Let's close out Cybersecurity Month with a two-part deep dive on CyberArk, its major transitions, and its evolution in the Identity Security market. This will be of interest to direct competitors like Okta and Microsoft, as well as next-gen security companies in the Zero Trust ecosystem like Google (acquired Wiz), Zscaler, Cloudflare, Palo Alto, CrowdStrike, SentinelOne, and Rubrik – especially those providing ITDR and Zero Trust access to infrastructure.
Join Premium for insights like this every week across AI & ML, Data & Analytics, Next-Gen Security, DevOps, SaaS platforms, and the hyperscalers. I've recently covered Rubrik's Q1 earnings and market shifts, Samsara's Q1 earnings, NVIDIA's GTC and Q1 earnings, Axon's Q1 earnings and market shifts, and looked at rising Federal headwinds across NVIDIA (China AI chip ban), IoT stacks like Axon & Samsara, and cybersecurity platforms like CrowdStrike, Zscaler, Palo Alto, Cloudflare, CyberArk, Okta, & Rubrik.
In Part 1, let's look at how the Industry Security market has evolved, how Okta stumbled (letting competitors catch up), and CyberArk's evolution and major transitions. Part 2 will be a deep dive into CyberArk's financials and products.
- CyberArk is a long-time Privileged Access Mgmt (PAM) provider that underwent some significant turmoil in FY20-22 as they shifted from license to subscriptions and into managed SaaS. Top and bottom lines were heavily impacted over that time, but both have greatly improved over the last year.
- At the same time, they were also morphing their platform from their core PAM into a broader Identity Security platform by adding in IAM, IGA, CIEM, and ITDR features – positioning themselves as a much stronger player going forward.
- Meanwhile, Okta was so overly busy integrating its massive acquisition of Auth0 in customer identity (CIAM) that it took years to fully release its platform shifts into adjacent areas of IGA and PAM that were first announced in 2021. This gave CyberArk a big opening to move towards Okta faster than Okta could move towards them.
Part 1: Identity Moves
- Identity landscape
- Okta's stumbles
- CyberArk basics
Part 2: Vaulting to success
- A walk through CyberArk's financials
- Product shifts & acquisitions
- GTM shift
- The rise of machine identities
- Final thoughts
Also, see my past next-gen security explainers (all free):
- Flavors of Security (Oct-19) covered a variety of security attacks and solutions being around them.
- What is Zero Trust? (Jun-21) covered the big push towards modern Zero Trust for secure access to enterprise apps.
- What are SASE Networks? (Sep-21) covered how Zero Trust features were part of a greater expansion of enterprise network security.
Identity landscape
I have found the identity side of the cybersecurity industry to be underwhelming as an investor, which is a surprise given how critical identity is to security in general – especially as the industry has been marching towards Zero Trust, SASE, and XDR [paid] since 2020.
Most identity players were long focused on becoming best-of-breed point products in their specific niche, across IAM (access mgmt), IGA (lifecycle mgmt and governance), and PAM (privileged access). But fast forward to today, these point products have all since shifted into a bundled "Identity Security" platform over all three features (IAM, IGA, PAM), with next-gen features emerging in cloud identity governance (CIEM), real-time threat detection (ITDR), behavioral analytics (UEBA), and posture scanning (ISPM).
A brief history of the Identity landscape over the past 10 years:
- Legacy on-prem IAMs like ForgeRock, IBM, Oracle, MicroFocus (acquired by OpenText), and CA Technologies (acquired by Broadcom) were slow to morph into cloud & SaaS.
- Microsoft adapted its widely used Active Directory to the cloud, then began to shift into wider system support (beyond Windows) and broader Identity Security.
- Cloud-native IAM (SSO, MFA, & workforce mgmt) solutions like PingID, Okta, OneLogin, Duo (acquired by Cisco), and JumpCloud emerged as disruptors to those legacy solutions, but have all since shifted into broader Identity Security.
- Sailpoint, One Identity, and Saviynt started in IGA, and have also since shifted into broader Identity Security.
- CyberArk, Delinea, and ARCON started in PAM, and have also since shifted into broader Identity Security.
- Some identity players, like Okta and Microsoft, are also moving into the customer side in CIAM, to provide developers with authentication services that are then embedded into SaaS apps.
- As this broader shift has been taking shape, Zero Trust partners like CrowdStrike, Palo Alto, Zscaler, Wiz (Google), and SentinelOne, have started encroaching on IAM by adding cloud identity governance (CIEM), real-time threat detection (ITDR), behavioral analytics (UEBA), and identity posture scanning (ISPM) features in their own XDR and CNAPP platforms – which all sit over and monitor existing IAM solutions.
But despite all the consolidation shifts into broader Identity Security, it has been hard to compete against the king here. Microsoft has long dominated in Identity due to the near-universal use of Active Directory (AD) within enterprise Windows networks, which is used to track every user and service account across an organization, what group roles they belong to, and what access rights they have.
That, in turn, has morphed into Azure AD, a managed cloud service that extends their IAM into cloud services and their Office 365 productivity suite, and can be integrated together with on-prem AD instances in hybrid environments. In mid-2023, their entire identity platform was re-branded as Microsoft Entra [paid], with Azure AD becoming Entra ID. They've extended their dominance into a broad suite of Identity Security products – not only in Entra, but also some of the PAM-like features across its Purview (data governance) and InTune (endpoint mgmt) product lines as well.
A lot of M&A
There has been a lot of turmoil in the market given all these competitive shifts, as cooperative partnerships turned into competitive ones, and poor product roadmaps and execution caused many identity players to falter. Several competitors have been gobbled up by major PE firms (Francisco Partners, Clearlake, and Thoma Bravo) over the past several years, as well as a huge amount of M&A as security platforms bolted on features.
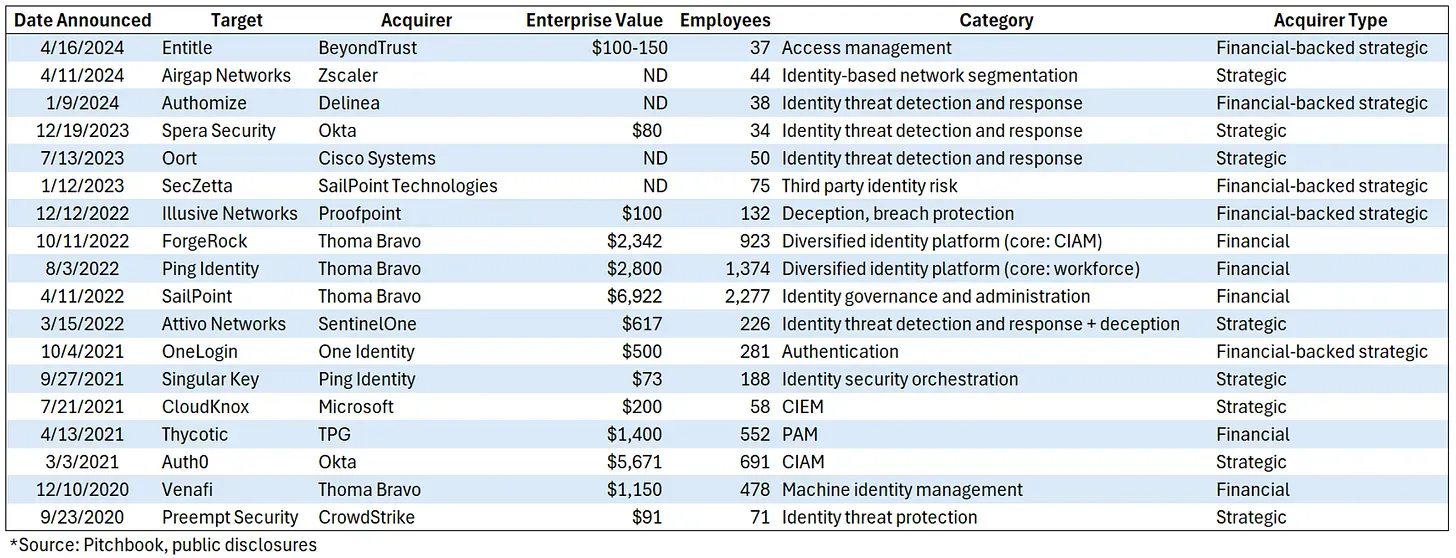
- Francisco Partners owned One Identity (as part of Quest Software, spun out from Dell in 2016), an IGA that acquired its way into PAM in 2018. In late 2021, they merged it with OneLogin to add IAM to its platform – and was all soon quickly sold off to Clearlake. They have treaded water in industry minder reports for PAM and IAM since.
- Francisco Partners also merged two PAMs when it acquired Bogmar from Thoma Bravo in Apr-18, and soon merged it with BeyondTrust. Clearlake decided to also invest in the company in mid-2021. They have remained a leader in PAM since.
- Thoma Bravo acquired Sailpoint in Aug-22, who by then had shifted from IGA into broader IAM, PAM, and CIEM. They are finally starting to show up in IAM industry reports as a contender.
- Thoma Bravo later acquired Ping Identity in Oct-22, and merged it with ForgeRock in Aug-23 to combine their strengths (across cloud vs on-prem, IAM vs IGA, and different geos). Ping ID remains a top leader in IAM.
There are now very few identity players left in the public market – after Thoma Bravo took several major IAM competitors private over 2022-2023, only Okta and CyberArk remain as the pure-plays, alongside conglomerates like Microsoft, Cisco (acquired Duo for IAM), and Broadcom (acquired CA Technologies for IAM), as well as legacy players like Oracle and IBM. Network security player Fortinet also added its own native IAM and PAM modules into its consolidated security platform – but these features are more to upsell to existing networking customers rather than to directly compete with leading IAM vendors. Surprisingly (or perhaps not, given how poorly Fortinet has done here), Palo Alto hasn't moved into identity at all in its big security consolidation play.
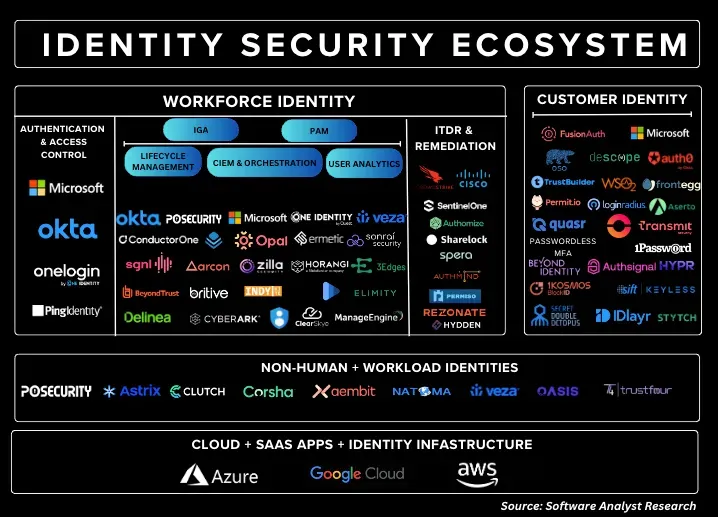
While it seems like a lot of identity players are sputtering after a period of huge M&A and consolidation, there are also plenty of startup point solutions ready to emerge. [See that industry ecosystem diagram above!]
Okta's stumbles
Of all these players, I watched Okta [paid] the closest, owning it in 2018-2021 as the cloud-native IAM experienced hypergrowth from being at the nexus of the Zero Trust & SASE ecosystems. However, as that growth began to wane, they wasted a lot of time and effort merging with customer-identity provider Auth0, when I preferred they move deeper into a broader platform that included IGA and PAM.
As covered before, Okta has given me a number of disappointments [paid] over the years, and wasn't looking much better in my last checkup [paid] in Jun-23 and their customer support breach [paid] in Nov-23. Their "greatest hits" of questionable product moves include:
- Okta announced it was acquiring Auth0 in Mar-21. After it closed in May, it then fumbled around for more than a year on how to best integrate the CIAM into its existing Okta Customer Cloud product and GTM engine. (See the "Auth0 Acquisition" section of Okta Moves [paid] for my thoughts at the time.) This caused massive rifts in top mgmt that eventually led to an exodus in late 2022 and early 2023.
- Right as that acquisition was closing, Okta finally announced they were moving into IGA in Apr-21, a long overdue move that I was hoping to see a year and half earlier. This then went GA a year and a half later in Aug-22 – so took them 3 years to get where I envisioned them moving. This shifted them into competition with Sailpoint and Saviynt.
- At the same time, Okta finally announced they were moving into PAM, after completely ignoring the PAM-like features acquired in ScaleFT in 2018. This finally went GA two and half years later in Dec-23 – so took them 4 years to get where I envisioned them moving. This shifted them into competition with CyberArk, BeyondTrust, and Delinea.
- Okta finally decided they needed to move deeper into real-time threat detection over IAM – an area Zero Trust partners had been encroaching into for years. They finally announced an ITDR product in Oct-23 that went GA in Aug-24. This was an evolution of their earlier Risk Engine, and integrates with several Zero Trust partners across XDR, CNAPP, and SSE – including Zscaler, CrowdStrike, Netskope, Palo Alto, Cloudflare, Rubrik, and Trellix. They will be enhancing it with features from their acquisition of Spera Security in Feb-24.
- They also finally announced a new ISPM posture scanner over external IAMs this Jul-24, another area that Zero Trust partners were encroaching on.
- In addition to those moves, Okta is also moving from enterprise into the consumer-side. They acquired Uno in Oct-23 to add a password manager app. This turned into Okta for Personal, which was announced in beta in Feb-24, and just went GA this month. This isn't a standalone consumer product (at least, not yet) – it more seems a way to have their existing workforce users using their SSO be able to separate business from personal.
I feel that Okta is trying to move in a lot of directions at once. They have had a huge amount of mgmt turnover since their Auth0 debacle, with their President of WFO and CRO leaving in disgust in late 2022 (to go to HashiCorp and Klaviyo) after the acquisition was fumbled, and their checked-out cofounder COO finally departed in late 2023 after a year-long sabbatical. While his role was filled by the CEO of Auth0, disappointingly, they promoted from within to fill other vacant critical roles, including CRO & CMO in Nov-23, and key GTM supporting roles in Feb-24. The mgmt churn hasn't stopped – most recently, their CTO left in July to go to DocuSign.
Besides these disappointing product moves, overall slow rate of innovation, and high degree of mgmt churn, don't forget my disappointment with their security incident handling across a number of indirect breaches over 2022 [paid] and 2023 [paid]!
As I stated in my Nov-23 take [paid] after their breach, Okta had a lot of tailwinds they should have ridden:
- Okta was at the nexus of security as castle-and-moat security morphed towards Zero Trust and SASE, where identity is the core. These are all areas that industry minders foresaw strong growth – however, Okta lost momentum as it floundered about with Auth0.
- They were the continued leader in IAM (over workforce) and CIAM in Auth0 (over SaaS apps) per industry minders, but were extremely slow in moving deeper into a broader Identity Security platform with IGA and PAM. They never took full advantage of its ScaleFT acquisition (Zero Trust access to infrastructure).
- Their trailing competition was in turmoil. As noted above, Thoma Bravo acquired 3 of their major competitors, across PingID & ForgeRock merger (IAM merger) and Sailpoint the year prior (IGA moving into IAM). These companies are now going to concentrate on cost-cutting and righting the ship instead of being a disruptive force. I don't worry about disruption coming from these PE rollups going forward.
I really want to find a good investment in the Identity space. Okta's slow product roadmap gave other players like CyberArk (in PAM) and Sailpoint (in IGA) an opportunity to move towards Okta (in IAM) faster than Okta moved towards them. So it's time for a look at CyberArk.
CyberArk (CYBR)
CyberArk was founded in 1999, went public in mid-2014, and has been a top leader in PAM ever since. Privileged Access Mgmt (PAM) products are used by ITOps staff to manage and govern the administrative (sysadmin) access and permissions across an organization's on-premise and cloud systems. PAM is a security and compliance/audit tool to tighten & track administrative access, and typically has advanced features like automated password rotation and one-time passwords created on the fly for time-limited access (just-in-time access or JIT).
CyberArk is based near Tel Aviv, Israel, but has offices globally, including a US HQ outside Boston. This makes them a foreign company that reports via a 20-K annually. They got a new CEO in Apr-23 by promoting the COO, after the founding CEO retired after over 17 years, stepping down from day-to-day mgmt to become Executive Chairman. The newly promoted CEO was hired originally as CRO in 2019, and rose quickly to COO in 2020. They later added a new CMO, Chief Product Officer, and CRO over 2022, and a replacement COO was finally hired in early 2024.
They have long relied on an ecosystem of partners (listed here) across VARs, MSPs, and cloud marketplaces to sell their products, and now mgmt seems especially focused on channel going forward as they shift platform and GTM [more on that in a bit]. And like Okta, they also created an ecosystem of tech partners (called the C-cubed Alliance) in order to have a huge number of out-of-the-box integrations to other security tools and SaaS apps – including CrowdStrike, Proofpoint, Palo Alto, Zscaler, Sailpoint, Okta, Microsoft AD, MS365, Google Workspace, and UiPath.
Pure-play PAM competitors include BeyondTrust, Delinea, and ARCON (all private), but as mentioned above, all major Identity Security players (like Okta, Microsoft, Sailpoint, and PingID) have since added PAM capabilities to their platform. Besides that crowded market of Identity players, other security providers have also moved deeper into PAM-adjacent tools for secure access to infrastructure, including:
- SSE/SASE providers like Zscaler, Palo Alto, and Cloudflare (including their highly related acquisition earlier this year of BastionZero) allow tunneling securely into infrastructure
- Zero Trust startups like Teleport and Twingate
- Hashicorp also moved deeper into Zero Trust access with its Boundary product for secure infrastructure access for developers
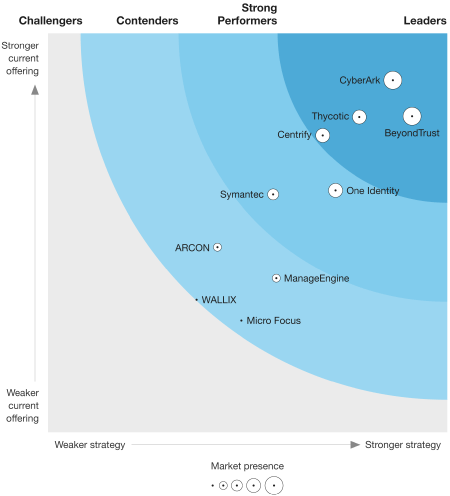
The PAM landscape is mature and has not changed much over the past few years. Even though IAM/IGA providers like Okta, PingID, and Sailpoint have moved deeper into PAM, they aren't showing up on industry minder reports yet. Like in IAM, there has been some M&A activity here – Delinea was created out of the merger of Thycotic and Centrify by PE firm TPG Capital in Apr-21, combining 2 of the top secrets mgmt and PAM players.
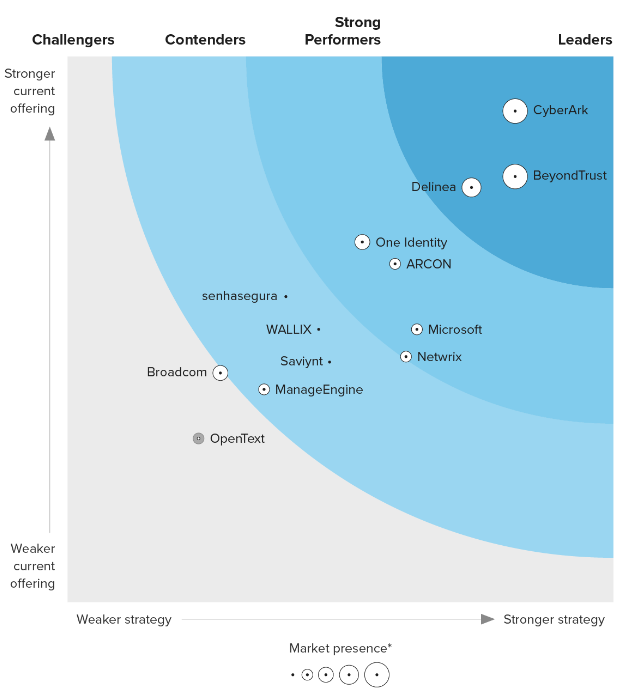
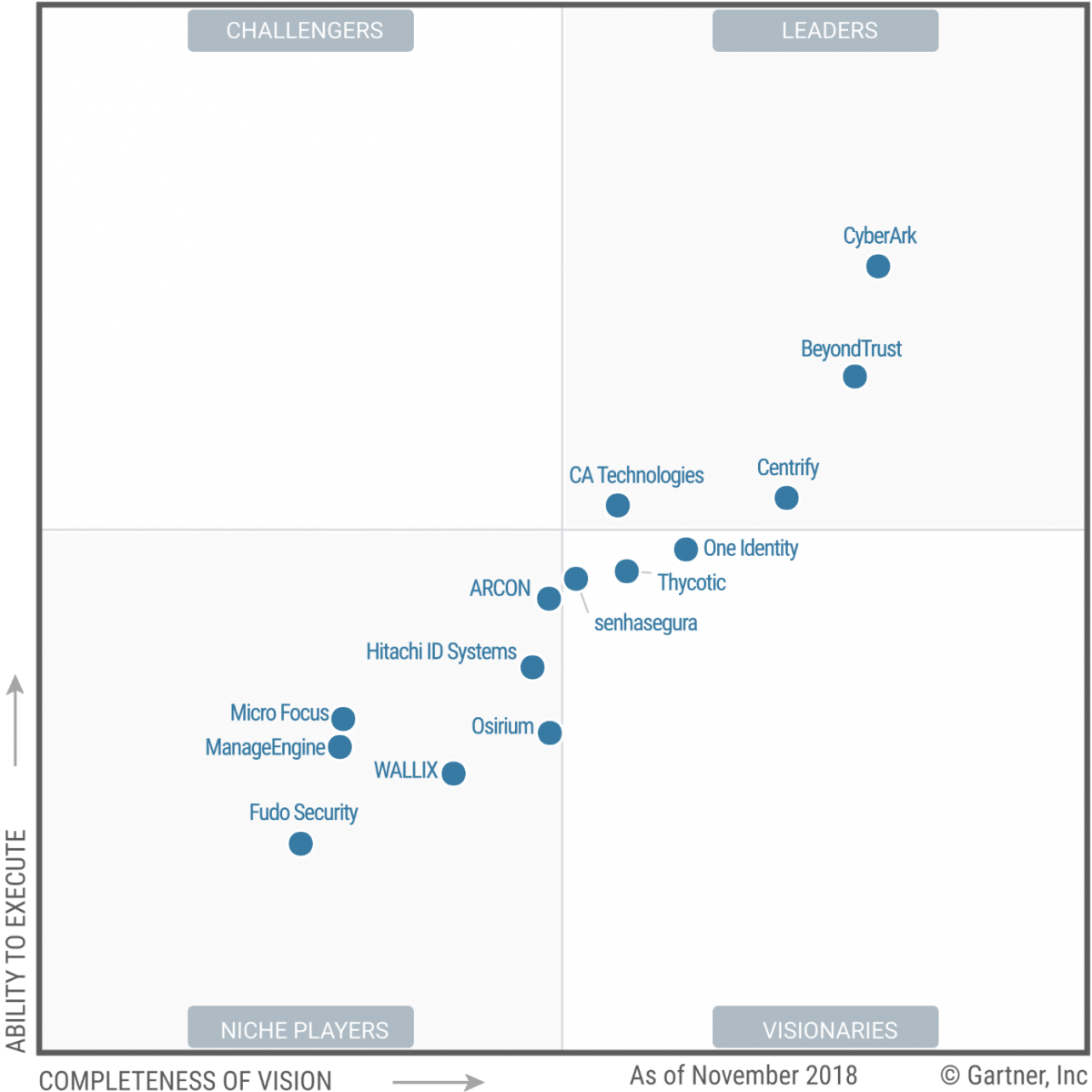
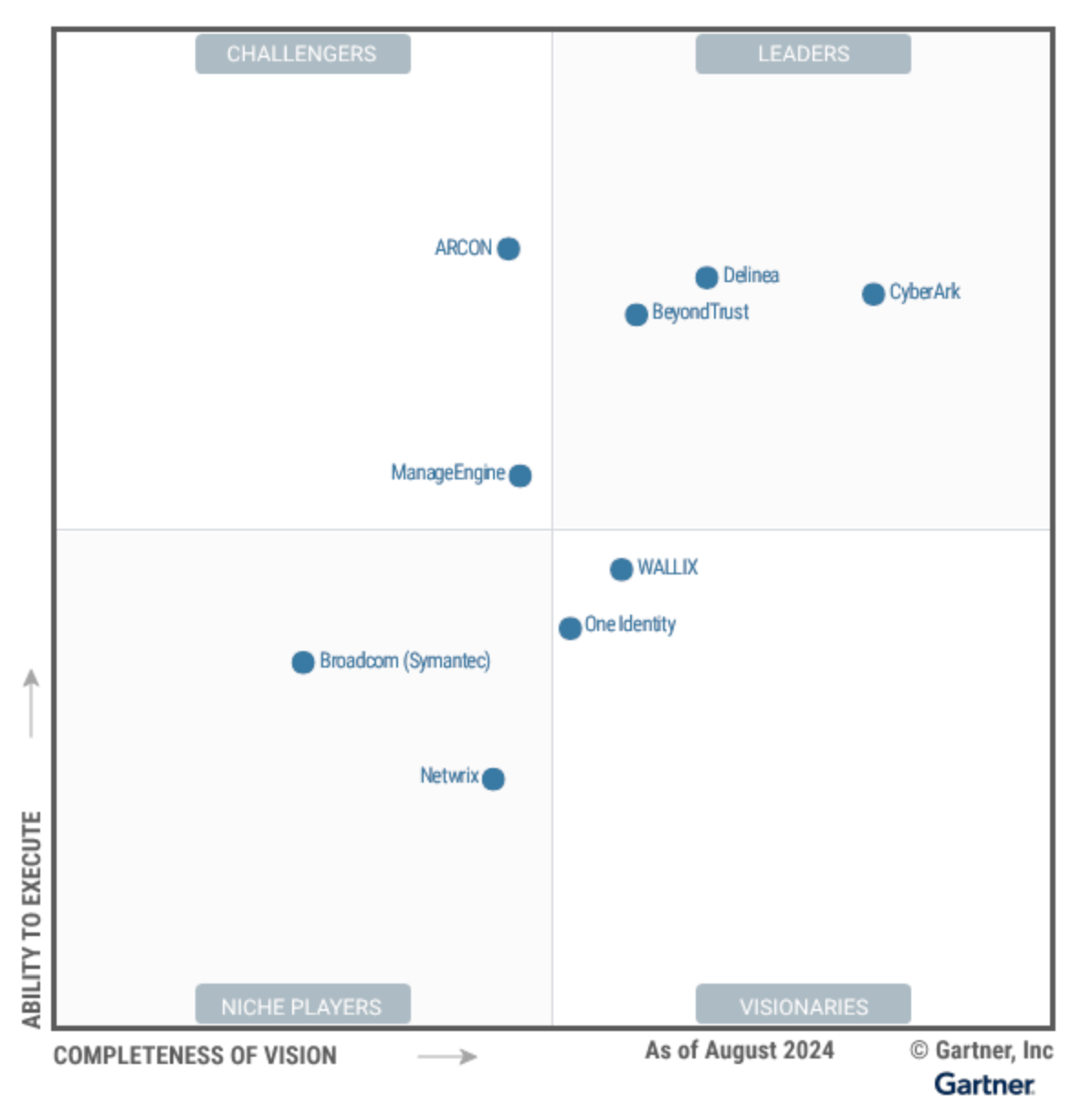
Some features of PAM could ultimately be disrupted by Zero Trust access in SSE platforms (like secure browser and JIT Zero Trust access to infrastructure). However, as we've seen with Okta, broader Identity Security platforms like CyberArk seem well-suited to work tightly with Zero Trust partners across XDR and SSE/SASE, instead of competing with them. (Both CrowdStrike and Zscaler are partners.)
3 transitions
The past few years of CyberArk's story greatly remind me of Splunk's [paid]. They both had to transition their software from on-prem to cloud as they shifted their business model from license to subscription (into self-hosted and SaaS). When I first looked at CyberArk in 2020, the financials were a mess (revenue stagnant, profitability retreating) due to this, and that continued for a few years as they worked through this transition in FY20-FY22.
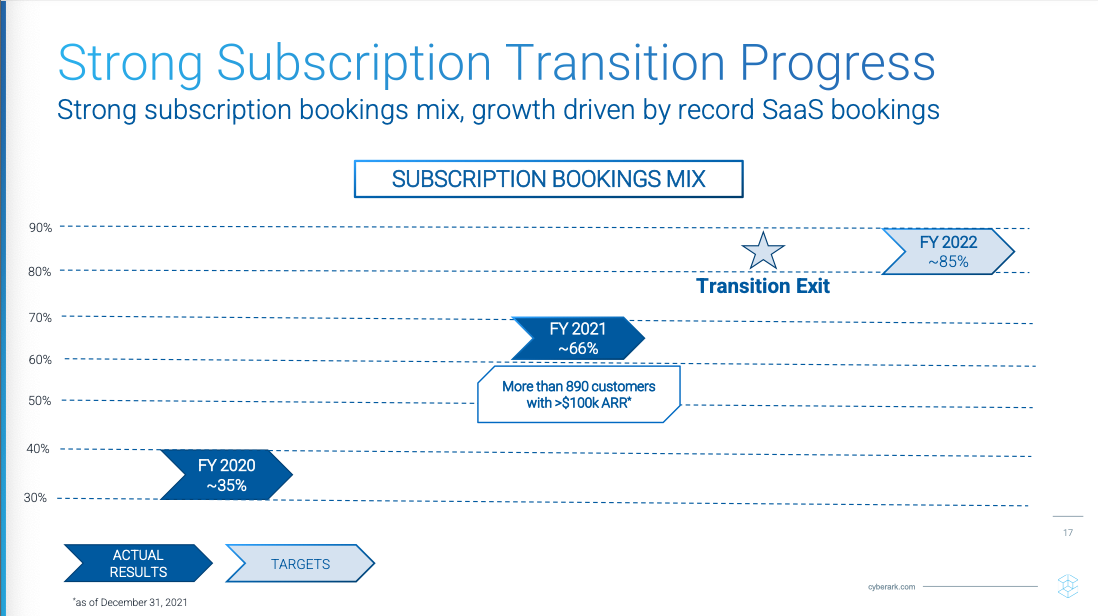
From an October 6-K filing: "Prior to 2020, we primarily derived our revenues by licensing our cybersecurity software, selling maintenance and support contracts, and providing professional services. We began executing our transition to a subscription business model in early 2021, and, in 2023, we reached our transition goals of selling primarily through subscriptions, including both SaaS and self-hosted subscriptions.
However, the analogy with Splunk breaks down from there. Splunk's big issue was that its cloud & subscription transition coincided with the rise of disruptors in observability like Datadog and Dynatrace. Datadog was a cloud-native solution that proved observability point solutions could be unified into a single platform (infra metrics, logging, and APM), and other observability players like Dynatrace and New Relic followed suit. Splunk ultimately found itself behind those disruptors, and also wasted time trying out ideas that didn't catch (stream processing). [I covered Datadog heavily in the Premium service.]
Unlike Splunk, CyberArk really didn't have to deal with a rising disruptor in the mature PAM market during this time (and Okta was busy trying to digest Auth0). Since the clear trend in identity security was moving towards bundled platforms, CyberArk then added a third transition – expanding its point product (PAM) into a broader Identity Security platform. They had already been using acquisitions to help bolster their PAM product, but it also allowed them to move quickly into other areas of identity security, such as IAM, IGA, CIEM, and ITDR.
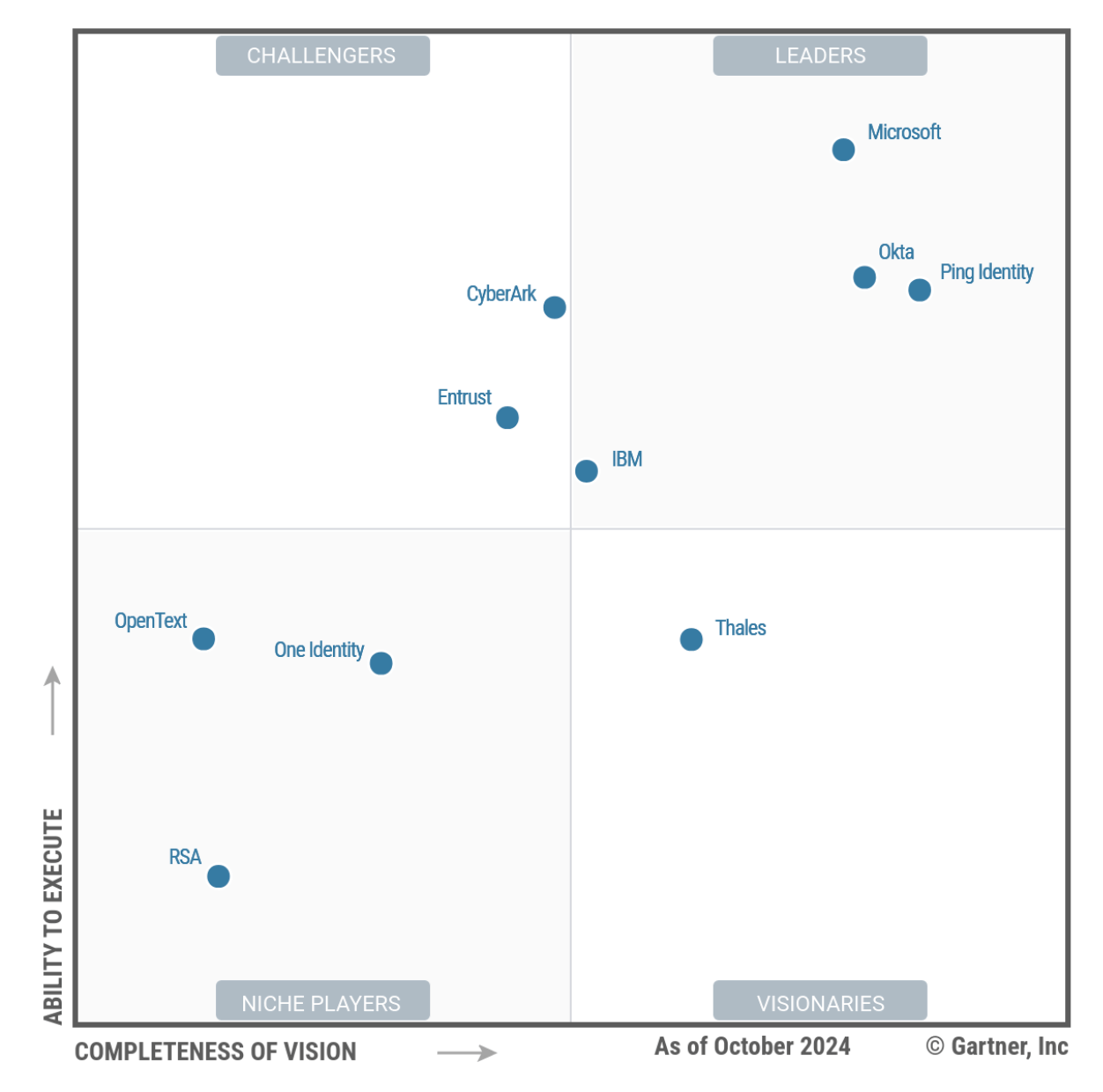
After moving deeper into IAM in 2020, they are finally rising in industry reports. The Forrester Wave for IAM in Q124 showed them as a leader, moving above more established players in that space like Ping ID, Sailpoint, and IBM.
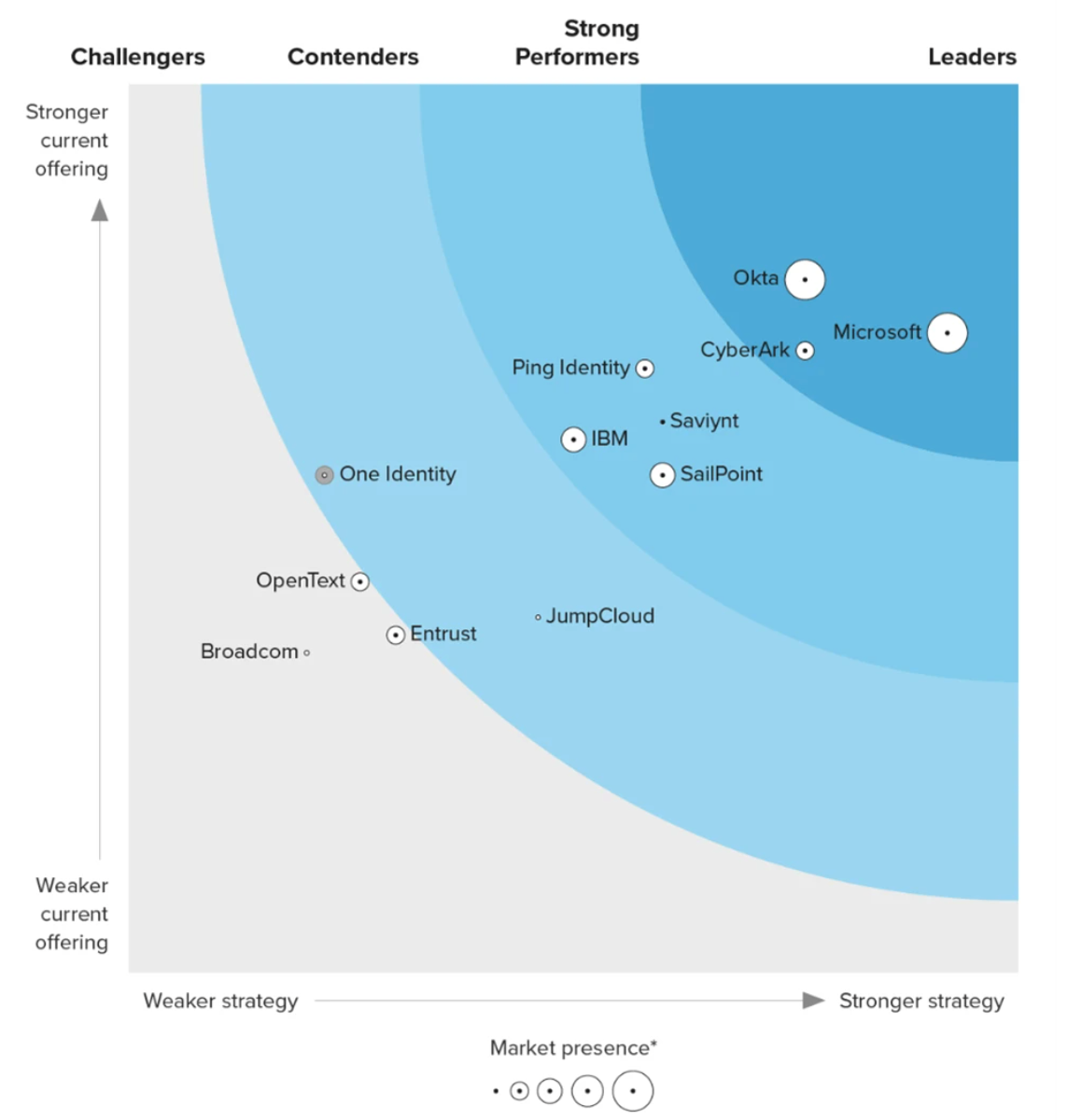
However, in Gartner MQ for IAM, they've been bouncing around the periphery of the leader quadrant.
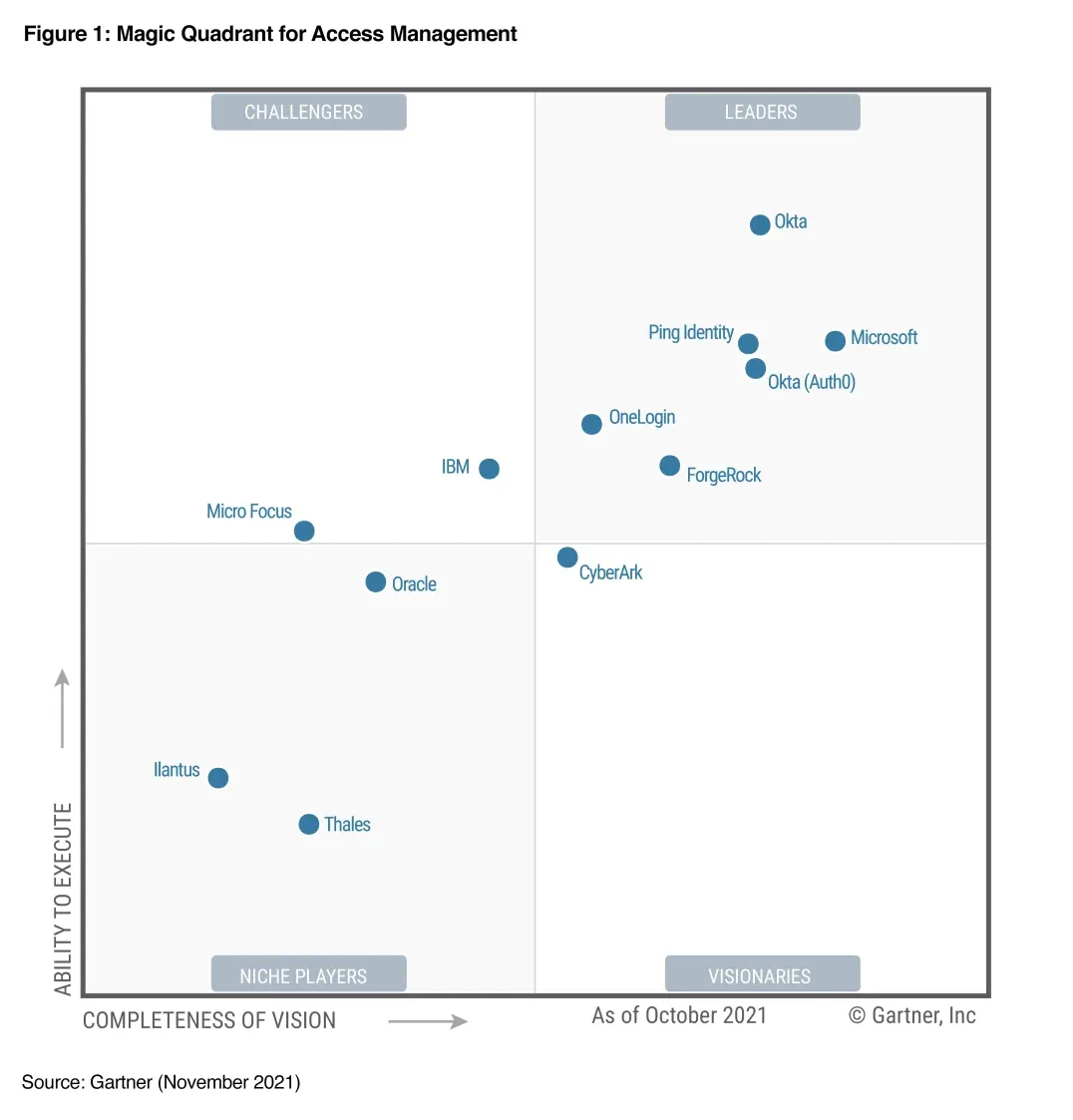
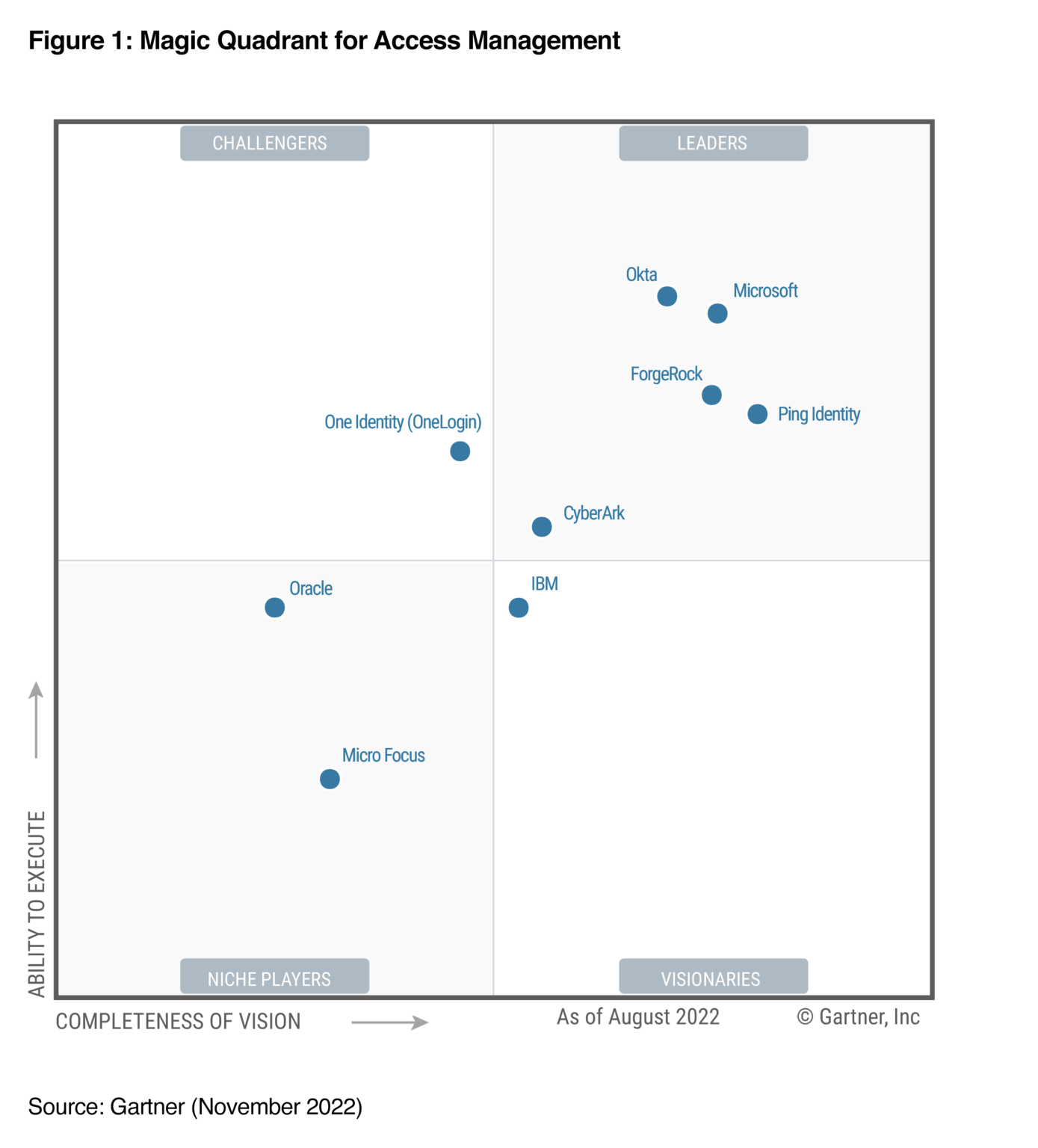
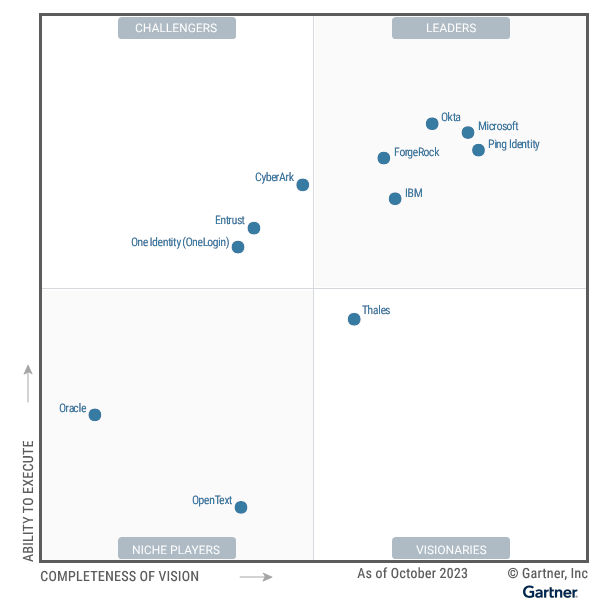
I'd like to see them advance into the Leader quadrant in the coming MQ report next month, and start to show themselves as a rising disruptor to Okta and Microsoft. CyberArk needs to continue to educate the market on its IAM/IGA features that expand it beyond PAM & Secrets Mgmt features. Hopefully, their GTM shift into personas will help with that [more on that in the next piece].
Add'l Reading
- Francis of Software Analyst covered the Identity Security ecosystem back in May.
- See my HashiCorp writeup for more on their Vault product for secrets mgmt and PAM, as well as their Boundary product for secure Zero Trust infrastructure access.
- Okta Moves covered Auth0 and their shifts into PAM/IGA. Read up on Okta [paid] and how their execution has faltered.
- See Microsoft's Security Shifts [paid] for its Entra moves, as well as their AI push into Security Copilot [paid] . They don't really have a dedicated PAM product in Entra, but parts of Purview and InTune provide PAM capabilities, and they are adding in SSE capabilities for Zero Trust secure access.
- I'm surprised Cisco Duo hasn't moved from IAM into IGA and PAM too, though did acquire Oort in Aug-23 to add ITDR. They must be busy moving into SSE and ingesting Splunk (SIEM) [paid].
- I just covered the XDR [paid] shift into identity, as well as the CNAPP [paid] and SIEM [paid] markets. And look back at the XDR series [paid] in 2022, which covered how CrowdStrike and SentinelOne moved into ITDR [paid] in 2020 (and ISPM posture scanning, before it was called that).
Next up, part two: a deep dive into CyberArk.
-muji
