I've previously covered the moves within the Zero Trust and SASE Network ecosystems. Today, it's finally time to revisit Zscaler, given the massive tailwinds it has going for it right now.
- Zscaler has seen reaccelerating hypergrowth since the pandemic began.
- Multiple pivots took place last December to put Zscaler in new directions in protecting cloud workloads, including machine-to-machine Zero Trust and SASE.
- Zscaler has vital partnerships in place with major security players that keep it highly in the mix (whether with its SASE solution or others).
- Its product lines solve networking security problems that are now in the headlines near daily (breaches! stolen data! ransomware!), with additional interest coming from US Federal Govt and in protecting the coming storm of IoT/OT traffic.
[To really understand Zscaler, I highly recommend you be familiar with the architecture of edge networks, from my prior "What are Edge Networks?" post, as well as understanding both Zero Trust and SASE in the security focused "What is Zero Trust?" and "What are SASE Networks?" posts. Probably doesn't hurt to understand the basics of cybersecurity either, in "Flavors of Security".]
Some Background
I previously owned this company from late 2018 (Q119) into early 2020 (Q220), after it had risen from +35% revenue growth to high +50% on the success of its platform and operational execution. But something happened after Q319 – after revenue peaked at +65%, the sales growth sputtered, lowering to +36% by Q220. Something was wrong, and the company was not living up to its potential. Over that time, the CEO acknowledged the ongoing issues with sales, and knew he needed expertise to help restructure the sales org, bringing on board a new CRO in Sep-19 (Q419) from Cisco. But I didn't have much patience for the continued fall, and after the continued drop to mid-30s, coupled with a drastic drop in cash flow margins in Q220 (FCF -1800bps YoY, to -2%), it was time to exit, and redirect my portfolio to other companies (luckily having just discovered Cloudflare as an alternative right then).
However, the company recovered much quicker than expected – with its sales reorg helped in large part by the global pandemic that shook the world in the very next quarter, May-20 (Q320). It suddenly found itself well positioned to solve an an incredibly urgent need, as companies needed to figure out this remote-work thing, and fast. Zero Trust had finally become mainstream, and vital, as attackers were taking full advantage of the chaotic situation most companies were in.
Now, coupled with the general mindset of moving from legacy hardware to Zero Trust to a full SASE (as now recommended by Gartner and Forrester), Zscaler finds itself in the sweet spot. It is extremely well positioned for taking a huge amount of marketshare over the next few years, as enterprises now try to figure out how to improve their networking and security postures, secure their widely distributed remote workforce across a widely distributed application/service landscape, all while continuing their transitions into the cloud (at whatever pace). Enterprises of all sizes can now let Zscaler run the entirety of their network, offloading all the IT and security expertise that, up until now, every enterprise has needed to retain internally.
The Quick Story
Let's look at their financials since they hit that low point of revenue growth in Q220.
| Q220 | Q320 | Q420 | Q121 | Q221 | Q321 | Q421 | Q122 | |
|---|---|---|---|---|---|---|---|---|
| Revenue YoY | +36.3% | +39.7% | +46.2% | +52.3% | +55.1% | +59.6% | +56.6% | +61.7% |
| Revenue QoQ | +8.2% | +9.1% | +13.9% | +13.3% | +10.2% | +12.3% | +11.7% | +17.0% |
| Billings YoY | +17.7% | +55.1% | +54.9% | +64.0% | +71.3% | +71.4% | +70.5% | +71.2% |
| FCF Margin | -1.9% | 8.2% | 8.7% | 29.6% | 11.5% | 31.6% | 14.1% | 36.2% |
| Custs > 100K | +46% | +51% | +52% | +53% | ||||
| Custs > 1M | +70% | +79% | +87% | +87% | ||||
| NRR | 116% | 119% | 120% | 122% | 127% | 126% | 128% | 128% |
Zscaler has had hypergrowth re-acceleration since its sales stumbles culminated in Q220. I hope to see this continue, and top their previous high of +65.2% in Q219. The long and the short of it is, once your company goes to Zero Trust and SASE, and pick a company like Zscaler to be the backbone of your enterprise network... you aren't ever going back to managing your own networking & security infrastructure. This is an extremely sticky service. This shift saves companies money, while lessening their risk. NOV saw a 35x reduction in infected devices after adopting. Siemens has seen a 70% reduction in infrastructure costs. GE has seen a 80% faster user experience when accessing apps.
Customers include Johnson Controls, Fannie Mae, AutoNation, Siemens, Ciena, NOV, Air France, Paychex, Hormel, Michelin, NBC, Sunkist, the FCC, and the US Navy. They break their customer segments into Majors (>40K users), Enterprise (6k-40k), Enterprise (2k-6k), and Commercial (<2k). They have a current focus on the Global 2000, but are continuing to move down the stack, with a newer focus on Enterprise (2k-6k). They state they currently have over 20M seats. The "audacious" goal from here? Per their Investment Day presentation in Jan-21, they are targetting 200M users and 100M workloads, a 10x increase. They anticipate that just their core ZIA+ZPA platform, and cross selling to existing customers, can see a 6x increase from here.
Beyond helping manage user access and security, Zscaler did a major pivot last year. They now can help manage machine-to-machine access and security as well, along with moving more fully into SASE features to become the interconnective glue that can be the backbone of an enterprise's global network. Zscaler can now be the entire perimeter. They feel like they have a $72B SAM (aka directly achievable part of their TAM). And that seems low, as they aren't including lower-end customers, or Workload & IoT/OT advancements from here (hints of future product areas).
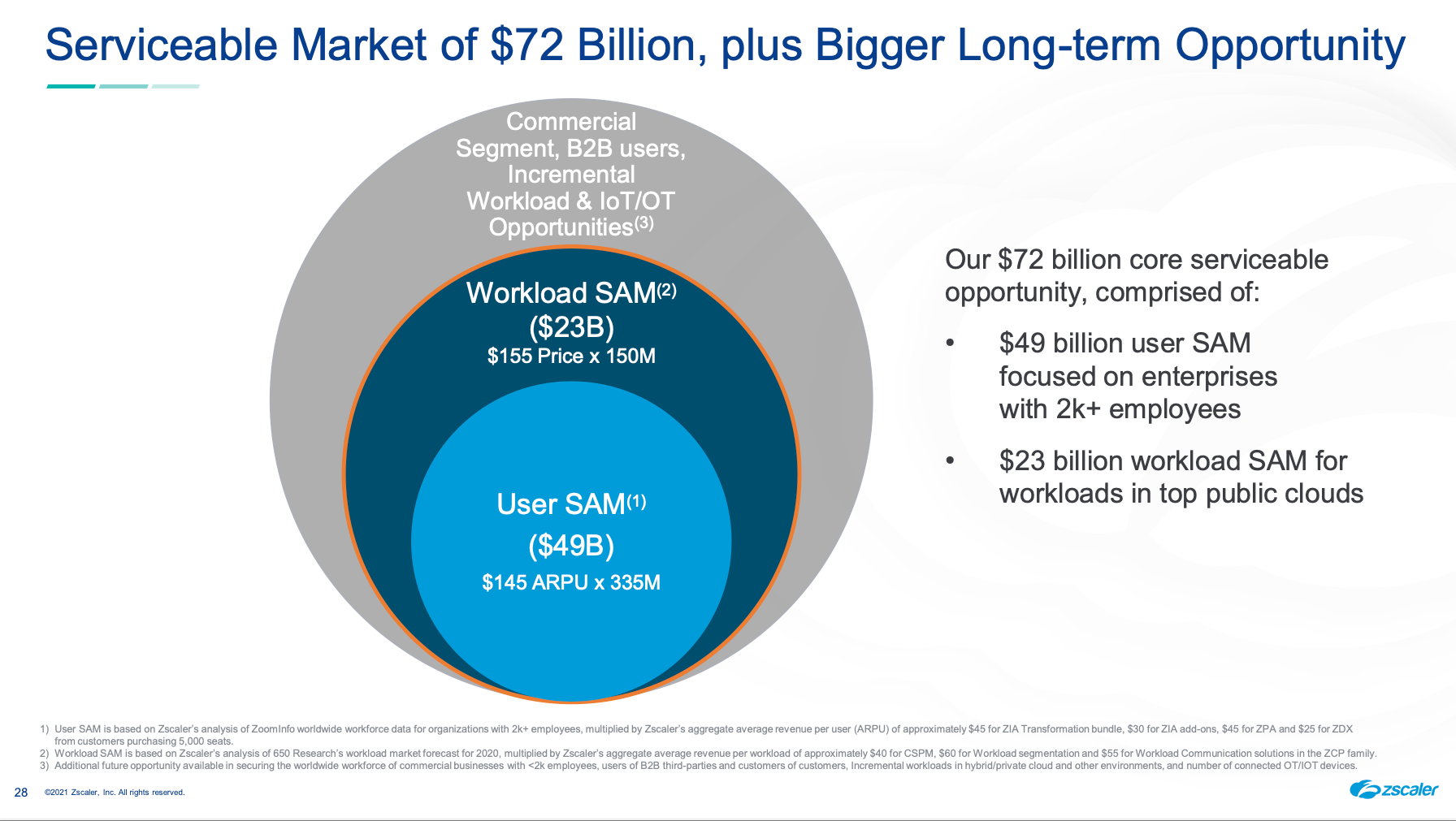
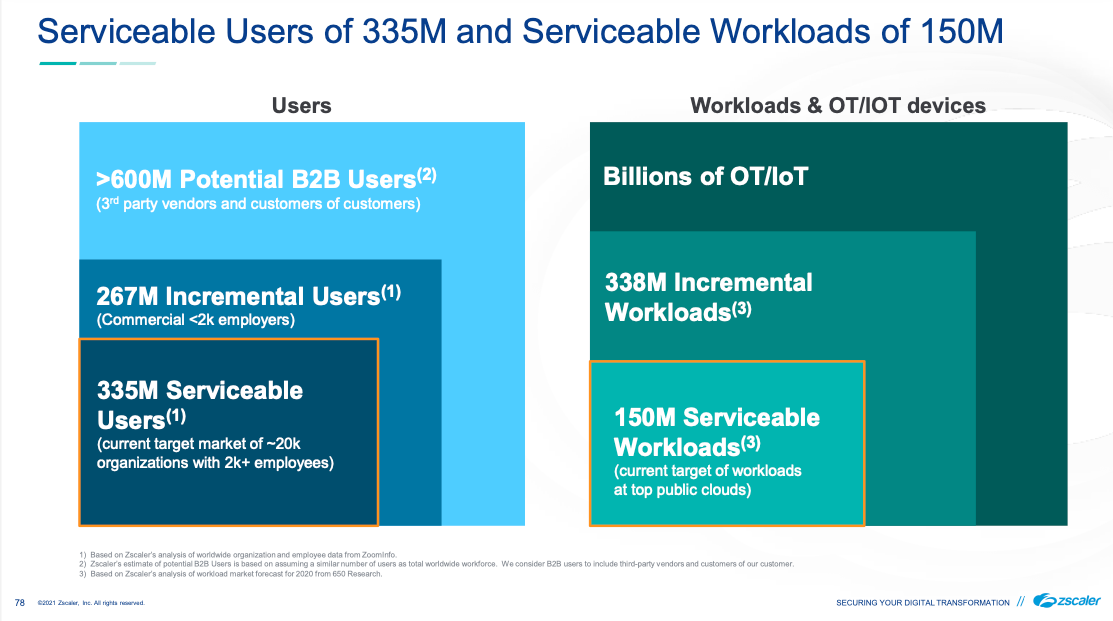
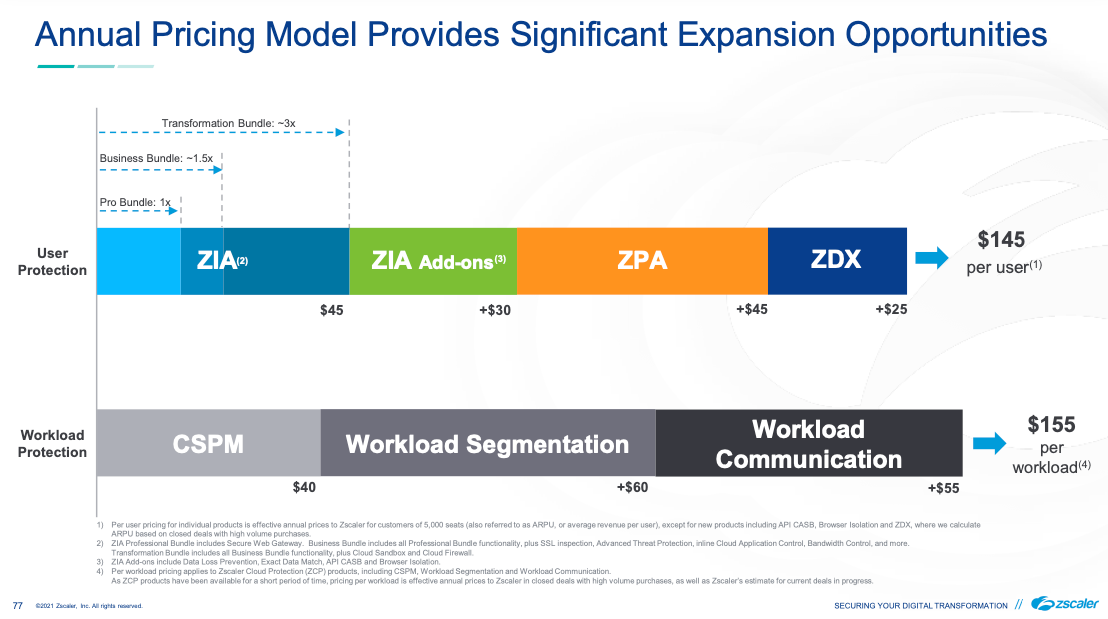
Land and Expand is the name of the game. They expect that the incremental gains will increase the ARPU/ARPW (avg price per workload) from here. Their investor day slides helpfully gave us some idea of what pricing is like, since it isn't clear on their website.
Key Staff
CEO Jay Chaudhry has been a serial entrepreneur around security, and started Zscaler in 2007 after his last company was acquired by Motorola. He struck gold with this idea, as Zscaler has turned into the trailblazer and top leader in SWG, and subsequently in Zero Trust. Glassdoor rates this company a 4.6 of 5, while the CEO gets 98% approval, and is #71 their "100 Top CEOs of 2021".
Zscaler's CTO had previously been CTO for Jay's earlier acquired company, then Motorola's networking division, but eventually followed Jay to Zscaler in 2011. He has overseen and built a very impressive architecture, and proved himself very forward thinking in designing their stack within a distributed edge network architecture. Not many took that path, and those that have tend to stand out in today's crowded landscape of globally distributed apps and users. (Hi, Cloudflare.)
After the enormous hiccup in sales execution in 2019, the CEO quickly recognized the issue, and set to find a new sales leader that could scale Zscaler operationally the same way the platform itself could. In Sep-19, they hired a new CRO & President of GTM from Cisco/AppDynamics. This was clearly a good choice, seeing the rebound in the sales performance after the team was reorganized and refocused over the next few quarters. Then COVID hit, thrusting the importance of Zscaler's core offerings back into corporate consciousness.
In marketing, they never seemed to find a good fit. After an early CMO was hired in Feb-16, they hired a new CMO in Oct-18. I was... not impressed at all. Throughout owning Zscaler across 2019 and 2020, their marketing was a jumbled mess. I understood the company through my research of their product lines and architecture, and even I could not make heads or tales of what they were spinning on their product pages. So while COVID was a huge tailwind, it seemed unfortunate that interested parties likely had difficulty in understanding the company's solutions.
I’m not one to dog on companies, but I cannot believe how bad Zscaler $ZS is at marketing. Is this understandable in any way?
— muji @ hhhypergrowth (@hhhypergrowth) November 17, 2020
The only thing made clear by this graphic is that it was drawn by a person who really likes the circle and cloud shapes in their flow chart app. pic.twitter.com/VG3QHdeG42
Luckily, they again recognized that there was an issue, and hired their current CMO in Nov-20, formerly of HP/Aruba, Nutanix and Cisco – having a much more ideal background (unlike his predecessors) of having worked in networking security companies that sell to large enterprises. The web site marketing is now so much better (so much clearer, so much cleaner), after drastically improving it all some time just before ZenithLive 2021 in June. Unfortunately, the iconography in their technical drawings still hasn't improved – they need to take a serious cue from Cloudflare on this, and hire specific talent to make their diagrams have more clarity and a whole lot better quality. For now, the technical drawings continue to look like they were designed by engineers in a flowchart program. But the marketing – soooo much improved.
As for staff, they have 8 R&D/Engineering centers (mostly US and India) and 15 sales offices around the globe.
Platform
Let's run through their core feature set (that I first explored in Oct-19), through all the product announcments since, including from the recent ZenithLive events in Dec-20 and Jun-21.
Zscaler stands for the "zenith of scalability". They provide an enormous edge-based security cloud spanning the globe, distributed across 150 POPs in order to be as near to the users, apps, and network locations as possible. At its core is the Zero Trust Exchange (ZTE), which, per their latest stats, handles a massive 200B+ requests a day, flagging 7B+ security incidents or policy violations, and blocking 80M+ threats. ZTE sits across each of those interconnected 150 POPs, as well as has colocations with major cloud providers (AWS, Azure, GCP) and major enterprise SaaS applications (like Microsoft Office 365, Salesforce, and Slack) to improve its performance in interconnecting with those services. In their Investment Day presentation in Jan-21, they claimed to have >20M licensed seats, with their platform handling 2.0PB of monthly traffic to Office 365 alone. [Please note that every mention of ZTE going forward means their entire globe spanning edge network.]
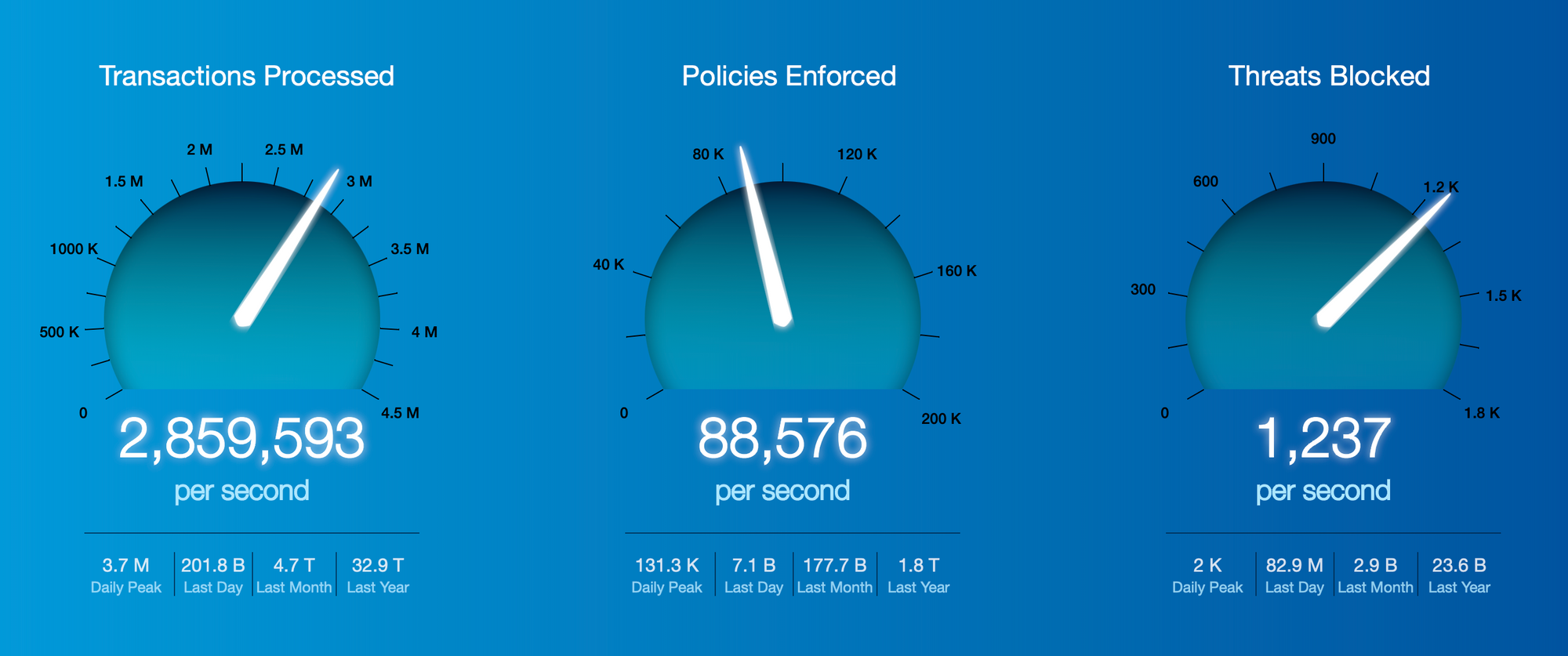
Their current marketing message is that their platform helps reduce the cost and complexity of networking & security by eliminating the networking hardware needed. It also helps deliver a better user experience, by reducing the latency between the points of traffic and allowing end-to-end monitoring over every step in the path. But most of all, it provides better security, by utilizing Zero Trust across its entirety (which, as you assuredly remember, prevents lateral movement and privilege escalation), with the extra bonus of helping companies to minimize their attack surface by greatly reducing the services & servers that are exposed to the public internet.
Their marketing sells this as:
- Modernizing Workplace Enablement: Reduce the need for leaky VPNs, while still centralizing policy and access mgmt regardless of location of the user or app. It also helps integrate 3rd party access, or expansions thru M&A.
- Infrastructure Modernization: Reduce the need to maintain all this networking and security yourself, and for greatly reducing costs by minimizing the IT staff and networking hardware needed to interconnect your enterprise, not to mention the security experitise that must be continually maintained. Modern enterprises use a huge number of SaaS services to run their operations, and you can no longer maintain a WAN perimeter.
- Security Transformation: Migrate your enterprise security into Zero Trust, and leveraging their global edge network to reduce risk, reduce costs and complexity, and have complete vision over your secure enterprise network.
Essentially, the ZTE is now a globe spanning switchboard that helps interconnect users and apps in a secure and low-latency way. In its core, in sitting as a proxy between users and the apps they utilize, is full SSL inspection, DNS control and protection, bandwidth control, and Intrusion Protection System (IPS) and Advanced Threat Protection features (for breach and malware detection). Beyond that, the core is using a variety of ML/AI features around security, as well as using it for improving the customer's ability to oversee and manage across all of their sprawl of apps, devices, and users.
A recent acquisition of Smokescreen in May-21 will add an interesting capability to the platform. Smokescreen's technology allows blanketing your network with decoys (known in the biz as "honey pots") in order to catch bad actors, as a way to test that network's resiliency of its app security and restrictions around lateral movement. This includes creating decoys at all levels, such as network (server decoys), endpoint (decoy files, credentials, and processes), identity (fake users), cloud (web servers, databases) and email. Once an attack is caught, it can help automate the forensics and root cause analysis, and can automate and orchestrate these actions by intergrating with external SIEMs, SOARs, firewalls, EDRs (endpoint protection), and outside threat feeds. This is quite unique a capability for Zero Trust & SASE platforms. Ultimately this allows for a more proactive approach in catching unknown threats and attack vectors, instead of solely relying on ML/AI to cast a net to catch these.
CEO, in Q420 CC - "Our platform is purpose-built for the cloud. It is designed to be extensible to integrate with our targeted acquisitions, as well as with third-party products. Legacy network security vendors can't create a cloud platform by cobbling together a bunch of acquired companies. History has shown that this approach does not work."
They are not strangers to using acquistions to bolt on new features, especially the cloud-based ones that help manage and protect cloud infrastructure. But their focus is on how their underlying architecture provides the vital difference in Zero Trust and SASE, in how their edge-based platform helps provide a better security and better user experience across the globe – all at a lower cost and complexity.
Outside of the platform and the product lines below, the primary software of theirs is the Zscaler Client Connector, the agent that sits upon across all users' devices. It serves as the agent for all their edge-delivered features (ZIA, ZPA, ZDX, Browser Isolation), and can run on workstations and laptops (Windows, Mac, and Linux) as well as mobile devices (iOS and Android).
They also allow cloud-to-cloud log streaming, by allowing customers to feed ZTE's logs into cloud file storage systems like AWS S3 or Azure Blobs for outside analysis, as well as allowing customers to stream log data into SIEM platforms like Splunk and Sumo Logic (via their ingest APIs). I expect them to further tie logging into their endpoint protection partners (that are veering into XDR) from here as well, like CrowdStrike and SentinelOne.
Core Products
The core platform started as a combination of a Secure Web Gateway to secure SaaS access (with a host of protection features), then added on Zero Trust to secure internal app access. It has since expanded into better observability and monitoring of the usage, and improving its browser isolation and DLP features.
In Sept-20 they announced several new cloud features, that, at their ZenithLive 2020 event in Dec-20, announced into the full Zscaler Cloud Protection (ZCP) platform. This pivots Zscaler from user-to-app to app-to-app protection, but also now firmly plants them as a SASE provider.
Zscaler Internet Access (ZIA)
Zscaler Internet Access (ZIA) is for protecting users that are accessing external SaaS applications. At its core, it acts as a SWG to control all user access, but also has a wide variety of ancillary features available that all tie together closely. Users utilized the Zscaler Connector client (agent on each device) which then connects their network into the ZTE platform, through a ZIA Public Service Edge (specialized intermediary service deployed per customer).
- Secure Web Gateway (SWG) = Provide firewall capabilities to secure outgoing user traffic to SaaS apps, and scan for malware or other attack vectors.
- Cloud Access Security Broker (Inline CASB), aka CASB in real-time mode = Sits as inline proxy over cloud application usage, to manage and monitor access to cloud apps in real-time. Can isolate unsanctioned apps being utilized (what is known as "Shadow IT"), and can allow blocking or alerting when found.
- SaaS-Integrated CASB (Out-of-band CASB), aka CASB in scanning mode = Integrate with external SaaS apps and services (via their APIs), in order to provide more integrated security features over access and user rights within the app, as well as provide malware and DLP features directly within those apps. They mentioned during ZenithLive 2021 that over 8000 cloud apps are supported, and they are constantly adding new ones.
- Cloud Data Loss Protection (DLP) = Provides integrated features with SaaS tools to provide data protection features. Integrates with the SWG & inline CASB features to allow scanning data in realtime for recognized signatures around compliance and regulations (like PCI or HIPAA). Also integrates with the out-of-band CASB (talking to services via API) to allow scanning of existing data in SaaS tools, including interfacing with raw storage (like AWS S3 and Azure Blobs), file drops (like Dropbox and Box), collab tools (like Slack and Office), source code repos (like Github), or CRM tools (like Salesforce).
- Cloud Sandbox = Provides a temporary secure location (sandbox) to test any unknown incoming file for detected malware.
- Cloud Browser Isolation = As we've been discussing recently with Cloudflare [premium], they too provide an edge-based sandbox for safer web browsing. It is from their Appsulate acquisition in May-19, and it just went GA in Apr-21. It seems very similar to Cloudflare's setup, where a browser service runs as a temporary instance in the edge to safely handle any web page data, before it sends a sanitized final version to the end user. It ties into the existing Zscaler Connector app that ZIA already uses, and is compatible with any browser or web app without special configuration.
Pricing is per-user, based on tiers. Pro Edition is basic ZIA, Business Edition adds in SSL Inspection, Adv Threat Protection, DLP, inline CASB, and SIEM logging, and Transformation Edition adds Cloud Firewall and Cloud Sandbox. Add-ons including DLP, out-of-band CASB, and Browser Isolation.
Sandbox, DLP and Browser Isolation all received heavy mention at their latest ZenithLive 2021 in Jun-21, and are areas they continue to shine. With Sandbox, they have recently improved the APIs over it to allow tighter integration with partners, for improving cross-coordination and automating remediation. As an example, a customer could hook up sandbox features within both CrowdStrike and Zscaler, so when CrowdStrike saw a file it didn't like, it could ask Zscaler to double check it. If Zscaler also marked it bad, it could reach back into CrowdStrike and tell it to take immediate action, or trigger an event in a SOAR service. CrowdStrike, in turn, could assure that bad file doesn't exist on any other devices.
With DLP, they demo'd their features available in both their inline and out-of-band CASBs. The app types covered by out-of-band included Public Cloud Storage, File Sharing, IT Service Mgmt, Source Code Repos, Email, Collaboration, and CRM tools, and direct mentions of AWS S3, Azure Blog, Dropbox, Box, Google Drive, Gmail, Exchange, Salesforce, Microsoft Teams, ServiceNow, Sharepoint, and Github. The DLP features contains compliancy templates to identity types of data, such as around PCI, financial statements, PII, HIPAA, and GDPR. Last year they added a feature called "Exact Data Match", to scan files/data to identify and tag which have these signatures. It can detect data signatures on the fly (inline), or can schedule scans of files/data in outside SaaS services (out-of-band). This year they added a new "Indexed Document Matching" feature to allow admins to tag specific files/data into certain policy rules themselves. Either way, once a file/data is tagged, the system can apply the customer's policies on who can access it (based on app, role, user, device, or other context), as well as set rules around time of day or bandwidth allowed (as in, don't let Randy download all 200 gigs of your Dropbox files over the weekend).
And going further, they are tying these same DLP capabilities into Browser Isolation. They believe that the Browser Isolation features enhances a customer's Zero Trust posture around 3 areas:
- Threat isolation (stop web attacks): This being the entire point of Browser Isolation, as it creates an airgapped copy of the browser in the edge while the user only gets a safe copy of it in the local browser (free of any malware or detected threat).
- Employee isolation (better isolate high value or high risk users): You can isolate high value users like C-suite or HR staff to always utilize Browser Isolation when accessing apps via ZIA, to assure they are better protected, or for higher risk users (say, a security employee that has to scan the dark web regularly).
- Data isolation (protect data): They have also integrated DLP features into Browser Isolation, to allow admins to restrict a users ability to download or copy data from the underlying website being viewed. You could require Browser Isolation for certain apps, to help protect sensitive data from being copied and transferred out.
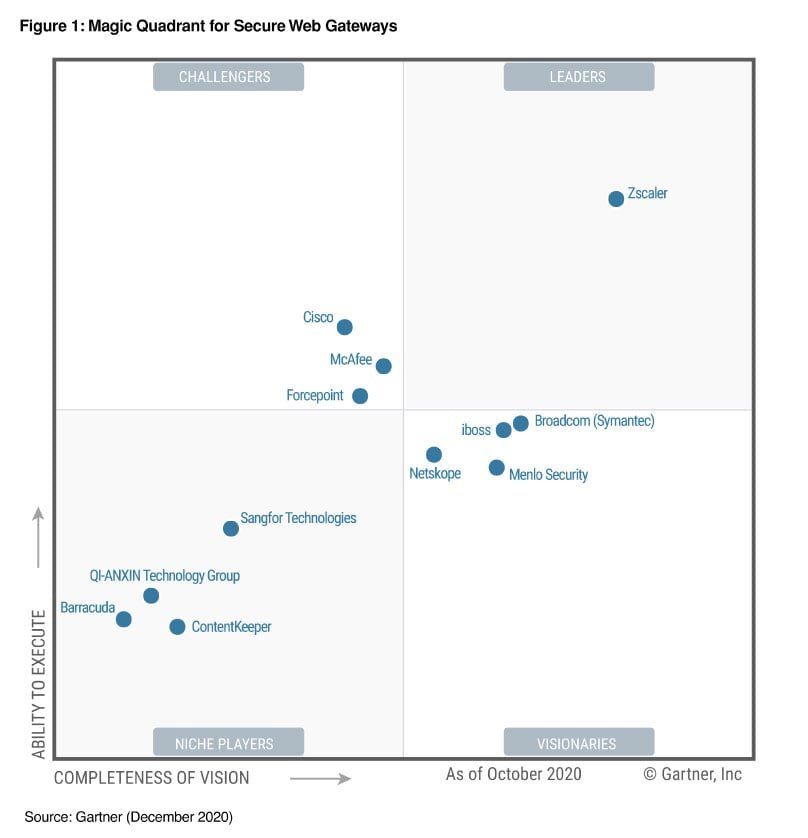
Even before these new DLP and Browser Isolation features, Zscaler was far and away the leader in SWG, as shown in Gartner's latest Magic Quadrant for SWG from Oct-20. [Netskope is the only other company I watch, expected to IPO at some point soon. You may remember them from Okta and CrowdStrike's partnership in Jun-20. Palo Alto and Cloudflare aren't showing up yet, but are likely to be in the next one.]
Zscaler Private Access (ZPA)
Zscaler Private Access (ZPA) is for protecting internal applications by managing user access via Zero Trust. It can be used standalone, but obviously pairs very nicely with ZIA, in order to cover both traffic to external SaaS apps as well as traffic to internal apps. This allows enterprises to control and secure all user access to internally hosted applications, regardless of the user's or the app's location. It works via app segmentation, to dynamically create an ephemeral network connection between the two, once the user is approved in Zero Trust polices. Users are never allowed on the network, and internal apps remain completely invisible to the outside internet. Via Zero Trust, admins can control app access by user, role, device, location, or any other context. It again ties into many of the security features above, and logs can be streamed to outside storage or SIEMs.
It is frictionless for customers to expand from ZIA to ZPA, as users utilize the same Zscaler Connector client (agent on each device) which then connects their network into the ZTE platform. From there, though, the setup changes. ZPA requires the ZPA Public Service Edge (specialized intermediary service deployed per customer) to handle the app access ZTE, which then talks to a locally hosted service, called an App Connector, installed as a lightweight VM within any cloud or on-prem location where the app is hosted. The App Connector can be deployed easily into cloud environment (AWS, Azure, or GCP) or any Linux host or hypervisor environment (VMware or Microsoft Hyper-V).
The capabilities here have expanded recently. In Apr-21, they announced a new ZPA Private Service Edge feature. Think of it as ZPA, but entirely on-prem (not just the app on-prem, but the users too). This allows putting the ZTE's feature set directly into your on-premise data center, which allows for local users to be able to access local apps directly, without the use of the public internet to reach ZTE. This helps customers having a hybrid setup around data centers, or that have a high level of security restrictions. It keeps the user access control and policies overall in one centralized platform (ZTE), but for a certain subset of users, allows accessing a locally hosted app directly, interconnecting without any internet exposure at all (or any added latency to the nearest edge POP).
Beyond ZPA for your internal workforce to access internal applications, they also offer a ZPA B2B feature, which allows customers to share their internal applications with external users, such as partners, customers, or suppliers. This allows for creating privately sharable apps, and, to me, is a major selling point of ZPA over other Zero Trust platforms (which is not mentioned enough in customer events or focused on in marketing, I feel). It supports multiple identity providers, and helps eliminate the overhead of having to manage external app access directly – if a supplier's employee leaves, they will be severed from access once they are disabled in that supplier's identity provider.
In addition, they expanded the Browser Isolation features for ZIA to now be fully available within ZPA. This means that you can use Browser Isolation over internal apps. But why? Your internal apps hopefully don't have malware and threats! Because this allows customers to be able to apply the integrated DLP features within Browser Isolation over their internal applications. As an example, if you allow Zero Trust access to an internal application to external users, because you cannot manage or know the state of their devices, you might require they use Browser Isolation for the added protection over files they are submitting, plus prevent them from downloading or copying the data exposed within that app via a DLP policy.
Pricing is per-user, again based on those same tiers. Pro Edition is basic ZPA for a limited number of apps. Business Edition provides full ZPA for an expanded number of apps, and two Private Edges. Transformation Edition adds in ZPA B2B, as well unlimited apps and greater number of Private Edges. Browser Isolation is a new add-on.
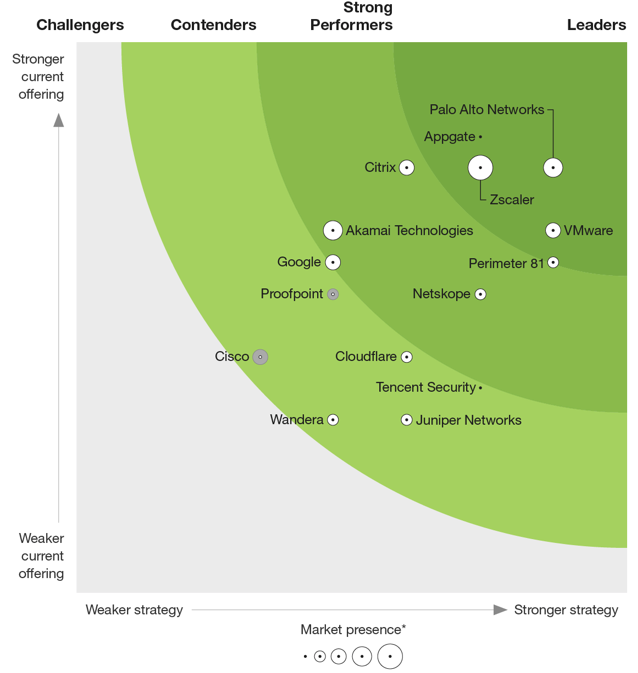
The Forrester ratings for ZTNA came out in Aug-21, and shows Zscaler ZPA as a the largest leader in the place (noting that Palo Alto & VMware being reported as ahead of them in strategy – which seems to completely ignore the Workload Segmentation I am about to discuss).
Zscaler Digital Experience
They expanded their platform with Zscaler Digital Experience (ZDX), announced in Nov-19. It provides visibility and introspection features to allow enterprises to triage issues impacting their users while using this platform.
This allows customers to proactively measure and benchmark the digital experience of every user across the platform. It again is handled by the Zscaler Client Connector, so is a very frictionless product addition for any ZIA or ZPA customer. The agent helps proactively monitor every user device within the organization for any user experience issues, tracking telemetry data about the traffic as well as real-time device health info (CPU use, memory use, processes running). [Which is starting to border very closely to EDR, and EPP wouldn't be a difficult move with their existing "beach front access" with their installed agent combined with their existing malware & threat protection features in ZIA... but CrowdStrike remains a vital partner at the moment, so not sure this is on the horizon.]
Some of the monitoring is handled on ZTE's side as well, which performs synthethic probing to SaaS or internal apps to probe every app's reliability and response times. In the end, the customer ends up with a dashboard over all usage, graded into High/Okay/Low performance across all users, apps, and global locations. They can triage performance issues, in order to pinpoint where the issues lie, such as if the issue in the local network, the device, an ISP, or Zscaler itself, and can even view network metrics down to the specific hop.
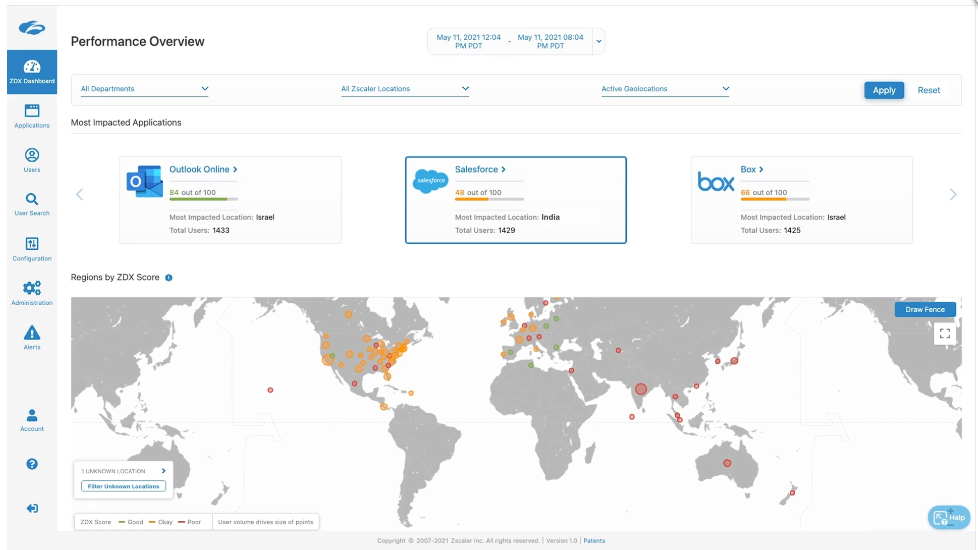
This provides one giant Observability platform over the global usage across this platform. Admins can monitor data centers, key SaaS apps, and SLA thresholds. Because it has device health, it can triage device issues as well, such as identifying issues with a specific OS or browser version. I have to wonder if this product will tie into Observability platforms ultimately (already part of the security logging into a SIEM), in order to allow overlaying all these app access logs over APM and infrastructure monitoring. It could be especially helpful when combined with Real User Monitoring, for instance, which traces a user's access through distributed services. Part of that journey is through the Zero Trust platform (and even through the Workload Segmentation discussed below), where ZDX could be tracing it. DevOps teams could potentially correlate the traces between RUM and ZDX for a full end-to-end view of the entire networking path a user's request takes
Zscaler Cloud Protection (ZCP)
All of that provides a massive Zero Trust platform for managing user access to apps (user-to-app), which, by itself, is a massive success. But Zscaler is just getting started. It finally came time for their moves into leveraging their platform into other Zero Trust directions beyond user-to-app. The first hint was when they acquired Cloudneeti CSPM in Apr-20, and released it to GA in Sep-20, but this was just the tip of the iceberg as for what was to come.
Zscaler Cloud Protection (ZCP) was announced in Dec-20 during Zenith Live 2020. ZCP is sold as protecting cloud workloads across any cloud environment – but also secures between those cloud environments as well, plus helps interconnect them. It consisted of several products that combine into providing cloud workload protection (over both the resources and the traffic between them) PLUS provides the underpinnings of a true SASE platform.
Cloud protection is an area that CrowdStrike is moving into, with its Falcon for AWS/Azure/GCP and the Falcon Horizon CSPM, but I see the two companies as having different pivot focuses right now. For CrowdStrike, they are pivoting into protecting the cloud resources, as they do the endpoint. For Zscaler, they are pivoting into protecting the workload traffic, as they do the user traffic. I expect more cooperation between their products, instead of competition, especially as Zscaler is entering SASE and new forms of Zero Trust, both of which rely heavily on device posture and added threat intel capabilities provided in Falcon. In fact, the only overlap right now in their product lines seems to be with CSPM.
Pricing on these new features is per-workload, with each service sold separately.
Zscaler Workload Posture
The Zscaler Workload Posture is actually 2 products in one. It started with the CSPM acquired from Cloudneeti that was released in Sep-20, but has since integrated with a CIEM after the acquisition of TrustDome recently in Apr-21. These two features pair together nicely – managing both the infrastructure configuration, as well as the authorizations that users have over it. [Not normally a fan of acquistions into existing security platforms, but I don't mind these types of self-contained SaaS solutions getting added in, as it gives them a much faster pace to market, and adds in a pool of developers with expertise. These clearly fit into the bigger picture.]
- Cloud Security Posture Mgmt (CSPM) = Cloud-based service that provides hygiene scanning of cloud resources. Allows customers to assure that cloud resources they are creating have proper configurations (across authentication, data encryption, and internet connectivity settings), for a strong compliance and security posture. It allows for scanning your cloud resources quickly, and provides a dashboard where you can filter by cloud, account, region, resource type, or detected risk levels. Zscaler's has 2500+ built in signatures to check configurations against known cloud security best practices as well as specific compliance policies for laws or regulations (HIPAA, GDPR, etc), that customers can customize as needed. It scores each resource on a risk matrix based on ISO 27005 standard of Risk Impact (Critical to Very Low) and Risk Likelihood (Certain to Not Likely). It also comes with 16 standard compliance frameworks to track security posture across your cloud workloads, and some automated remediation features as well. These features are akin to CrowdStrike Horizon from their close partner (and loads of other CSPMs are cropping up in other security platforms, with Palo Alto, Datadog, Splunk, and others all having it now too). But unlike those, Zscaler's not only continuously monitors and helps to remediate app misconfigurations and spotted vulnerabilities in cloud infrastructure (like containers and VMs), but also across heavily utilized enterprise SaaS apps (like Microsoft Office 365 and Salesforce). [I believe it ties into the out-of-band CASB integrations with SaaS apps that they already have built, to be able to use the APIs of these SaaS apps to check configurations.]
- Cloud Infrastructure Entitlement Mgmt (CIEM) = Cloud-based service that manages and oversees the access and rights that users have in those same cloud resources. It scans all human-based users, as well as machine-based ones (service accounts) used by VMs, APIs, apps and serverless functions. Like CSPM, it assesses the risk of these users, and continuously monitors cloud resources for anomalous behaviors (asking for resources you don't have right to) and misconfigurations (setting lax admin rights). This is great for finding unnecessary or elevated rights, to assure you are enforcing least privilege access required by Zero Trust. It provides a graph view to see how rights flow through roles/identities/policies/resources, for easier triage and tracking, and can provide automated remediation to block access or remove any misconfigurations.
These features combine to ultimately help discover and eliminate most common causes of data breaches and compliance violations. Gartner states 99% of cloud attacks come from misconfigurations, and predicts that adopting CSPM can reduce security incidents by 80% thru 2024. These features are the ones most likely to overlap with CrowdStrike, and given their focus on identity security right now (via their Preempt acquisition, whose product sits over identity stores), I expect to see CrowdStrike also introduce a CIAM product as well.
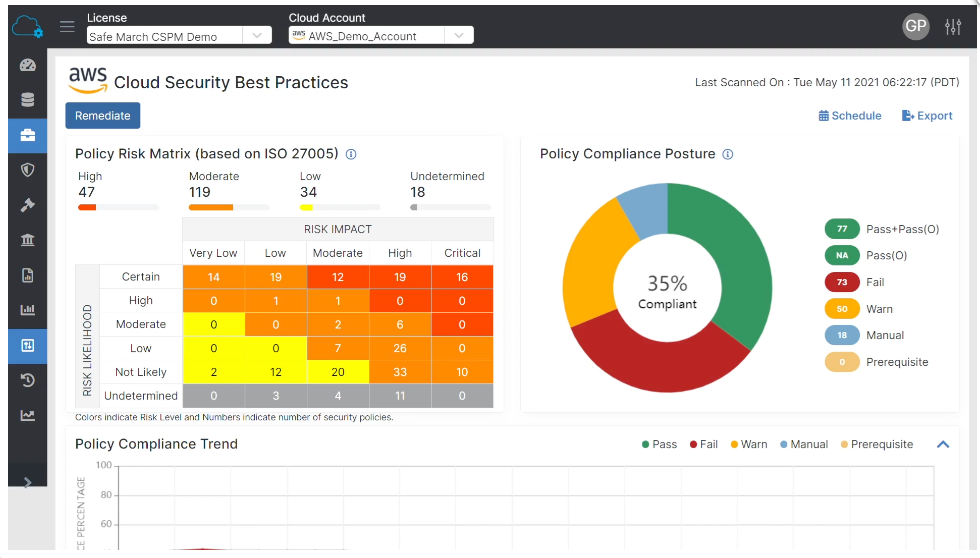
Beyond that, they are tying the out-of-band DLP features in ZIA (that tie into SaaS services and apps via API, to search over data at rest) into the Workload Protection product. They focused on this heavily in ZenithLive 2021, showing how to use Workload Protection for doing DLP scanning of files in cloud storage services like AWS S3. This ties in nicely with CSPM and CIAM (which scan cloud resources for misconfigurations and access rights), for customers to be able to set up a file scanner to identify sensitive data for compliance policies.
Zscaler Workload Segmentation
We could also see this feature coming, when in May-20, they acquired Edgewise Networks. This provides a new direction to Zero Trust [as previously mentioned in my "What are Zero Trusts?" piece], as Zscaler is now pivoting its Zero Trust from human-to-app to app-to-app (or machine-to-machine). This product secures application-to-application communications across public clouds and data centers that are connected to ZTE (Zscaler's platform).
Zscaler Workload Segmentation (ZWS) utilizes AI/ML to discover all the applications deployed across ZTE, to map out the internal applications being hosted across the enterprise. It can isolate unsanctioned apps (Shadow IT), and enforce only allowing legitimate (approved) apps. It then maps out the usage patterns between all those services, in order to create and enforce Zero Trust communication between all those services. As new cloud resources (containerized services or serverless functions) get spun up, they join the mix.
Basically, instead of mapping your entire service map out yourself via policy rules, this system scans your internal networking traffic between services, and figures out the normal traffic patterns for you. It then creates Zero Trust policies for all the different types of intercommunication between services. This is for any type of system or service that "talks" across your enterprise, between APIs, apps, file stores, databases, identity stores, IoT devices, and more.
Workload Segmentation is a new way to segment application workloads. With one click, you can enhance security by allowing workload segmentation to reveal risk and apply identity-based protection to your workloads—without any changes to the network. The workload segmentation identity-based technology provides gap-free protection with policies that automatically adapt to environmental changes. Eliminating your network attack surface has never been simpler.
Every service is fingerprinted and tracked, and maps it to the identity (service acct) that that service uses across its requests to every other service. From a blog post on the product, they dive further into how they are using identity-based microsegmentation (Zero Trust's fancier name) over workload interconnections.
Zscaler Workload Segmentation begins by mapping the application communication topology using ML, a process that takes about 72 hours (a huge improvement over the months it takes to perform manually). Once complete, we can measure the total network paths available and the application paths that are actually required by the business applications. Typically, only a fraction of pathways is required. We can eliminate all unnecessary communications paths to reduce the attack surface—typically, our ML algorithm can shrink the number of paths by about 90 percent, while ensuring full coverage of the environment.
... Zscaler verifies the identities of communicating software in real time. This zero trust approach prevents unapproved and malicious software from communicating. Piggybacking attacks using approved firewall rules become a thing of the past. Identity is the secret to achieving simpler operations and delivering stronger protection compared to traditional network security controls.
Because the identities of communicating software are so specific, Zscaler simplifies the number of policies required to protect a segment. ... And because segmentation policies are built using software identity, even if the underlying network changes, policies don’t break. If the system can’t verify the unique identity of what’s trying to communicate, no communication occurs.
All this boils down to the exact same thing Zero Trust has been used for with users – create ephemeral connections for authorized requests, in order to eliminate public exposure & lateral movement. It is pivoting its Zero Trust capabilities from user-based (user-to-app requests) to also be system-based (app-to-app requests). This opens up an entire new market to Zscaler, and provides an entirely new way to scale up the platform usage.
And that's not the only major exciting pivot.
Zscaler Workload Communications (let's just call it SASE)
Zscaler has been talking about SASE since 2019, including having several partnerships with SD-WAN companies over the years, but has never shown us a product to allow them to become the interconnective fabric between all the network locations an enterprise might have across the globe. Thus far, they have only concentrated on using SD-WAN to interconnect to the traffic over from user requests.
However, in ZCP, they now have a product for interconnecting disparate networks directly to the ZTE edge, called Zscaler Workload Communications. Just as their Zscaler Connector connects user devices to the ZTE, and App Connector connects the internal apps to the ZTE, now their new Cloud Connector connects disparate network locations to the ZTE. This is the first product that actually moves Zscaler into being the unified control plane for an enterprise network, and firmly into being a SASE. It is being marketed as allowing enterprises to reduce the cost and complexity of any direct connections o their platform.
"Establish fast and secure cloud connectivity without the cost and complexity of network security appliances. Built on top of the Zscaler Zero Trust Exchange, Cloud Connector provides secure internet access and zero trust connectivity between cloud applications."
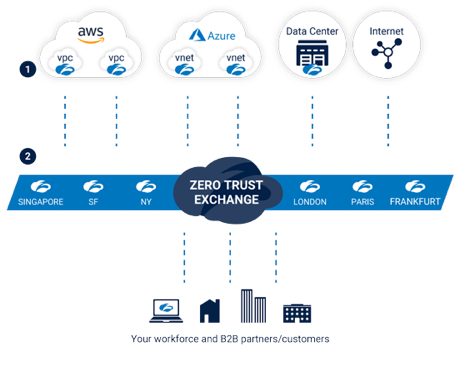
Cloud Connector is a service instance that sits inside a public cloud, private cloud (AWS VPC or Azure VNET), or on any on-prem hypervisor (VMware), and provides a direct link from that network to ZTE, via the closest POP. It allows customers to direct connect to the cloud from any location, which means it can now be the backbone for any cloud-to-anywhere communications. Zscaler focused most on cloud-to-internet (such as calling SaaS services from cloud workload), cloud-to-cloud across cloud vendors, regions and zones (such as service in AWS VPC calling a service in Azure VNET), and cloud-to-data center (calling internal API from a cloud workload).
This finally gets Zscaler into SASE, and opens up the door to all the other features that can combine with it as a total cloud network security package. Workload Segmentation pairs extremely well with Workload Communications. With that, you can control all the app-to-app communications across all your cloud and on-prem environments via Zero Trust, but when each of the separate locations of those services are interconnected directly to ZTE, you further minimize the exposed attack surface. Then add in external partner access, where, with ZPA B2B, you can secure and control private networks across partners for direct API-to-API communications without any public internet exposure, as you can again interconnect the various locations directly to ZTE via SASE. You can tightly control all access through Zero Trust across an entirely private network. With all the network traffic going through ZTE, it means all the other features, like SSL inspection, IDS, advanced threat detection, bandwidth control, DNS protection, and DLP can be utilized for all network traffic, not just user-to-app requests – whether or not the Workload Segementation is used.
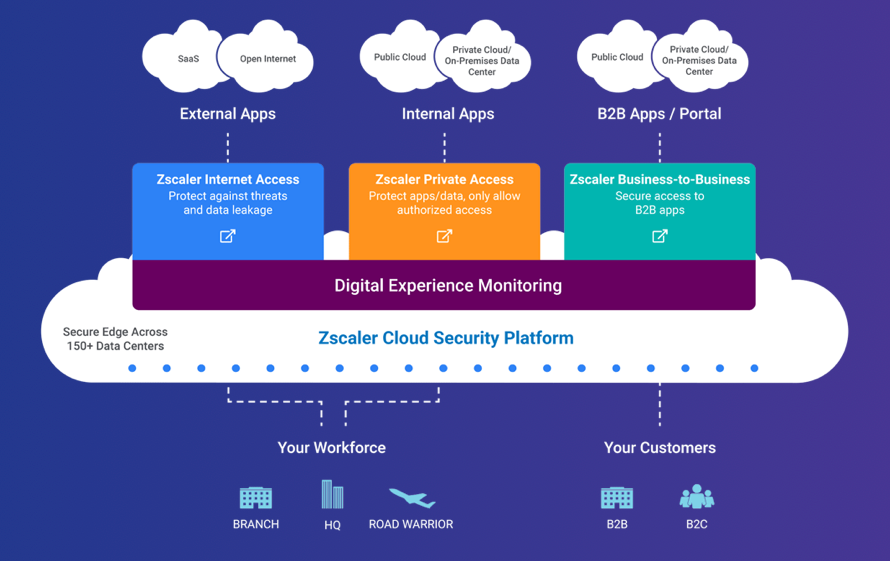
What I like about this is that it begins to greatly simplify how much effort the customer has in order to interconnect their various networks with Zscaler's platform. Getting new customers and new network locations on board their platform has always required a lot of interconnection work, typically involving system integrators (SI) and system providers (SP aka telco) partners. The one knock I've had with Zscaler (from my first Nov-19 piece) is the difficulty in getting new customers onboard.
Zscaler appears difficult to implement, at least for companies going "all-in". They have a heavy reliance on System Integration partners, like Deloitte, Accenture, Cognizant, and Infosys, and on system network partners like AT&T, Sprint, Verizon, BT, and Tata . My initial understanding of Zscaler was that it could be bolted onto existing WAN network setups for initial projects (like Office365 protection) and worm their way into more from there (land-and-expand), but they have been saying that upfront deals are larger now. Larger deals require a longer timeframe due to the complexity to plan and set up (hence the integration partners). ... Hopefully they start to focus on some self-install capabilities for certain marketing angles (to allow customer to be more nimble, and putting Zscaler back into "land-and-expand"), while still working on the "all-in" larger deals of the bigger enterprises.
They are making improvements here, and I believe this SASE product is just the start. Going farther on the simplification front, they mentioned in ZenithLive 2021 that they are now allowing customers to self-provision their GRE tunnels (like Cloudflare allows with the Cloudflare Tunnel) instead of having to involve SI/SP partners to hook it up, including being able to tie into Zscaler's API to automate provisioning. In this age of ephemeral cloud workloads, I want to see more and more steps like this, that allow customers to more easily connect their disparate locations and devices to ZTE's edge. Zscaler seems to be missing a self-provisioned interconnect capability, like Cloudflare has with its Cloudflare Network Interconnect (CNI). Beyond that, Zscaler needs to allow its customers to tie in more closely via Infrastructure-as-code systems (like HashiCorp Terraform) to better automate provisioning of their SASE and Workload Segmentation features, Zero Trust Policies, and other features like ZIA, ZPA, and ZDX. I also forsee them needing to tie into PAM and ephemeral credential tracking systems like HashiCorp Vault to better protect system credentials for service accounts.
Partners
Zscaler has a wide variety of large partners, and likes to celebrate the many successes they've had. Back at ZenithLive 2018, they had talks from Microsoft CEO Satya Nadella, VMware CEO Pat Gelsinger, Dell CEO Michael Dell, and Salesforce EVP of Platform. Not too shabby a line up. After announcing their Partner Awards at ZenithLive 2019, in Feb-20, they finally set up their Summit Partner Program. They just announced a new set of partner awards at ZenithLive 2021 in Jun-21, as well as introduced new certification programs for partners to include Associate, Sales Pro and Sales Engineer training. [Yes, these awards are a lot of back patting between partnering companies, but it shows you who they rely on, and does sometimes include some nuggets, such as how last year Verizon helped them secure 2 of their 5 largest ZIA lands.]
They maintain partnerships with (links to partnership white papers):
- Cloud vendors, including AWS, Azure, and GCP
- Cloud services, including Microsoft Office 365, Zoom, Box, GotoMeeting, RingCentral, Dropbox, ServiceNow, and Slack
- Global and Regional Service Providers (telcos), including AT&T, Sprint, T-Mobile, Tata, BT, and Verizon
- Identity providers, including Okta, PingID, and Microsoft Azure Active Directory.
- Endpoint protection platforms (EPP), including CrowdStrike, Sentinel One, Microsoft Defender for Endpoint, and VMware/Carbon Black.
- SD-WAN providers (many of which were later swept up in acquistions by networking firms), like VMware, HP/Aruba, HP/Silver Peak, Aryaka, Citrix, Cisco/Viptela, Cradlepoint, Oracle/Talari, Palo Alto/Cloudgenix, Nokia/Nuage, Riverbed and Azure Virtual WAN.
As you can see, a lot of Microsoft and VMware up there. Let's focus on a few of the deeper ones, specifically..
CrowdStrike Partnership
Zscaler and CrowdStrike combine for a potent combination, to protect the user traffic via Zscaler, and the user device with CrowdStrike. Some of it is overlapping (such as malware detection from web apps), but they combine into those "layers of the onion" to protect both the device, and the traffic to and from it. They initially started a partnership with CrowdStrike in Sep-19, and in Mar-21, greatly expanded it, announcing deeper integrations between their platforms, and cross-coordinated GTM campaigns. Zscaler was the first partner that CrowdStrike added under its Zero Trust Assessment (ZTA) integration.
- Zscaler ZPA integrates w/ CrowdStrike ZTA for adding device posture rules to Zero Trust policies
- Zscaler ZIA can trigger device quarantine in CrowdStrike Falcon EDR
- Falcon X threat intel data and Falcon EPP device data is now shared w/ Zscalers ZTE
- Developing deeper cross-platform workflows
Both companies greatly talked up this partnership, including on earnings calls, and in May-21, they both co-hosted a shared Beyond the Perimeter event to showcase these combined platform features. Later in Jun-21, in Zscaler's 2021 Partner Awards, they awarded CrowdStrike with their GTM Tech Partner of the Year. In Oct-21, they announced that they further deepened their deeply integrated partnership, with Zscaler becoming a launch partner in CrowdStrike's new XDR Alliance.
Microsoft Partnership
Microsoft and Zscaler have always had a tight partnership, and it runs deep. It started with how Zscaler ZIA improved the user experience and security around using Office 365, but has expanded into cooperation between multiple Azure security products around Zero Trust, including integrations with Azure AD and Azure Sentinel. On their Investor Day presentation in Jan-21, Zscaler stated they were the only security vendor in Microsoft's Networking Partner Program.
Last year, Zscaler won ISV of the Year in Microsoft's 20/20 Partner Awards. In May-21 of this year, they took Zero Trust Champion. In return, in Jun-21, Microsoft won Zscaler's 2021 partner award for Zero Trust Technology Partner of the Year, as Azure has adopted more and more Zero Trust postures within their security products.
AWS Partnership
Zscaler has worked with AWS for a long while, being a presence at AWS re:Invent at least since 2017. They first achieved AWS Security Competancy for ZPA in Sep-18, and have since been a AWS Advanced Technology Partner in Security Competancy, Public Sector Partner, and Marketplace Seller. On their Investor Day presentation in Jan-21, Zscaler stated they had joint GTM initiatives around using Zscaler in AWS. In Jun-21, in Zscaler's 2021 Partner Awards, they awarded AWS with their Customer-Centric Tech Partner of the Year. I want to see this deepen more, as the Microsoft Azure partnership is, and hopefully more deeply embed in any new AWS security products.
VMware partnership
VMware and Zscaler have been partners around SD-WAN and EPP for a long while. There were some initial hints about a deeper partnership back at ZenithLive 2018, where the VMware CEO talked about its VeloCloud acquisition for SD-WAN, and hinted they were integrating more closely with Zscaler. At ZenithLive in Sep-19, Zscaler awarded VMware a partner award for Partner of the Year for Americas. A deeper partnership finally appeared in a big way, as they recently expanded their relationship in Sept-20, integrating ZIA & ZPA more closely with SD-WAN and EPP/EDR products to help their combined customers adopt SASE.
VMware later announced a new Cloud Web Security product in Jun-21, selling it as having 150 POPs. This curiously matches the number of Zscaler POPs. A whitepaper explains the setup – users connect to ZScaler's platform one of two ways, through direct access from branch SD-WAN Edge to nearest POP, or through VMWare SD-WAN Gateways.
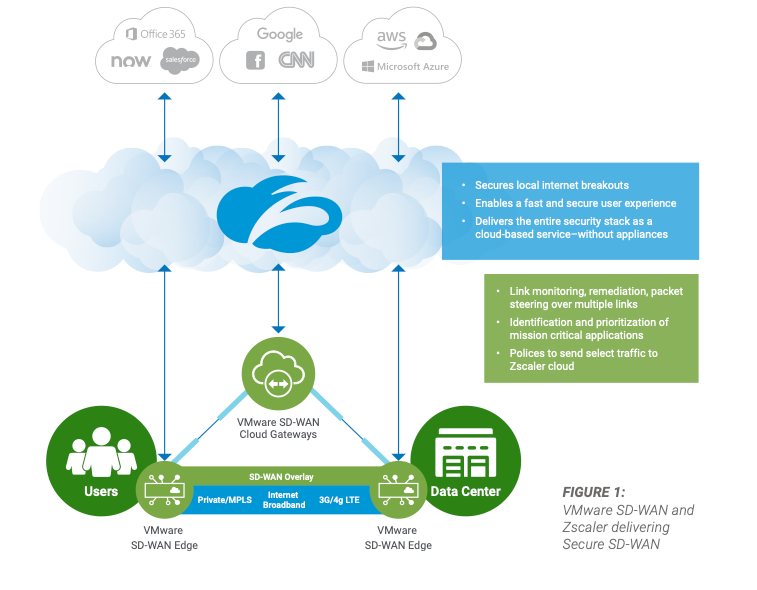
Most Recent Partnerships
In Apr-21, they announced a partnership with Splunk, in order to now be able to stream Zscaler logs directly into the Splunk Security Cloud. In return, Splunk Phantom, their Security Orchestration and Response (SOAR) product, ties into Zscaler's APIs to trigger automated response handling.
In Jun-21, they announced a partnership with ServiceNow, with deeper integrations between the platforms across Zscaler's ZIA, CASB, and DLP features.
With Zscaler Data Protection integrations, customers’ can improve data protection and compliance on the ServiceNow Now Platform. By allowing Zscaler to control authentication, remote and unmanaged devices can be easily restricted from accessing ServiceNow’s platform and data. Devices can only access ServiceNow through Zscaler, whereby security policies and access control to sensitive data can be enforced.
All of these show that Zscaler doesn't mind if you want to use its product lines piecemeal, as part of a larger security system around Zero Trust or SASE, or tie in other security analytical tools.
Growth
Their Investor Day presentation from Jan-21 reallllly digs deep into their GTM strategy and growth vectors from here, with segments from the CRO, CMO and CFO all highlighting the growing trends.
For me, it all boils down to...
- Growth of Zero Trust: Companies must lose their reliance on VPNs, with Zero Trust allowing them to simplify and improve user and app security, while both users and apps become more and more globally scattered.
- Growth of SASE Networks: Companies are allowing networking clouds, like Zscaler, to be the backbone of their entire enterprise network, handling all user and service traffic between their various cloud and data center locations, and giving them visibility over it all.
- Growth of Cloud Workloads: As companies move more and more of their workloads into the cloud, those resources and traffic need protecting, and enterprises need Zscaler to be the interconnective glue securing the traffice between their disparate environments.
- US Federal Government: The US Govt is drastically changing their security posture, and which Zscaler is very well positioned for to provide long-term solutions (already having the US Navy and FCC as Federal clients, amongst many many others).
- The rise of 5G and IoT/OT: The rise of IoT/OT is making data be generated at the edge, and requires more and more secure interconnections across that edge.
We've gone over the product lines addressing the first 3 trends, so let's dive further into their moves around the latter 2.
Government
Beyond its focus on Global 2000 (expanding now into more mid and small customers), Zscaler is serious about getting governmental clients, which typically require large long-term contracts. It has had ZIA at FedRAMP Moderate since Dec-18 (which allows PII and financial data), and is seeking High (which allows more sensitive law enforcement, emergency, and healthcare data). As of Feb-21, it was announced as prioritized in the Joint Authorization Board's (JAB) pipeline, meaning it is due soon. ZPA, on the other hand, gained FedRAMP High in Apr-20. I expect the new Cloud Protection products will go through this same process soon.
They've been marketing their readiness on government solutions here heavily, having solution pages for Public Sector, Federal, and State/Local. This attention to getting broad Federal approval by FedRAMP has clearly paid off. The FedRAMP Marketplace reports that ZIA is used by the CDC, DOE, DHHS, State and OIG, FCC, and the FTC. ZPA is used by CDC, DOE, Commerce, Labor, DHHS, State and OIG, Interior, Vet Affairs, FCC, FDIC, FTC, GSA, Los Alamos, NIST, SSA, and on and on. It seems the Federal agencies are taking Zero Trust seriously.
In Jan-20, a Zscaler executive won a 2020 Fed100 award for his efforts in removing the roadblocks for Federal adoption of modern security like Zero Trust. In Jan-21, Zscaler hired a new CISO, formerly the CISO of the CDC. And in Apr-21, they hired a new VP of Public Sector Channels, formerly from VMware.
But Zscaler has its sights set higher than FedRAMP. In May-20, they were hired by the DOD's Defense Integration Unit (DIU) to provide an initial prototype for a Secure Cloud Mgmt (SCM) system for securing their user access to apps across all 3 major cloud environments. In Apr-21, Zscaler partnered with a helper company to assist them with achieving all of the DOD's new Cybersecurity Maturity Model Certification (CMMC) requirements, required on all new DOD contracts. Finally, in Jun-21, the DOD announced the SCM prototype for DIU was successful. They used a 3rd party to verify, using the DOD's Defense Information Systems Agency (DISA) criteria, that Zscaler's platform delivers a fast, secure, controlled access over internet. This approval allows any DOD organization to now utilize Zscaler. Zscaler has been well positioned between DISA's new Zero Trust Reference Architecture published in Feb-21, and the new White House EO from May-21 (that I discussed before [premium]). In Oct-21, ZPA received Impact Level 5 (IL-5) authorization, allowing its Zero Trust platform to be used at all unclassified levels of the US Dept of Defense (DOD).
The US isn't the only Federal Government that Zscaler is after. They want the Australian Government as well, having received IRAP certification in Oct-20, then a second IRAP accessment in Feb-21. I expect this to continue straight into the European Union, given the existing GDPR friendliness in Zscaler's CSPM compliance checks and DLP signatures.
In Jul-21, NIST's Nat'l Cybersecurity Center of Excellence (NCCoE) picked Zscaler as a partner in their new Zero Trust Architecture Project, allowing them to be a voice at the table in helping NIST/NCCoE solidify the best security practices to recommend to the public. In the latest Q122 earnings, the CEO mentioned a major win with a defense industry integrator, and an upsell by a state govt to add Workload Segmentation. He also mentioned in Q&A that they expect a boost from the Infrastructure plan this FY, and that the White House EO has sped up the (always slow) govt deals. They stress they are the only security vendor with FedRAMP High authorization on both SWG & Zero Trust – though I don't see that ZIA's High designation is yet official. (Interestingly, they are not a partner in CISA's new initiative to collaborate with industry partners. I'd like to see them join.)
IoT/OT
IoT is now everywhere. IoT (Internet of Things) includes anything internet-connected, typically labelled with "smart". This includes set top boxes, smart TVs, media players, smart watches, smart glasses, geolocational trackers, medical trackers, data scanners, printers, smart vehicle/building/city sensors, digital signs, cameras, payment terminals, city traffic controls, digital home assistants, voice controlled anything, smart home locks, smart doorbells, smart lightbulbs, and, hell, I could go on all day, so let's just say any smart home devices you are hooking up to Alexa or HomeKit. And that is just the home and retail focused ones ... don't forget about the OT (operational technology) side for industrial and manfuacturing environments, including SCADA (supervisory control and data acquisition) and HMI (human machine interface) devices controlling equipment on factory floors or telco/network/energy distribution centers, or the PLCs (programmable logic controllers) hooking up to monitor or control non-smart equipment.
When you see the adjective "smart" applied to things, as in smart home, smart clothes, smart toys, smart phone -- substitute the term "hackable." They always come together.
— Kevin Kelly (@kevin2kelly) December 13, 2018
IoT has long been a focus of Zscaler (who has included IoT, OT, Factory points on their platform drawings for a long while). The reason being that you cannot install an agent on these devices, to bring them under the protective spell of an EPP/EDR platform like CrowdStrike or SentinelOne. For IoT devices, you must protect them in an agent-less way, which means through the networking. Zero Trust and SASE are the only path forward, and 5G is about to greatly enable the vast interconnectivity of these devices, and massively magnify the amount of data we can collect from the field.
In Feb-20, Zscaler released their 2019 IoT report, focusing on Shadow IoT (unauthorized devices). They showed a +1500% increase in IoT transactions over the year, with 83% of devices sending data unsecurely (in unencrypted plain text). They were blocking 14k malware attempts per month, 7x what they were seeing just 6 months prior, as they were seeing more and more attempted exploits to pull these devices into botnets for attack.
By their next 2020 IoT report, released in Jul-21, these alarming stats drastically increased. This time their focus was on all the unattended IoT left behind in enterprise locations, abandoned during the pandemic. They showed a 700% increase in IoT-specific malware attempts since 2019, with over 97% of being malware attacks for the Gafgyt and Mirai botnets. While 76% of IoT traffic remains unsecure (a slight improvement over the prior 83%), enterprise and home entertainment and smart devices showed an alarming 97% of traffic as plain text, with 11% of them transmitting to suspicious destinations.
This cannot continue. Enterprises must secure their IoT devices, and, in particular, OT devices enabling smart factories, equipment, and distribution. In Aug-21, Zscaler partnered with Nozomi Networks, an OT/IoT platform focused on the manufacturing, pharmaceutical, and energy industries. Together they will interconnect their platforms as a new protection platform over Industrial IoT (IIoT). ZPA will be utilized to provide edge-based Zero Trust access over Nozomi's OT/IoT management platform, to better allow more secure remote connectivity into smart factories and equipment.
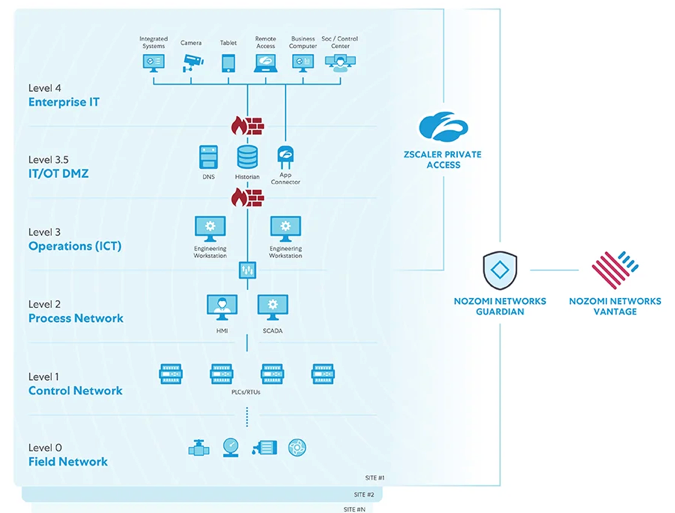
In a related blog post, Zscaler positions themselves as the ideal security platform over smart factories, providing Zero Trust capabilities over remote access, while keeping the underlying apps/devices invisible to the internet. Previously, heavy OT environments like smart factories were isolated and airgapped (not internet connected), which has to modernize with today's distributed environments and dispursed users. Gartner predicts by 2025 that attackers were be weaponizing OT devices. That seems ludicrously far out, as it is already happening. In Feb-21, a hacker nearly poisoned a town by changing chemical levels in their water supply, luckily discovered before harm was done. In May-21, a ransomware attempt made Colonial Pipeline shut down its pipelines that supply the East Coast with gasoline (as covered before [premium]), drastically affecting a major section of the US. Attacks against manfacturing equipment and factories are inevitable. I expect Zscaler to eventually introduce specific IoT/OT focused features over ZPA, Workload Segmentation, and SASE interconnects. In Sept-21, they announced that they have expanded their partnership with Siemens for protecting OT (Operational Technology) devices.
Conclusion
As stated at the start, this company has seen re-accelerating hypergrowth since the pandemic began. Operational leverage is kicking in, shown in their FCF margin at an all time high of 36%. It is an industry leader across its product lines, that customers continue to flock to and spend more and more. NRR is rising, and customers over $1M is growing 87%.
But beyond its core ZIA and ZPA, Zscaler is now entering new directions in protecting cloud workloads, including machine-to-machine Zero Trust and SASE. It continues to focus heavily on vital partnerships, and is well positioned to help the US Federal Govt and IoT/OT adopt Zero Trust.
Add'l Reading
I previously wrote up Zscaler as part of my Flavors of Security series back in Oct-19, when I first covered Zero Trust. If you need help with the security acronyms (like SWG and DLP), I recommend you revisit the first part of that series. And as mentioned before, see my prior "What are Edge Networks?", "What is Zero Trust?" and "What are SASE Networks?" posts to get the complete background on the cybersecurity ecosystem.
This post was originally written in September 2021, and Zscaler went on to report two more excellent quarters. Sign up for Premium if you want more coverage of SASE Networks, Edge Networks, Zero Trust, Data & Analytics, Observability, Dev Tools, and Enterprise SaaS.
- muji
