I first bought into Okta in Oct-18, and have followed it extensively since. This company is so well positioned from its technology stance, but the financials tell a slightly different story -- it has been slowly leaving its hypergrowth behind, and is now entering its next phase around profitability. Over the past year, I have been reducing my position as the top-line growth has waned, finally exiting the position this past May. Beyond (or, perhaps, behind) the faltering top line growth, I see a few platform and product concerns that I wanted to detail further. Yet at the same time, I see a lot to be excited about as Zero Trust is more adopted.
A quick stroll through my prior coverage:
- In Apr-19, Okta was my first tech deep dive, driving into what identity means in security. Later in Oct-19, Okta was one of the top 4 companies I focused upon in my Flavors of Security series, and the next wave of hypergrowth within the cybersecurity industry. At the time, I predicted Okta would move into IGA (governance), UEBA (behavioral analytics), PAM (Zero Trust access to servers), and IAP (Identity Access Proxy, a form of Zero Trust over web apps). Okta has had varying degrees of success on those, which I believe has ultimately lead to its declining top line.
- In Apr-20, I uncovered a few insights from Oktane20. At the time, they seemed heavily focused on adapting their platform into becoming building blocks around identity workflows (with Platform Services, and no-code Workflows), which is great for improving the stickyness of the platform, but utimately isn't resulting in new revenue streams. They also added device risk as a signal in Threat Insight, via their expanded EPP/EDR partnerships. Then, a few months later in Jul-20, they deepened a cross-cutting Zero Trust security partnership between CrowdStrike, Netskope (for SWG & Zero Trust) and Proofpoint (email & human security).
- More recently, in Jun-21, I covered Okta as a picks-and-shovels play in the Zero Trust ecosystem, detailing how they are further expanding their Threat Insight into a Risk Engine that other security partners can both tap into and enrich. Also in Jun-21, I covered how the White House EO is giving a green light to Zero Trust [premium post] - which Okta is well positioned for (at FedRAMP Moderate).
[This was originally written in Jul-21. Since then, they've released Q222 earnings, plus had an event called Okta Showcase 2021 in Oct-21 to further discuss the combined Okta + Auth0, with an add'l Investor Q&A session.]
Okta has always been a major gateway for users to access enterprise SaaS platforms. It has a unique vision into the usage patterns over enterprise SaaS, which it presents every January in a report called Business @ Work. Via its Integration Network, enterprise customers can more easily manage access to every SaaS service they utilize through a single sign-on (SSO), can tie into Okta's platform further to not only track users and access rights (Universal Directory), but can also automate the provisioning of users and changing of access rights as the workforce adjusts (Lifecycle Mgmt).
As mentioned in my recent Zero Trust writeups, it has major tailwinds from being a vital picks-and-shovels play to Zero Trust & SASE Network platforms. This alone will keep it highly successful for a long time, as the platform provides a vital need for this new security paradigm. And Zero Trust is only becoming more and more important, as shown in the recent US Federal Executive Order, and the constant barrage of news covering breaches and attacks. However, I believe some of Okta's feature set is beginning to be sidestepped by its Zero Trust partners, such as how those platforms can create their own single sign-on interfaces, where a user first establishes identity (via IAM), and can then access the various services they have rights to under Zero Trust (potentially side stepping Okta's SSO).
Over the past year, CrowdStrike has positioned itself as a cooperative partner to Zero Trust platforms, with an integration platform called Zero Trust Assessment (ZTA) announced in Oct-20, and then a further deepening of its partnership with Zero Trust partners like Zscaler and Cloudflare in Mar-21. In comparison, Okta doesn't quite seem to know where it wants to go with Zero Trust. It acquired ScaleFT in Jul-18 for its Zero Trust capabilities across 2 products: Access Gateway (Zero Trust for app access) and Advanced Server Access (Zero Trust for infrastructure access). I once noted how odd it seemed that Okta didn't embrace the term "Zero Trust" in its marketing of those 2 products, while ScaleFT clearly did. Does Okta want to be a vital picks-and-shovels component to Zero Trust partners, or enter this market itself? Access Gateway, in particular, happened to directly compete with partners like Zscaler ZPA and Cloudflare Access. But ever since it released, that product does not seem to be in the limelight at all, leaving Advanced Server Access to be the only focus. Up until now, I couldn't tell what Okta wanted to do these products.
A Wake Up Call
Okta has always been the dominant leader in IAM (Identity Access Mgmt), having been the clear leader in Gartner's Magic Quadrant for several years. However, as of Nov-20, the newest Gartner Magic Quadrant for Access Management showed that Okta no longer dominated the pack. Microsoft now ranks as top leader, while Ping shows up higher on ability to execute.
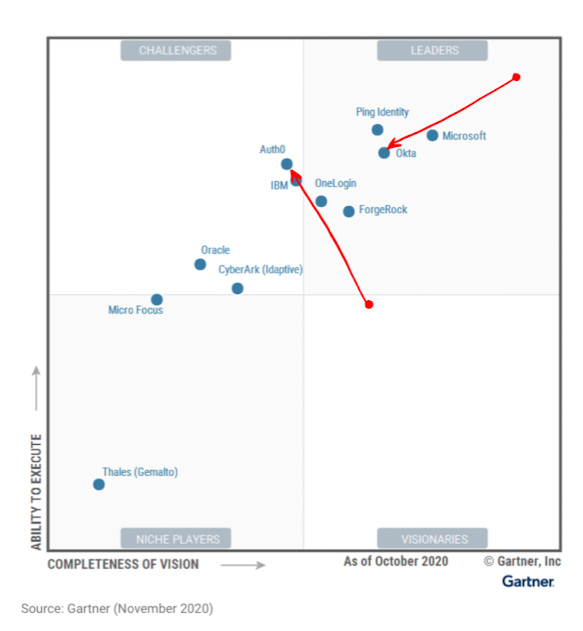
It appears that Microsoft and Ping are starting to erode its leadership while undercutting it on pricing. The CEO had a good response thread on Twitter that they were paying attention, and taking the criticisms seriously.
Feedback is a #1 priority for a CEO, especially when you’re in an enviable position like @okta. And this year, we got some tough feedback from the Magic Quadrant. We've been a leader in every identity MQ, but we have a lot to learn from this year’s.
— Todd McKinnon (@toddmckinnon) December 4, 2020
Gartner's negatives for Okta include:
- Lacking some fuller features like governance [addressed with a newly announced product line in Apr-21]
- Not geographically diverse outside of North America [somewhat addressed with Auth0 acquisition announced in Mar-21, plus their continued expansion of headcount internationally]
- Their Customer IAM (CIAM) product is more simplistic [addressed with Auth0 acquisition]
- Pricing is "well above average"
A concern I have had in my thesis, and that Gartner agrees with, is how international expansion has not been enough of a focus. It has remained at ~16% of the mix for 2 years, finally bumping to 17% in Q122 this year [as they slowed down so much in domestic sales, that the fairly meager +43% international growth moved it up a percent]. Over the past few quarters, they have been focused on hiring to expand headcount internationally. However, the prior CFO, on his way out the door, admitted to "letting their foot off the gas" in playing the pandemic very conservatively – pulling back on GTM investments, including their international expansion initiatives.
CFO in Q421 earnings call: "I think that the other thing to take into consideration is that early in the pandemic, like a lot of companies, we scaled back our investments. We recalibrated. And I think that as a result of that, we probably in hindsight -- because the pandemic was not as impactful as we thought it was going to be potentially, although we outperformed and are very pleased with our performance, it's possible we could have done even better. And because we're a subscription model, as you know, that's going to weigh on this year's revenues a bit because revenues is really a lagging indicator."
Some interesting conjecture from Gartner in that same report:
- 50% of all IAM will leverage UEBA by 2024 (aka CARTA, or what I prefer to call Continuous Analytics) [Okta is now doing this more fully with improvements to Threat Insights, and now the new Risk Engine announced in Apr-21.]
- At least one IAM vendor by 2024 will introduce a converged offering that includes PAM and IGA [Which didn't take long, as Okta added both as new product lines at Oktane'21 in Apr-21, for eventual release in early 2022.]
Recent Moves
Massive changes have been occurring this year (perhaps spurred on from those criticisms from Gartner), with a major acquisition to strengthen its CIAM segment (tackling both the CIAM and int'l exposure concerns), the continued expansion of headcount internationally, and now entering new adjacent markets (tackling the governance concern) – all while a major revamping of executive leadership is going on.
Okta has been clear about its dreams of being a major security cloud, but my response to its moves of late is mixed. The most important moments so far in 2021 were [and my take]:
- The new Risk Engine API [A strong move into being a threat detection platform that other platforms can tap into. But do those partners want to?]
- The acquisition of Auth0 acquisition [I have mixed feelings, but ultimately results in the top CIAM platform.]
- Entering the adjacent PAM and IGA markets [About time! Much too slow here.]
- New management executives [Overall strong, except the bungling of CFO position]
Risk Engine
I discussed the Risk Engine in more depth before in my earlier Zero Trust ecosystem piece. Ultimately I feel that the Risk Engine is the strongest move towards Okta's goal towards becoming a "primary security cloud", by allowing partners to tap into threat detection and further enrich it by providing more direct context from their platform. I find this similar to what CrowdStrike and Sentinel One are striving for, by turning EDR into XDR, and, in fact, Okta is already partnering with many EPP/EDR providers (though not Sentinel One yet) for getting device context.
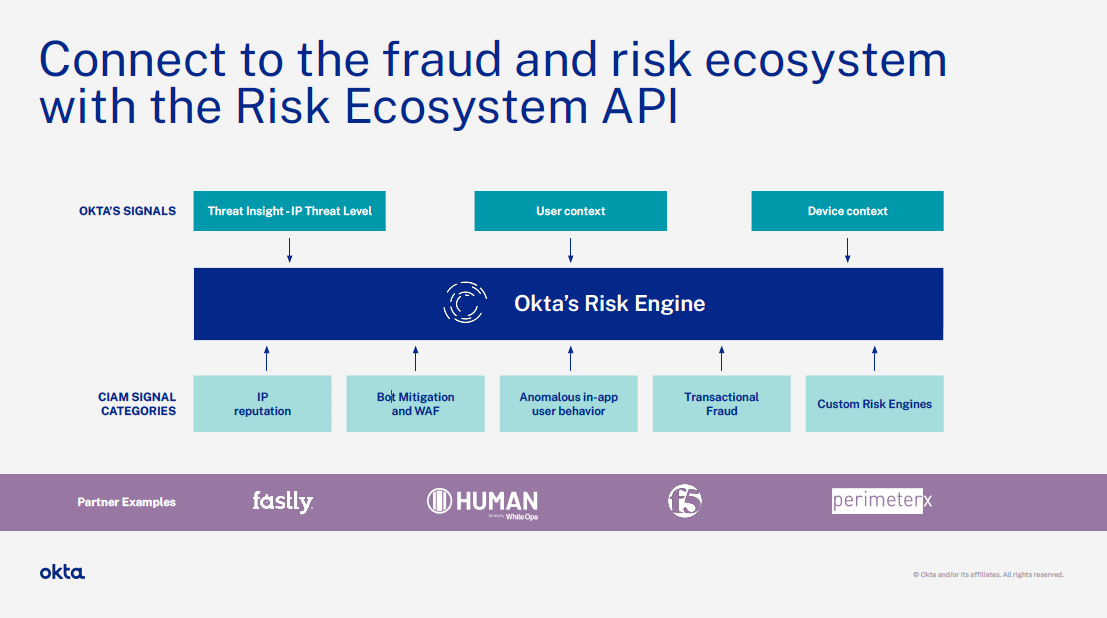
However, in the architecture diagram they provided in Investor Day in Apr-21, notice how Okta is abstracting out "device context", neglecting to mention its EPP partners like CrowdStrike? Acknowledge your vital partners, Okta! I pressed them on this in a question during Investor Day Q&A, and they acknowledged that the Risk Engine is ultimately about achieving better risk analytics to improve the intel across all partners. I am also wondering why that earlier partnership with CrowdStrike, Proofpoint, and Netskope was not part of this Risk Engine announcement either. Shouldn't all these integrated partners be intermingling threat intel signals in this platform? Perhaps it is because these partners also want to be the analytical engine underlying all these Zero Trust platforms. [As I have discussed before, control of the analytics is up for grabs. Who will own the analytics across these Zero Trust ecosystems?]
Auth0 Acquisition
Okta started into Customer-focused IAM (CIAM) with its acquisition of StormPath in 2017. It is now reported to be 1/4 of their business, and is growing faster than the Workforce segment, at >50%. [Meaning Workforce segment is the biggest drag on growth right now. This past Q122 had revenue growth dropping to +38%, so by my rough calc, the other 3/4 of their business only grew 33% at most.]
After first approaching them in Nov-20, Okta announced an agreement to acquire Auth0 in Mar-21, in a $6.5B all stock transaction (1/6 of their market cap). It was discussed over and over – first covered in a slide deck about the acquisition and discussed in the same day Q421 earnings call, then again was a major focus during Oktane'21 and their Investor Day in Apr-21. The deal closed quicky (in two months), and was then again discussed in the subsequent Q122 earnings call in May-21 [then again, after this was published, in a Showcase event in Oct-21]. I guess it shows how important it is now, given how the combined CIAM segment will now be nearly 40% of their revenue, and be growing faster at >50%!
Auth0 has a majorly different GTM motion in their CIAM platform from Okta. Auth0 has been built as a developer-focused SaaS platform and SDK that is used by developers to embed authentication and authorization features into their application. It is vital developer tooling that can provide a core piece of an application's functionality, like Stripe (for payment processing) and Twilio (for handling customer communications) do, for embedding features that no development team wants to build from scratch. With such a heavy developer focus, Auth0 had a clear bottom-up GTM motion, yet also had major customers, including Pfizer, The Economist, News Corp, and Mazda. Okta, on the other hand, approached the CIAM market as it did its earlier Workforce-focused platform – from the top-down, selling it into mgmt and C-suite, in order to take over all identity concerns for the platforms that its customers are building. One of its major customers is Adobe, which uses its CIAM platform to manage all user access to its Creative Cloud.
Unfortunately, they aren't sharing many specific financials yet from Auth0 [this appeared later, in Q222's slide deck]. What we do know is that this joining of two CIAM platforms was nearly a merger of equals: Auth0 was mentioned as having >$200M ARR by "the end of this year", growing >50%, while Okta mentioned that CIAM is nearly 25% of their revenue, also growing >50%. At the time, Okta had $835M TTM Revenue, so ~$208M of that from CIAM. For now, Auth0 will be a separate unit, with Auth0's CEO Eugeno Pace reporting to CEO Todd McKinnon.
At first blush, this acquisition seemed an admission by Okta that their GTM motion was all wrong – but they assure us this is not the case. They heavily stressed that both GTM motions are valid (as the near equal success of both platforms prove), and both will continue to operate in this space. Auth0 also has a much larger international presence – both in its remote workforce, as well as how 40% of revenue is coming from outside the US.
On the plus side, this takes out a rising major competitor, adds in a large group of new customers, and expands Okta internationally, all while grabbing some stellar talent and platform that should nicely align around a common forward vision. They sold it as strengthening their overall position in CIAM, and it is immediately accretive. On the downside, there is just a lot to figure out here by Okta and Auth0 product and sales teams going forward. It feels odd in how Okta plans on keeping the 2 diametrically opposed GTM motions at play here, but they insist there is not much overlap in the sales cycle.
There was a lot of talk about "synergies" in slides about the acquisition (ugh), which shows they clearly don't know yet what those are, or how these 2 separate CIAM platforms (and the GTM motions that they use to sell it) can slowly be integrated into one. The one planned platform change mentioned initially is that they can combine security risk intel (so is likely powering both platforms from Okta's Threat Insights and new Risk Engine). They talk up the potential for cross-sell, but, while I don't recall seeing specific numbers, they mentioned there is overlap of existing customers. [It seems pretty likely that a significant portion of customers already use Okta for Workforce IAM and Auth0 for Customer IAM.] The CFO also mentioned the possibility of their partner channel selling Auth0, but that seems a huge reach considering the bottom-up GTM motion that Auth0 has. This acquisition also blurs the financial picture at the same time I am disappointed in top-line growth waning.
Adjacent markets
During Oktane'21 in Apr-21, Okta made a bold new proclamation that they are finally entering adjacent markets – ones that prognosticators like myself (and Gartner, see above) have seen coming for a while now. They are (finally!) veering into the Privileged Access Mgmt (PAM) and Identity Governance and Admin (IGA) markets. Unfortunately, both of these are just dreams right now - actual products won't be ready until a year from then, in early 2022.
Privileged Access Mgmt (PAM) is about controlling access to systems by the users that can administer them (sysadmins). This might be controlling access to on-prem or cloud servers, or other app stacks like Kubernetes or databases, that users can log in to with administrative rights to make system changes, create cloud infrastructure, deploy apps, or launch containers. The just released Gartner Magic Quadrant for PAM for Jul-21 shows that CyberArk and BeyondTrust are the top leaders in this space. PAM features typically include secrets management, access rights tracking, and a mechanism for dynamicly logging into to host servers through their platform via temporary credentials (in what is called Just-in-Time access).
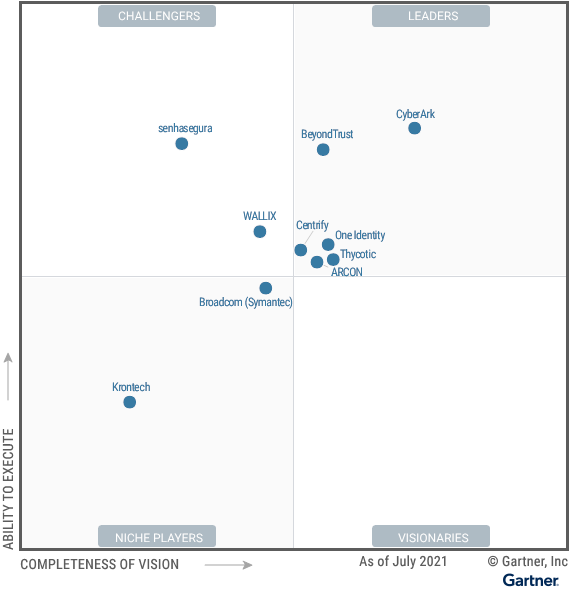
However, I urge a strong caution with this particular Gartner report. Gartner seems to be heavily focused on the past features, not the future ones, by requiring companies in the report to have a local agent running on the host systems. [A very rare misfire from Gartner in regards to Zero Trust, as they have been all over the general trends in Zero Trust, Continuous Analytics, and SASE Networks over the past few years.] Not sure why their criteria here would be so strict as to exclude Zero Trust PAM solutions, which would typically be agent-less. The report mentioned excluding Fudo Security, Saviynt, Remediat, Teleport, and XTON platforms for this very reason, with all having Zero Trust or other forms of cloud-based Just-in-Time features. Instead of using a host-based agent to manage remote admin logins into a company's systems, Zero Trust provides a fantastic mechanism for creating a temporary one-off network connection to the requested server, after verifying the user's identity and device.
Okta announced in Apr-21 that it is pivoting its Advanced Server Access into a new PAM product. It will track authorization rights for sysadmins, and use Zero Trust based methods to create ephemeral, one-off connections to those systems. Relatedly, as recently mentioned, Cloudflare is also getting into remote system access via Zero Trust [premium post], including having Zero Trust SSH and VNC access available through the browser, which seems like a direction Zscaler could move towards as well.
I don't see much to worry about in existing PAM platforms that are mostly rooted in the legacy agent-based solutions. CyberArk has been busy expanding from PAM into Workforce and Customer CIAM (moving towards Okta). However, they are also busy shifting their customer base from licensed into SaaS subscriptions. Q121 had revenue growth of just +5.6% – yet ARR continues to grow in the low 40%s every Q. BeyondTrust is more a pure-play PAM competitor. Again, I see Zero Trust disrupting these legacy PAM players.
Identity Governance and Administration (IGA) involves the orchestration and tracking of users' access rights across your application (typically meaning over an IAM). Okta already does the "A" in IGA, with their Lifecycle Management system that allows for tracking and automating workflows around managing identity, combined with their no-code Workflows system that allows a user admin to stitch together a custom workflow. They are now committing to doing more of the "G" in IGA – the governance. Governance is all about assuring compliance with set business policies, and automating processes in order to minimize errors and risk. They perhaps gave us a hint they were thinking about IGA, when they explained what it is an in-depth blog post back in Oct-20. In their upcoming new IGA product announced in Apr-21, they are adding in new features to better track access level change, while automating the workflows around how users request & approve access.
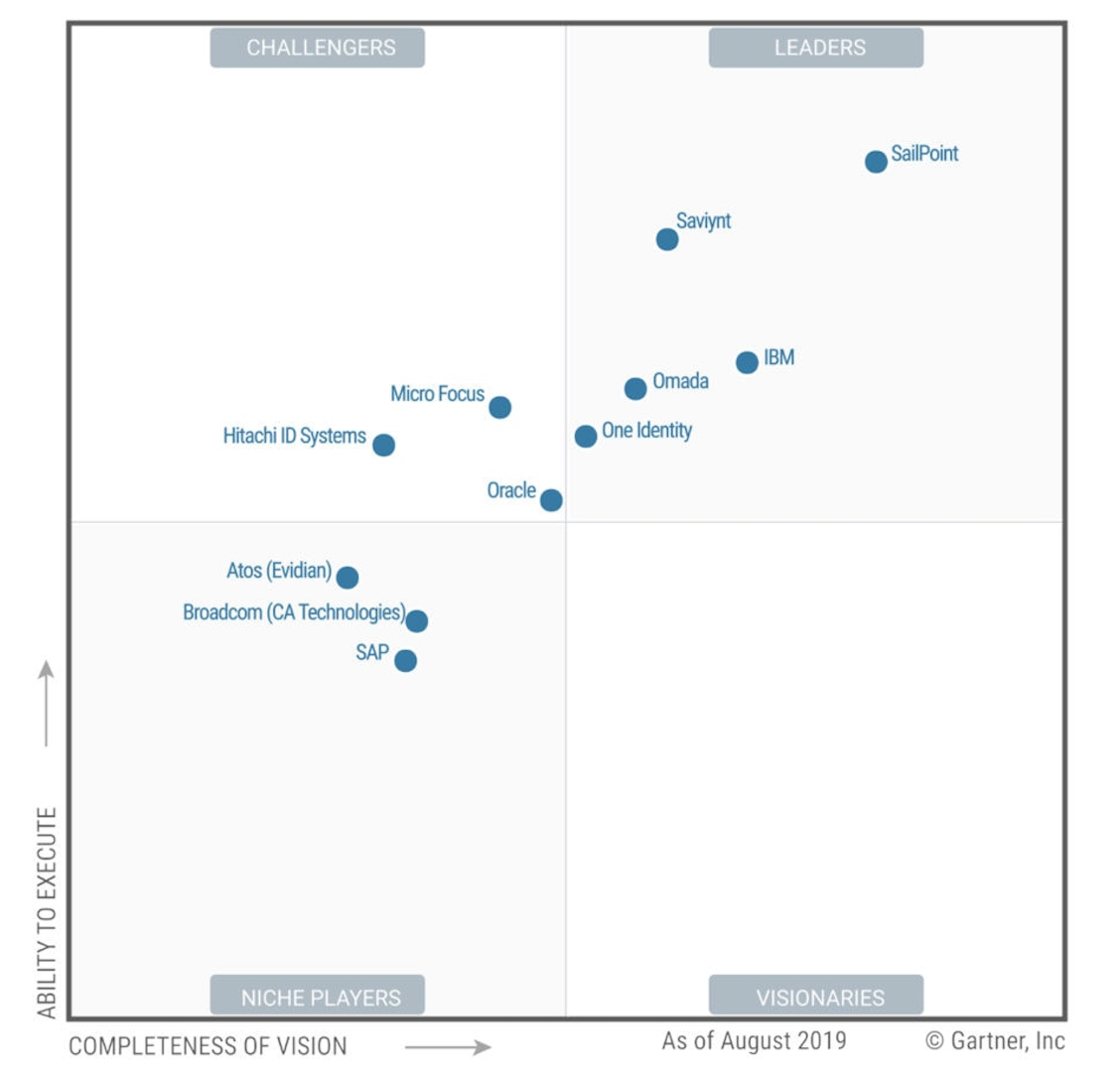
The market here is pretty forward thinking. Sailpoint is the top leader in the Gartner Magic Quadrant for IGA. [Note, however, that Gartner discontinued publishing it last year, and is only doing Market Guides now, like this one from Dec-20.] IGA is still a heathy market too, as Sailpoint had subscription revenue grow +35% YoY in its latest reported quarter, while ARR grew +43%. Sailpoint is also adding Cloud Infrastructure Entitlement Management (CIEM) features, after its acquisition of Orkus in Oct-19. CIEM provides IGA features over cloud workloads like VMs, containers, and serverless functions. Saviynt is another leader in IGA to watch, who are also expanding into Zero Trust PAM and CIEM. And Zscaler also has a CIEM product, after its acquistion of Trustdome back in Apr-21. I fully expect Okta to move into CIEM as well.
[And talk about confusing acronyms ... SIEM ("sim"), CIAM ("see-yam"), and CIEM ("see-yem") are all different parts of these security platforms!]
Adding IGA (and CIEM) is a strong move toward an overarching identity platform with better management and compliance features across whatever environments a company might have. Not only do IGA features integrate completely with IAM for governance over user access rights, but also with PAM for governance over sysadmin rights. Focusing on these adjacent markets is long overdue. Unfortunately, we won't see any new products for a year – they were clear that we should not expect much until the first quarter of 2022 (the start of FY23 for Okta). So maybe we'll see a revenue impact by Q223? I wish they had added these adjacencies sooner, which could have possibly kept Land and Expand rolling along, keeping revenue and customers growing at a stronger level.
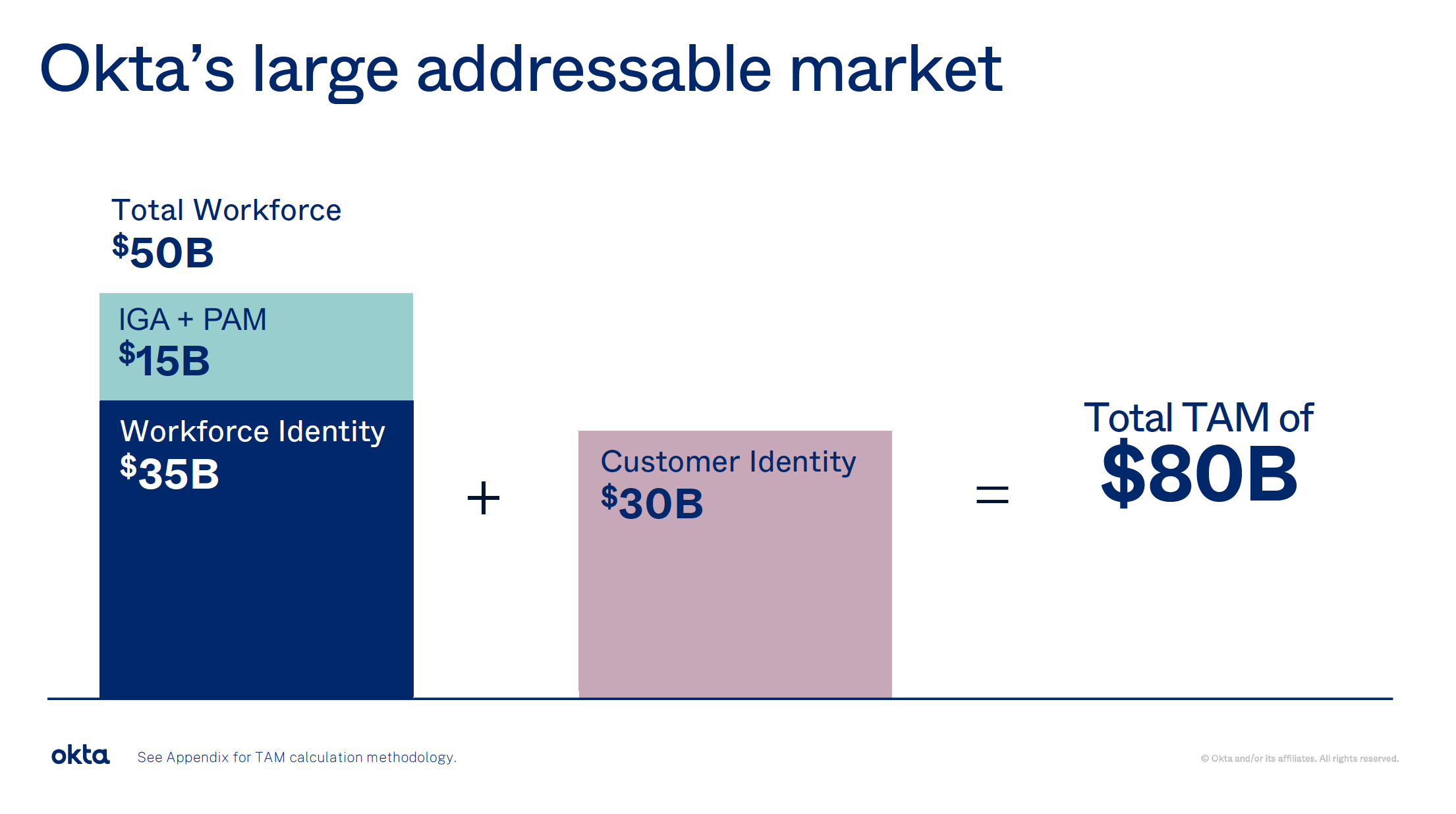
What do these new markets mean in terms of TAM expansion? During Investor Day during Oktane'21, they noted that Workforce and Customer TAMs have both grown by $5B, and that PAM and IGA features over Workforce will add an additional $15B.
Management changes
With all these product additions and a major acquistion under their belt, why not have a major shift in executive management!
During Q321 earnings in Dec-20, they announced that the long-time CFO was retiring as of Mar-21. Mike Kourey, a BOD member since Oct-15 that headed the Audit committee, would then step into the role... and barely lasted a single quarter, departing on June 1. In an interview with Jim Cramer, the CEO stated it was a culture clash – an odd take given that Kourey was very well known as a BOD member for nearly 6 years! What a mess. Until a permanent replacement is found, the SVP of Finance will serve as interim CFO. Not a good time for this, having to merge financials with a major acquistion. [Update in Oct-21 – still no permanent CFO in place.]
Luckily, other personnel changes look quite promising. One major step was in hiring Susan St Ledger back in Sep-20, to replace the retiring President of Worldwide Field Operations. Susan has lead major growth initiatives at Splunk and Salesforce. She took a pretty active role in the Investor Day in Apr-21, and detailed how excited she is about Customer IAM, how much room Okta has internationally, and how they can leverage partners like SIs and cloud marketplaces. During Investor Day Q&A, she detailed how she plans to leverage what was learned at Splunk and Salesforce, and how the high growth motions used there were repeatable. There is more success to come as Okta transitions into something larger.
To bolster her plans, they recently hired a new CRO in Mar-21. Steve Rowland, ex-VP of Sales at Splunk (and DataStax and Apigee before that), previously worked with Susan St Ledger, and now reports to her. They also hired a new CMO at the same time, who previously had different roles at Accel, WeWork, AppDynamics (observability company acquired by Cisco), and Salesforce. This role will also report to Susan St Ledger. Most recently, they hired a new Chief Digital Officer in Jul-21, again a person from Salesforce. He is responsible for the "holistic creative, campaign, digital, and brand strategy", and reports to the CMO.
[The previous CMO is now "working on an emerging project inside of Okta". Intriguing! This was before they announced IGA and PAM, so cannot tell if it was related to one of those, or is something yet to come.]
Conclusion
Okta remains a strong company with a fantastic position in the trends. The continued adoption of cloud and hybrid architectures, plus the industry shifts towards Zero Trust to secure it, will continue to drive a healthy growth rate for years to come. I'm just not sure it will be at hypergrowth any longer – at least until new revenue streams start appearing from the adjacent markets they are entering, further helped by the federal government hopefully adopting Zero Trust en mass [premium post] in 2022. They continue to spend on expanding S&M internationally – but it will take a while for these intiatives to ramp up and start producing.
They are now the top name in Customer IAM with Auth0, and plan to continue to attack this market from the bottom-up and top-down simultaneously. Ultimately these platforms and operations will combine, but it will happen slowly – likely over several years. They aren't signaling that they know how to best integrate the platforms or the sales organizations yet. And unfortuately, they remain close lipped about the financial profile of Auth0, and what effect the acquisition will ultimately have on Okta's numbers. This is not being helped by the CFO transition, and the last conference call in Q122 was a mess (especially the last question about impact of Auth0 vs organic in guidance). [This paragraph is likely out of date now, with the Okta Showcase event they just had to further discuss the plans post-acqusition. I haven't watched it yet, given how my interest in this company has waned.]
Their FY22 guidance was originally +29-30% YoY in Q421. In Q122 earnings, they upped this to +47-48%, after a net increase of $135M (top of guidance grew from $1.09B to $1.225B). Much better! [Q222 earnings further bolstered FY22 guidance to +50%.] However, this now includes the impact of Auth0, who should contribute an ARR of $200M by then. Since they aren't giving us numbers, let's guess that Auth0 is at $145M ARR a year right now. Considering that Auth0 closed on May 3rd, and that Okta's fiscal year ends Jan 31st, it should contribute $110-120M over the remaining 9 months of the FY (May-Jan). This leaves the FY guidance for organic growth at around +32-34% now. [This was a good estimate on Auth0 contribution, who contributed 38M in Q222. Okta ultimately did +39% growth, a slight re-acceleration. For Q3 they guided to that same range, ~+33% organic.]
Hopefully they can start regaining a higher level of revenue growth in these new adjacent markets. RPO remains healthy, growing in the 50%s, with Current RPO also growing ahead of revenue at +45%. [In Q222, this further dropped to +42% and +43%.] Profitability is inevitable; Okta has been cash flow positive for nearly 2 years now, and were operational margin positive for most of the past year (until this latest quarter), and FCF margin is at nearly 15%. There is a lot to be excited about here. While the bulk of the company is growing in the low 30%s, now a roughly 40% of the company – their combined CIAM segment – is growing over 50%. Two new product lines are adding some very relevant adjacencies that they can upsell to existing customers – but it's a year until we see the impact from these. I'm content to watch Okta on the sidelines while it figures these new moves out, such as how to best integrate Auth0 into a holistic combined CIAM platform, and what the success will be of the the PAM and IGA product lines.
As a final comparison (because I can't help comparing these two), CrowdStrike is at a higher level of revenue ($303M vs $251M) and higher levels of profitability (FCF margin 32% vs 15%) – all while still maintaining revenue growth of 70%. It does have a lower RPO ($1.47B vs $1.89B), but will surpass that soon too, given that it is growing much faster (+80% vs +52%).
In the Q2 earnings since this post was written, the financial picture becomes a bit more muddled with the Auth0 acquisition – however, their investor slide deck does a good job of giving the isolated picture between Okta organic and Auth0 contributions. (Kudos to Okta for breaking it down so clearly.) The overall slide in organic revenue growth continues, with Q3 guidance for +50% equating to ~33% organic growth, after removing Auth0's same $38M contribution from Q2.
I haven't watched the latest Showcase events that discussed the Okta + Auth0 combination further, but my criticisms all remain about how Okta is ignoring its partners in its rollout of Risk Engine, a product entirely based upon integrations with partners. To compare Okta again to CrowdStrike, I have written a premium piece lately on CrowdStrike's release of XDR, who I believe has a much better approach integrating with and focusing upon vital partners in the security ecosystem. The partners featured in their new XDR Alliance include Okta.
- muji
