Like "Zero Trust" and "SASE Networks", Extended Detection and Response (XDR) is a term that has a significant amount of buzzwordiness, with enough vagueness that every vendor envisions something slightly different. Today, let's cover what XDR is, from the lens of EDR platforms like CrowdStrike Falcon, SentinelOne Singularity, and Palo Alto Cortex, and how well it integrates into the Zero Trust paradigm.
A Brief Overview of Network Security
But before we dive into XDR, we need to see where it came from in the network security landscape. Let's review a few security solutions right quick:
- Endpoint Protection Platform (EPP) = a service (via an installed agent) deployed on all servers, laptops, and devices (collectively known as endpoints) for monitoring and detection of malicious activity. EPP is about protecting the device itself, not the traffic to and from it. It includes preventing malware and virus attacks, and typically includes cloud-based endpoint mgmt capabilities (EDR).
- Endpoint Detection & Response (EDR) = a cloud-based platform over deployed EPP agents, to continuously monitor a pool of endpoints for advanced threats and broader attacks, and helps automate remediation (such as taking action when a malicious file or breach is detected).
EPP/EDR is what CrowdStrike's (Falcon) and Sentinel One's (Singularity) platforms have provided from the start. They provide an agent that installs onto endpoints in order to provide threat protection, and a cloud platform to manage and observe over that pool of endpoints. "Endpoint" typically means all the systems an enterprise has in its possession upon its network, including servers, desktop workstations, laptops, and mobile devices – anything with an operating system (OS) the agent can install upon. To further fill in the security gaps, EPP/EDR platforms have been adding network scanning capabilities, to map out any devices on an enterprise network that cannot be protected by an EPP agent (like IoT devices, cameras, and printers), and monitor over the network traffic they generate. EDR platforms also offer in-house threat intel (CrowdStrike Falcon X, SentinelOne Singularity Signals, and Palo Alto Cortex Autofocus) to further enrich the analytics, plus allow customers to ingest 3rd-party threat intel feeds from partners. CrowdStrike even goes a step further with Falcon X Recon, looking through the dark web for threats & data exposures.
With the migration to the cloud, the exposed surfaces have been increasing beyond the systems within an enterprise's immediate control, so endpoint companies have been expanding into:
- Cloud Workload Protection Platform (CWPP or CWP) = a service (via an installed agent) deployed into cloud-native environments that provides real-time threat detection and monitoring. Can be thought of as a cloud-native version of EPP/EDR, specifically for the runtime protection of VMs, containers, and Kubernetes clusters that are running in the cloud.
- Cloud Security Posture Mgmt (CSPM) = a scanning service that continuously and autonomously monitors cloud environments for the security posture of all cloud infrastructure, typically including VMs and containers. It evaluates configuration & settings against set policy & compliance rules, allowing for an enterprise to score its risk against known vulnerabilities, regulations, and cloud-native security best practices. The starting C can also stand for "Container" (instead of "Cloud") for services focused solely on scanning cloud-native containers.
All of these EDR platforms have veered heavily into cloud security – although I will note that SentinelOne does not (yet) have a CSPM capability for proactive scanning of cloud infrastructure. But endpoints and cloud workloads are but one part of the network security puzzle. Besides the endpoints being monitored, enterprises must also protect the users using those endpoints, the apps and data being accessed by those endpoints, and the network interconnecting it all. Enterprises must typically utilize other security services for:
- User and Entity Behavioral Analytics (UEBA) = is the utilization of ML algorithms to track the normal behavior of users and systems, in order to detect anomalous behaviors or deviations, to help mitigate against insider threats, compromised accounts, brute-force attacks, or intrusions.
- Network Detection & Response (NDR) = network service (akin to an EDR for endpoints) that continuously monitors over all enterprise network traffic for signs of advanced threats and broader attacks, and helps automate remediation (such as taking action when malicious traffic is detected).
- Network Traffic Analysis (NTA) = is the utilization of ML algorithms and rule-based detection over raw network traffic and flow data, in order to isolate abnormal traffic and suspicious activities on an enterprise network. Think of it as UEBA, but for anomalous network traffic.
All of the security data across an enterprise network, from network appliances (firewalls & routers), network access services (SWG & Zero Trust), cloud infrastructure, identity stores, and app & data usage, must be stored and analyzed in a centralized location.
- Security Information & Event Management (SIEM) ["sim"] = A forensics-oriented centralized collection system for tracking and correlating disparate events from network, system, app, and device logs, for near real-time monitoring & alerts.
- Security Orchestration and Automated Response (SOAR) = Service to automate workflows and incident response handling of low-level security events and policy violations detected in a SIEM. (Typically combined as a SIEM+SOAR.)
SIEMs are traditionally the tool where security teams and operation centers (SOCs) do their security analysis, by trying to piece together how actions correlate across the various layers of their network and security stack being collected. SIEMs tend to need a lot of curation – of both the data going in, and the analytics being done over it. In order to turn any insights into actions, SIEMs have been extending or integrating with SOAR capabilities, in order to more fully automate response actions back into the systems that feed into them. SIEMs are essentially giant security-focused data lakes with analytics – but they have a number of challenges.
One challenge is the complexity – it's up to the security team to figure out how one security system's logs relate to another in the SIEM. Security teams have to stitch together a log ingest system to feed the security logs into the SIEM, and may need to curate the data to align it between systems. They must also add in any needed integrations in a separate SOAR system if they want to push actions back to those systems. And the team must hone their analytics to fine-tune it somewhere between too sensitive (lots of false positives) and not sensitive enough (lots of false negatives). Another is the delay – it takes time for all the systems to feed into this centralized location, and correlating between the various feeds into the "big picture" can be a challenge. This is not helped by how the ingest and SOAR integrations are typically detached from each other (log mgmt for ingesting, vs out-bound integrations for orchestration). And possibly the largest challenge is the sheer size of data. Once the ingest of all these security feeds is automated, a huge amount of data can suddenly swamp the system (and the costs). Enterprises are starting to leverage directly-managed data lakes in public clouds (or even Snowflake) for the longer-term historical data, where they can more easily manage the amount of data they retain and the associated cost. This is why many SIEMs (as well as Observability platforms) are taking a data lake-focused approach to their platform, like Splunk and now Datadog [with their new Online Archives for warm storage, and data lake export in Logging Without Limits for cold storage discussed in Nov-21 (premium post)].
But, most important to the rising tide towards adoption of Zero Trust & SASE Networks, SIEMs are ultimately a passive pool of security data – with, perhaps, some of the repetitive actions in detection & response being automated via SOAR. Combining all these challenges ultimately means that SIEM+SOAR are not particularly ideal for making real-time decisions that Zero Trust and SASE Networks can use for tracking conditional access, which can adjust dynamically in real-time based on the user's actions (as discussed with Zero Trust before).
Enter XDR
XDR is how EPP/EDR platforms are moving closer to being a SIEM+SOAR. It makes sense to have endpoints be the focal point, as they are the biggest part of the equation in network security – in that all network traffic is either originating from an endpoint (requests coming from a laptop, device, or cloud workload) or is the destination for it (requests coming into a server or cloud workload).
- eXtended Detection & Response (XDR) is extending EDR further by pulling in complementary data sources to provide the full context of endpoint usage. This can include security data from any other related network systems (such as network traffic, cloud infrastructure, and application logs), pulling from either a centralized SIEM, or directly from other integrated partnering services. Think of XDR as EDR+SIEM. Full bidirectional integration with XDR partners is ultimately similar to what a SIEM+SOAR is striving to achieve, but XDR allows for adjusting conditional access in real-time across integrated services.
XDR is about providing the EDR's security analytics with more context about the endpoint's actions from surrounding security layers. This means integrating the data from networking, identity, and app logs, in order to get the fuller picture over the entire security stack – from user to device to network to app to data. XDR can then be providing capabilities akin to NDR (threat hunting over network traffic), NTA (analytics over network traffic), and UEBA (behavioral analytics over user or system actions) in combination with EDR (threat hunting over endpoints). XDR is about getting the bigger security picture, so ultimately, is about owning the analytics over the entire networking stack.
Palo Alto's CTO & founder coined the term "XDR" at their Ignite conference in May-18 (naming it at @46:44), saying it meant the anything detection & response platform. EDR ultimately has too limited a view from the endpoint, so must pull in context from the other parts of the networking stack. He mentioned how it was vital for XDR to overlay and interwork between tools (via direct integration), instead of trying to stitch together separate point solutions in a SIEM. Ultimately, the goal for XDR is to better automate across threat detection and response.
At a minimum, XDR is EDR+, improving EDR by allowing it to see more context around endpoints. But ultimately, it can likely replace many SIEM+SOAR instances, given that the bulk of networking occurs between endpoints or cloud workloads. SIEM+SOAR platforms, of course, want to consider XDR as just another source to pull into their solution (see Splunk's take in Jun-21), but that leaves XDR as just another security silo to pull into a centralized store.
Some SIEMs are even renaming themselves as XDR, as an evolution of the SIEM+SOAR. But the industry minders like Gartner and Forrester both agree that XDR is the next-gen of EDR. CrowdStrike, of course, agrees, per their Fal.con keynote in Oct-21 and a later blog post in Feb-22, as does SentinelOne in this blog post from Oct-21. The common stance is that security over the endpoint and its traffic has to be coming from the endpoint, not from the outside platforms focused on doing ML over collected data. While SIEMs want XDR to be another data source, it seems now more appropriate to have the SIEM feed any related contextual data it collects into the XDR, than it is to do the opposite.
XDR can provide complete protection over all attack surfaces (endpoints, cloud infra, networks, apps), by interconnecting correlated events from across the different layers. But beyond that, XDR (and its tighter integrations) is much more adept than a SIEM+SOAR at fulfilling the Zero Trust notions of controlling access in a conditional way, adapting in real-time based on the behaviors of the user (identity), system (endpoint), or traffic (network). XDR, being over the endpoints themselves, can provide not only active but reactive protection. It can trigger real-time actions (such as cutting off access, or quarantining a file) when it sees anomalous behaviors in and across security layers.
I said above the challenges for SIEM+SOAR are complexity, delay, and data size. Addressing both the complexity & delay, XDR hopes to provide a simpler automation capability than SOAR. Platforms are creating an ecosystem of partners that tightly integrate bi-directionally, in order to automate both the ingest and response capabilities, instead of having to create separate log mgmt and SOAR integrations. Some are also starting to use AI methods to pre-correlate the data upfront in real-time during ingest, instead of after the fact – like a SIEM must over disparate logs that ingest at different rates. And as for the size of all that data, XDR platforms are keenly aware of the challenges in handling the sheer scale of data needed for unsupervised ML. The more context (data), the better the analytic insights. This is why EDR platforms like SentinelOne and CrowdStrike have heavily focused on obtaining data lake-based analytical capabilities (acquiring Scalyr and Humio in Feb-21), to help with the ingest and to better handle the analytics at scale.
Over time, several kinds of XDR have emerged – native XDR, hybrid XDR, and open XDR. Native XDR typically means an all-in-one platform that tries to not only provide the EDR capabilities, but also all the other detection services being pulled into it for context – such as Palo Alto Cortex XDR, across Palo Alto's wider product line of Prisma Access (SSE), Prisma Cloud (CWP & CSPM), & Prisma SASE. (In fact, there isn't native integration within their Cortex XDR – customers must use the separate XSOAR product for orchestration between tools.) Open XDR is typically attempting to make XDR become a common layer for analyzing and automating across existing security tools already in place, such as what private startups Exabeam, Stellar Cyber, and ReliaQuest provide. Hybrid is in the middle, where XDR platforms are creating a tighter ecosystem of closely-integrated partners, in order to better cross-automate the ingest and orchestration between the tools. CrowdStrike and SentinelOne are both hybrid, having created partner ecosystems around their XDR platform with an associated marketplace. I believe this to be the better approach, as these integrations then feed nicely into the Zero Trust & SASE ecosystems that are emerging to manage and secure enterprise network access. As mentioned before, when these ecosystems work together, they can bi-directionally interoperate across Zero Trust tools to conditionally control a user's access in real-time. XDR makes for a stronger Zero Trust.
And some platforms are pulling XDR into other adjacent directions from here, with the most interesting moves being around adding in fuller identity and data protection (especially tying in behavioral analytics over it all). CrowdStrike has made some interesting acquisitions in Preempt in Sep-20, and SecureCircle in Nov-21, while SentinelOne just acquired Attivo Networks in Mar-22.
Palo Alto hasn't moved towards identity or data security, but instead has been expanding more into new features around networking. They acquired Expanse in Nov-20 (now Cortex Xpanse) for attack surface mgmt, to map out & secure the various systems, devices, and cloud infrastructure within an entire organization's network. They also acquired Sinefra in Nov-20 to provide digital experience mgmt (DEM) for monitoring the performance of interconnected endpoints. [This is akin to Zscaler's ZDX.] I don't expect other XDR platforms to follow suit in these directions, as Palo Alto is the one trying to navigate both sides of networking (Prisma) and endpoint (Cortex). CrowdStrike and SentinelOne are likely to be more content to let Zero Trust partners like Zscaler and Cloudflare provide these types of capabilities.
Managed Services
Automation can only get you so far – you will always need human oversight over security tools, to know what to watch for, better hone the analytics, and, most importantly, know how to investigate and react to a discovered attack or breach. But SecOps skills are extremely in demand, and, even once a new hire is obtained, will need continual upskilling to keep up with shifting modern tools and attack vectors. CISOs need to bring in help, and several different managed services exist to help enterprises augment or replace the in-house Security Operations Center (SOC).
- Digital Forensics and Incident Response (DF/IR, or just IR) = Advisory services that help clients deal with a security breach, investigate a security incident to determine the scope and timeline of the breach, and take responsive action to remediate.
- Managed Security Services Provider (MSSP) = Outsourced service that uses log aggregation to discover threats. Customers ship logs to an automated service that provides user alerts via a portal. Think of it as a managed SIEM.
- Managed Detection and Response Services (MDR) = Outsourced service that uses continuous monitoring to discover threats and take responsive action to remediate. Provides deeper inspection than MSSP, which typically involves human monitoring as well as ML/AI over NDR and EDR (network and endpoint threat detection), plus DF/IR services. Can be thought of as a SOC-as-a-Service.
Given the new directions of EDR moving into cloud workloads and now XDR, new managed services have emerged to oversee and manage these security platforms for you.
- Managed Extended Detection and Response Services (MXDR) = An MDR service that is focused on monitoring over the broader XDR landscape, continuously tracking endpoint behavior as well as context from network, cloud, identity, and data security.
- Managed Cloud Workload Protection (MCWP) = An MDR that is solely focused on providing managed monitoring and threat detection over CWP platforms (cloud-native services, VMs, and containers).
All of the EDR platforms have a heavy focus on supporting all of these managed services as partners, and have multi-tenant capabilities to allow these services to manage over any number of mutual customers. These partners serve as a funnel for new customers. MSSPs and MDRs are likely to be non-exclusive users of these EDR tools, opting to use whatever tools their own customers already have in place – though might certainly push their favorites into new customers. The IR services, however, might prefer their staff use a specific EDR/XDR tool for their investigation & remediation phases. CrowdStrike and SentinelOne both provide a variety of ancillary services geared for these managed service partners, to help customize rule sets and allow direct control of the underlying endpoints (say, to better observe or help isolate an attack in real-time).
Yet while supporting MDR partners, all these EDR platforms are happy to help ease the SOC burden. They all offer managed threat hunting services over their native platforms, in CrowdStrike Falcon OverWatch, SentinelOne WatchTower, Palo Alto's Unit42. Some also have in-house MDR capabilities over their own native platforms, such as CrowdStrike Falcon Complete and Sentinel One Vigilance Respond. Palo Alto decided to solely rely on outside services for MDR, creating an MXDR partner program that launched in Nov-21.
SentinelOne likes to repeatedly claim they don't compete with partners, which completely seems to ignore their own in-house MDR and the additional DF/IR tier over it. This is obviously is a dig at CrowdStrike, but these attacks just come off as silly. CrowdStrike has an extremely strong standalone DF/IR service – which also happens to serves as a highly-effective funnel into their EPP/EDR platform. CrowdStrike is happy to help SOCs manage many of their services, and beyond their MDR, they added an MCWP service (Falcon CWP Complete) over their cloud protection capabilities during Fal.con in Oct-21, as well as a managed service over their dark web threat intel solution (Falcon X Recon+) that was announced in Jul-21. Yet even with all these competing in-house services, CrowdStrike heavily supports a wide number of MSSP, MDR, and IR partners (just like SentinelOne does), including a new MXDR service from Deloitte announced in Jan-22.
The landscape
Gartner's Magic Quadrant last covered EPP/EDR in May-21. At the time, Palo Alto could not meet the inclusion criteria, due to the "ongoing consolidation of its endpoint platform". (I find that a bit odd, in that their Cortex XDR was first announced in Feb-19. They later released v3.0 of Cortex XDR in Aug-21, expanding it to protect cloud workloads.) Crowdstrike was the overall top leader (as I discount the Windows-centric Microsoft Defender), while Sentinel One rose to the leader board.
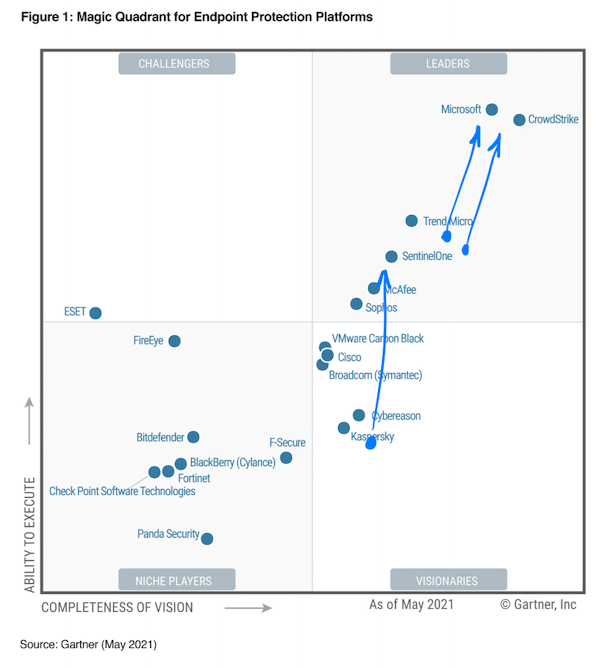
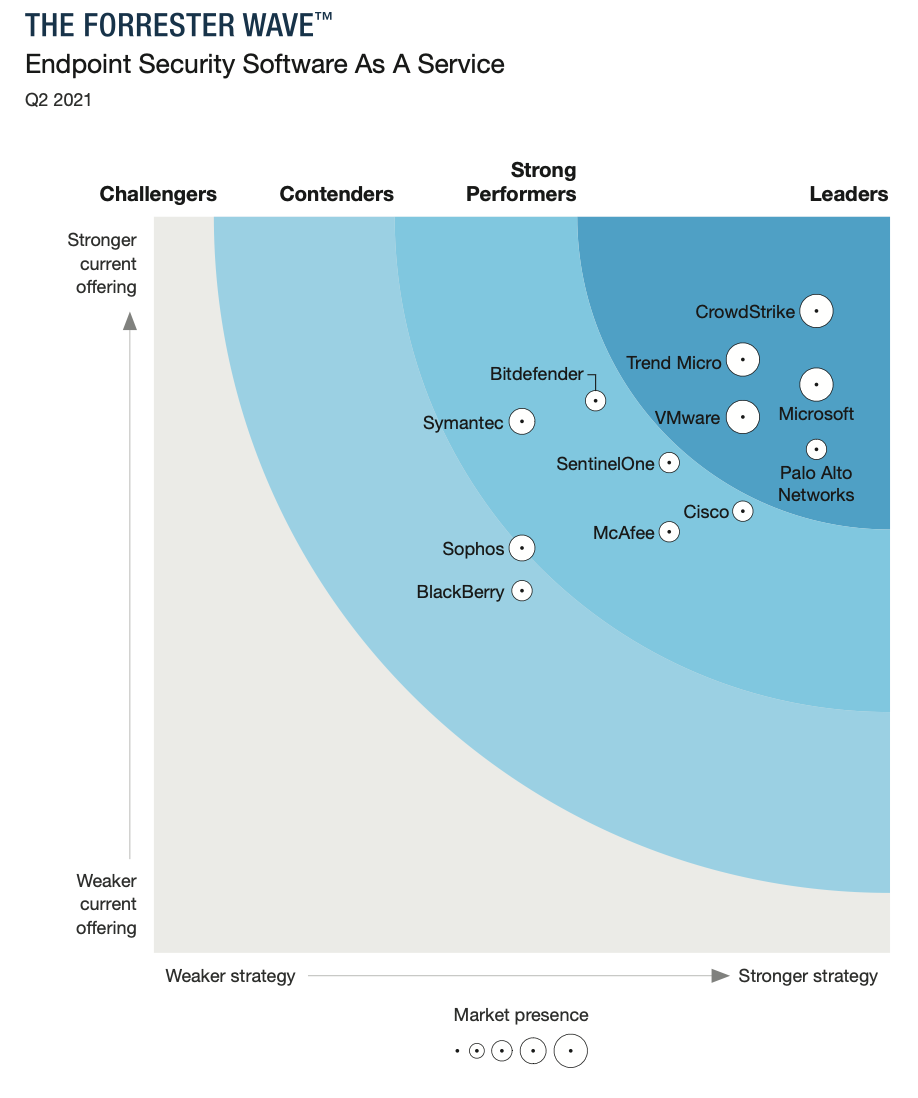
Forrester Wave covered EPP/EDR as well in May-21, and gave a different picture. CrowdStrike was still the top leader, as well as a less strong offering from Palo Alto, but here they have SentinelOne as the rising Strong Performer knocking on the Leader door.
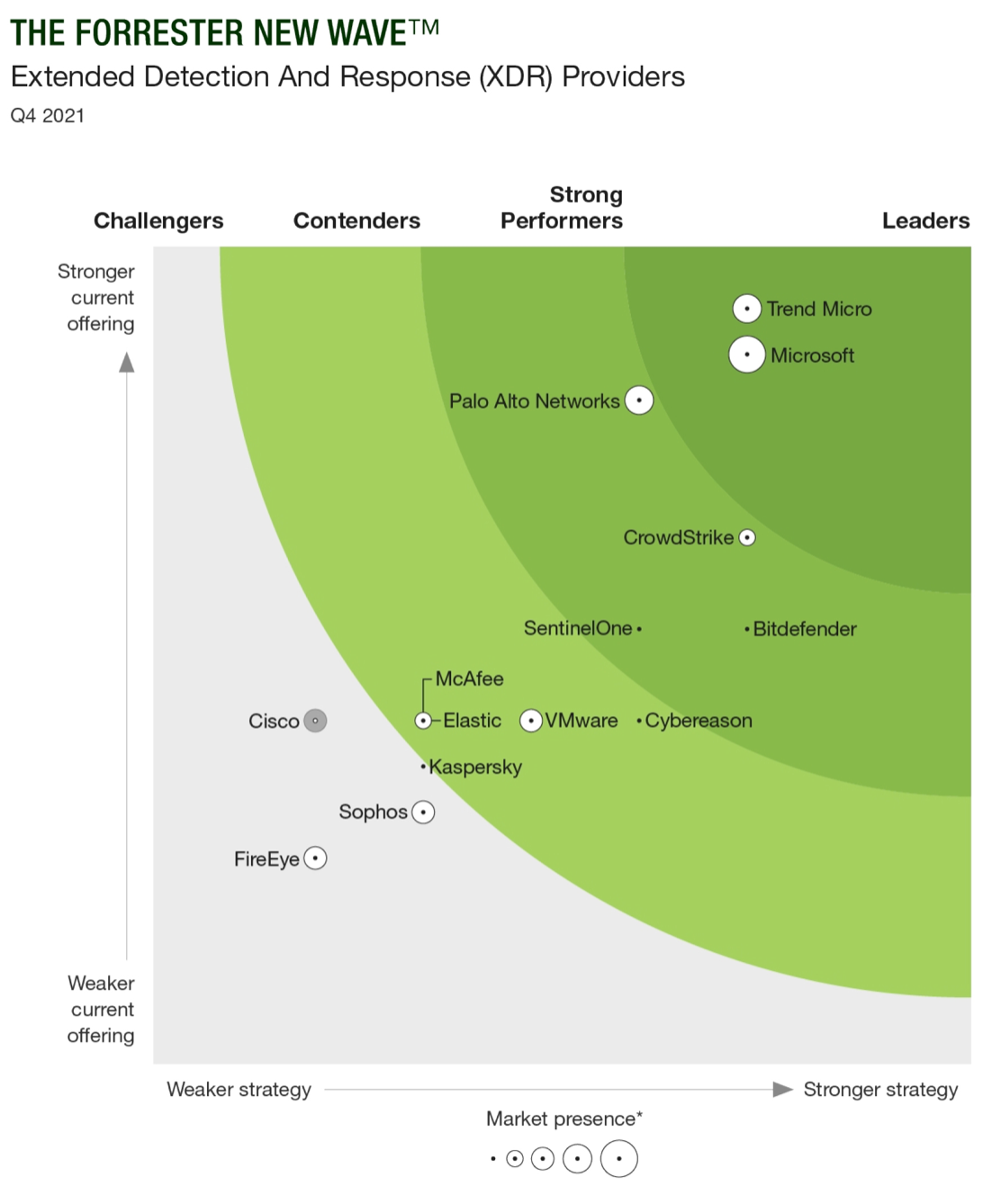
In Oct-21, Forrester New Wave then took a look at how EDR providers have shifted into XDR. But I don't understand how they have so drastically changed their view (especially of market presence) over that half a year since the EDR report. These rankings all seem quite premature. Here Palo Alto and CrowdStrike are both Strong Performers, but with Palo Alto having a much stronger current offering. (I am a bit amused by the fact that as the pioneer of XDR, Palo Alto is not seen as the leader, and how CrowdStrike is shown as having a stronger strategy.) One reason for CrowdStrike's "demotion" was that they had not yet announced their Falcon XDR at Fal.con (premium post), which happened immediately after this report. Another odd shift from the report 6mo prior is how SentinelOne is now a tiny speck on market presence, and barely a Strong Performer. Over them all is Trend Micro (a long-time enterprise security company based in Japan), who is surprisingly strong in all these reports, yet is growing like molasses (grew +9.4% YoY over the past year).
Gartner then put out a Market Guide for XDR in Nov-21 to help organizational decision-makers [and it was a good read, once you understand the acronyms above]. They see XDR as having an immediate benefit to smaller orgs that lack an existing SIEM+SOAR. For larger orgs, they see it as one step in a longer transition towards Zero Trust (SSE and SASE), as enterprises continue the trend of consolidating security products and vendors. They predict that by the end of 2027, 50% of orgs will be using XDR and SASE solutions to reduce security vendors from 5% today – which of course, also causes enterprises to greatly simplify their layers of security, improve their security & risk levels with Zero Trust, and likely reduce their TCO (especially in data storage costs and SecOps personnel) in using these platforms and managed services.
Exit XDR
XDR has become so buzzywordy, that even Palo Alto has decided to now move into other new acronyms for the next evolution (or "revolution" as they stressed in the PR). Palo Alto announced in Feb-22 a new vision they called Extended Security Intelligence & Automation Management (XSIAM), which is focused on making a SIEM be AI-driven and automated. I guess they see these as sitting over their existing XDR and XSOAR capabilities, as a greater XSIAM platform – continuing Palo Alto's desire to be an all-in-one platform over it all.
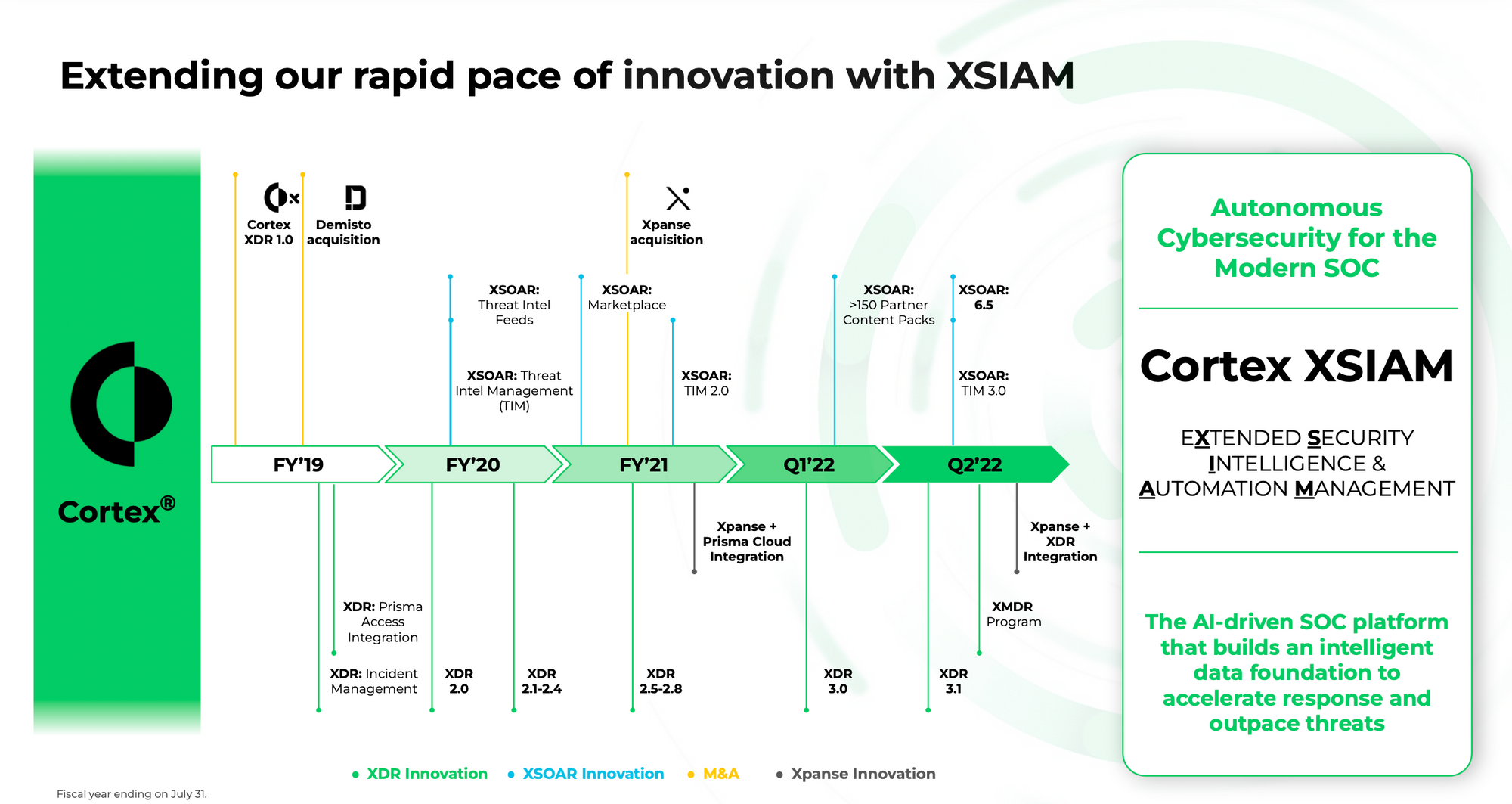
It's interesting to see how the godfather of XDR is already seemingly moving beyond it. But then again, Palo Alto always seems to carve its own path – sometimes the right one (they were way ahead on XDR – yet are not the current market leader), and sometimes the wrong one (they were very late to Zero Trust & SASE, as it was an attack against their core firewall business).
Add'l Reading
For an in-depth piece over the flavors of cybersecurity attacks, see my original series from Oct-19, and subsequent pieces on Zero Trust and SASE Networks.
- Flavors of Security (Oct-19) explained the types of cybersecurity attacks & solutions, and how Zero Trust emerged to provide a better solution.
- Flavors of Security - Hypergrowth! (Nov-19) covered what I look for in cybersecurity companies, with specific breakdowns of Okta, Zscaler, CrowdStrike, and Elastic.
- What is Zero Trust? (Jun-21) covered the next-gen of network security over enterprise user access to apps.
- What are SASE Networks? (Sep-21) covered the next-gen of enterprise networking-as-a-service.
This was the first "explainer" post that kicked off a multi-part series covering XDR (premium post) in Mar/Apr-22 over CrowdStrike and SentinelOne. The series dove into Palo Alto's evolution into next-gen security (XDR, Cloud Security, and Zero Trust & SASE), how EPP/EDR platforms like CrowdStrike and SentinelOne shifted into cloud security & XDR, a deep look at their acquisitions (Preempt, Humio, Scalyr, Attivo) in that journey, and a final comparison. Sign up to premium to read the more in-depth coverage!
- muji
