Okta's in the news again (and again, and again). Let's look at why, plus at the SEC's new rules around security incident disclosures. This will be of interest to other next-gen security platforms like Zscaler, CrowdStrike, Sentinel One, Microsoft, Cloudflare, and Palo Alto.
Join Premium for insights like this every week across AI & ML, Data & Analytics, Next-Gen Security, DevOps, and the hyperscalers. I recently covered Zscaler in depth, as well as CrowdStrike & its Fal.con announcements. I also published a Security Cheat Sheet to explain security terms like XDR, CNAPP, SASE, ITDR, and more.
I last looked at Okta [paid] in June, and found 4 big negatives: they aren't dealing with security issues well, a major exodus of top mgmt, the fumbled integration of Auth0, and how brutally slow they are to innovate into new adjacencies. I believe these are all contributing factors to their rapidly waning growth.
There have been a lot of high-profile breaches since then that find Okta with a significant role. In many, the security gaps are in their customers' architectures around Okta, not Okta itself. They are a major identity provider, so of course, any gaps in their customers' security layers will absolutely involve Okta, as attackers try to gain access to that customer's Okta instance to use it to unlock admin access to deeper systems. Given this, Okta always needs to tread carefully when determining if they are at fault. But they are a security company and this is a day-to-day need to remain vigilant.
However, Okta has ultimately found itself at fault in several of these major breaches. Thankfully for them and their customers, these security issues are all tangential to their security platform. Hackers are instead exploiting gaps in the lax security around Okta's own internal processes. Past reasons have included breaches elsewhere (Twilio SMS hack allowing attackers to easily circumvent Okta MFA), loss of source code (security of GitHub), and last year's hack of a workstation at an external IT support vendor that had access to customer info in their internal admin dashboard (Okta's fault!).
So let's be clear – Okta's identity platform is not full of gaping security holes. It's their internal tools and vendors around supporting their platform where gaps are being exploited. It seems abundantly clear that top mgmt doesn't particularly care to shore up the security of these operational processes. (I don't understand how their CISO is still there, given the lackluster responses by Okta when they are at fault. Perhaps, like past sales mgmt, he is being hamstrung and overridden by the CEO, or perhaps the board lawyers above mgmt.)
SEC Regulation Changes
Investors need to be aware of some SEC rules changes with 8-Ks (material events) and 10-Ks (annual report). After their initial proposal in Mar-23, the SEC finalized new rules in late July around reporting of cybersecurity incidents.
"The Securities and Exchange Commission today adopted rules requiring registrants to disclose material cybersecurity incidents they experience and to disclose on an annual basis material information regarding their cybersecurity risk management, strategy, and governance.
... The new rules will require registrants to disclose on the new Item 1.05 of Form 8-K any cybersecurity incident they determine to be material and to describe the material aspects of the incident's nature, scope, and timing, as well as its material impact or reasonably likely material impact on the registrant. An Item 1.05 Form 8-K will generally be due four business days after a registrant determines that a cybersecurity incident is material.
... The new rules also add Regulation S-K Item 106, which will require registrants to describe their processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats, as well as the material effects or reasonably likely material effects of risks from cybersecurity threats and previous cybersecurity incidents. Item 106 will also require registrants to describe the board of directors’ oversight of risks from cybersecurity threats and management’s role and expertise in assessing and managing material risks from cybersecurity threats. These disclosures will be required in a registrant's annual report on Form 10-K.
... The rules require comparable disclosures by foreign private issuers on Form 6-K for material cybersecurity incidents and on Form 20-F for cybersecurity risk management, strategy, and governance.
... The Form 10-K and Form 20-F disclosures will be due beginning with annual reports for fiscal years ending on or after December 15, 2023. The Form 8-K and Form 6-K disclosures will be due beginning the later of 90 days after the date of publication in the Federal Register or December 18, 2023."
That "if any" in the SEC statement is a big caution flag, as public companies damn well better have security processes in place to assess the risk of cyber threats! But I think the message is clear – top mgmt and boards are being held accountable for security incidents and overall security risk mgmt, and now have to report on their internal processes to limit & understand these risks, plus report on material incidents immediately after impact analysis. Now, there is plenty of space for companies to navigate these rules (for instance, they could hold off on a final analysis to delay things, or the vagueness of "material"), but the long and short of it is:
- After determining that a cybersecurity incident occurred (typically involving a breach, data exfiltration, and/or ransomware attempt) and doing a full impact analysis, a company has 4 days to disclose the material impact in an 8-K starting on December 15.
- Companies must describe their internal process for determining security risks and material effects and how the board is overseeing those processes in their 10-K starting on December 18. I expect this to include various levels of detail on the security & risk mgmt layers that each are employing.
This is all part of the Federal mandates [paid] towards better security and adoption of Zero Trust architectures. While these new reporting rules officially kick in December, companies are already beginning to disclose breaches and ransomware attacks in 8-Ks (as we'll see below).
I believe these newly required disclosures will spur further mgmt/board interest in modern next-gen security platforms around Zero Trust and security posture, like SSE and SASE for secure user access, XDR for endpoint posture, CNAPP for cloud & SaaS security posture, and EASM for overall outside-in exposure. Companies like CrowdStrike, Zscaler, Palo Alto, Cloudflare, and Okta should benefit from this increasing interest from large enterprises, as even the technology stragglers are being forced to look at the faultlines & gaps in their overall security & risk posture. I also think we'll see a big rise in risk mgmt solutions in these same next-gen security platforms to give top mgmt and boards a measurable view of their security risk posture. [For instance, Zscaler just announced Risk360 at Zenith in June. More on that soon.]
CrowdStrike, Zscaler, and Palo Alto have written on these new SEC rules, and I agree that all are well positioned.
From CrowdStrike: "From our view, the intent of the SEC rules is to protect investors by requiring more clarity, consistency and timeliness in how companies handle cyber-related disclosures. An ancillary effect is that companies may implement better overall cybersecurity hygiene and risk management processes to be more resilient to cyber incidents in the first place. ... The best strategy for handling the SEC’s disclosure rules is to prevent material incidents from occurring in the first place."
Okta
What's always been frustrating about Okta over the past few years is that it has so much going right for it in the overall trends.
- They are at the nexus of security as castle-and-moat security morphs towards Zero Trust and SASE, where identity is the core. These are all areas that industry minders foresee strong growth over the next several years, such as Gartner projecting a +32% CAGR by 2025.
- They continue to be a leader in IAM (over workforce) and CIAM (over SaaS apps) per those industry minders, and are moving deeper into adjacent markets like IGA and PAM.
- Their trailing competition is in turmoil. Thoma Bravo took nearly all of Okta's public IAM/IGA competitors private in 2021 (Sailpoint, PingID, ForgeRock), as well as Sophos (EDR & MDR) and Proofpoint (email security) before that. We'll have to see what emerges from all this, but to start, PingID and ForgeRock were combined in August. This means these competitors will be busy combining their heavily overlapping IAM platforms (like with Cisco and Splunk [paid] in observability) instead of disrupting identity security. Mgmt mentions they will leverage the "unique strengths" of each (without specifics), and how the combo broadens their geo footprint.
The one IAM competitor to watch continues to be Microsoft [paid], which has long been a leader in IAM with Active Directory – which is being folded into a new identity-focused security platform called Entra. From there, Microsoft has shifted into cloud SIEM+SOAR, XDR, CNAPP, and now SSE (with hints of a coming SASE).
While Microsoft is a continued leader due to the ubiquity of Active Directory, Microsoft's failures in properly securing it have led to the rise of ITDR (identity threat detection and response) as a critical capability within XDR and SSE platforms like CrowdStrike, Sentinel One, and Palo Alto. Microsoft Active Directory is always the first IAM that these ITDR platforms are sitting over to protect. Zscaler just announced their own ITDR at Zenith in June, as did Okta at Oktane in October.
From my XDR series [paid]: Identity Threat Detection & Response (ITDR, or IDR) provides tools that sit over an existing identity store (IAM) to bolster its security through the use of scanning and runtime monitoring. Scanning systems monitor the IAM for misconfigurations & known vulnerabilities, plus track privilege changes and risks in the pool of identities. Runtime tools provide protection via behavioral analytics as the IAM is used for authentication (verification) & authorization (access granted) actions.
Again, this is all about the battle for security analytics. Identity is a crucial part of the Zero Trust puzzle, and adjacent security platforms (XDR, SSE/SASE, CNAPP) are adding in better analytics over identity usage & attack detection (ITDR), which then ties into continuous risk assessment features within Zero Trust engines. This highlights how all these tools form an ecosystem around identity – once you determine a bad actor in your network/device, you need to sever access as quickly as possible before they build in other back doors beyond the compromised identity.
Mgmt shuffle
As I said in my June review [paid]:
Since that last Oktane, the co-founder and COO announced a year-long unpaid sabbatical (Nov-22 to Oct-23), disappearing at a crucial time and a signal he isn't that interested in managing the company any longer. Their much-touted President of Worldwide Field Ops (from Splunk) left in Nov-22 after an <2yr stint, and the CRO (her righthand man brought in soon after, also from Splunk) then left in Jan-23. It seems they had some disagreements with top brass over how to integrate Auth0, with the CEO overriding everyone -- meaning the failures are all on his plate. This Q, the CEO announced that the former CEO of Auth0 that leads their new Customer Identity Cloud has now been shifted into the new President of Business Operations -- seemingly positioning the company for a COO exit after that sabbatical.
... I know this is the cofounders' baby, but it is not being well run. Maybe Eugenio Pace as the new President of Business Ops will turn it around after the absent COO – or may he ultimately moves straight to the CEO role.
After the co-founder & COO went on sabbatical for a year in Nov-22, we eventually saw Eugenio Pace get promoted to President of Business Operations in Jun-23. Little surprise on the news a few months later in August (in the latest Q224's 8-K).
"On August 24, 2023, J. Frederic Kerrest, the Company’s Executive Vice Chairman, Chief Operating Officer and Co-founder, notified the Company that he will not return as an employee from his current sabbatical, which ends on October 31, 2023. Mr. Kerrest will continue to serve as a member of the Company’s board of directors as Vice Chairman."
So now it's clear that Auth0's leader was promoted to replace outgoing Kerrest in everything but title. We still don't have permanent replacements for those missing CRO or PWFO roles. Their leadership page shows their head of EMEA in London stepped in as interim CRO (now for 9 months). [For some reason that page doesn't show their CMO of the past two years.]
We have since seen their former CRO join Klaviyo [paid], while their "retired" President of WFO eventually joined HashiCorp.
Slow to innovate
They are finally moving into IGA and PAM, adjacencies that I have been expecting since late 2019:
It is veering heavily into Zero Trust with its new Server Access (Zero Trust PAM) and Access Control (Zero Trust IAP proxy), after its acquisition of ScaleFT. PAM features compete against CyberArk ... From here, I feel Okta could easily move in some other directions that are identity- & access-related, such as Governance side of IGA (against Sailpoint), CASB/DLP (against Cisco, McAfee), and even SWG (against Zscaler's ZIA, Cisco).
... They are fully embracing Zero Trust, acquiring ScaleFT a year ago to enable multiple new directions: Server Access (PAM) and Access Gateway (IAP, aka an IAM+Zero Trust proxy). That acquisition is why I am still fully invested in Okta -- it is a fantastic new ancillary direction of Zero Trust yet still very Identity-related. Server Access is a Zero Trust flavor of PAM, an incredibly relevant bolt-on product that existing customers are sure to expand into. Access Gateway is not being called such, but it is an IAP (Identity Aware Proxy) flavor of Zero Trust per its architectural docs, not ZTNA via micro-segmentation.
I foresaw them moving more directly into Zero Trust access instead of being solely the identity provider side of the ecosystem – but they never did fully embrace the Zero Trust products from their ScaleFT acquisition, and to this day refuse to call Access Gateway a Zero Trust solution. Ultimately, Advanced Server Access gave them the building blocks for a fuller PAM product.
Those expected adjacencies into IGA and PAM finally showed up at Oktane'21 in Apr-21 ... and then we waited, and waited, and waited. I finally griped about this in June [paid] on how slow Okta is to innovate:
But what about that huge move into IGA (identity governance) and PAM (privileged access) that they announced way back in Apr-21? They have been extremely slow at moving into these newly announced market adjacencies. IGA was first announced in Apr-21, and finally went to GA in Aug-22 -- a year and a half later. PAM was announced at the same time, and in this earnings call, mgmt stated it had been in beta for the past 6 weeks – meaning it has taken over 2 years to get this product out. The CFO said it was likely to go GA by the end of year, meaning Okta will not see benefits until FY25 or more like FY26. The next Oktane conference is in early October, and I expect PAM to be a major focus, along with any other new platform announcements.
Okta just held its annual Oktane conference and the theme of the many announcements was "limited early access ...coming in 2024". They continue to project a lot of great new directions, but also how it is all under active development that will take a year+ to emerge. [I take their "limited early access" as basically meaning private beta.]
- They announced a new ITDR to better tie their risk engine ecosystem together. It integrates with XDR and SSE partners like CrowdStrike, Zscaler, Netskope, Palo Alto Networks, Trellix, and others. This is coming to early access Q1 2024.
- They announced a new Okta AI initiative, which will lead to coming Generative AI features across their Workforce and Customer platforms. They mention it is built atop Google Cloud & Vertex AI (likely using PaLM or the upcoming Gemini LLM). These are coming to early access across Q1-Q4 2024. In a blog post they assert how they have a strong pool of security data to drive this new underlying AI, and how it is forming a core AI that will drive multiple AI-based capabilities across Workspace, Customer, and IGA products.
- In their faster-growing Customer platform (managing users in SaaS apps), they continue to support more advanced use cases, such as adding phishing-resistant passkey support plus other features like finer-grained authentication, SCIM support, and 4 future Okta AI-driven features. [Too bad they aren't using phishing-resistant keys within their own organization, as we'll see below.]
- They recently pivoted into a new consumer-facing product in September with Okta Personal, a free personal password-tracking app that competes with LastPass, Keeper, and 1Password. During Octane, they announced they had acquired the Uno mobile app team to accelerate its development, and added a new Okta Personal for Workforce product in beta as a hybrid solution that blends the new Personal app with their existing Workforce product – allowing employees to access both work and personal sites from the same device. From here, the consumer app is adding a Family plan, which may be another way to monetize it.
- What about that long overdue PAM product first announced in Apr-21? They announced it will finally go GA in December – nearly 3 years since it was first announced. [I am a bit flabbergasted it took this long, given the head start they had with Advanced Server Access from their ScaleFT acquisition.]
- They are also expanding their new IGA product to add self-managed provisioning (IGA Entitlement Mgmt).
Okta finally added its own ITDR. Yet again, this just makes me think that Okta could have moved into this area earlier, and how it could have provided a great funnel. ("Don't trust your Microsoft as your identity provider but aren't ready to fully rip it out? Use Okta as an ITDR umbrella over it.")
However, unlike other ITDRs (like from CrowdStrike and Sentinel One) that sit over Active Directory, Okta's ITDR is more about sitting over a Zero Trust ecosystem to better tie it all into Okta as the main controller, to then trigger workflows in Okta and actions in integrated platforms from there. For instance, Zscaler's just announced integration ties its own new ITDR (running at the endpoint, similar to ITDR solutions in XDR platforms) that then ties in with Okta's ITDR to trigger identity actions.
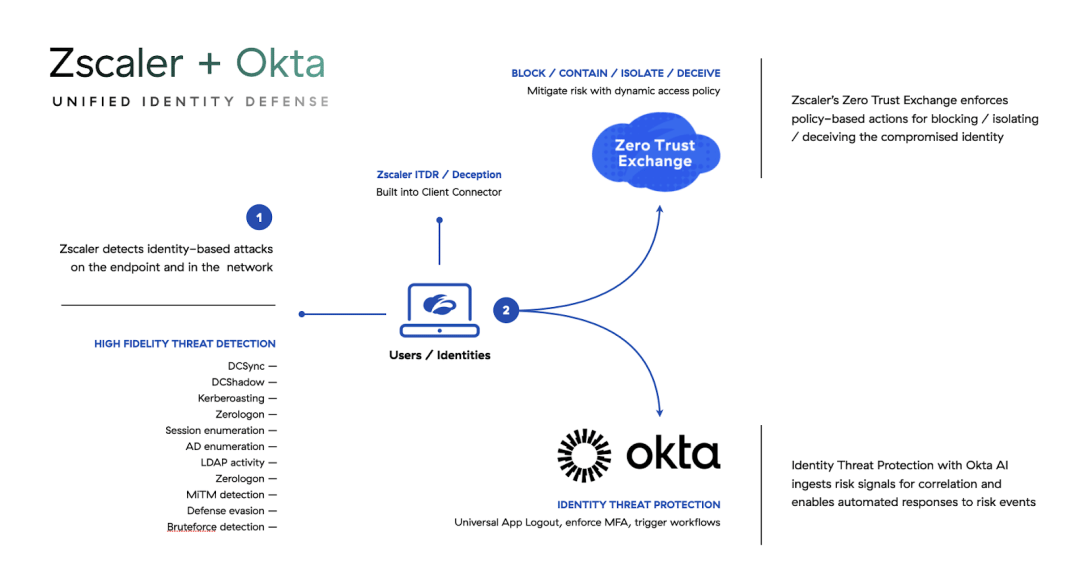
These solutions continue the battle for who owns the analytics over these ecosystems. But rather than providing a "universal" ITDR like the other platforms (that protect over an identity store like Microsoft), Okta's new ITDR solution is really the same Risk Engine/Ecosystem (with a new name) that has been expanded to integrate with other ITDRs. [See my past Zero Trust piece for more on their Risk Engine that emerged in Apr-21.]
Breaches
I was last on this topic back in early 2022, after Okta had a breach [paid] of their internal apps through an external support vendor. More worrying than the security gaps in their own internal processes was their lackadaisical response. [The soundtrack to this part is "Something's Gone Wrong Again". And again, and again.]
As I wrote before:
This seems to be some legal wrangling on what entails "breached" and what part of their stack was affected. It seemed quite clear from the images that their backend tools were accessed via a compromised user account. However, their words seem to be focused on their security platform ("the Okta service") that customers use – which, let's be fair, was not breached – but this response is muddled and starting off wrong.
... I also find it extremely odd that they JUST got the forensics report. It apparently took 8+ weeks to research, and it seems there was little movement from Okta during that time (as, again, they left the investigation and remediation to their third-party vendor).
... I cannot believe how much Okta downplays the capabilities exposed in the breach. Yes, this is all true... and seems to be meant as a way to comfort the (now very worried) customer base just learning of all this through the news and the CEO's tweet. But again, this is a hacker group that thrives on worming their way into identity systems (via social engineering) and exploiting gaps! This breach should not be so easily dismissed, as it allowed an MFA-exploiting hacking group access to reset MFA at will.
You won't be surprised that Okta's customers and Okta's internal operations have again (and again) been breached by another hacker group that specializes in social engineering.
In August, Twilio was hacked, which led hackers to be able to exploit SMS in order to circumvent Okta's MFA (multi-factor auth) techniques that utilize SMS. This is a highly insecure form of MFA, given how hackers are using SIM swapping and cloning techniques (via social engineering against telcos) in order to mimic a target's phone in order to receive incoming SMS messages. See Twilio's full post-mortem, which showed 125 customers (later revised to 163) affected including Cloudflare, Digital Ocean, Doordash, and Mailchimp. Cloudflare commented on the situation to stress how their Zero Trust service and reliance on phishing-resistant hardware keys (put in place after the last Okta breach in early 2022 that affected them) helped block the attack.
So if Twilio’s SMS services get hacked… guess what…
— muji @ hhhypergrowth (@hhhypergrowth) August 30, 2022
… then Okta’s multi-factor auth (MFA) services that rely on SMS also get hacked. $TWLO $OKTA
It’s turtles all the way down… hackable at any level of the chain. https://t.co/K9Xq7p1T05
Okta's CEO spoke on this in the last earnings call, after an analyst asked about the rise of SMS cloning (and how unsafe SMS is as part of MFA):
CEO in the latest Q223 Q&A: "I think the problem is that some of these customers were in a situation that they had a resource that was sensitive, and they were using this approach that turned out to be not as secure as it should. So, the task for us is, first, openness and transparency. We're being very aggressive about communicating what happened. I don't know if you saw, but we have a blog post on this that Scatter Swine that kind of outlined everything that happened and we share that with customers. And then also, we need to do a better job, I think, helping them understand exactly the configuration of the product and what the risk versus their configuration, the risk appetite on the resource they're protecting and help the whole industry along with our customers move up toward this unphish-able configuration, which is no password, no log-in page.
But all of our conversations with customers have been very confident in our ability to protect them and configure the product in a way that's effective. And we're being a good partner to them to understand how to defend these things on mass because this is happening all the time to customers. They know that all of their infrastructures being attacked and having partners that can help them ratchet up their defenses all the way toward this unphish-able configuration is something they're very comfortable with.
Comforting words! Okta is here to help!
A month later, right before its annual Oktane conference, several high-profile attacks by this same hacker group (known as Scatter Spider, Scatter Swine, Oktapus, and other names, depending on the threat intel provider) against Vegas casinos lead to breaches, data exfiltration, and ransomware extortion. Caesars was the first victim, which lead to data exfiltration of their loyalty program database with PII. (Luckily it did not lead to ransomware, so Caesars is doing something right.) They ultimately paid $15M (per WSJ) and got the data back. They filed an 8-K immediately stating it was a breach from a social engineering attack on an outsourced IT support vendor (a familiar refrain), but they ultimately didn't know the financial impact yet beyond offering credit monitoring to affected customers.
MGM wasn't so lucky. A similar attack caused them to shut their internal systems down quickly to contain it. After a vague PR, they confirmed that their VM hosts had been encrypted in a ransomware attack. This caused mayhem across their many casinos (MGM, Bellagio, Aria, Cosmo, Mandalay Bay, etc), including hotel room keys, reservation systems, and slot machines no longer working. It ultimately took 10 days to fix, and by September 20 announced they were operating normally. An interview with the supposed hackers by Financial Times suggests the attack took a mere 5 hours and evaded detection for 8 days.
Later on October 5, MGM filed a PR with a post-mortem and an 8-K that stated they too had a data loss that exposed PII. MGM noted it cost them $100M in lost EBITDA from the confusion and guest impact, plus an additional $10M in one-time expenses in remediation to clean up the breach and ransomware. The impact of that one incident would pay for decades of next-gen security services!
MGM 8-K: "Promptly after detecting the issue, the Company responded swiftly and shut down its systems to mitigate risk to customer information, which resulted in disruptions at some of the Company’s properties but allowed the Company to prevent the criminal actors from accessing any customer bank account numbers or payment card information. Since that time, operations at the Company’s domestic properties have returned to normal and virtually all of the Company’s guest-facing systems have been restored. The Company continues to focus on restoring the remaining impacted guest-facing systems and the Company anticipates that these systems will be restored in the coming days."
Okta detailed the steps the hacker group took in their post-mortem. But again, this wasn't directly Okta's fault – outsourced IT support desks used by the customers were to blame.
All ALPHV ransomware group did to compromise MGM Resorts was hop on LinkedIn, find an employee, then call the Help Desk.
— vx-underground (@vxunderground) September 13, 2023
A company valued at $33,900,000,000 was defeated by a 10-minute conversation.
But that's not all! Right before its Oktane in early October, Okta again had a breach within its own internal operational processes – just like in early 2022. Krebs on Security covered the details well. Somehow a hacker wormed their way into Okta's internal support case mgmt system, and from there, was able to access browser session recordings that Okta's support asks its customers for when they have issues. (Yes, the customers uploaded sensitive session keys. But it's Okta's support process they were following. Why isn't Okta scrubbing them as they are uploaded?)
Apparently, BeyondTrust discovered illegitimate access attempts on its Okta instance on October 2, and thwarted the attacks. Cloudflare noticed the same on October 18, and also thwarted the attacks. Earlier than those was how 1Password saw attempts as early as September 29. Finally, on October 20 (~18-21 days after being notified by those above), Okta finally accepted the blame as being on their side, after initially thinking it was yet again customer-related gaps being exploited.
From the Kreb's piece: "In an interview with KrebsOnSecurity, Okta’s Deputy Chief Information Security Officer Charlotte Wylie said Okta initially believed that BeyondTrust’s alert on Oct. 2 was not a result of a breach in its systems. But she said that by Oct. 17, the company had identified and contained the incident — disabling the compromised customer case management account, and invalidating Okta access tokens associated with that account. Wylie declined to say exactly how many customers received alerts of a potential security issue, but characterized it as a “very, very small subset” of its more than 18,000 customers. ...Okta’s Wylie declined to answer questions about how long the intruder may have had access to the company’s case management account, or who might have been responsible for the attack. However, she did say the company believes this is an adversary they have seen before. “This is a known threat actor that we believe has targeted us and Okta-specific customers,” Wylie said.
Per a TechCrunch article, Okta said ~1% of customers were impacted, which means 184 (of the 18.4k they last reported). As in early 2022, this is an operational failure by Okta, not a platform failure. They haven't provided any further details on how this hacker gained access to their case mgmt system, but their breach led to customers' breaches.
As much as they liks to talk up Zero Trust, Okta assuredly doesn't use Zero Trust itself internally nor the phishing-resistant hardware keys that its own platform supports. The understandably frustrated Cloudflare (impacted 3 times in the last 2yrs by Okta-related exploits) offered Okta several valid suggestions on how to improve itself internally, as well as how customers of Okta can better harden their identity security. (Is it time for Cloudflare to make its own ITDR or edge IAM?)
Financial Checkup
Since I last checked in [paid], Okta reported Q224 in Aug-23. The top line continues to slow. Revenue was $556M for +23% growth, rebounding to +7.3% seq growth from +1.6% the prior Q. The Customer segment (Auth0) was strongest at +29% growth. cRPO grew +18% to 1.77B.
Profitability remains the best part, with margins going positive over the past year. Op margin grew +14pp to 11% and FCF margin +14pp to 9%. These topline challenges are making their TTM Rule of 40 fall from its high of 65% to now 41% – with Q2 hitting a new low of 32%. NRR has been dropping over the last 2Qs to now 115%. Q3 is being guided to revenue +16% (under +1% seq, their 2nd worst) and cRPO +13%, with FY24 revenue raised to +19.2%.
Adding Okta to the landscape in next-gen security from the last piece on Cisco & Splunk [paid] shows their (diminishing) top-line growth well below other next-gen security platforms I follow.
| Company/Segment | Last Q Rev | YoY Growth |
|---|---|---|
| Okta | $556M | +23% |
| Cisco/Security | $987M | +0% |
| Palo Alto/NGS (from ARR) | $739M | +56% |
| CrowdStrike | $731M | +37% |
| Zscaler | $455M | +43% |
| Sentinel One | $149M | +46% |
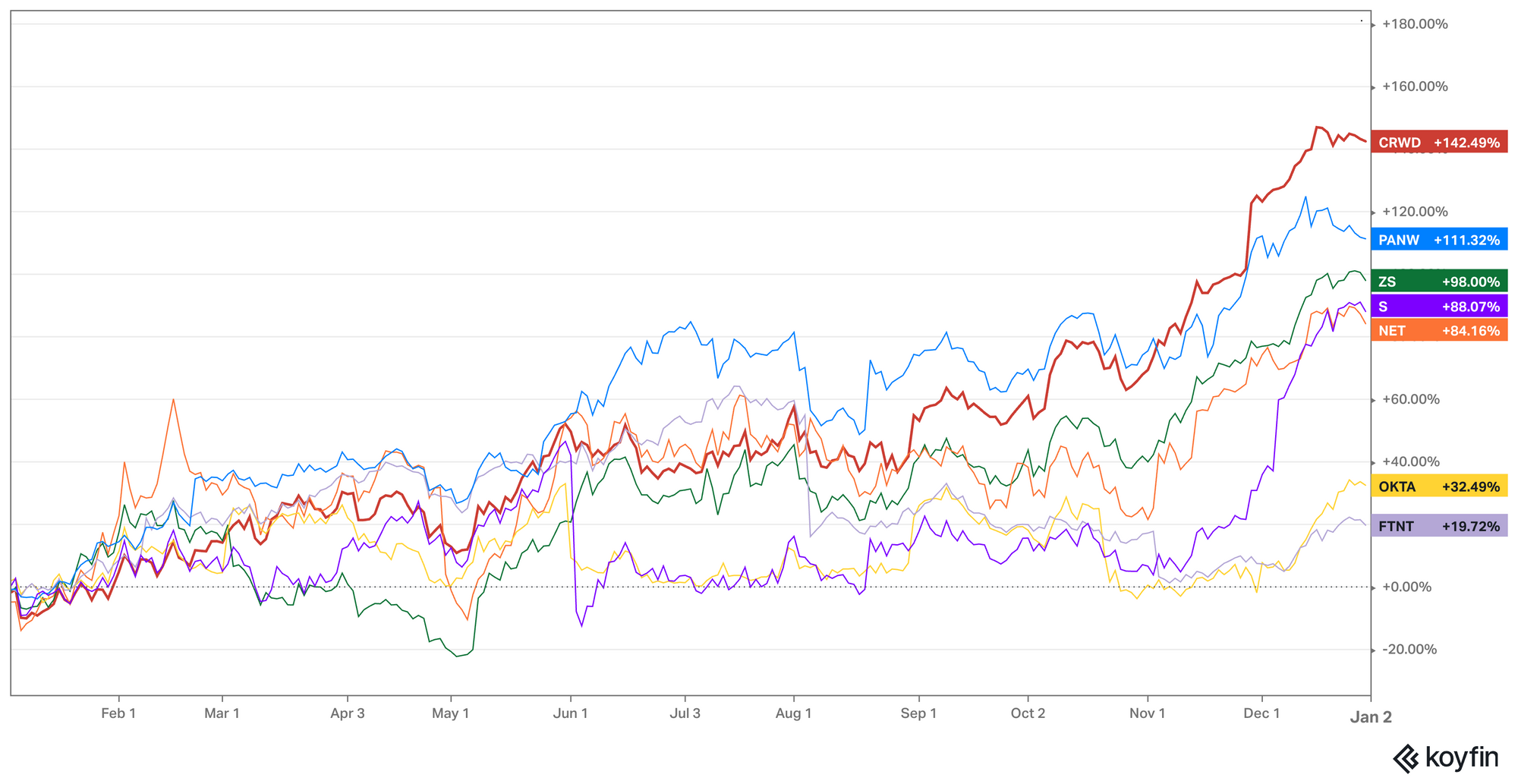
Okta remains quite unappealing, and the market agrees. It ended 2023 well below other next-gen security names.
Add'l Reading
- See the past Flavors of Security series for an extensive primer on next-gen security, as well as detailed pieces on Zero Trust and SASE.
- I have a number of related pieces on next-gen security in my Premium service [all paid], including an XDR series explaining why endpoint platforms are adding cloud security, security data lakes, and identity protection, a Federal Zero Trust series on how the Federal government is adopting Zero Trust, a summary of Microsoft's moves into security, my take on Cisco's acquisition of Splunk, and recent reviews of Zscaler and CrowdStrike. Join Premium to read more!
Let's hope Okta pulls out of this tailspin, puts some better mgmt at the helm, and starts taking customer reports of breaches more seriously.
-muji
