SASE were being recognized as important next steps in secure enterprise networking (especially in highly dispersed, hybrid, or multi-cloud environments), and competition was rapidly increasing for Zero Trust leader Zscaler.
- Networking leaders Palo Alto and Fortinet had been transitioning from physical firewalls & SD-WAN appliances to (VM-based) virtual ones for cloud environments, then started creating SASE layers (via software-defined networking) that interconnect across all those on-premise and cloud environments.
- Cloudflare was leveraging its globe-spanning edge network to move more heavily into SSE and SASE.
- Meanwhile, Netskope was busy moving into SSE/SASE from the CASB flank.
- Microsoft was also a leader in CASB, but was much later to moving into SSE. They finally announced an Entra SSE product in 2023 [as previously covered in a paid post, but more on this below].
Zero Trust pioneer Zscaler remained the sole leader in SWG and ZTNA industry reports during this time, but Netskope started to appear in 2020 as an upstart. After Gartner consolidated CASB, SWG, and Zero Trust into a single SSE category in 2022, a new leader board emerged – much to Zscaler's consternation [previously discussed in my premium Zscaler Q222 take]. Palo Alto and Netskope seemed to quickly catch up with Zscaler as the SASE and SSE concepts were being refined into specific feature sets (secure networking vs secure user traffic).
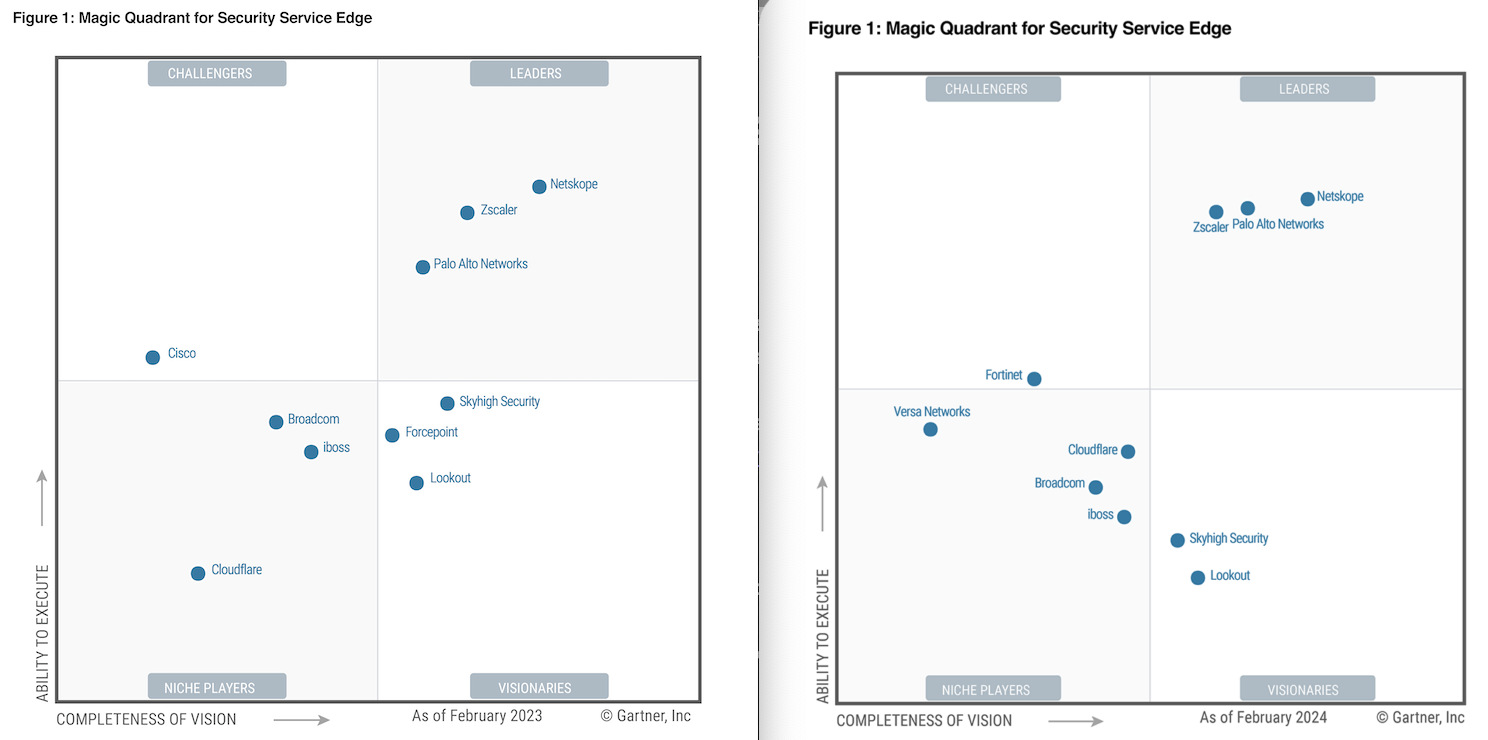
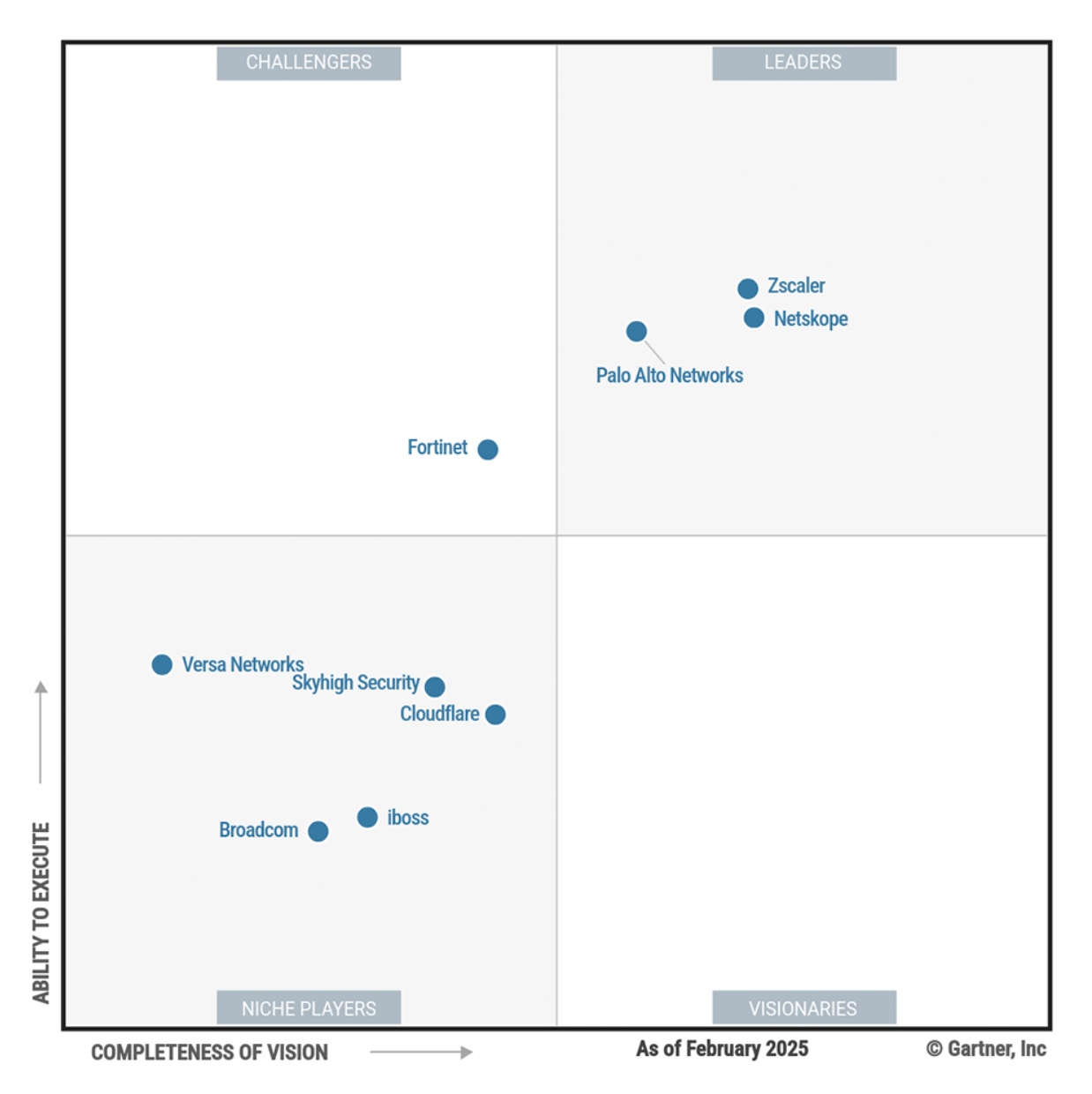
Now all of these SSE players are battling it out in SASE as well, which bolsters their SSE capabilities further with secure networking and interconnects across disparate locations and on-prem & cloud environments. Palo Alto and Fortinet had an advantage here with existing physical and virtual SD-WAN & NGFW solutions that they could combine with new SSE features to form a broader SASE solution.
Netskope moved into SASE after its acquisition of Infiot in Aug-22. Zscaler and Cloudflare are newer entrants in these SASE reports, as they lacked the SD-WAN branch interconnectivity that Gartner saw as a requirement. Zscaler and Cloudflare both eventually added Branch Connector and Magic WAN Connector [premium link] in 2023 and now appear on these reports.
Gartner originally called this category "Single-Vendor SASE" but now considers it all just SASE after every big player has caught up to their requirements.
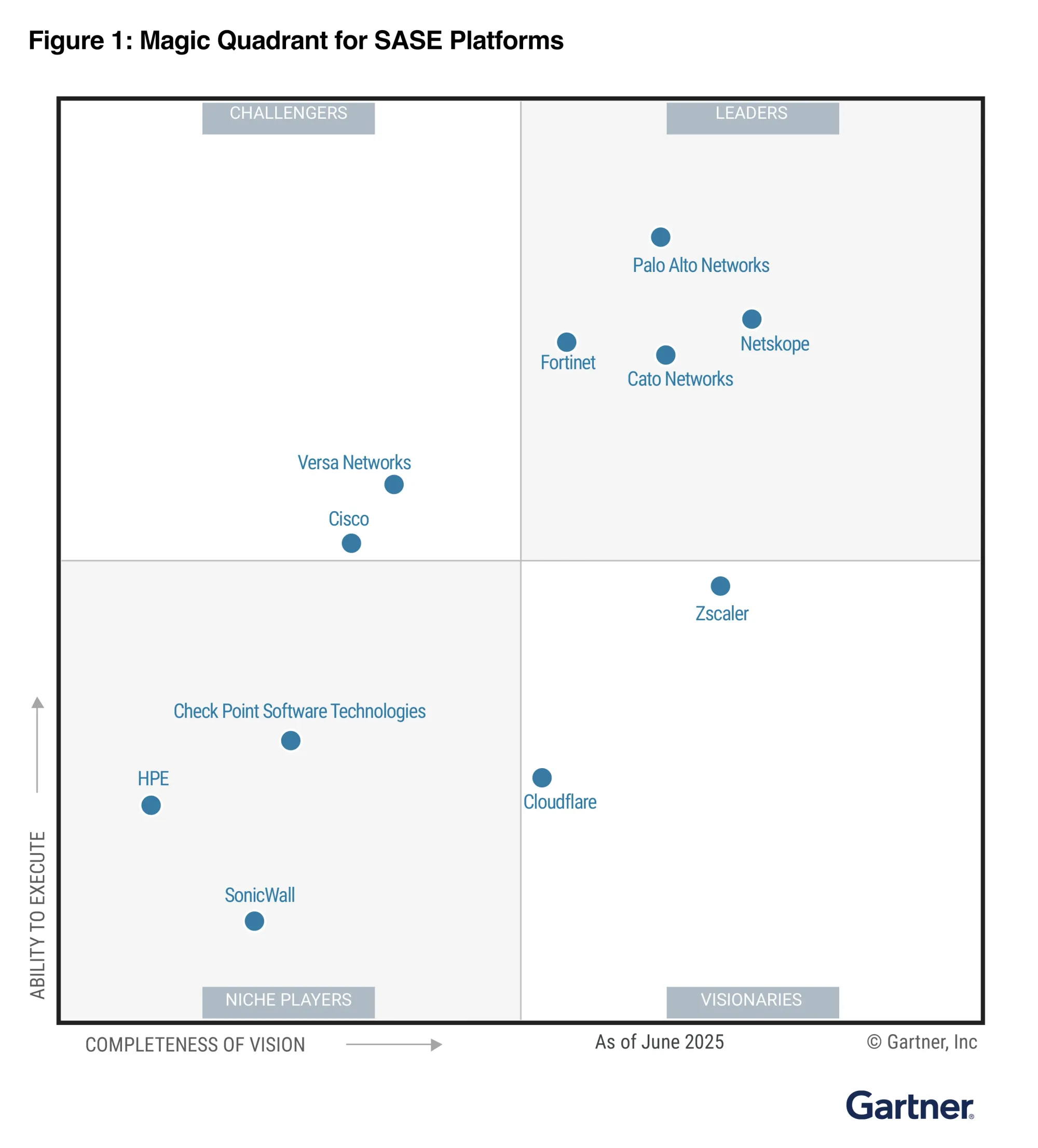
Platform skope
Today, Netskope is a fully-featured SSE/SASE platform that it calls "Netskope One". [Yes, the same naming scheme that Cloudflare started using 4 years prior!]
- On the SSE side, this includes SWG, ZTNA, CASB, Remote Browser Isolation (RBI), and data protection across DLP (inline) and DSPM (scanner).
- On the SASE side, this includes cloud-based SD-WAN and gateways for interconnecting clouds, data centers, branches, IoT devices, and users' devices, as well as a FWaaS for inline network security and a DEM for monitoring over all enterprise network activity.
- More recently, they have added in a new Secure Enterprise Browser, and, like every SSE competitor, are moving more deeply into inline data security over AI usage.
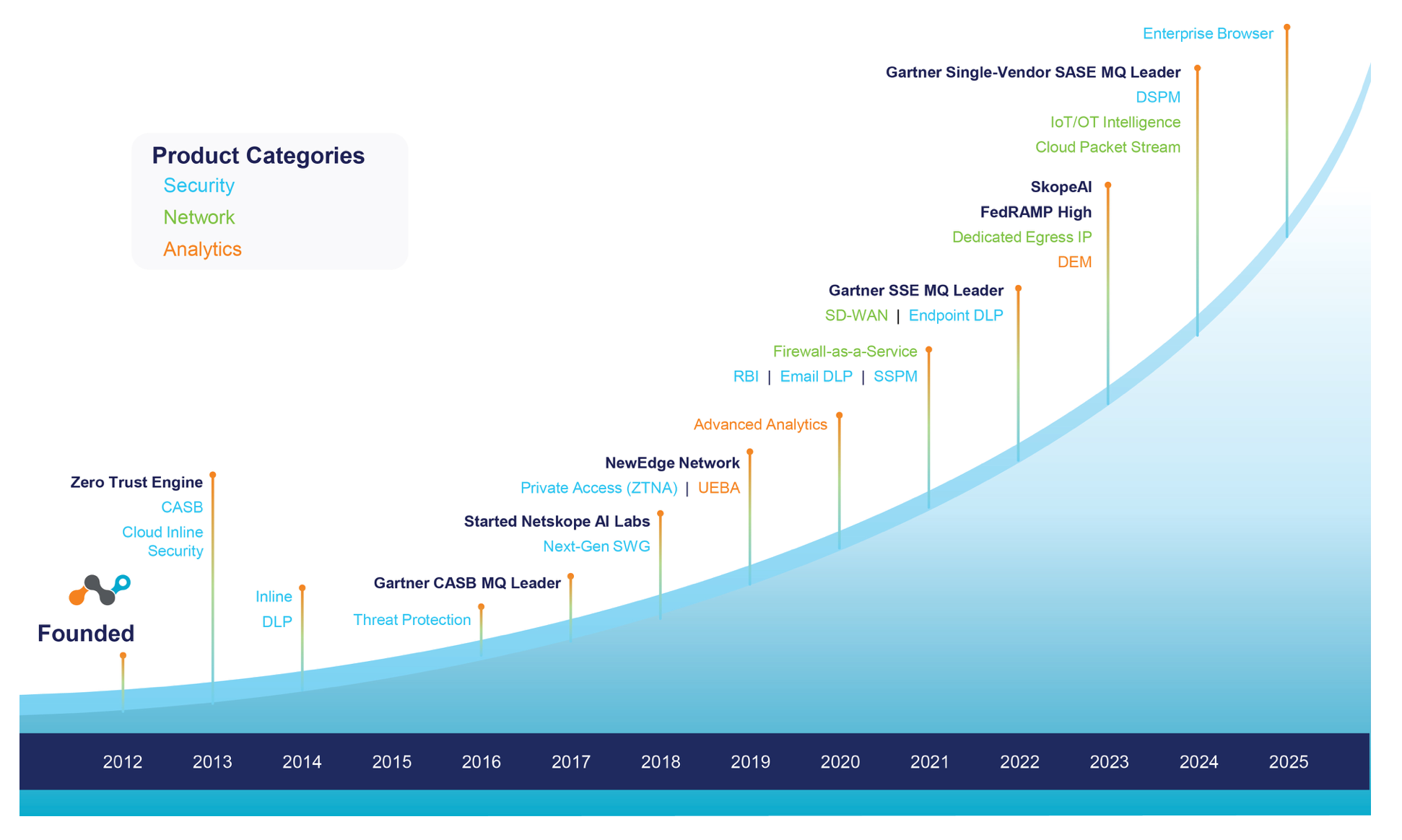
They acquired a number of companies along the way. As part of filling out their SSE featureset, they acquired RBI, SSPM, and IoT/OT features over the past few years, pivoted into SASE with a cloud SD-WAN platform, then bolstered their platform with DEM and DSPM.
- They acquired Randed for remote browser isolation (RBI) in Aug-21, based in Spain.
- They acquired Kloudless for SaaS Security Posture Mgmt (SSPM) in Aug-21, based in Taiwan. This pivoted their CASB into an SSPM that scans for misconfigurations and sensitive data in enterprise SaaS tools like MS365, Salesforce, and GitHub.
- They acquired WootCloud in Jun-22 to add in Zero Trust features for IoT/OT.
- They acquired Infiot for Cloud SD-WAN in Aug-22, which pivoted their SSE heavily into SASE. This was initially called "Borderless SD-WAN" when it went GA in Apr-23, but now undergirds their entire One SASE platform.
- They acquired Kadiska in Sep-23, based in France. This added inline DEM monitoring to their SSE, SD-WAN, and entire NewEdge edge network.
- They acquired Dasera in Oct-24 to add in Data Security Posture Mgmt (DSPM), bolstering their inline DLP with a data scanner.
Newer areas
Like other SSE platforms, they have been leveraging AI in their platform, have been moving deeper into SaaS app and data protection, and been pushing heavily on AI protection. Like Palo Alto, they have also added in their own secure enterprise browser.
Leveraging AI
Netskope has long been leveraging ML and AI internally for threat detection. In mid-2023, they added a new AI layer dubbed Skope AI to further enhance their product suite with LLM and chatbot capabilities to improve the DLP data classification and threat detection with contextual awareness.
They also pivoted their SSE to monitor and protect over Generative AI usage. Today, they tout having a full suite of AI security features across their SSE, Data Security (DLP + DSPM), and Skope AI that can monitor and secure enterprise AI usage.
They had been slow to add inline Copilot to their own platform, but had a few recent announcements here.
- They pivoted their new DSPM to better protect over enterprise data being fed into AI models in training, fine-tuning, and through vector databases (RAG).
- They announced a new MCP server that allows AI security copilots to interact with Netskope.
- They also enhanced Skope AI with a new Copilot (chatbot) for setting up Zero Trust connections. [This new Copilot was mentioned in both PRs linked above.]
SaaS app protection
SaaS Security Posture Mgmt (SSPM) is a security feature that is highly adjacent to CASB. While CASB is an inline monitoring & control tool over the user traffic to SaaS apps, SSPM is a cloud scanner (via API) over those same SaaS apps for monitoring misconfigurations and excessive privileges. These features obviously combine well, and both CNAPP and SSE/SASE providers have been adding this feature over the past 3 years.
Palo Alto added SSPM to their CASB in 2022, and Zscaler (Canonic), Cloudflare (Vectrix), CrowdStrike (Adaptive Security), Netskope (Dasera), and Fortinet (Suridata) have all added this via acquisition. CNAPP startups like Orca and Wiz seem to be relying on partners for this for now. [I previously looked at Canonic, Vectrix, and Adaptive Security acquisitions in Zscaler, Cloudflare, and CrowdStrike premium coverage.] When Cloudflare acquired Vectrix, it looked a lot like a combined CASB & SSPM, and Cloudflare formally released their SSPM earlier this year.
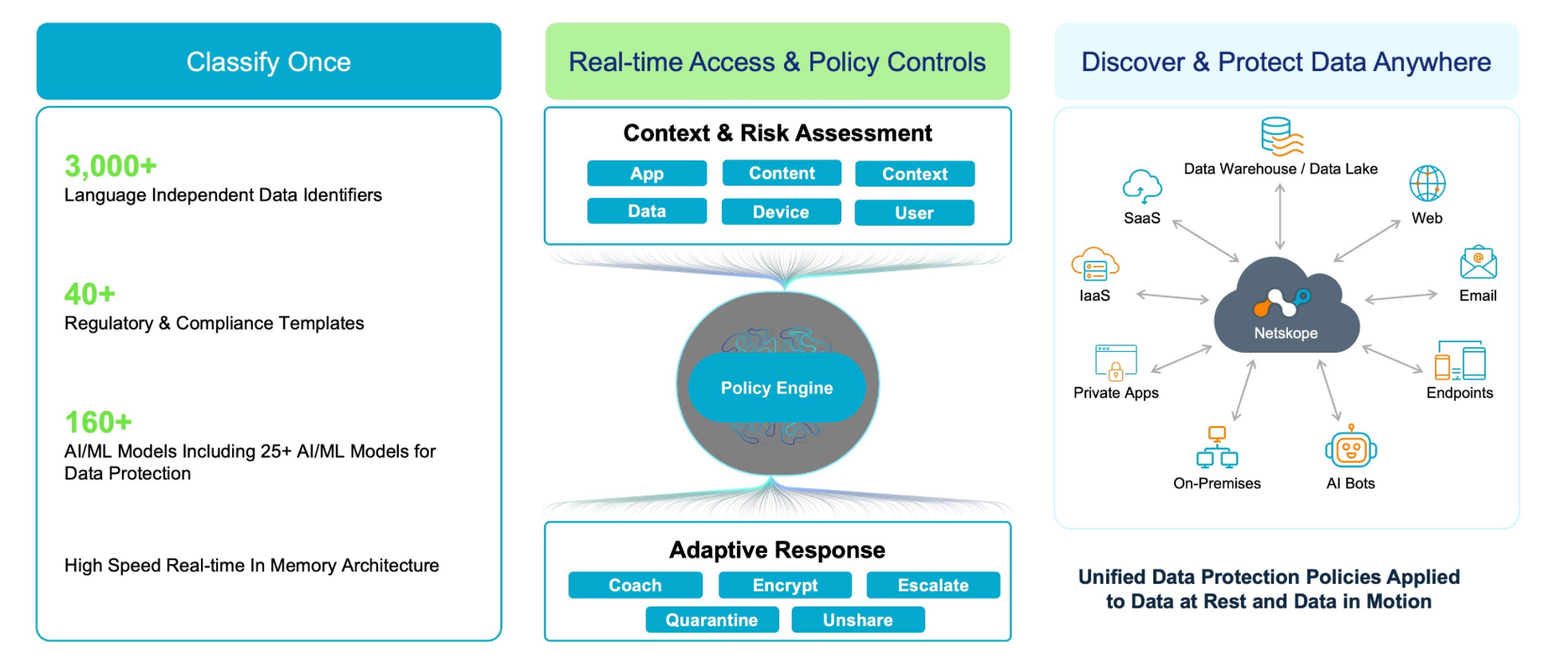
Data protection
From there, Netskope has been heavily focused on building out its Data Security features, like every other SSE/SASE, XDR, and CNAPP provider seems to be. After CNAPP startups Wiz and Orca added data scanning (DSPM) in 2022-2023, Palo Alto (Dig Security), CrowdStrike (Flow Security), and Rubrik (Laminar) added it via acquisition. Zscaler announced a new DSPM a year ago. A bit late to the party, Netskope finally acquired their own a year ago. There is no sign yet of a DSPM module from Cloudflare yet (though it likely an easy pivot from their SSPM and existing DLP) – Cloudflare seems to be behind Zscaler and Netskope in DLP featureset, likely why they continue to lag in those SSE industry reports above.
After combining their inline DLP and DSPM data scanner into an overall Data Security module, Netskope has been busy in 2025 bolstering it further.
- They announced a DLP On-demand service in Apr-25, taking their inline capabilities and making them available via an API as a service. This seems likely to be adding a consumption lever to pricing.
- As noted before, they pivoted the new DSPM in Apr-25 towards AI data protection, to classify and monitor all sensitive data across RAG use and AI training or fine-tuning.
Enterprise browser
Netskope also added a new secure enterprise browser in Feb-25, which provides enterprise customers with a specialized web browser that has Netskope's SSE features directly embedded. These dedicated browsers essentially ensure that enterprise users (including contractors and those using BYO devices) are on Netskope's SSE network – so are natively using the SWG (to SaaS apps) and Zero Trust (to private apps) modules. This is a more elegant solution than the Remote Browser Isolation (a cloud-based sandbox that serves as a middleman), but not every SSE provider is heading in this direction.
This will compete with Google's new Chrome Enterprise, as well as Palo Alto's Prisma Browser (via its Talon acquisition). This also competes with existing RBI solutions from Zscaler and Cloudflare. Palo Alto and Netskope now have both solutions, offering an RBI and an Enterprise Browser.
From the PR: "Bring-your-own device (BYOD) policies and the temporary work requirements of contractors are two of many use cases that can create security risks for businesses based on access to data. Enterprise browser functionality that is well integrated with a full SSE offering means that organizations can count on data security not only when users interact with cloud and SaaS apps, but also to prevent data leakage both to apps and unmanaged endpoint devices, ensuring SSE adaptive policy controls are consistently applied."
Google doesn't seem to be moving into SSE/SASE directly, but instead is leveraging SSE & SD-WAN partners in its new Cloud WAN service. With Chrome Enterprise, they are also relying on partners, having integrations with Zscaler (ZTNA), Cisco Duo (endpoint trust), and Trellix (DLP). [Remember that DLP On-demand? Netskope could tie in its DLP like this as well.]
So Zscaler has decided to partner with Google's browser instead of supporting its own enterprise desktop application. There is no sign of an enterprise browser emerging from Cloudflare or other SSE competitors, either.
This makes me wonder why Netskope decided to build its own desktop application. I assume it is revenue-generating, but I would rather see them move into CNAPP. And given how both Palo Alto and Netskope are already big Google Cloud partners in Cloud WAN, perhaps they will go both ways (have their own browser plus, like Zscaler, integrate with Chrome Enterprise).
Pushing into AI security
All SSE/SASE and CNAPP competitors are moving into AI security on a few fronts.
- 1) New CASB/SWG-based platforms are emerging that sit as a middleman between enterprise use of AI engines, in order to monitor usage, costs, and prompts and responses (inputs and outputs) over time. Observability and SSE companies, such as Datadog, Zscaler, and Cloudflare, are adding features like this, as has Netskope. This becomes especially important in the age of agentic AI, where an AI can interconnect with internal or external tooling or data sources.
- 2) AI Security Posture Mgmt (AI-SPM) scanners are now appearing. After Wiz added this in late 2023, Palo Alto, CrowdStrike, Orca, Zscaler, and Cloudflare have added similar features. These are typically a pivot of an SSPM to focus on scanning the security posture of public AI engines for misconfiguration and for tracking prompts and input data. Oddly, there is no sign of this yet from Netskope.
- 3) Data Protection platforms are all veering heavily into enterprise use of AI, by extending DLP (inline detection) and DSPM (data scanning & classification) into tracking how that sensitive enterprise data moves into public AI engines, as well as into custom AI training, fine-tuning, and vector databases (RAG). Zscaler, CrowdStrike, and Cloudflare have all made recent announcements here, as has Netskope.
- 4) SSE platforms are starting to leverage their Secure Web Gateways (SWG) to secure the user traffic to and from public AI engines, and Zero Trust connectivity to secure private AI model & app stack deployments. Palo Alto (AI Access), Cloudflare (Cloudflare for AI), and Zscaler (AI Guard) have all been pushing on Zero Trust connectivity to AI models. As noted before, Netskope has been focused on this since the introduction of Skope AI.
- 5) Real-time cloud protection features (the CWP in CNAPP platforms) are also being extended into custom AI model & app stack deployments as well. Palo Alto just acquired Protect AI here, and CrowdStrike is pushing its CNAPP into NVIDIA-based AI inference environments (NIMs).
- 6) Traditional app security services (WAF/WAAP) are also being extended over AI app stacks. Cloudflare is extending its NGFW into a Firewall for AI, and API Gateway has morphed into an AI Gateway.
Netskope seems to be pushing most on the 1st and 3rd directions above via CASB and DSPM, and, even if they aren't going deeper in CNAPP, I soon expect the 2nd direction to show up too in their SSPM morphing into an AI-SPM.
I think SSE platforms have the best stance here on AI protection compared to CNAPPs, as they already oversee all the enterprise user traffic to and from SaaS apps in their CASB and SWG components. [Of course, many SSE platforms are becoming CNAPPs themselves, so these categories are blending.] Palo Alto, Zscaler, Fortinet, and Cloudflare are all well-positioned as SASE providers over enterprise networking and data movement. Netskope could join them, but it seems a bit behind.
I believe they are extremely well-positioned to take advantage of nearly all of the new AI security directions above (except #5, which provides real-time protection via a deployed CWP agent). And while they are not moving into CNAPP like Zscaler or Palo Alto, I could also see them moving more deeply into that direction from here (adding in real-time protection and posture scanning over those interconnected multi-cloud environments).
What they are not
Let's be clear about what Netskope is not moving into, next-gen security-wise:
- They have not veered heavily into workload protection. Zscaler has moved from users to workloads (and per-user to per-workload pricing), and Cloudflare also combines Zero Trust with their core app security features (WAF/WAAP and secure interconnects) over app-to-app communication. This could be a potential vector going forward.
- They have not veered into broader CNAPP. They started in CASB (SaaS usage monitoring) plus added in SSPM (SaaS security posture scanner), but haven't gone deeper into other scanning or real-time features now embedded in most CNAPP platforms (CSPM, CWP, container security, etc). This could also be a potential vector going forward, as it is for other SSE providers like Zscaler and Palo Alto.
- They have not veered into Identity Protection in any way. Zscaler and CrowdStrike both now provide ITDR (detection) and ISPM (scanning) solutions, Palo Alto is acquiring CyberArk (IAM, PAM, and ITDR), and CrowdStrike is going further (veering into CyberArk and Okta's lane) into endpoint PAM.
- They are obviously not an XDR, SIEM, or Identity provider in any way. They are complementary to these platforms, so only tangentially compete with CrowdStrike, SentinelOne, CyberArk, Sailpoint, or Okta. The only area of competition is from any of those companies that have a CNAPP focus (specifically in SSPM or DSPM).
- They are clearly moving deeper into DLP and Data Protection, an area that Rubrik is also heavily focused on. However, as mentioned before, I find the Rubrik platform [premium] to be complementary to SSE, XDR, and CNAPP providers with DLP/DSPM, given that it focuses on data access via backup, not overseeing real-time user or device traffic.
Partners
They have partnerships in multiple directions:
- Hyperscaler cloud partners in Microsoft, Google, and AWS.
- Complementary next-gen security partners in CNAPP, XDR, IAM, and SIEM, including partnerships with Wiz, CrowdStrike, and SentinelOne, as well as Identity providers (Okta, CyberArk, Sailpoint, Ping ID), SIEMs (Cisco/Splunk, Microsoft, Sumo Logic, and recently CrowdStrike), and other next-gen security players (Mimecast, Extrahop, Illumio).
- Data resilience providers like Rubrik, Commvault, and Cohesity.
- SD-WAN providers like Aruba, Aryaka, Citrix, Fortinet, VMware, Juniper, Palo Alto, and Versa. Most SASE providers support interconnections with existing enterprise SD-WAN providers such as these.
- They also partner with the enterprise SaaS platforms they protect over (in CASB/SSPM), including MS365, Salesforce, Slack, ServiceNow, Asana, Zoom, Workday, Box, Dropbox, Elastic, Miro, and others. This year, they expanded protection over Google Workspace and OpenAI's ChatGPT enterprise.
- They also have a large number of GSI/MSP service partners. [More on this in GTM.]
Netskope was an early partner in Microsoft's security AI (Security Copilot). Netskope then announced an integration with Microsoft's new Entra SSE at the end of last year. This year, they have tied into their SIEM (Sentinel) and integrated their Data Security platform with Microsoft's data governance tool (Purview).
They recently announced an integration into Google Cloud's new Cloud WAN, which allows an enterprise to connect its Netskope SASE network with other hybrid and multi-cloud environments via Cloud WAN. Google also has partnerships with other SSE/SASE providers (including Palo Alto, Fortinet, and Menlo Security) and SD-WAN providers. Google does not seem to want to go directly into SASE itself, but wants to be the global connective fabric across them. [Microsoft has a similar service in Virtual WAN, but it only has integrations from only with SD-WAN and NGFW partners. It isn't allowing any SSE integrations, even from its own Entra SSE, from what I can tell.]
Given these interconnection partnerships with Microsoft and Google, Netskope appears to be taking an "all of the above" approach in order to tie more deeply into all of these hyperscaler SSE/SASE-related initiatives.
A global edge network
With SSE/SASE platforms, a significant difference in approach lies in how the platform manages its underlying networking architecture. Netskope appears to be positioned between Cloudflare (backed by an edge network with dedicated backbones) and Zscaler (backed by private links and public internet), unlike Palo Alto and Fortinet (backed by a hyperscaler cloud edge network).
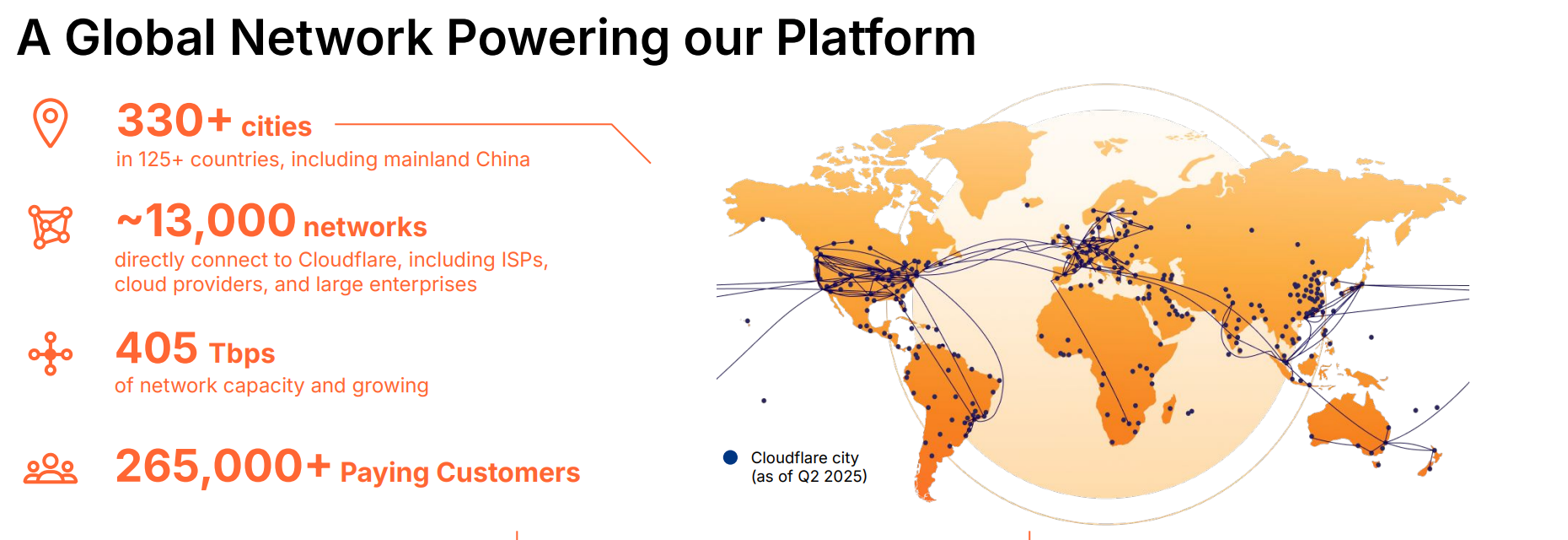
- Cloudflare's edge network spans 330 cities and is backed by 405Tbps of global network capacity (backbone). They have 13K interconnects with Internet eXchanges (IX), cloud regions, and enterprise networks.
- Zscaler's platform utilizes over 150 distributed data centers for platform serving and interconnect points (typically located near IX points), and relies on the public Internet and private links for routing between them. They also use hyperscaler clouds for hosting centralized features.
- Palo Alto utilizes hyperscaler clouds for hosting its cloud services instead of its own data centers, including utilizing Google Cloud's edge network with 202 PoPs for interconnection points and routing. [Palo Alto also insists that more PoPs are not the solution, and that they solved it with software via their SASE App Acceleration module.]
- Fortinet also uses hyperscaler clouds for interconnection points (like Palo Alto, it utilizes Google Cloud as well as AWS). However, Fortinet appears to be taking an "all of the above" approach as it shifts from using hyperscaler PoPs (like Palo Alto) to managed PoPs (like Cloudflare) – and even into self-owned PoPs based on its own ASICs. [More on that move in the Convequity blog, who follow Fortinet heavily. But I don't agree with their ASIC excitement here.]
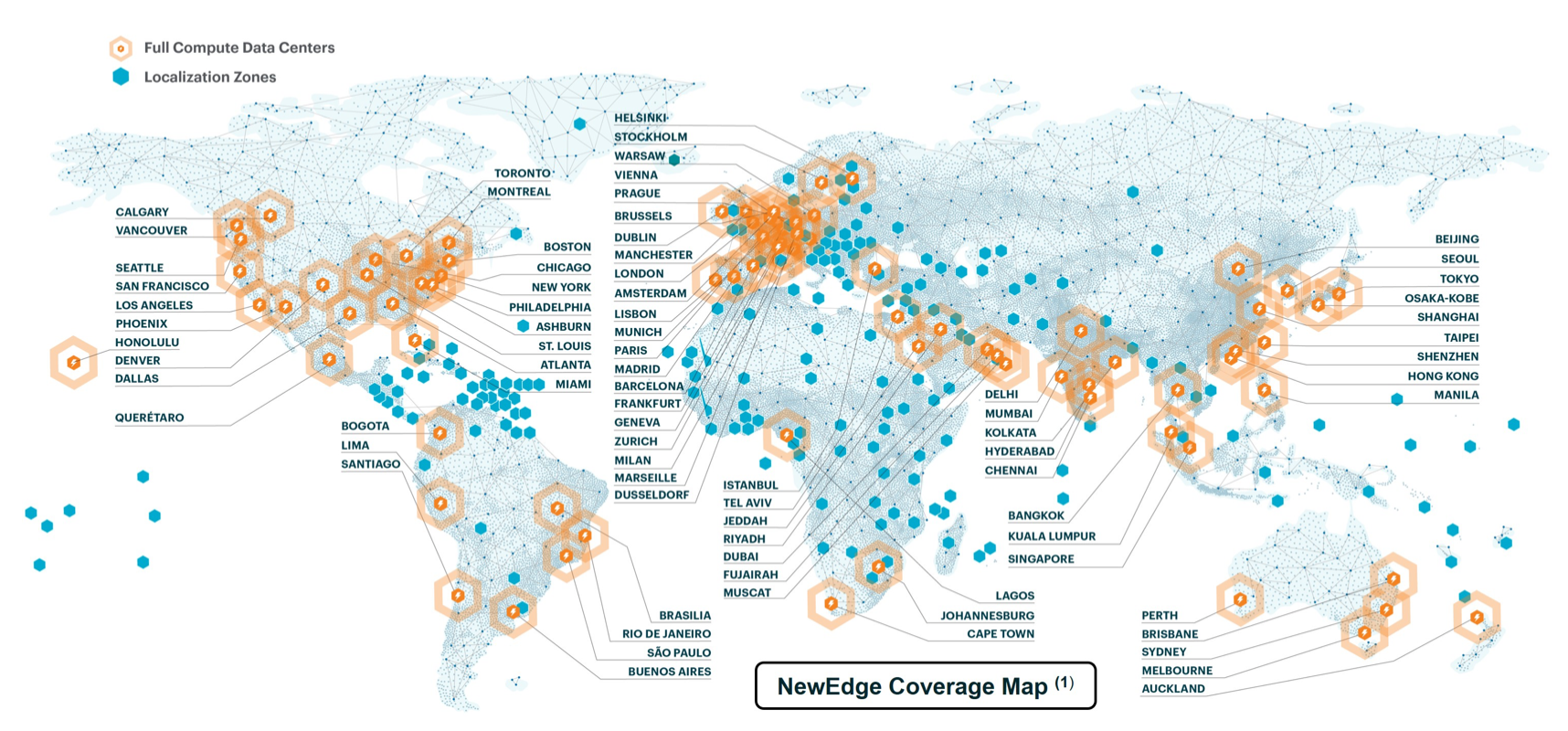
Netskope touts its global network as "NewEdge", which interconnects 75+ regions across 120+ data centers. Beyond serving the "hot spots" for traffic (US, EMEA, APAC), they also have 200 "localization zones" as local on-ramps into the nearest data center. This edge network was further expanded in 2024 and 2025 with 4 new regions and 4 major expansions.
It's these localization zones that really set them nearer to Cloudflare than Zscaler, which creates local on-ramp points into their network that are nearer to dispersed end-users and locations in areas not served by their data center network. Also, like Cloudflare, they have a unified stack that they distribute across all data centers, rather than running services across separate networks like Zscaler.
Per the S-1: "Each of our NewEdge network data centers are available to all customers and capable of running all of our products. For example, there is no traffic re-routing to other data centers to run certain products that are not available in the originating data center, allowing our NewEdge network to deliver superior performance with the lowest possible latency."
A whitepaper in 2023 and a third-party report they commissioned in 2024 help provide further details about NewEdge.
From the report: "To optimise network performance, every NewEdge DC is extensively interconnected with direct peering to Microsoft and Google in every region possible, as well as primary web/cloud/SaaS providers (e.g. AWS, Salesforce, IBM Cloud, Oracle etc) and ISPs. Also notable that Netskope supports public (IX) or private (PNI) peering NewEdge DCs directly with customers’ networks."
From the S-1: "Our NewEdge network leverages an extensive interconnection strategy, featuring over 10,000 network adjacencies to over 700 unique Autonomous System Numbers. This strategy uses premium transit and comprehensive peering with Internet Service Providers and leading web, content delivery, cloud, and SaaS providers. For example, our NewEdge network maintains peering and direct interconnection with Amazon Web Services, Google Cloud Platform, and Microsoft Azure datacenters in mutually available locations, along with other major cloud and SaaS platforms."
The report noted NewEdge having 3.2K networking interconnects as of 1.5 years ago, and as of their latest NewEdge expansion in early 2025, it was up to 5K. The S-1 then inflates this to over 10K – I'd like more detail from mgmt on how this metric doubled in a few months.
NewEdge is directly peered with AWS, Microsoft, and Google regions, and the web page notes how they protect 15% of MS365 users today – an area that Zscaler heavily focuses upon. They used to tout having interconnects into China, but that is clearly being deemphasized in today's geopolitical climate. [Only 2 mentions of China in the S-1, only in supply chain risks.]
Unfortunately, they haven't been very public with how they handle backbone, but my assumption is that they have dedicated backbone connections between data centers and regions, as does Cloudflare. They note having a "full mesh" network, suggesting redundant routing that lets them sidestep outages and provide high availability. They also have the ability to segment this network for data sovereignty needs, and the whitepaper notes having 12 different geo-regions for this.
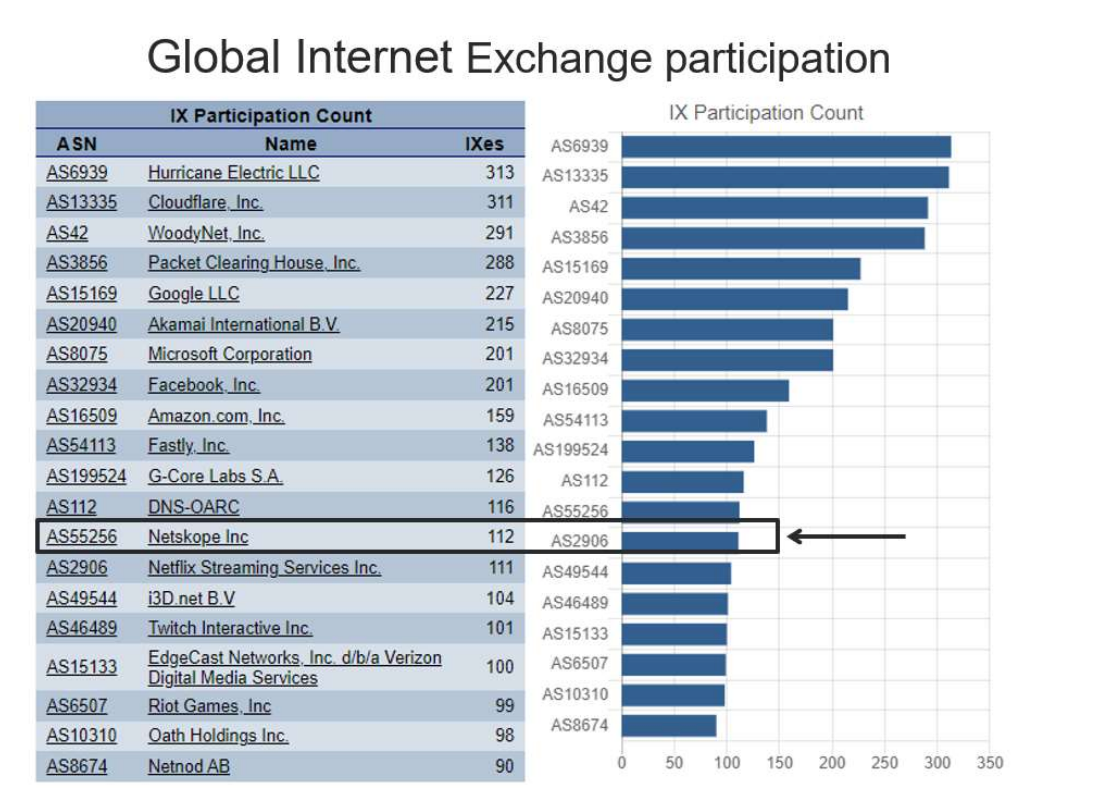
That 3rd-party report noted that Netskope is the 12th most active Internet interconnection (IX) participant, up there with the hyperscalers (Amazon, Meta, Google, Microsoft). Note Cloudflare in 2nd place (as well as Akamai and Fastly), which is from their long history in core app services (CDN, DDoS, WAF) served by their edge network – a huge strength that enabled them to enter the SASE market with an interconnection advantage.
Like with Cloudflare, I believe this architecture was a good choice. This decision entails higher upfront costs, as it requires maintaining a global set of data centers and networking interconnects that are constantly expanding and being upgraded. However, this then provides them with more flexibility and control over the enterprise traffic that is continually routed around the globe.
From the report: "The company has since invested more than $250m deploying its NewEdge network ... with over 200 individuals dedicated to its platform engineering team. It is worth noting that this was the same set of individuals who previously built some of the world’s largest public clouds and CDNs, including AWS and Limelight – not a bad CV. Taking a private cloud approach gives Netskope full control of its infrastructure. It means that – rather than relying on public clouds - or where not all services are available in every region - there is no backhauling of traffic required with its NewEdge architecture and the company retains complete control over all networking aspects of service delivery.
Feedback from a user base exceeding 3,000 customers suggest that NewEdge was a key factor in their selection process in three key areas: it makes Netskope more accountable for end-to-end performance; it allows for more robust SLAs and – finally – it avoids the problem-related finger pointing that is common with vendors relying on 3rd-parties."
Key to this network is their Netskope One Gateway, a set of interconnection options for dispersed enterprise users, devices, data centers, branch offices, IoT/OT devices, private apps, SaaS apps, remote APIs, databases, and more. Locational connectivity is via their SD-WAN Gateway, which has physical and virtual appliances for secure interconnectivity of data centers and enterprise networks, as well as branch, cellular, and roaming office connectors. [Netskope previously had physical appliances for on-premise deployment, but retired these in March to focus solely on virtual appliances (deployed as VMs). However, they do still provide physical appliances as a gateway into their SASE network for branches, as Cloudflare and Zscaler have both added.]
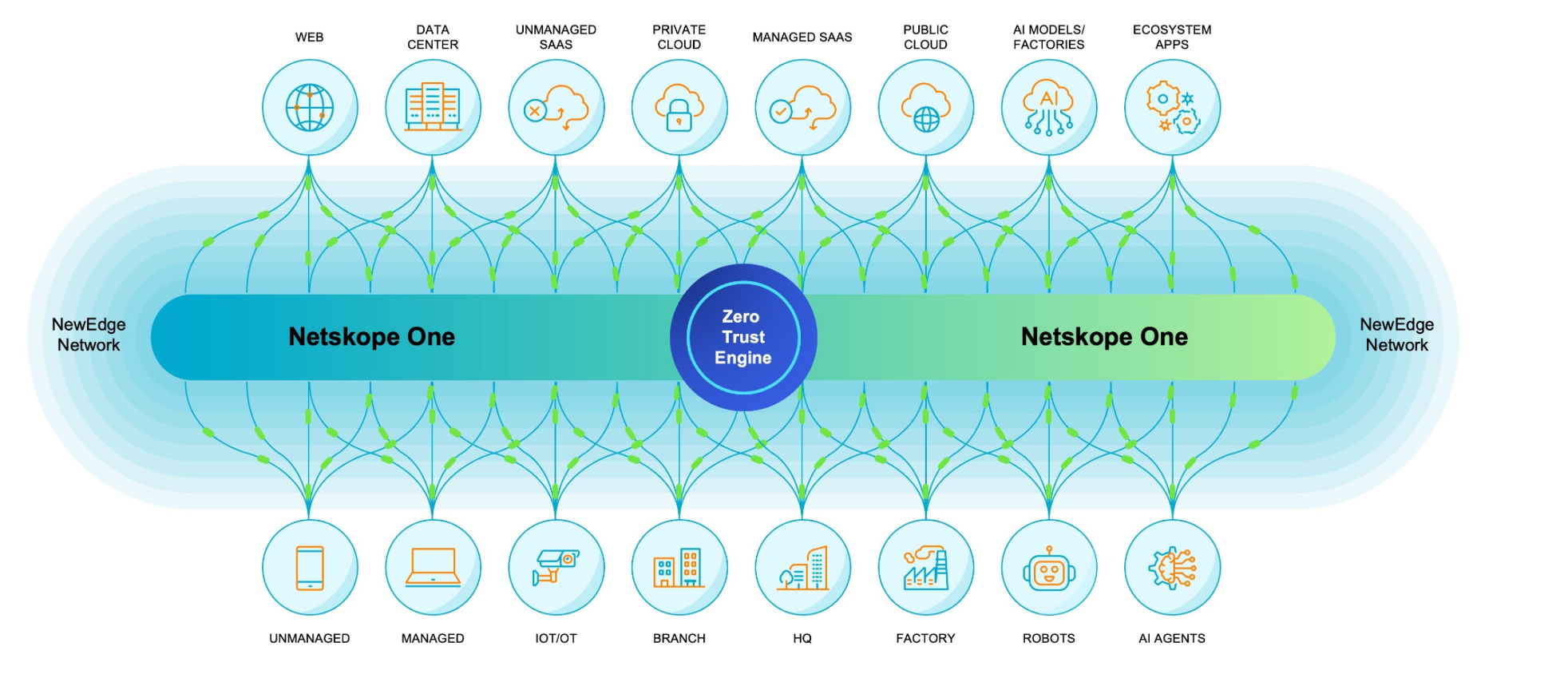
Per the S-1: "Our convergence of networking and security also extends to branch and multi-cloud environments through our Netskope One Gateway, forming a new thin, lightweight on-premises network edge. Our Netskope One Gateway, available in physical, virtual, cloud, or client form factors, consolidates SD-WAN and a range of local network services such as routing, WiFi, 5G, firewall, IPS, IoT/OT intelligence, DEM, and Edge Compute, along with a seamless on-ramp to our Netskope One platform, into one simple, zero-touch provisioned device. This microservices-based architecture is designed to eliminate the need for disparate network and security appliances at each location, reducing complexity and cost at scale. Netskope One Gateway software also runs as a service within our NewEdge network to optimize transcontinental site-to-site and site-to-cloud traffic. Combining our SD-WAN product at the network edge with our SSE offering enables organizations to achieve a true SASE architecture that converges security and networking in a single platform, delivering secure and optimized connectivity for users and applications, regardless of their location."
Financials
They gave us a hint of their financials a year ago in Jun-24, when they hit $500M in ARR from 3400 customers. However, the S-1 is the first real look at their execution.
- They are now at an ARR of $707M, growing +33%.
- TTM Revenue was $616M, growing +31%.
- Revenue in Q2 2025 was $171M, growing +32% or +8.3% seq, a slight acceleration.
- Customers rose +21% to 4317.
- They have 1372 large customers (custs>$100K), growing +29%. These represent over 85% of ARR, implying smaller customers are 15% of the mix.
- They have 111 massive customers (custs>$1M), growing +32%. These represent 37% of ARR, implying the rest of those large customers (ARR of $100K to $1M) are 48% of ARR.
- NRR rose +5pp to 118%, while gross retention rose +1pp to 96%.
| Q423 | Q124 | Q224 | Q324 | Q424 | Q125 | Q225 | |
|---|---|---|---|---|---|---|---|
| Revenue | $113.89 | $121.00 | $130.25 | $138.52 | $148.49 | $157.74 | $170.76 |
| ... YoY | 36.40% | 32.70% | 30.52% | 30.38% | 30.36% | 31.10% | |
| ... QoQ | 7.31% | 6.24% | 7.65% | 6.35% | 7.19% | 6.23% | 8.26% |
| ... net new | $7.76 | $7.11 | $9.26 | $8.27 | $9.96 | $9.25 | $13.02 |
| ... TTM | $406.88 | $439.17 | $471.27 | $503.66 | $538.26 | $575.00 | $615.50 |
| ... TTM YoY | 32.29% | 30.93% | 30.61% | ||||
| Gross Margin | 66.4% | 65.4% | 67.9% | 70.4% | 71.5% | 73.6% | 74.5% |
| Op Margin | -42.2% | -54.1% | -43.9% | -25.6% | -15.5% | -18.1% | -19.9% |
| Op margin TTM | -56.2% | -53.0% | -48.7% | -40.9% | -33.6% | -25.1% | -19.7% |
| FCF Margin | -35.4% | -54.9% | -46.1% | -20.7% | 2.7% | 11.1% | -11.5% |
| FCF margin TTM | -51.2% | -50.4% | -46.9% | -38.8% | -28.1% | -11.7% | -4.3% |
It looks like things are going well lately. Revenue growth had flattened at the 30% level over the past few quarters, then showed a slight reacceleration in Q2. And while deeply unprofitable, they are trending in the right direction in gross margin, op margin, and FCF margin.
- Gross Margin has risen +6.6pp over the past year. This remains under peers like Zscaler (79%) and Cloudflare (76.2%, down from a high of 79.5% after adding GPUs across its network).
- Op margin TTM rose a whopping +29pp over the past year.
- FCF margin TTM rose an even more astounding +42pp over the past year.
- Despite this improvement, they only have a Rule of 40 TTM of 26.
They created new metrics called "Incremental Gross Margin" (GAAP and Non-GAAP) that try to highlight operating leverage on incremental revenue. However, I am completely ignoring these, as it seems to ignore past sunk costs such as the build-out of their operational teams and their NewEdge edge network, as well as ignores how today's costs might lead to future revenue instead of current.
Per the S-1: "Incremental gross margin is intended to measure the efficiency of our revenue growth in generating incremental gross profit. It is calculated as the year-over-year change in gross profit, divided by the year-over-year change in revenue. ... These measures provide insight into what portion of each marginal dollar of revenue translates into incremental gross profit or non-GAAP gross profit, as applicable, reflecting our ability to grow revenue, manage cost of revenue, and efficiently scale."
FCF in particular has shown massive improvements over the past year, including two positive quarters (then sank back negative in the most recent Q) – however, this seems to be due to a billing change that made multi-year customers get billed annually.
From the S-1: "Additionally, subscriptions that are invoiced annually in advance or multi-year in advance contribute significantly to our short-term and long-term deferred revenue. Earlier this year, we shifted more of our business to annual billing of multi-year contracts. As a result, we expect our growth rate of billings and deferred revenues to decline in subsequent quarters, and we may experience negative growth in billings or deferred revenue in certain quarters in the future. "
The rise in NRR (+5pp) and GRR (+1pp) is also very impressive, but it is important to read the fine print. For some reason, GRR excludes contraction as most others define it.
From the S-1, p88: "Our dollar-based Net Retention Rate ("NRR") reflects the percentage of our ARR from existing customers, inclusive of the effects of upsell, cross-sell, contraction, and churn. ... Our dollar-based Gross Retention Rate ("GRR") reflects the percentage of ARR retained from existing customers, inclusive of the effects of churn."
A Zscaler comparison
| Metric | Zscaler | Netskope |
|---|---|---|
| Revenue | $719.2M | $170.76M |
| ... YoY | +21.3% | +31.3% |
| ... QoQ | +6.0% | +8.3% |
| ... TTM | $2673M | $616M |
| ... TTM YoY | +23.3% | +30.6% |
| ARR | $3.015B (+21.9%) | $707M +33% |
| ... YoY | +21.9% | +33 |
| Op Margin TTM | 21.7% | -19.7% +29pp |
| FCF Margin TTM | 27.2% | -4.3% +42pp |
| Rule of 40 TTM | 50 | 26 |
| Custs>$100K | 3494 +13% | 1372 +29% |
| Custs>$1M | 664 +18% | 111 +32% |
No idea why Zscaler mgmt stated in the Q126 earnings call that Red Canary is not material in their Q or that organic growth was stable! (See my rant about this on Twitter.)
However, let's look at Zscaler when it was at a similar size to Netskope today.
- When Zscaler was at a ~$700M implied ARR level (Q321, aka Feb-Apr 2021), it was growing +59.6% YoY, and eventually accelerated up to +62.6% over the next few quarters.
- When Zscaler was at a ~$700M implied ARR level (Q321), TTM op margin was 11.6%, and TTM FCF margin was at 21.1%.
Will upstart Netskope become a Zscaler-level powerhouse over time? I'm not so sure, as, like when comparing upstart Sentinel One to giant CrowdStrike [premium], I see some cracks in their trajectory. Let's look at where other next-gen fast growers were at this level of ARR.
- When CrowdStrike was at a ~$700M ARR level (Q121, aka Feb-Apr 2020), it was growing +85.4% YoY.
- When upstart SentinelOne finally hit that same level nearly 4 years later (Q424, aka Nov 2023 - Jan 2024), it was then growing +38.8%.
Fast forward to now, and both of these EDR/XDR platforms have been at nearly the same growth levels over the past year. Today, CrowdStrike is at +23.5% TTM growth while SentinelOne is at +25.4%, with both showing slight re-accelerations in the latest quarter. SentinelOne will never catch up to CrowdStrike at this rate.
Winners keep on winning, and CrowdStrike continually proved itself the better company. CRWD eventually returned to well above the peaks hit in Nov-21, while S has languished.
Though to be fair in this comparison, I believe SentinelOne's execution along the way was impacted by some terrible mgmt decisions along the way (including questionable acquisitions at inflated prices, mgmt churn, and a lack of a cohesive plan to better shift into CNAPP).
Netskope is likely to have a better outcome.
GTM
They are a SaaS platform focused on land-and-expand, with expansion occurring from customers adding more users and upselling into new modules. They have been growing more internationally in EMEA and APJ, yet are now re-accelerating in the US/Americas.
Customers include Estee Lauder, IHG, Juniper Networks, iRobot, Gilead, QVC, Ross, Yamaha, Tivo, JLL, Colgate-Palmolive, Airbus, Home Depot, Qualcomm, SunLife, Tyson Foods, Tata Motors, Hugo Boss, and Bayer.
- The revenue mix is 56% in the Americas (North and South), 25% EMEA, and 19% APJ.
- EMEA and APJ are growing revenue fastest at +37% and +33% YoY, compared to +28% for the Americas. But while EMEA and APJ are growing faster, they are showing slowing hypergrowth.
From the S-1: "We have also made, and plan to continue to make, significant investments to expand geographically... In EMEA and APJ, we are growing our sales team and continue to expand our ecosystem of channel partners, including MSPs. We believe that our market opportunity is large, and we are committed to long-term growth through strategic investments in our business. Our geographic reach continues to expand."
- However, ARR in the Americas has accelerated over the past year from +22% to now +35%, thanks to increased S&M capacity, opening up the US Federal market with FedRAMP High, and expanding channel partners into mid-market.
From the S-1: "In the Americas (which we define as the United States, Canada, and Latin America), this includes continuing the growth of our sales team, selling into the U.S. federal government market now that we have achieved FedRAMP High Authorization, and growing our channel partners, including MSPs, to expand within the mid-market. As a result of these investments, year-over-year growth in ARR for our Americas region accelerated from 22% as of July 31, 2024 to 35% as of July 31, 2025."
- This is clearly a business driven by its largest customers, at over 85% of ARR. They note having 30% of the Fortune 100, yet only 18% of the G2K – suggesting underpenetration in large enterprises outside of the US.
- The vast majority of business (93%) comes from channel partners, with only 7% being direct – though this is not atypical in enterprise security platforms sold top-down (see Microsoft, Cisco, Palo Alto, Fortinet, Zscaler, etc). The top partner was noted as being 12% of revenue.
They note having 2900 employees, which shows a rather poor $210K of revenue per. But they are focused on improving operational leverage from here.
- S&M went from 60% to 45% of the mix over the past year.
- R&D went from 52% to 43% of the mix.
- G&A went from 14% to 11% of the mix.
They have had a few GTM shifts over the past year plus:
- They got FedRAMP High authority in Jan-24 as they added a new Fed sales head. They are especially focused on gov sales across US, Canada, EU, and Australia.
- They are pushing deeper into mid-market via channel partners, and added a new VP of Worldwide Sales.
- They also hired a new VP of EMEA and LatAm Sales from Palo Alto (from the Cortex line, not SASE) and a new VP of Americas from Mandiant, along with 2 other sales leaders from Zscaler.
- They had Forrester do an ROI study in Nov-24 that found 109% ROI over 3 years and a payback under 6 months.
Final Thoughts
As of the financials above, it appears to be a typical hypergrowth story that I'd be deeply interested in if this were 2019-2021. The SASE story is now facing more competition and more budget scrutiny; however, it remains as important as ever for enterprise security. Netskope is a leading solution and likely to remain so as they continue to mature. That said, they are well behind Palo Alto and Zscaler in moving into other adjacencies like CNAPP and workload protection (app-to-app Zero Trust).
The slight re-acceleration in the latest quarter is a good sign, but I'd really like to see an earnings report or two before I get too excited here. The company is making strong strides in profitability, but the billing change is goosing FCF margin. The improvement to NRR is very encouraging, as is the ARR growth re-acceleration of the Americas. They also seem to be underpenetrated internationally (G2K).
They remain on the watch list, and I will continue to watch them closely.
Add'l Reading
- See this Netskope S-1 breakdown from Mostly Metrics that goes more deeply into the numbers and VC investments. He notes that Netskope has a heavy number of employees for its revenue level.
- Friends of the blog Meritech also had a set of slides breaking down the S-1, and again noted the lower revenue per employee.
Past premium [paid] coverage:
- I covered competitor Zscaler heavily across 2019-2023, including their big shift into SASE. I also covered Palo Alto's shifts into next-gen security (including SSE/SASE) in Apr-22.
- See my Cloudflare catch up post in June to see how another Netskope competitor is faring. I also just looked at recent SSE/SASE industry charts in my recent Q2 take. You may recall last year how Cloudflare expanded its Zscaler migration tool to also migrate new customers off Netskope.
- Also see Microsoft's and Google's moves into SSE. I re-visited Google's moves into Cloud WAN during Cloud Week this past May, and how they have integrated it with SASE partners like Palo Alto, Fortinet, and Netskope. (And again, Palo Alto can't be too happy its edge network provider is directly competing with it now, as well as enabling its direct competitors to interconnect.) I have also discussed Microsoft's competing Virtual WAN.
- In my Q2 Cloud Week take, I also briefly discussed Google's acquisition of Wiz as well as their new secure enterprise browser, and how Zscaler is integrating with it. Palo Alto and Netskope now both compete with Chrome Enterprise via their own secure enterprise browser solutions.
- A year ago, I looked at how adjacent security areas across XDR, SIEM, and CNAPP were shifting, then had deeper dives into CNAPP, SIEM, Identity, and Data Resilience markets from there.
-muji
